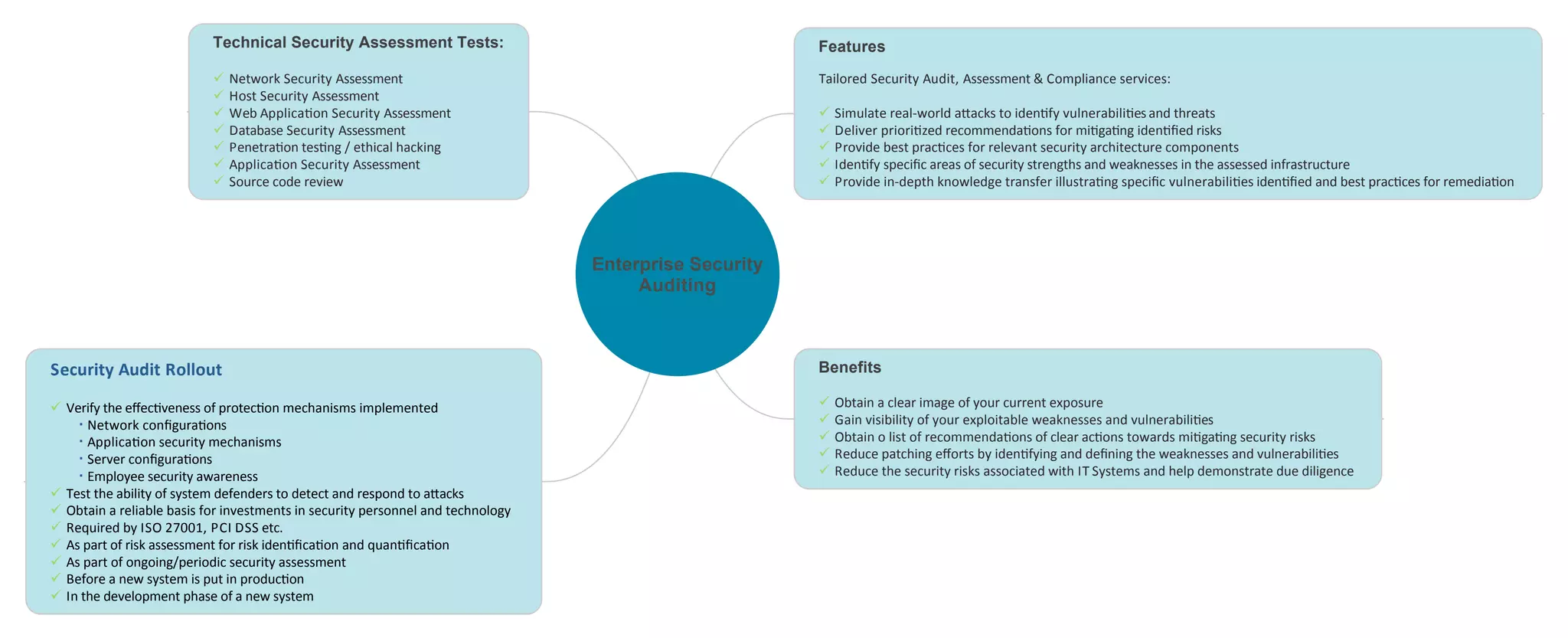
This document describes technical security assessment tests and enterprise security auditing services. It lists features such as network, host, web application, and database security assessments as well as penetration testing and ethical hacking. The services help identify security vulnerabilities and weaknesses, provide best practices recommendations, and increase security knowledge. Security audits verify the effectiveness of implemented protections across network configurations, applications, servers, and employee awareness. Benefits include gaining visibility into exposures and reducing security risks.