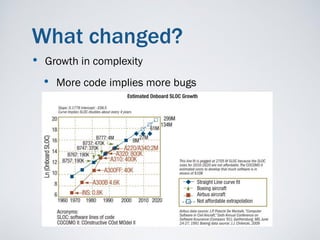
This document summarizes a presentation on secure software development given by Rod Chapman. It discusses how safety-critical systems have historically used formal methods like correctness-by-construction (CbyC) to build reliable systems. However, secure systems operate in a malicious environment and must assume arbitrary attacks. While CbyC offers confidence by verifying properties, it is not a silver bullet and still requires solid security engineering. There are also concerns that efforts focus too much on legacy code instead of prevention and that security requirements are an infinite set that cannot be fully enumerated. The future may involve combining formal verification of critical components with other techniques for less critical parts and architecting to isolate systems of differing security needs.







![Safety and security…
the difference?
• Possibly the most notable difference is in the
environment itself.
• Safety-related systems – mostly operate in a benign
environment that we can control to some extent.
• Security-critical systems operate in a openly malicious
environment where we might have no control over inputs,
access, and so on
• ..and…attackers are arbitrarily intelligent, well-funded and
motivated.
• “Programming Satan’s Computer” [Needham and Anderson]](https://image.slidesharecdn.com/securesoftwarechapman-130207094620-phpapp01/85/Secure-software-chapman-9-320.jpg)






