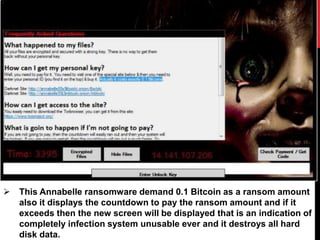
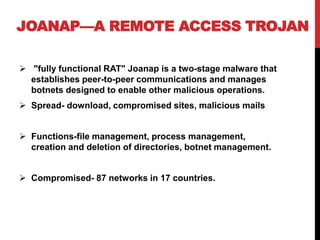
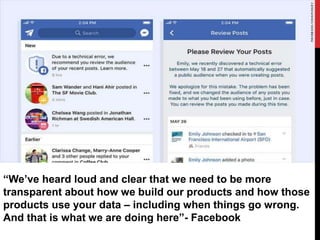
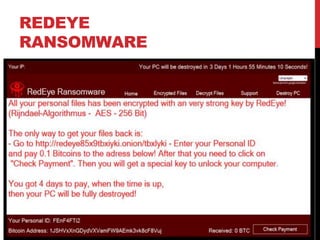
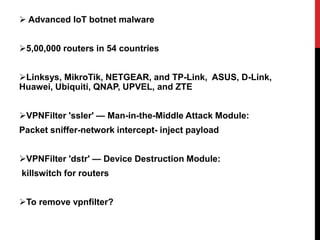
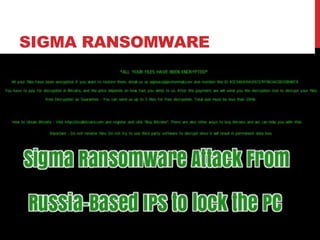
This document provides a monthly roundup of cybersecurity news and events from May 2018. It discusses the emergence of new ransomware variants called Annabelle and MBRlock that encrypt the master boot record. It also reports on alerts issued by the FBI and DHS about malware used by the North Korean hacking group Hidden Cobra called Joanap RAT and Brambul SMB worm. Other topics summarized include a Facebook bug that set posts to public by default, the newly discovered RedEye ransomware, a vishing scam that stole Rs. 7 lakhs from a woman in India, Microsoft's acquisition of GitHub, and data breaches at MyHeritage and Operation Prowli impacting over 40,000 servers.