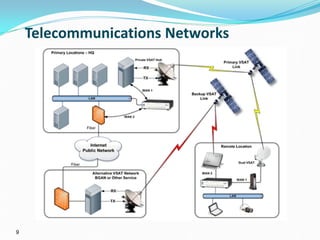
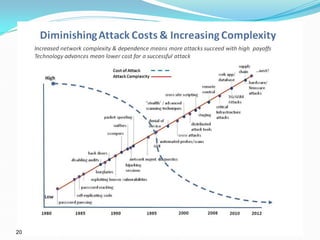
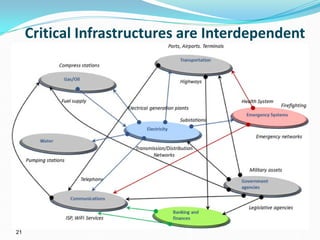
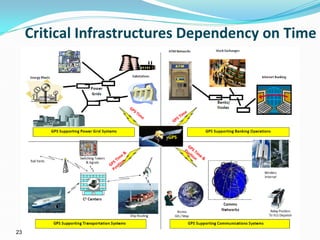
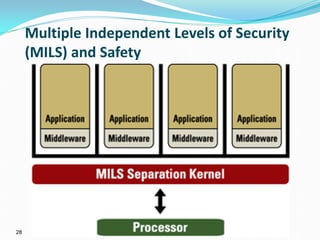
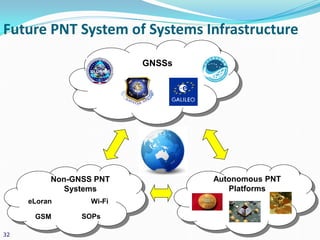
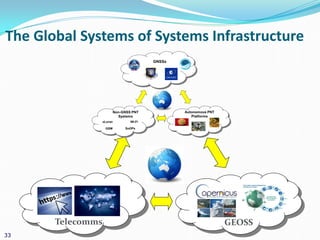
The presentation discusses the security challenges faced by large, complex systems that underpin critical infrastructures, which are vulnerable to cyber-attacks and require robust information security measures. It emphasizes the interdependency of critical infrastructures and outlines essential solutions for enhancing security through resilient system architecture and effective design principles. The conclusion highlights the necessity of integrating security features from the onset of system design to address the growing demand for safety and security in increasingly networked environments.


![3
Critical Infrastructures
• Critical infrastructures are “so vital (…) that the incapacity
or destruction of such systems and assets would have a
debilitating impact on security, national economic security,
national public health or safety.” [U.S. Homeland Security
Presidential Directive on Critical Infrastructure
Identification, Prioritization, and Protection, December 17,
2003];
• An EU critical infrastructure is an “asset, system or part
thereof located in Member States which is essential for the
maintenance of vital societal functions, health, safety,
security, economic or social well-being of people, and the
disruption or destruction of which would have a significant
impact in a Member State as a result of the failure to
maintain those functions” [Council Directive 2008/114/EC of
8 December 2008].](https://image.slidesharecdn.com/sp4scrome2015lisiv02-150824223409-lva1-app6892/85/Security-in-Large-Strategic-and-Complex-Systems-Challenges-and-Solutions_Lisi_2015-3-320.jpg)