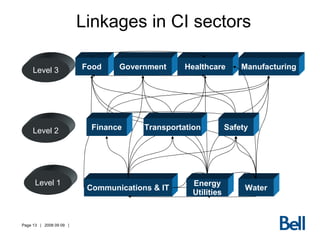
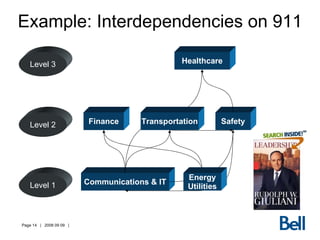
The document discusses critical infrastructure (CI) in Canada and strategies for protecting it. It identifies key sectors like energy, communications, finance, and transportation. It outlines a strategic approach involving federal and provincial collaboration with CI owners. The challenges include the vastness and interdependencies of the systems. Communication networks are recognized as highly important CI. The Internet poses unique challenges due to its size, lack of governance, and potential for cyber attacks.

























![Brian Phillips [email_address] 403 831-2434 Thank you](https://image.slidesharecdn.com/brian-philipsbell-focused-sessionoct28-1226590584306323-9/85/A-Network-of-Networks-34-320.jpg)