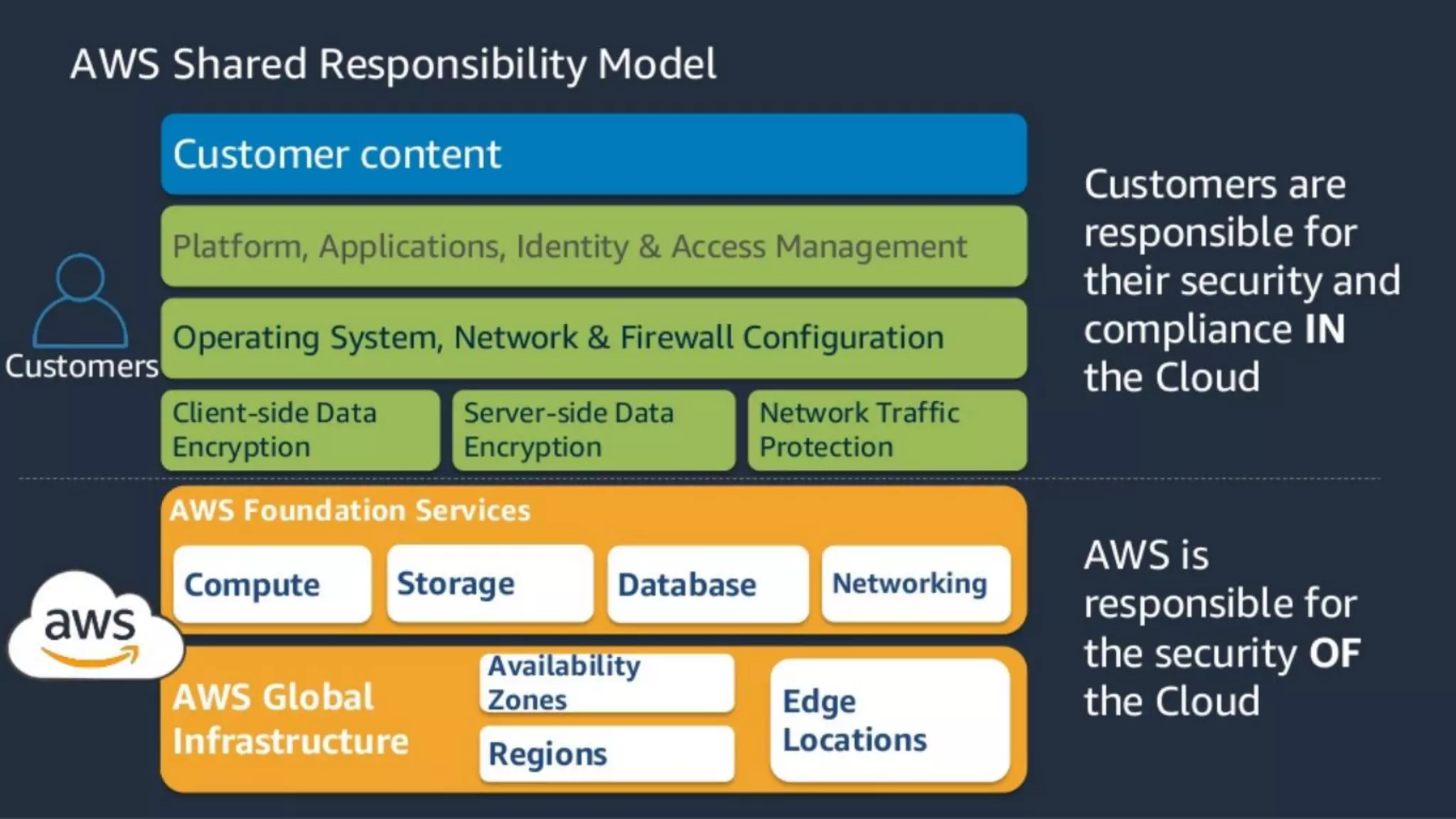
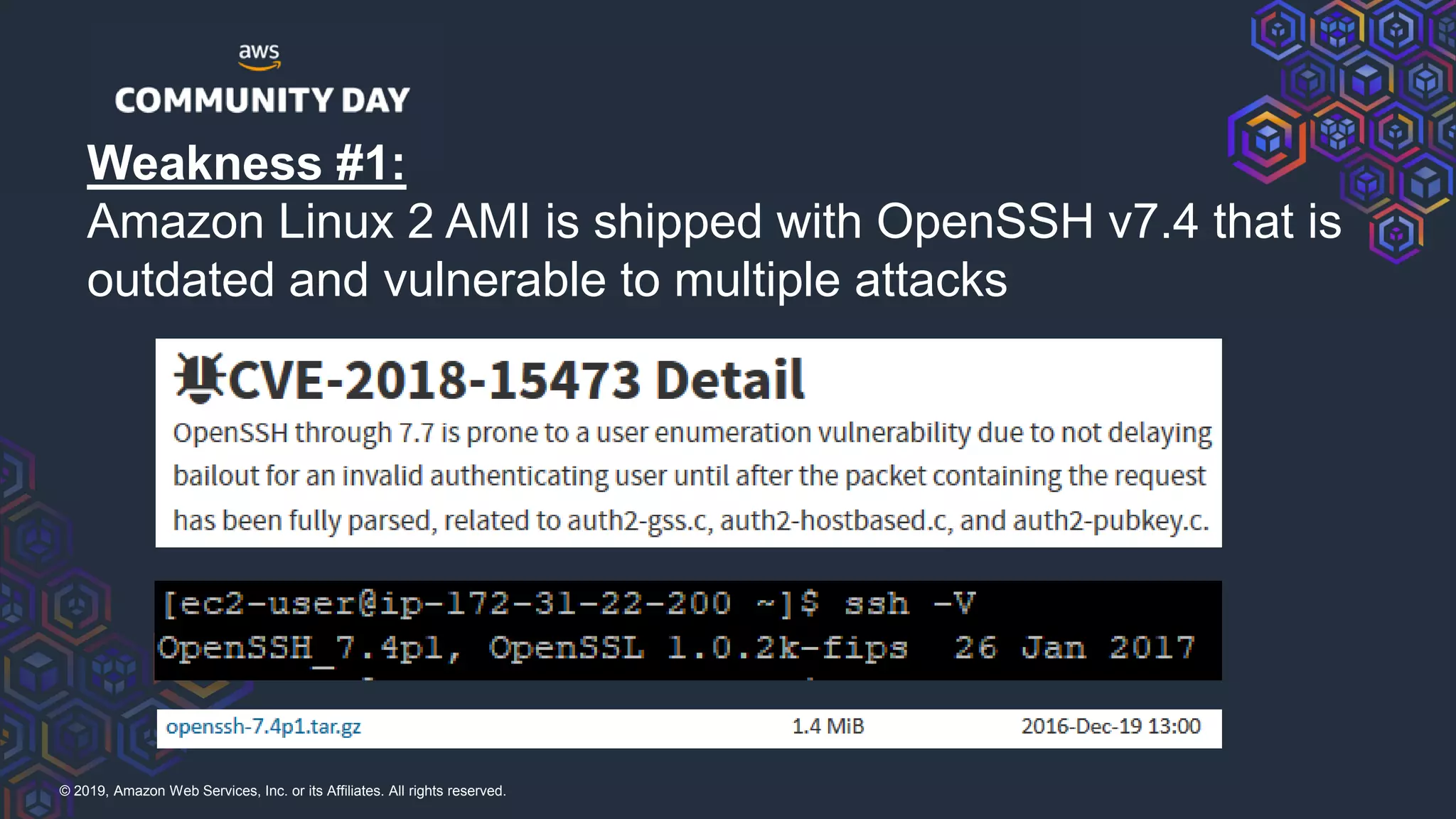
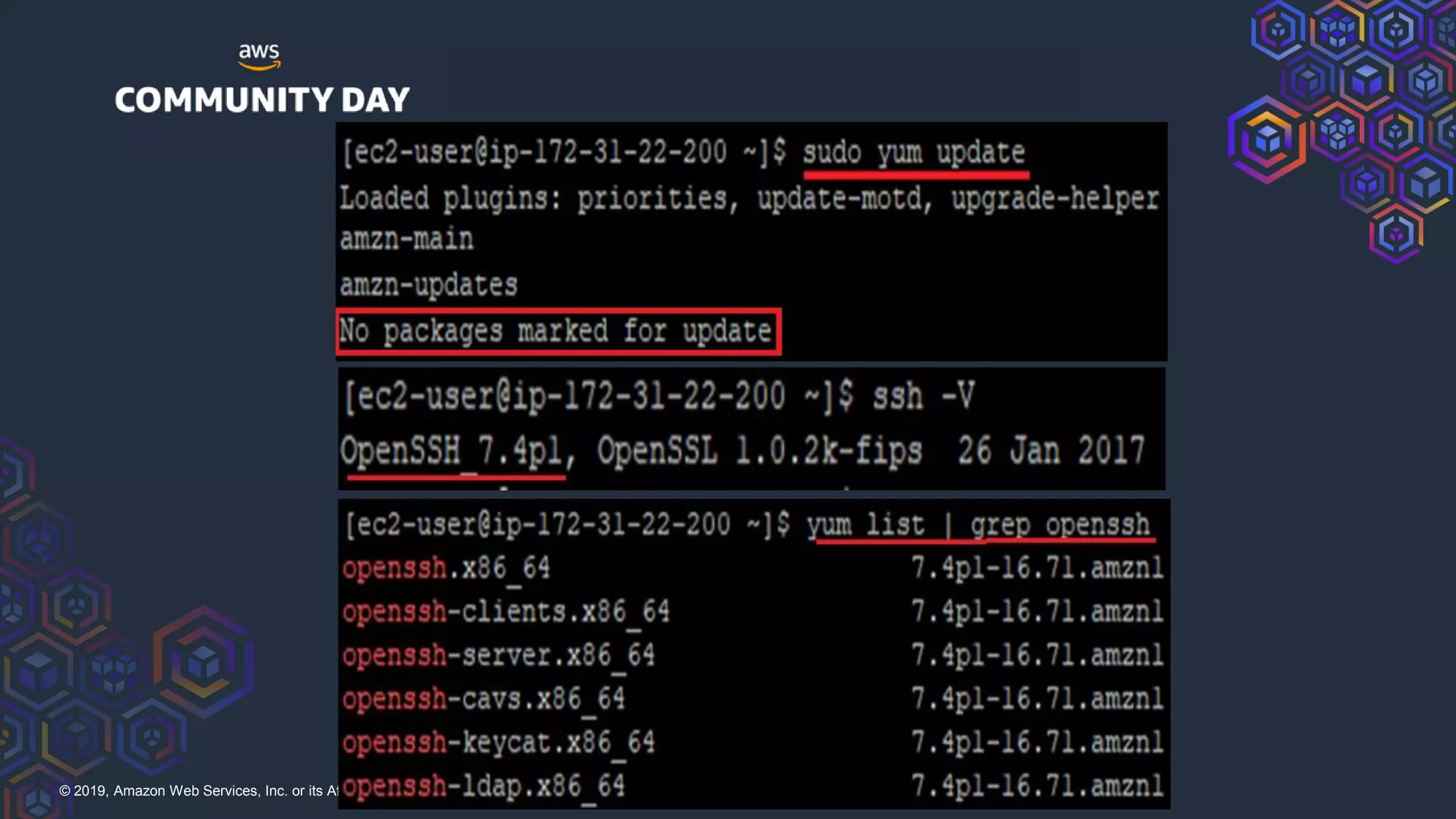
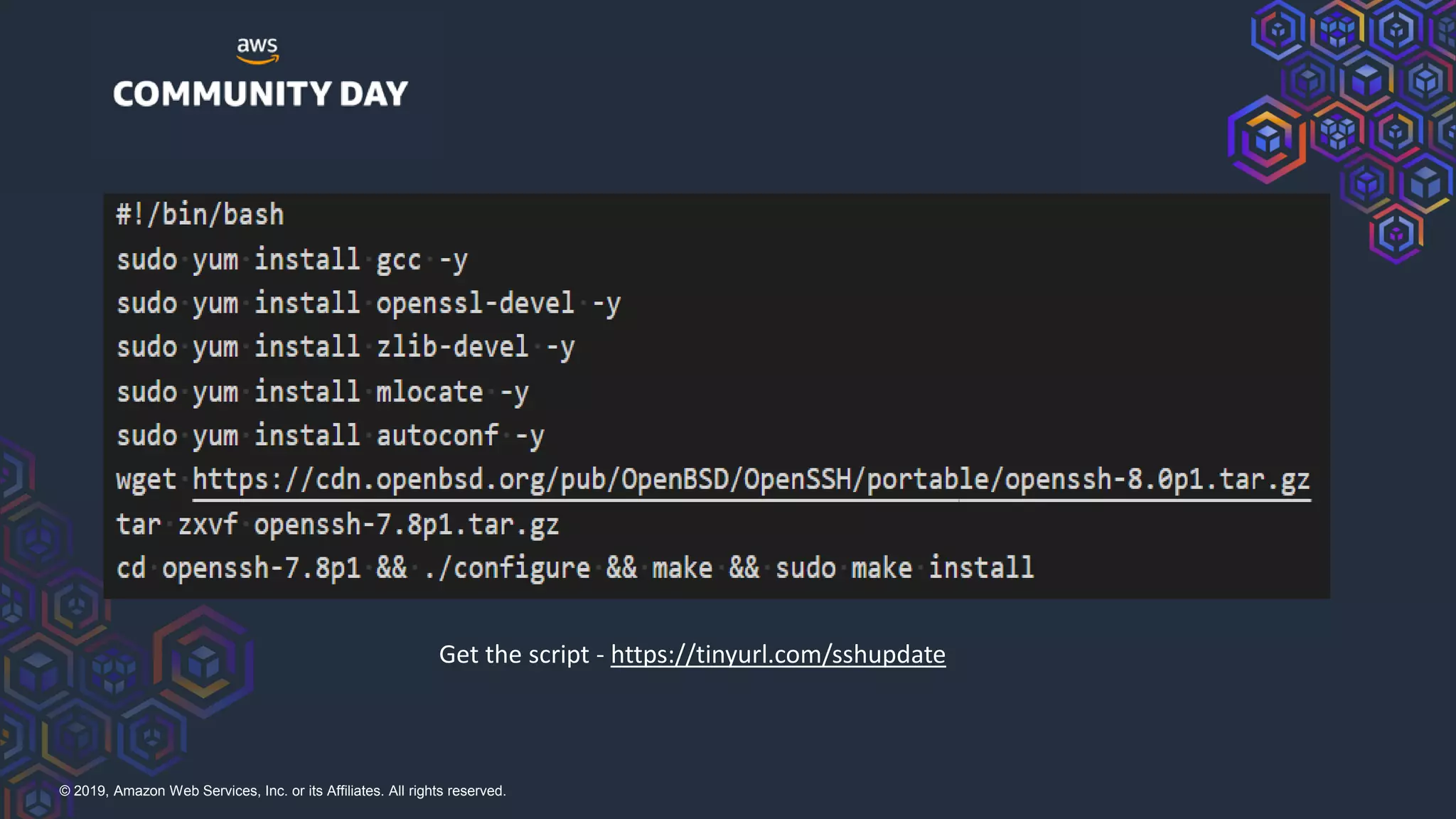
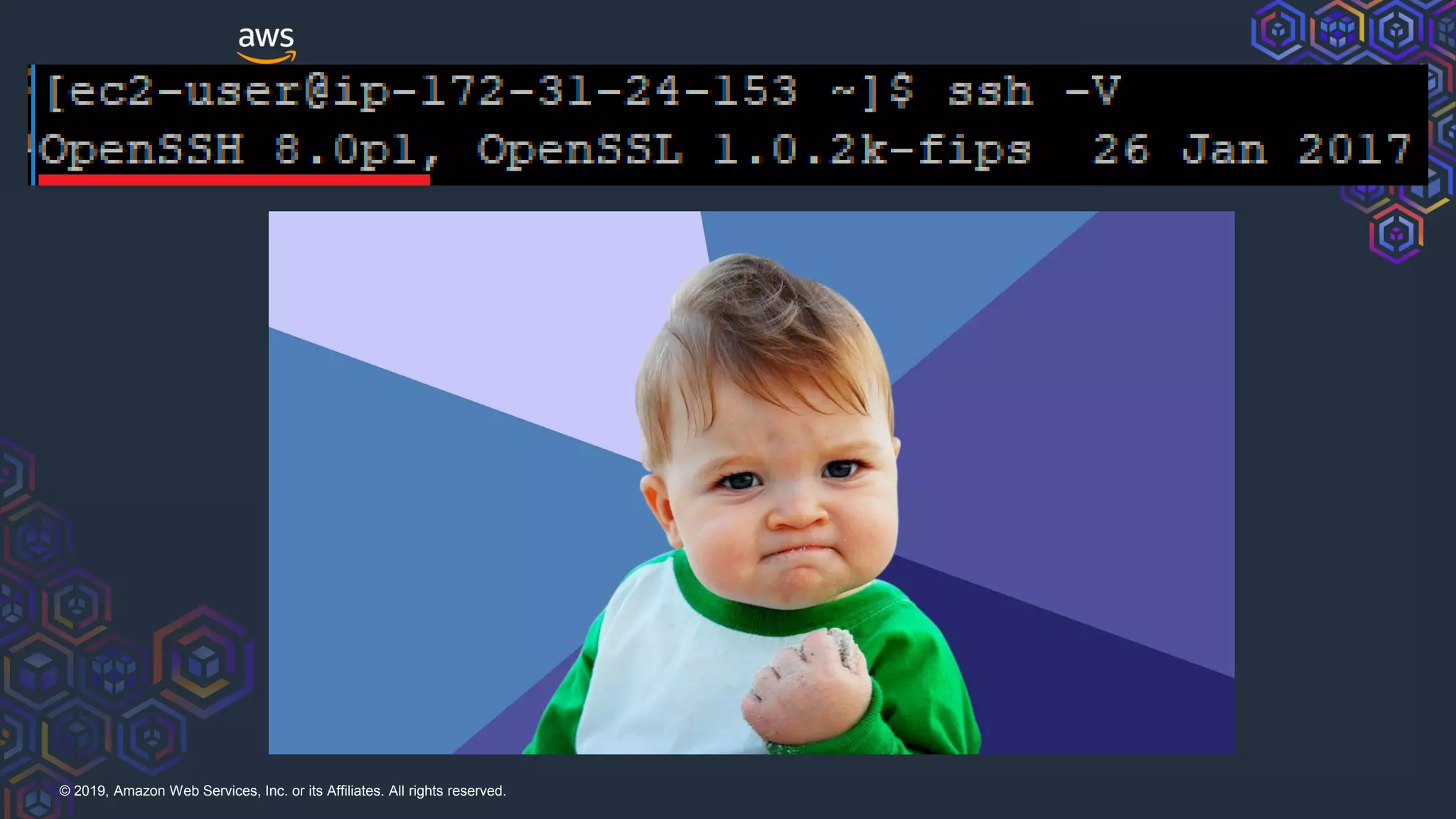
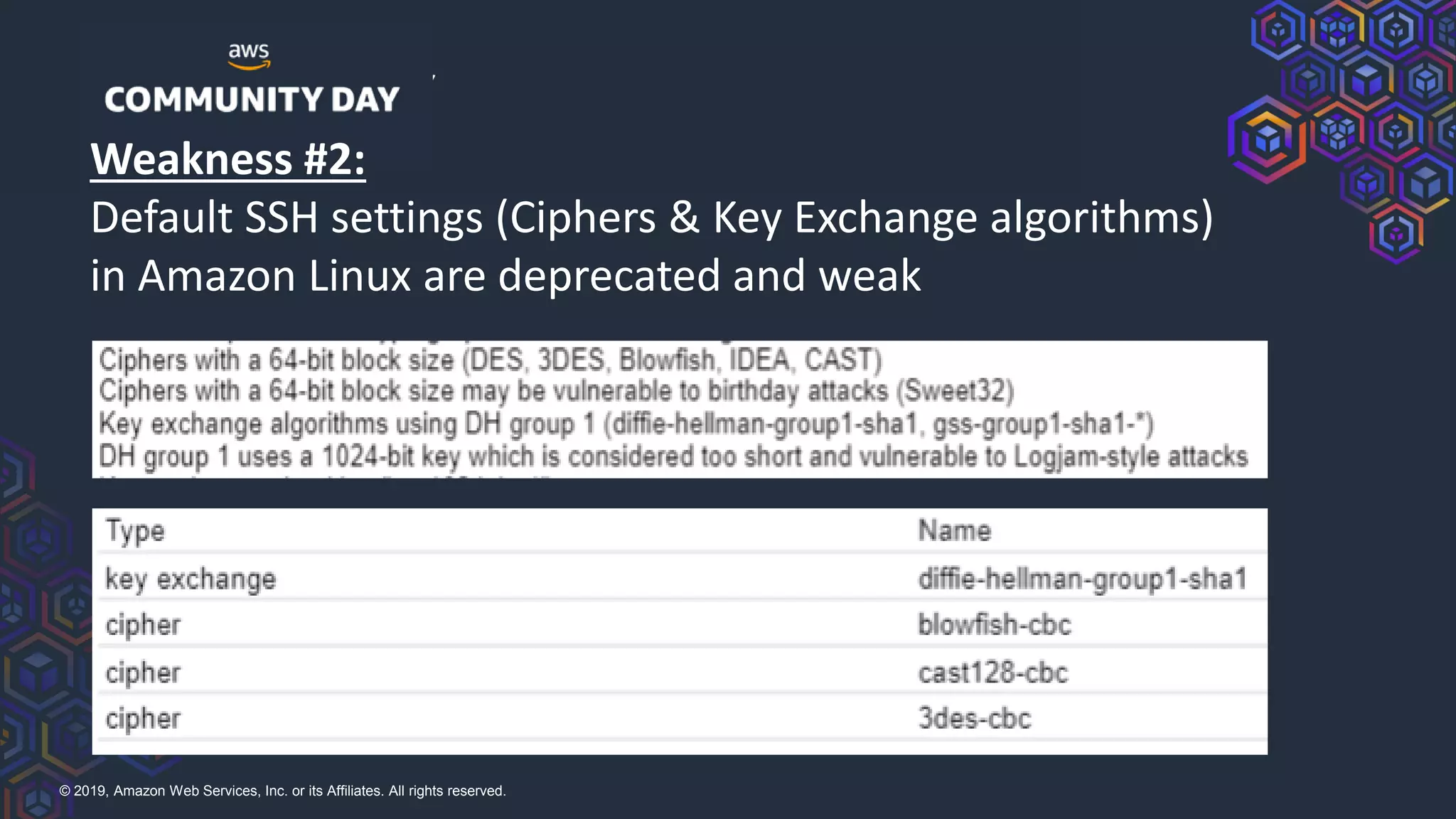
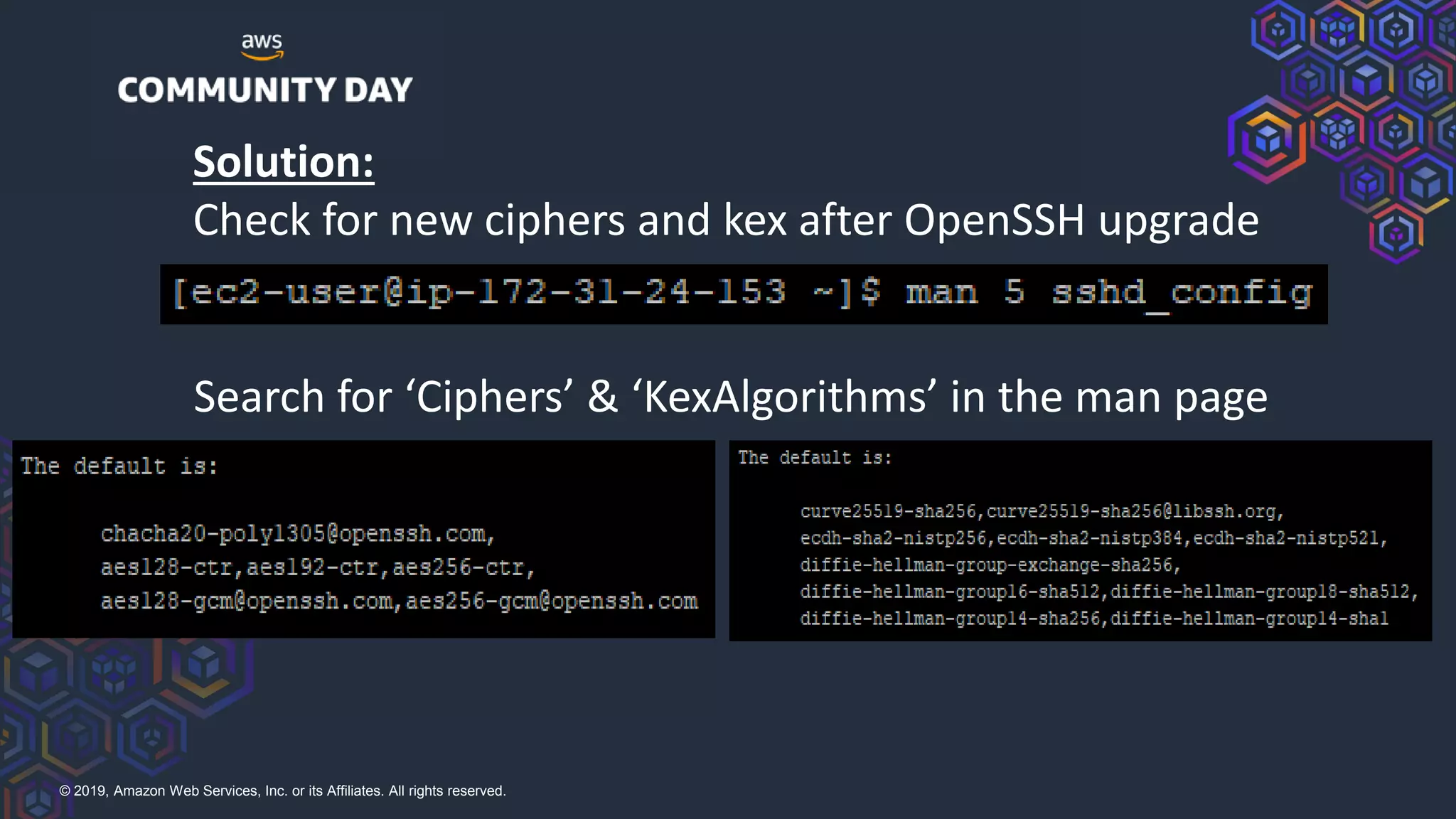
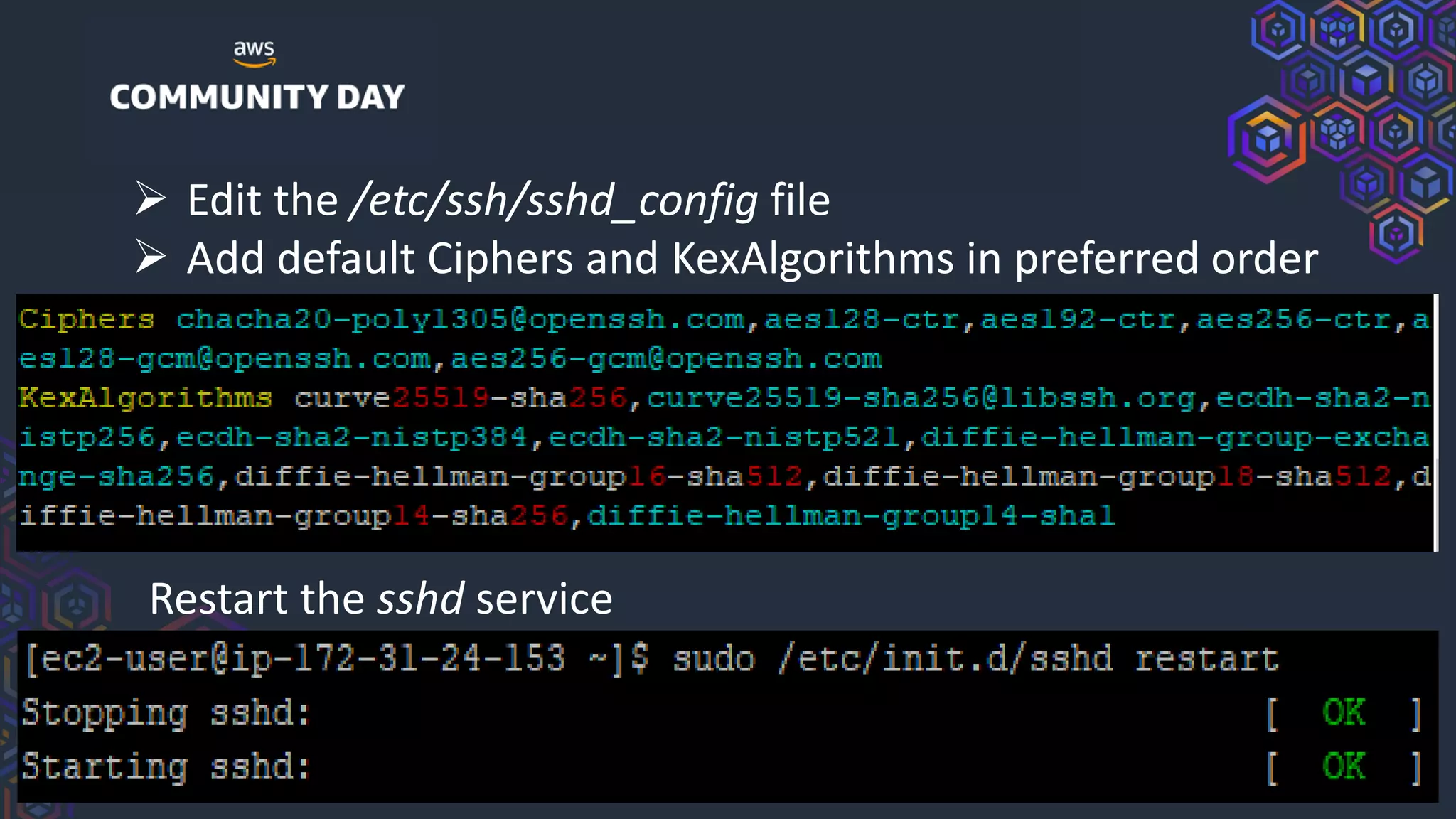
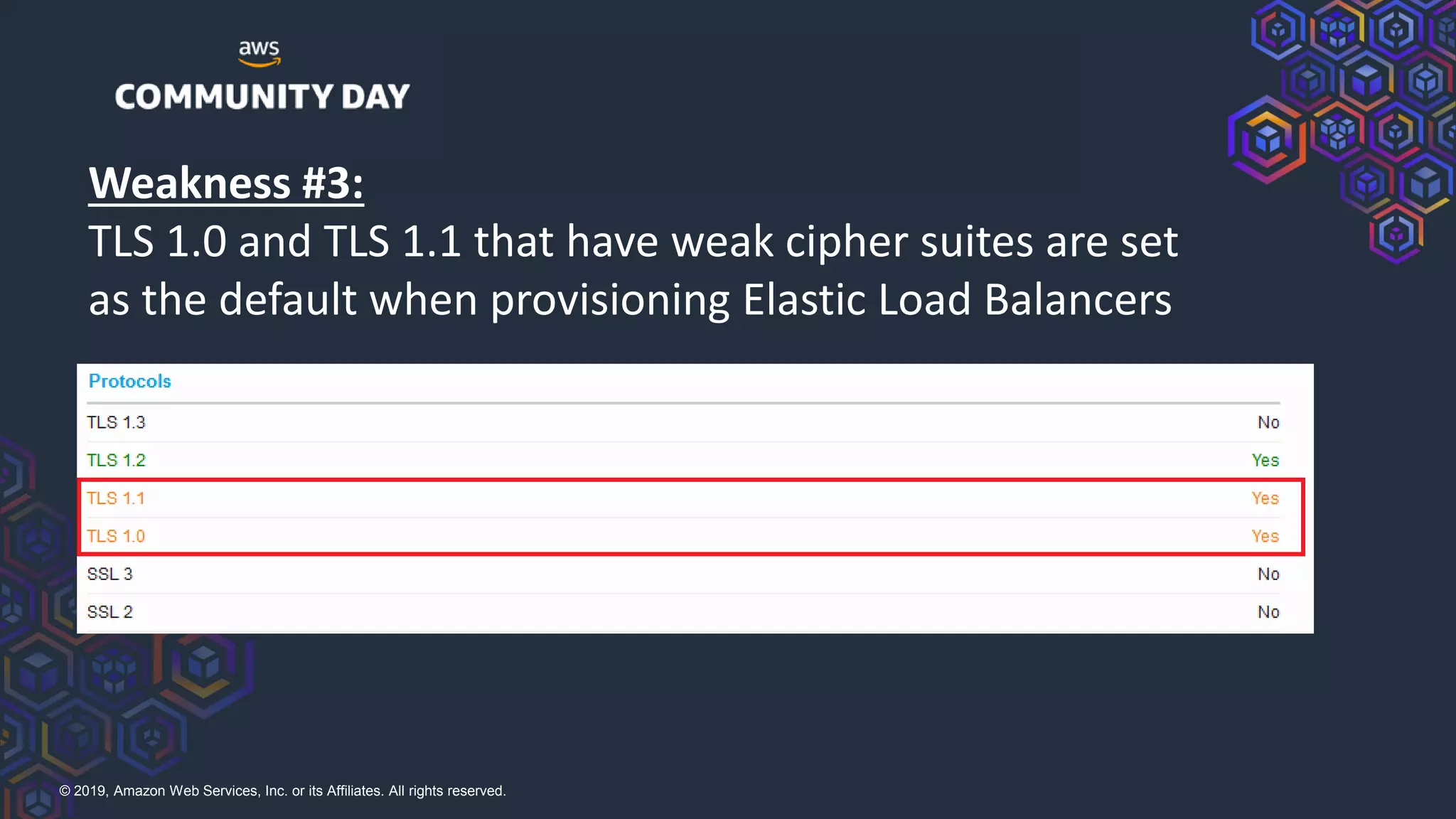
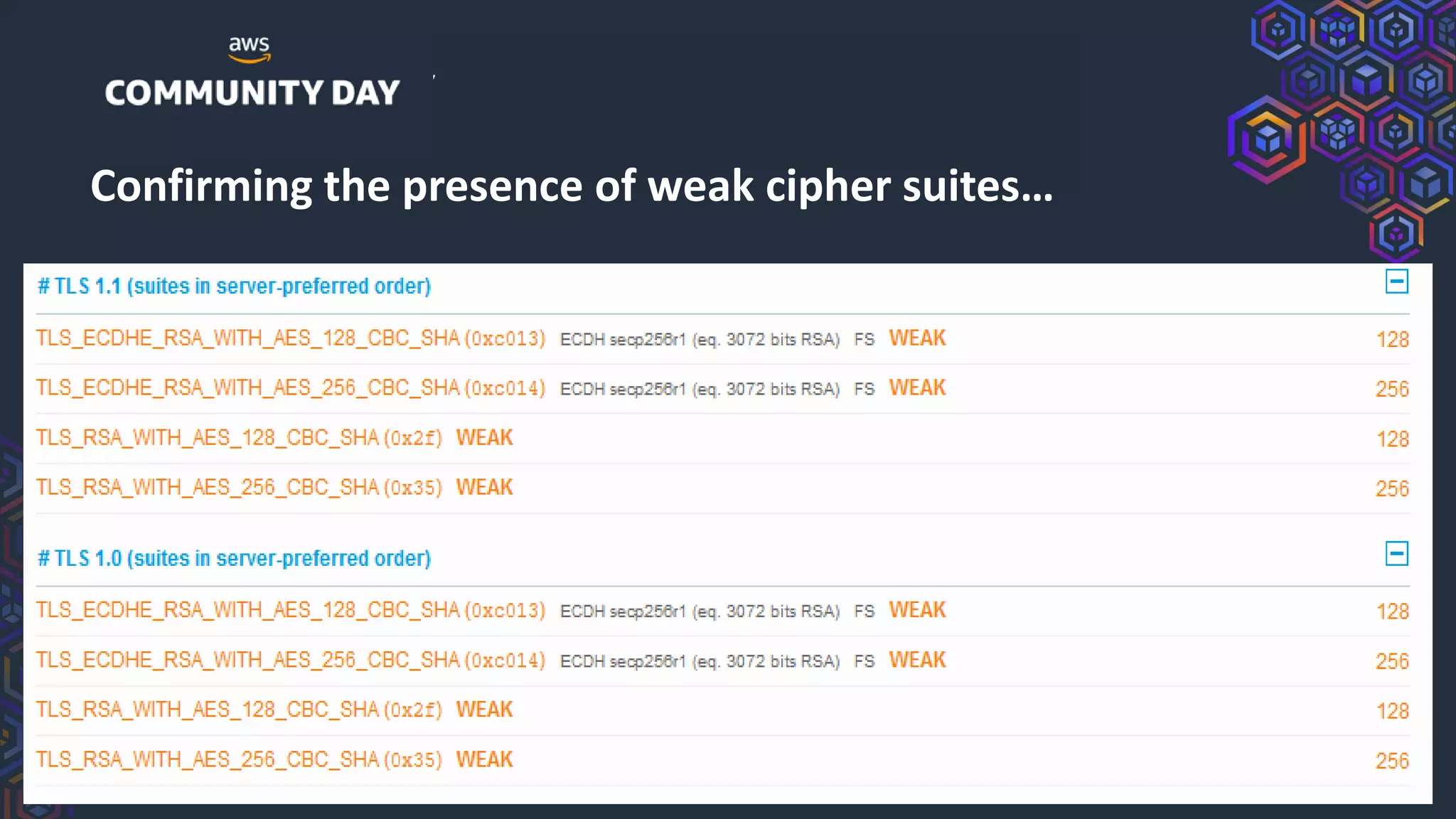
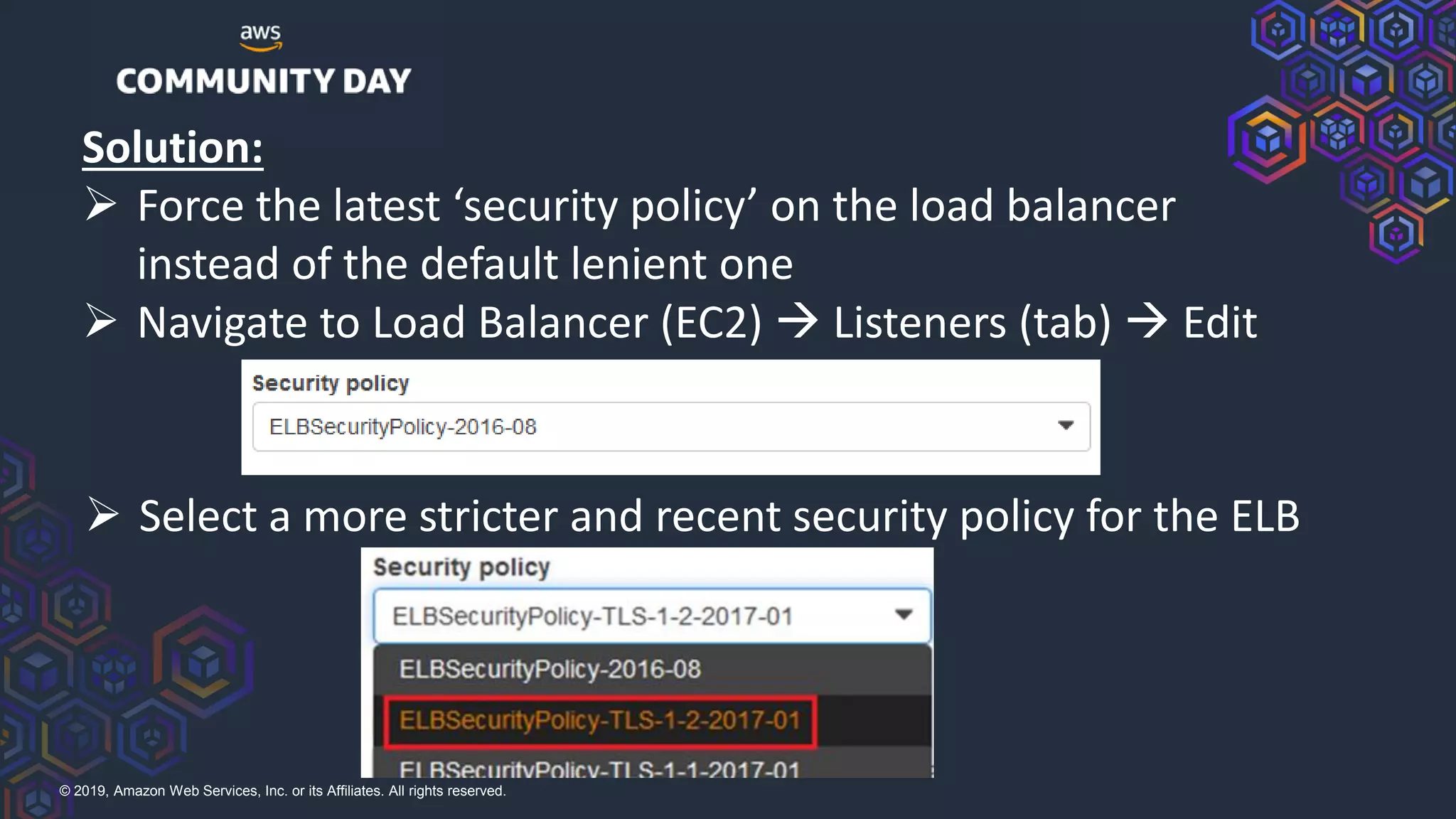
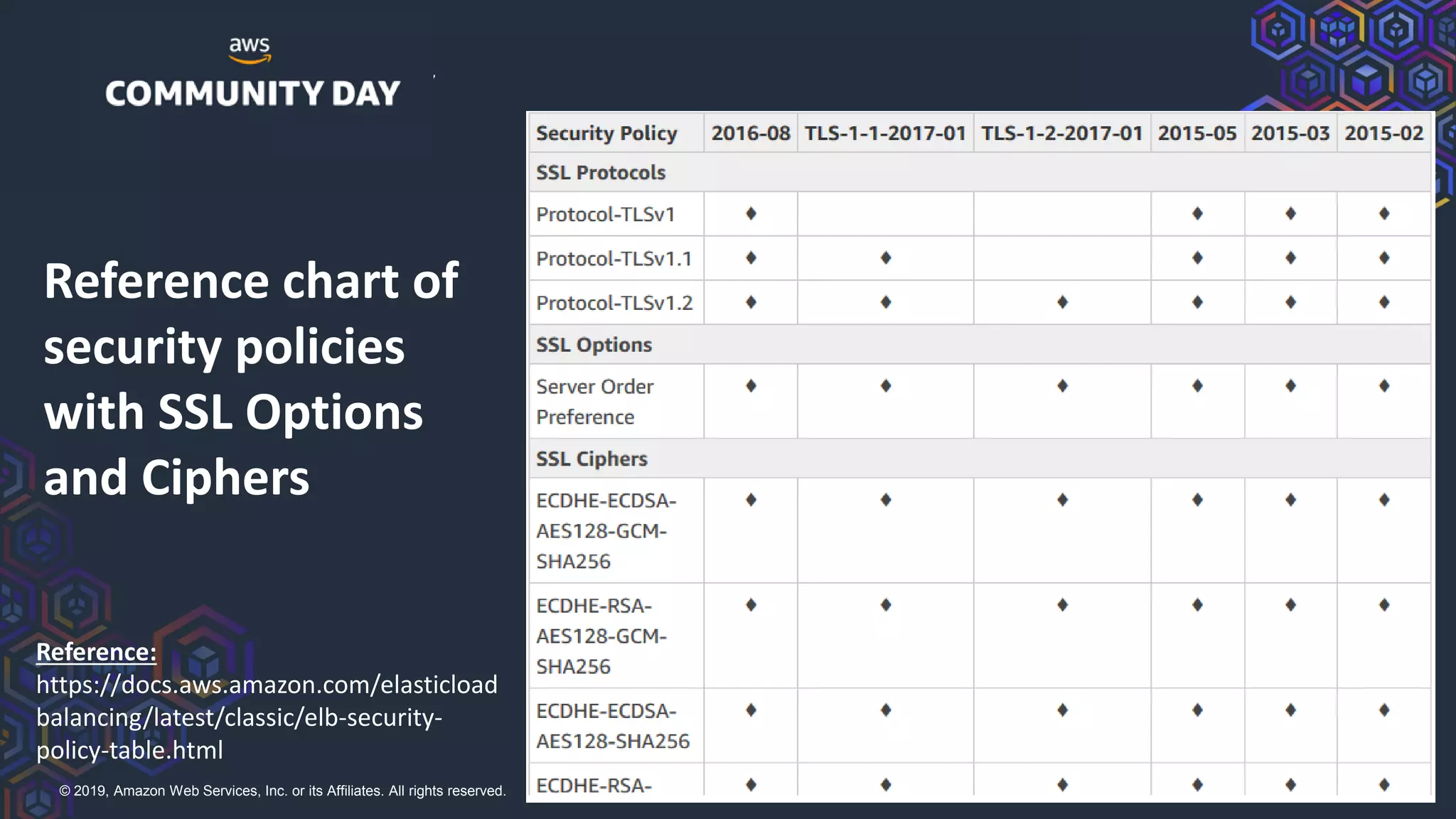
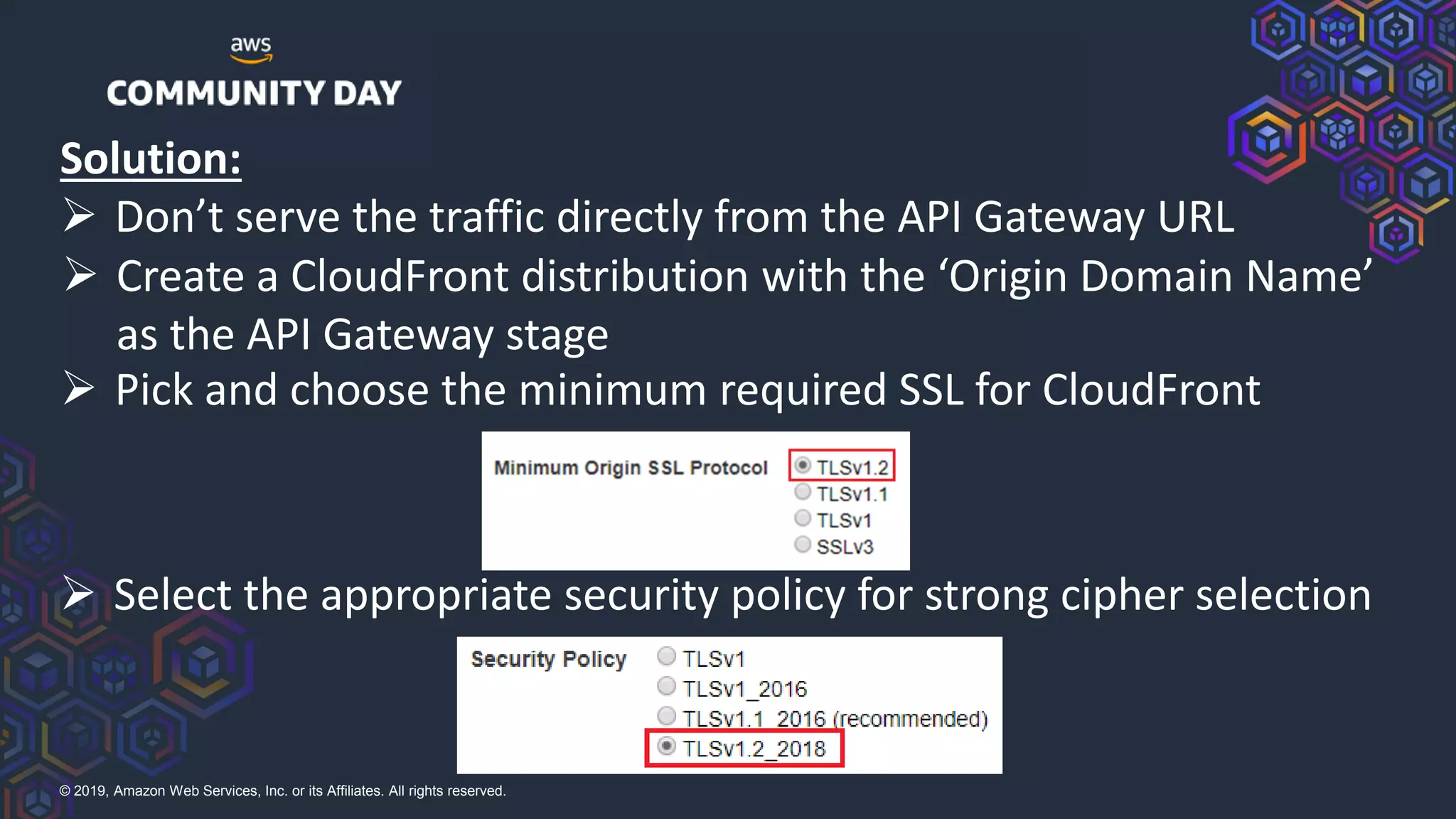
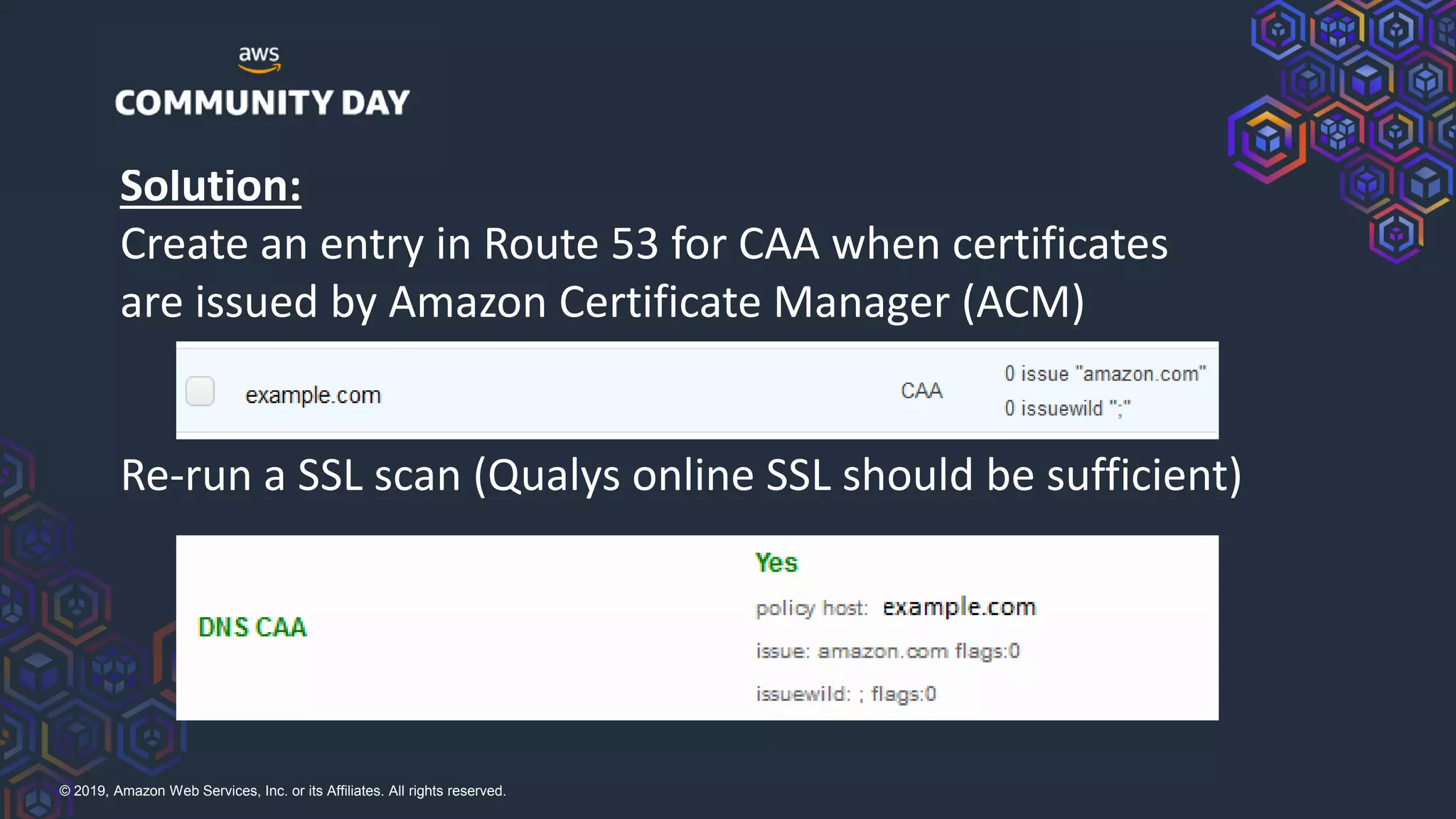
The document discusses security hardening of core AWS services. It identifies weaknesses in the default configurations of Amazon Linux, Elastic Load Balancers, API Gateway, and Certificate Manager. It provides solutions such as upgrading OpenSSH, configuring stronger cipher suites and TLS versions, using CloudFront to front API Gateway, and adding CAA records for certificates. The document aims to help harden AWS services against common vulnerabilities and misconfigurations.