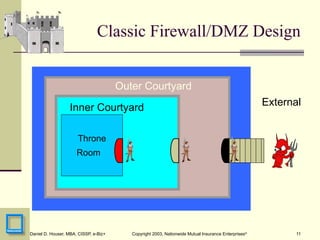
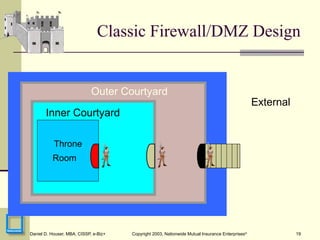
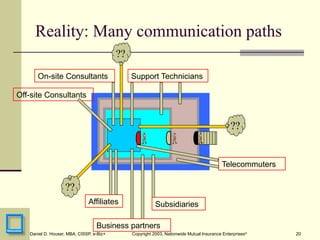
I wasn't nearly clever enough to call this concept Zero Trust, but this is some of that formative discussion early in the ZTA arc. I presented this at RSA 2003 and it was quite well received, and lead to the publication of an article, "Submarine Warfare" in InfoSecurity Magazine.