Next generation data protection and security for oracle users - gdpr blockchain and quantum
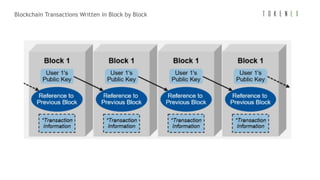
- 1. 1Source: Gartner Blockchain Transactions Written in Block by Block
- 2. 2 The Oracle Blockchain Solution Source: Oracle
- 3. 3Source: Oracle B l o c k c h a i n b a s e d o n O p e n S o u r c e
- 4. 4Source: Gartner Blockchain is NOT a Database
- 5. 5Source: Gartner B l o c k c h a i n S t r e n g t h s , We a k n e s s e s , O p p o r t u n i t i e s a n d T h r e a t s
- 6. 6Source: Gartner Many Challenges to Widespread Blockchain Adoption
- 7. 7 Blockchain is decentralized Blockchain Security – What keeps your transaction data safe?
- 8. 8 Blockchain offers encryption and validation Blockchain Security – What keeps your transaction data safe?
- 9. 9 Blockchain is virtually impossible to hack Blockchain Security – What keeps your transaction data safe?
- 10. 10 Blockchains can be private or public Blockchain Security – What keeps your transaction data safe?
- 11. 11 Blockchain is decentralized Source: IBM Blockchain Security – What keeps your transaction data safe?
- 12. 12 Blockchain is virtually impossible to hack Source: IBM Blockchain Security – What keeps your transaction data safe?
- 13. 13Source: Gartner B l o c k c h a i n O p p o r t u n i t y a n d R i s k - B o a r d - L e v e l O p i n i o n s
- 14. 14Source: Gartner Blockchain Business Projections
- 15. 15 Oracle Customer Quotes Source: IDC and Oracle 30 % Productivity Gain in Documentation in Shipping Industry Global Food Safety and Quality
- 16. 16 Oracle Customer Quotes Source: IDC and Oracle Minimize Cost and Complexity in Electronic Fund Transfers in Investment Banking Customer Advantage to Trace Products Across Entire Supply Chain
- 17. 17Source: Gartner Example - Bitcoin Transactions
- 18. 18Source: Gartner How Could Blockchain Be Important to Your Supply Chain?
- 19. 19Source: Gartner Example – a Manufacturer Send a Product to a Distributor
- 20. 20 Blockchain Industry Examples Source: IDC 1. In financial services, direct connections to shared ledgers can help consolidate internal and external data in secure ledgers. Improving data quality helps improve compliance programs such as know your customer (KYC) and new account onboarding. 2. In manufacturing, distributed ledgers can improve multiple data-intensive processes such as chain-of-custody record keeping and warranty compliance programs. 3. In retail supply chains, manufacturers and retailers are investing in DLT to improve their visibility in the flow of funds and chain of custody to help them fight fraud and reduce the flow of counterfeit goods. 4. In supply chain finance, market participants are looking at DLT to help improve profitability for all players by reducing the time it takes to complete reconciliation of records and issue the payment. 5. In healthcare, providers, regulators, and agencies are looking at DLT as a way to help in the delivery, management, and security of patient records and manage electronic health records (EHRs).
- 21. 21Source: Media E s t o n i a G o v e r n m e n t
- 22. 22Source: David Bentley T h e N e t h e r l a n d s N a t i o n a l B l o c k c h a i n A g e n d a
- 23. 23Source: Danish Minister for Industry D e n m a r k B l o c k c h a i n E U Pa r t n e r s h i p
- 24. 24Source: Oracle G e n e r a l D a t a P r o t e c t i o n R e g u l a t i o n ( G D P R )
- 25. 25Source: Oracle E u r o p e a n U n i o n G D P R Ai m
- 26. 26Source: Oracle G D P R M A I N B E N E F I T S
- 28. Encryption and Tokenization 28Source: GDRP framework Discover Data Assets Security by Design A GDPR FRAMEWORK - 5 KEY ACTIVITIES TO ADDRESS GDPR
- 29. Tokens Tokens PII Tokens Tokens • Protecting Personally Identifiable Information (PII), including names, addresses, phone, email, policy and account numbers • Compliance with EU Cross Border Data Protection Laws • Utilizing Data Tokenization, and centralized policy, key management, auditing, and reporting 29 29Source: International Customer Case Study PROTECT PII DATA CROSS BORDER - BEST PRACTICES Enterprise Data
- 30. Field Real Data Tokenized / Pseudonymized Name Joe Smith csu wusoj Address 100 Main Street, Pleasantville, CA 476 srta coetse, cysieondusbak, CA Date of Birth 12/25/1966 01/02/1966 Telephone 760-278-3389 760-389-2289 E-Mail Address joe.smith@surferdude.org eoe.nwuer@beusorpdqo.org SSN 076-39-2778 076-28-3390 CC Number 3678 2289 3907 3378 3846 2290 3371 3378 Business URL www.surferdude.com www.sheyinctao.com Fingerprint Encrypted Photo Encrypted X-Ray Encrypted Healthcare / Financial Services Dr. visits, prescriptions, hospital stays and discharges, clinical, billing, etc. Financial Services Consumer Products and activities Protection methods can be equally applied to the actual data, but not needed with de-identification 30Source: Customer Case Study DATA DE-IDENTIFICATION / ANONYMIZATION
- 31. *: Underlying sensitive value (USV) Source: ANSI X9 31 ANSI X9 - CURRENT TOKENIZATION STANDARD
- 32. • Format-preserving encryption (FPE) is useful in situations where fixed-format data, such as Primary account numbers Social Security numbers, must be protected. • FPE will limit changes to existing communication protocols, database schemata or application code. 32Source: Accredited Standards Committee ANSI X9 2018 ANSI X9 STANDARD FOR FORMAT PRESERVING ENCRYPTION
- 33. 33 33Source: Gartner ENCRYPTION & TOKENIZATION LEVELS
- 34. 34 34Source: Gartner Less Secure More Secure ENCRYPTION AND TOKENIZATION BEST PRACTICES
- 35. 35Source: Integrigy Corporation I n t e g r i g y D a t a P r o t e c t i o n P r o c e s s
- 36. 36Source: Integrigy Corporation W h e r e S e n s i t i ve D a t a m i g h t b e
- 37. 37Source: Integrity Ty p e s o f E n c r y p t i o n
- 38. 38Source: Integrity Ty p e s o f E n c r y p t i o n
- 39. 39Source: Integrity S t o r a g e / Ac c e s s O r a c l e E n c r y p t i o n S o l u t i o n s
- 40. 40Source: Integrity W h a t i s O ra c l e T D E ?
- 41. 41Source: Integrity Ta b l e s p a c e E n c r y p t i o n
- 42. 42Source: Integrity T h i r d - Pa r t y E n c r y p t i o n E x a m p l e - Tra n s p a r e n t T h a l e s Vo r m e t r i c
- 43. 43 P u b l i c A d m i n i s t r a t i o n Source: Verizon 2018 Data Breach Investigations Report
- 44. 44 F i n a n c i a l a n d I n s u r a n c e Source: Verizon 2018 Data Breach Investigations Report
- 45. 45 M a n u f a c t u r i n g Source: Verizon 2018 Data Breach Investigations Report
- 46. 46 I n f o r m a t i o n Source: Verizon 2018 Data Breach Investigations Report
- 47. 47 R e t a i l Source: Verizon 2018 Data Breach Investigations Report
- 48. 48 P r o f e s s i o n a l , Te c h n i c a l a n d S c i e n t i f i c S e r v i c e s Source: Verizon 2018 Data Breach Investigations Report
- 49. 49 H e a l t h c a r e Source: Verizon 2018 Data Breach Investigations Report
- 50. 50Source: CEO of Vigitrust, Mathieu Gorge Re g u l a t i o n s Does blockchain, GDPR, Cloud, and IoT conflict with compliance regulations complicating your SEA? GDPR is not blockchain-compatible the way it is written today. Blockchain data can't be deleted. So will its applications be illegal? • There are ways for Blockchain applications to be compliant - data could be stored off-chain in distributed or cloud-based servers. Cloud considerations • From a storage and compliance perspective, they accumulate information about humans and our interaction with IoT devices. • One of the key questions asked how we make sure this is done in a correct and secure way; as well as how we make sure it is done in compliance with the new EU GDPR, because it’s going to be very hard to track everything.
- 51. 51 Impact on the Organization Source: IDC and Oracle
- 52. 52 IoT- Energy Management Solutions are Game-Changers
- 53. 53Source: iot-core Example – IoT Transactions, Cloud and Analytics
- 54. 54 54Source: Forrester 2017 BEST PRACTICE - FIND AND PROTECT YOUR SENSITIVE DATA
- 55. 55 ISO/IEC 27018 PII in Cloud ISO/IEC 27002 Security Controls ISO/IEC 27001 PII OnPrem ISO/IEC 27005 Risk Management ISO/IEC 29134 Privacy Impact ISO/IEC 17789 Cloud Architecture ISO/IEC 29101 Privacy by Design ISO/IEC 29100 Privacy for Cloud ISO/IEC 17788 Definitions ISO/IEC 27000 series – ITSEC Management ISO/IEC 27002 5 Information security policies 6 Organization of information security 7 Human resource security 8 Asset management 9 Access control 10 Cryptography 11 Physical and environmental security 12 Operations security 13 Communications security 14 System acquisition, development and maintenance 15 Supplier relationships 16 Information security incident management 17 Information security aspects of business continuity management 18 Compliance GDPR 12+ GDPR RELATED INTERNATIONAL STANDARDS & CLOUD
- 58. Safe Integration – Enterprise & Public Cloud Safe Integration 58
- 59. Protect Sensitive Cloud Data Internal Network Administrator Attacker Remote User Internal User Public Cloud Examples Each sensitive field is protected Each authorized field is in clear Cloud Gateway 59 Data Security Agents, including encryption, tokenization or masking of fields or files (at transit and rest) SecDevOps
- 60. Trust Risk Adjusted Computation – Location Awareness Elasticity Out-sourcedIn-house Corporate Network Private Cloud Private Cloud Public Cloud H L ProcessingCost H L 60
- 61. Virtual Machines & Containers Data Security Agents, including encryption, tokenization or masking of fields or files (at transit and rest) Source: GiacomoVacca/docker-from-scratch SecDevOps SecDevOps 61
- 62. OS File System Encryption User / Client Database Native Encryption User Access Patient Health Record x Read a xxx DBA Read b xxx z Write c xxx User Access Patient Health Record z Write c xxx User Acces s Patient Health Data Record Health Data File Database Process 0001 Read ? ? PHI002 Database Process 0001 Read ? ? PHI002 Database Process 0001 Write ? ? PHI002 Possible DBA manipulation Complete Log No Read Log No Information On User or Record 3rd Party Database Encryption PII/PHI/HIPAA Case Study: Granularity of Reporting and Separation of Duties Possible DBA manipulation : Security controls, Encryption services, 62
- 63. Time Total Cost of Ownership Total Cost of Ownership 1. System Integration 2. Performance Impact 3. Key Management 4. Policy Management 5. Reporting 6. Paper Handling 7. Compliance Audit 8. … Strong Encryption: 3DES, AES … I 2010 I 1970 Cost Of Encryption / Tokenization I 2005 I 2000 Format Preserving Encryption: FPE, DTP … Basic Tokenization Vaultless Tokenization High - Low - 63
- 64. Cloud Gateway - Requirements Adjusted Protection Data Protection Methods Scalability Storage Security Transparency System without data protection Weak Encryption (1:1 mapping) Searchable Gateway Index (IV) Vaultless Tokenization Partial Encryption Data Type Preservation Encryption Strong Encryption (AES CBC, IV) Best Worst 64
- 65. Tokenization vs. Encryption Used Approach Cipher System Code System Cryptographic algorithms Cryptographic keys Code books Index tokens Source: McGraw-HILL ENCYPLOPEDIA OF SCIENCE & TECHNOLOGY TokenizationEncryption 65
- 66. Positioning Different Protection Options Evaluation Criteria Strong Encryption Formatted Encryption Tokens Security & Compliance Total Cost of Ownership Use of Encoded Data Best Worst 66
- 67. Tokenization Server Location - EXAMPLE Best Worst Tokenization Server Location Evaluation Aspects Mainframe Remote Area Criteria DB2 Work Load Manager Separate Address Space In-house Out-sourced Operational Availability Latency Performance Security Separation Compliance 67
- 68. Worry Only About the Major Breach Patterns Source: Verizon Data Breach Investigations Report 68 Application Attacks
- 69. Data Security context Operating System Security Controls & Agents OS File System Database Application Framework Application Source Code Application Data Network External Network Internal Network Application Server 69 High - Low - Data Security Context
- 70. A SecDevOps Flow Static Application Security Testing (SAST) Dynamic Application Security Testing (DAST) Fuzz testing is essentially throwing lots of random garbage Vulnerabilit y Analysis Runtime Application Self Protection (RASP) Interactive Application Self-Testing (IAST) 70
- 71. Security Metrics from SECDevOps 71 # Vulnerabilities Time
- 72. 72Source: Integrigy Corporation Ab o u t I n t e g r i g y C o r p
- 73. 73Source: Oracle O r a c l e S e c u r i t y Ar c h i t e c t u r e F o r D a t a P r o t e c t i o n
- 74. 74Source: Oracle Au d i t , M o n i t o r a n d D e t e c t
- 75. 75Source: Oracle D e f e n s e - i n - D e p t h S e c u r i t y C o n t r o l s
- 76. 76Source: Oracle O r a c l e D a t a b a s e S e c u r i t y
