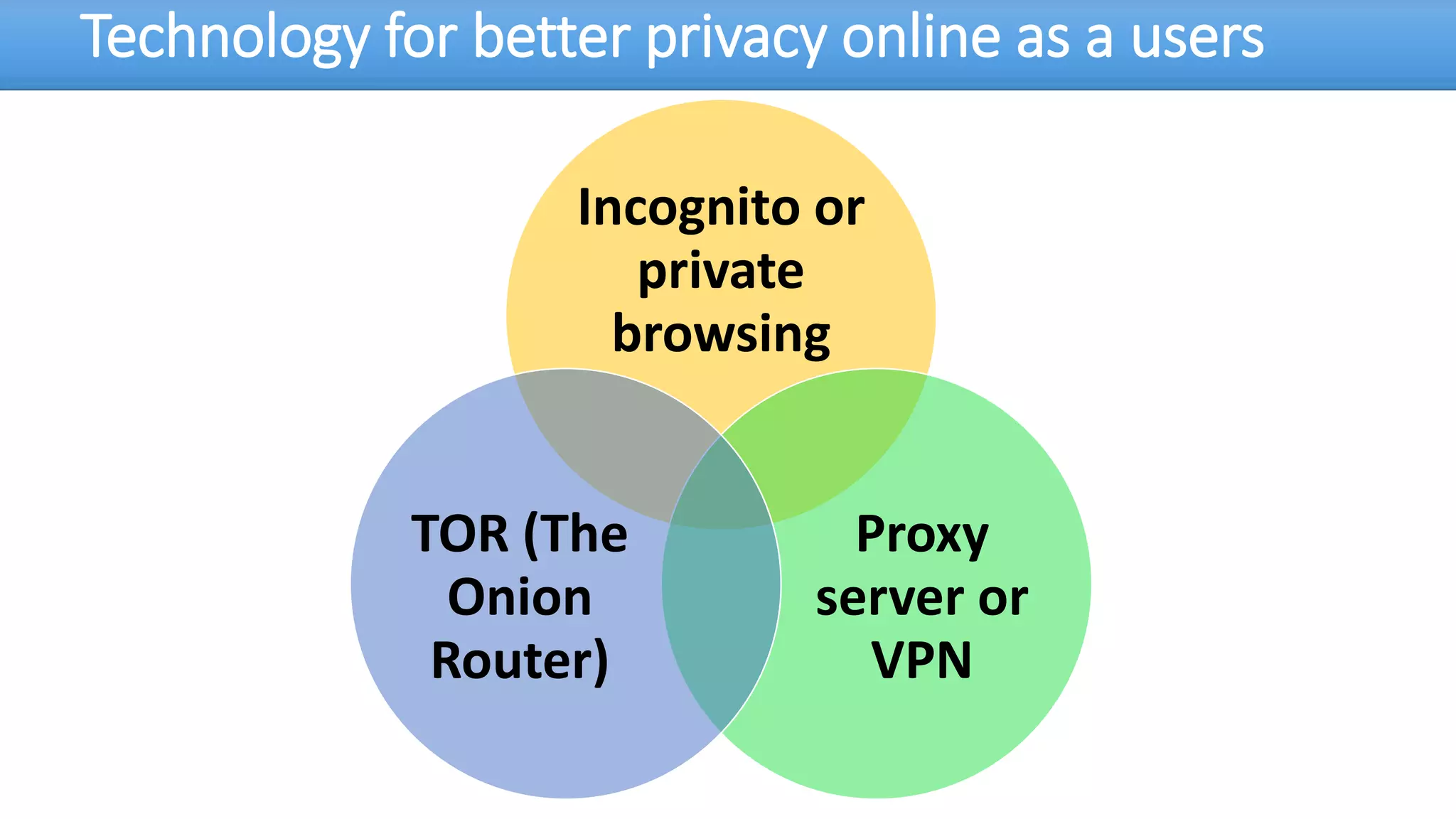
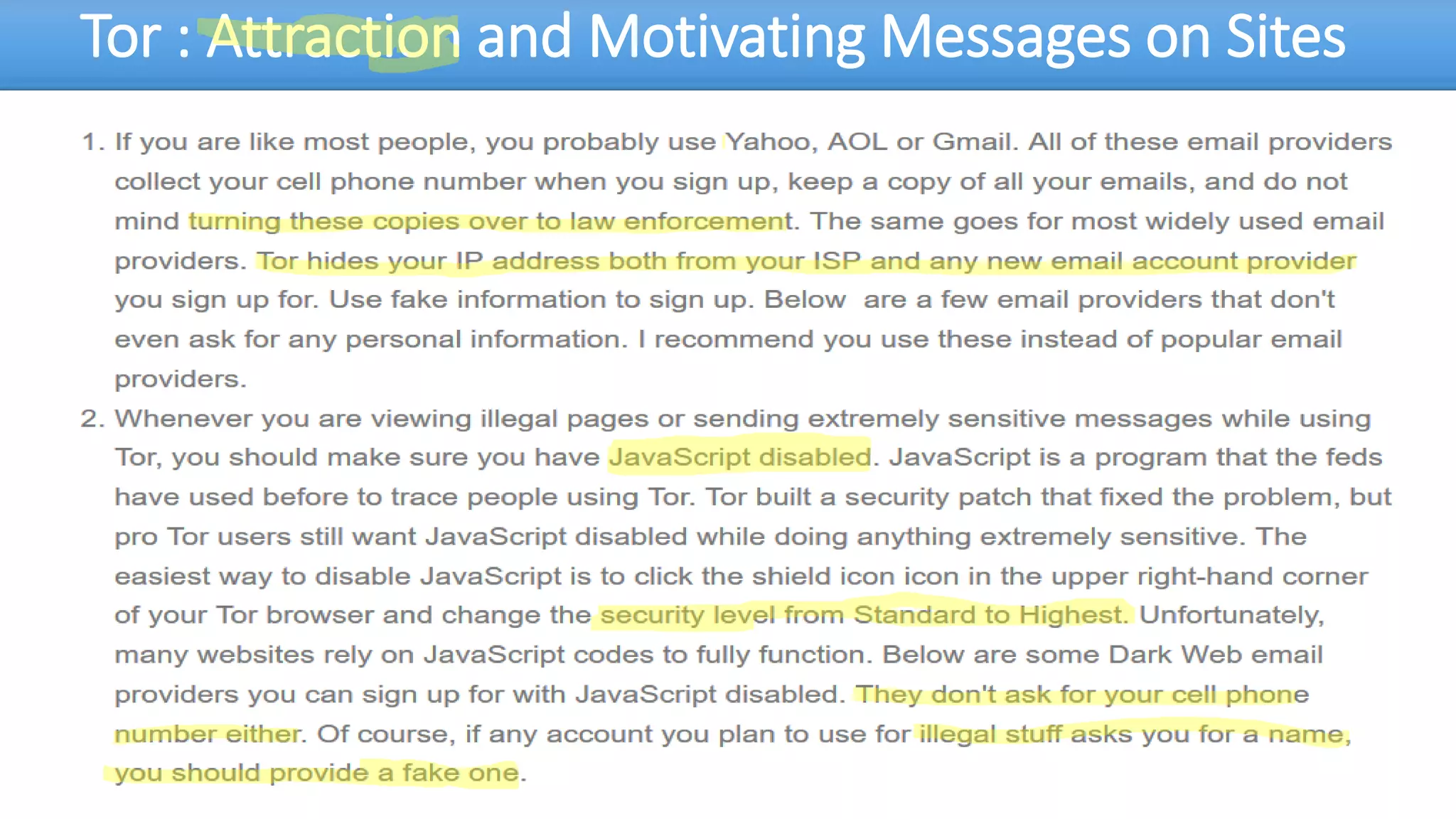
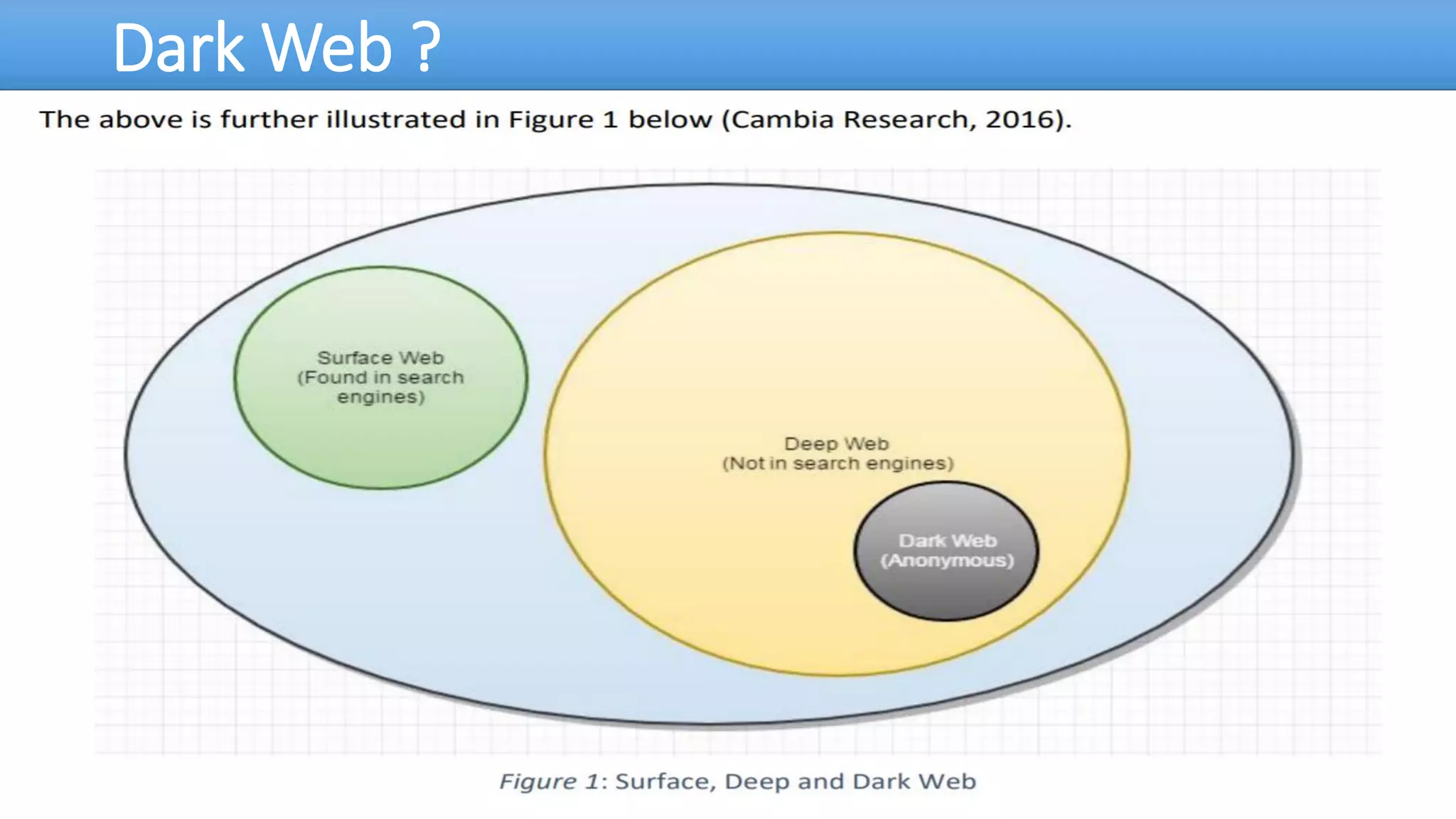
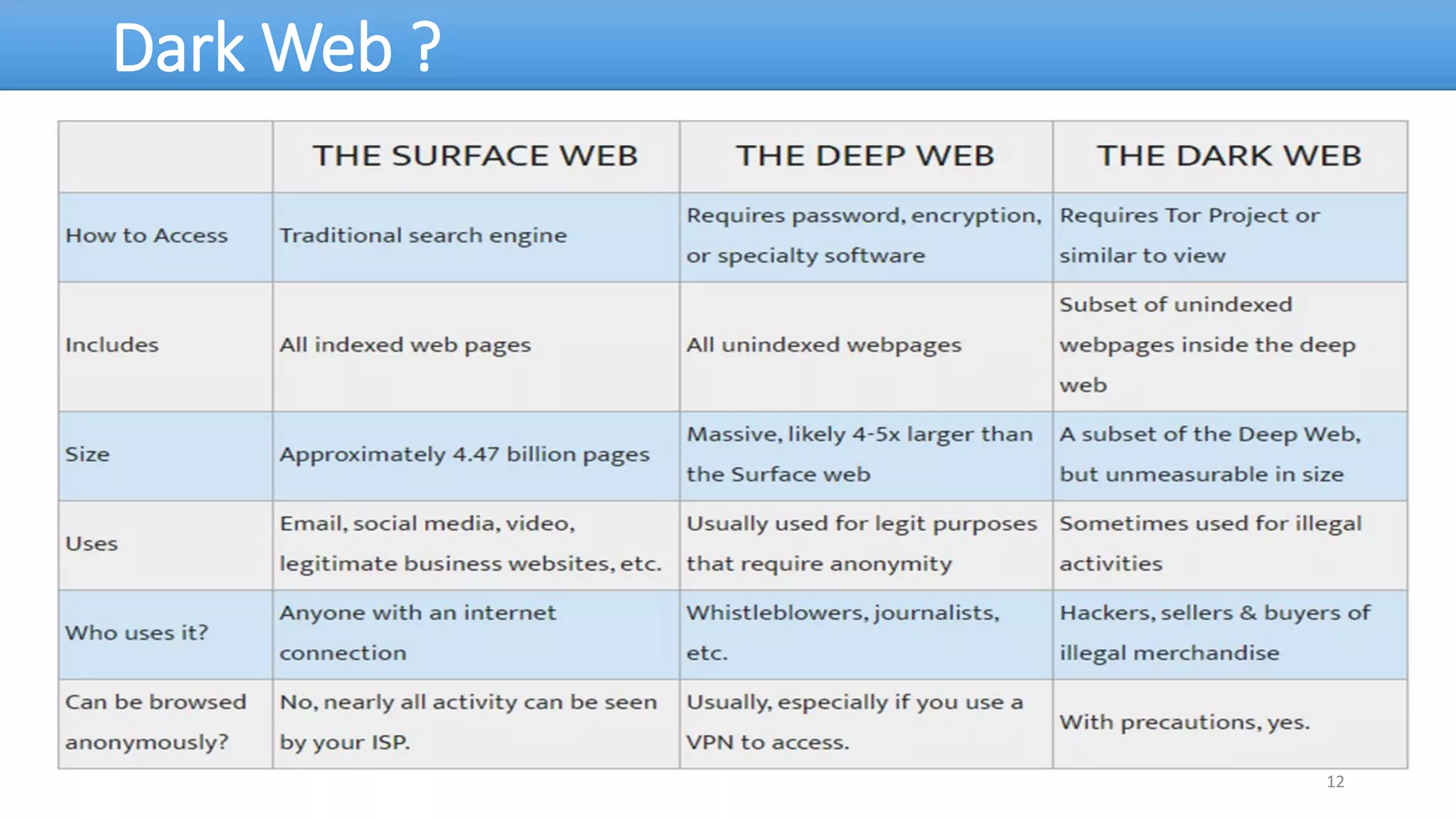
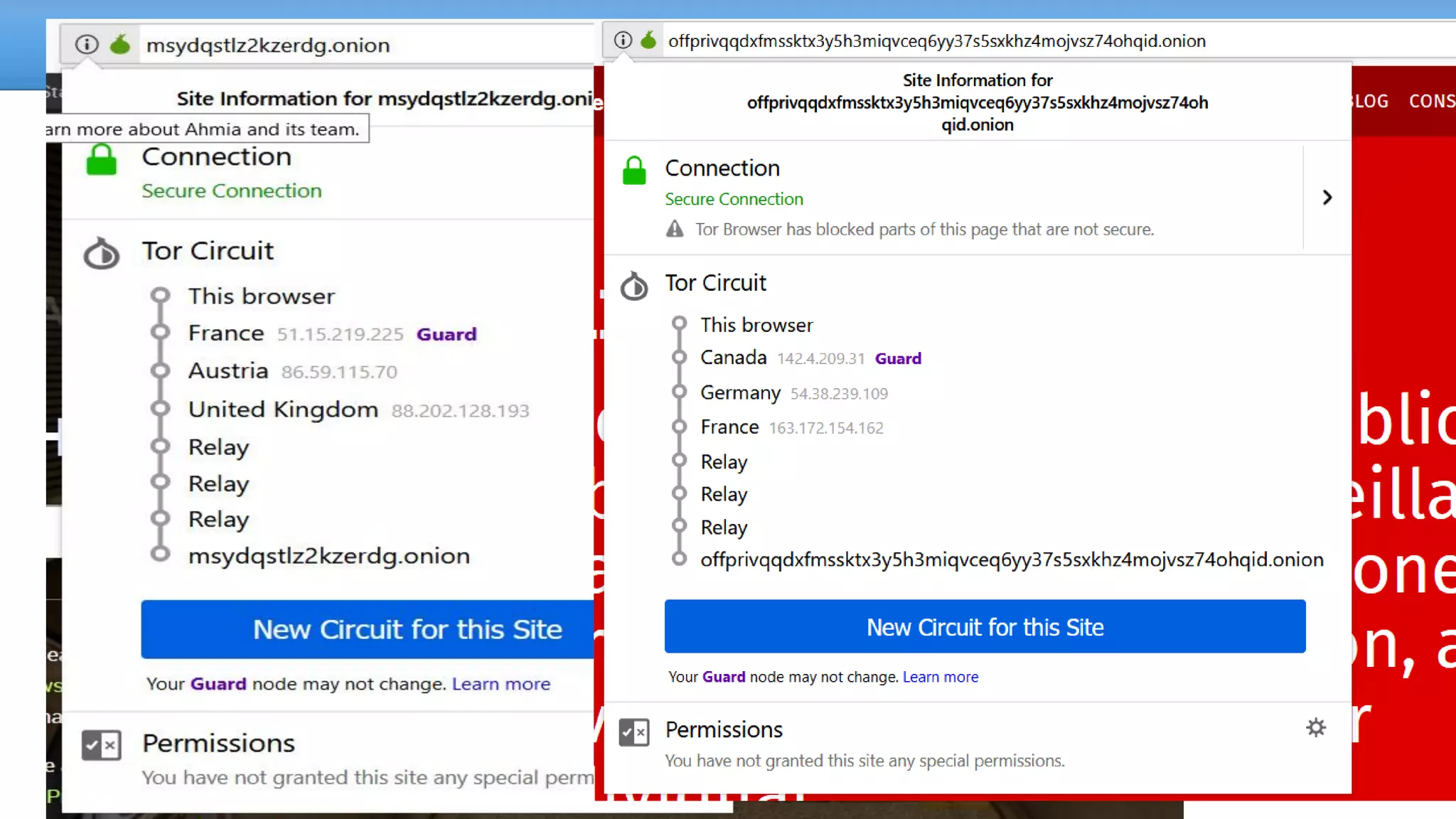
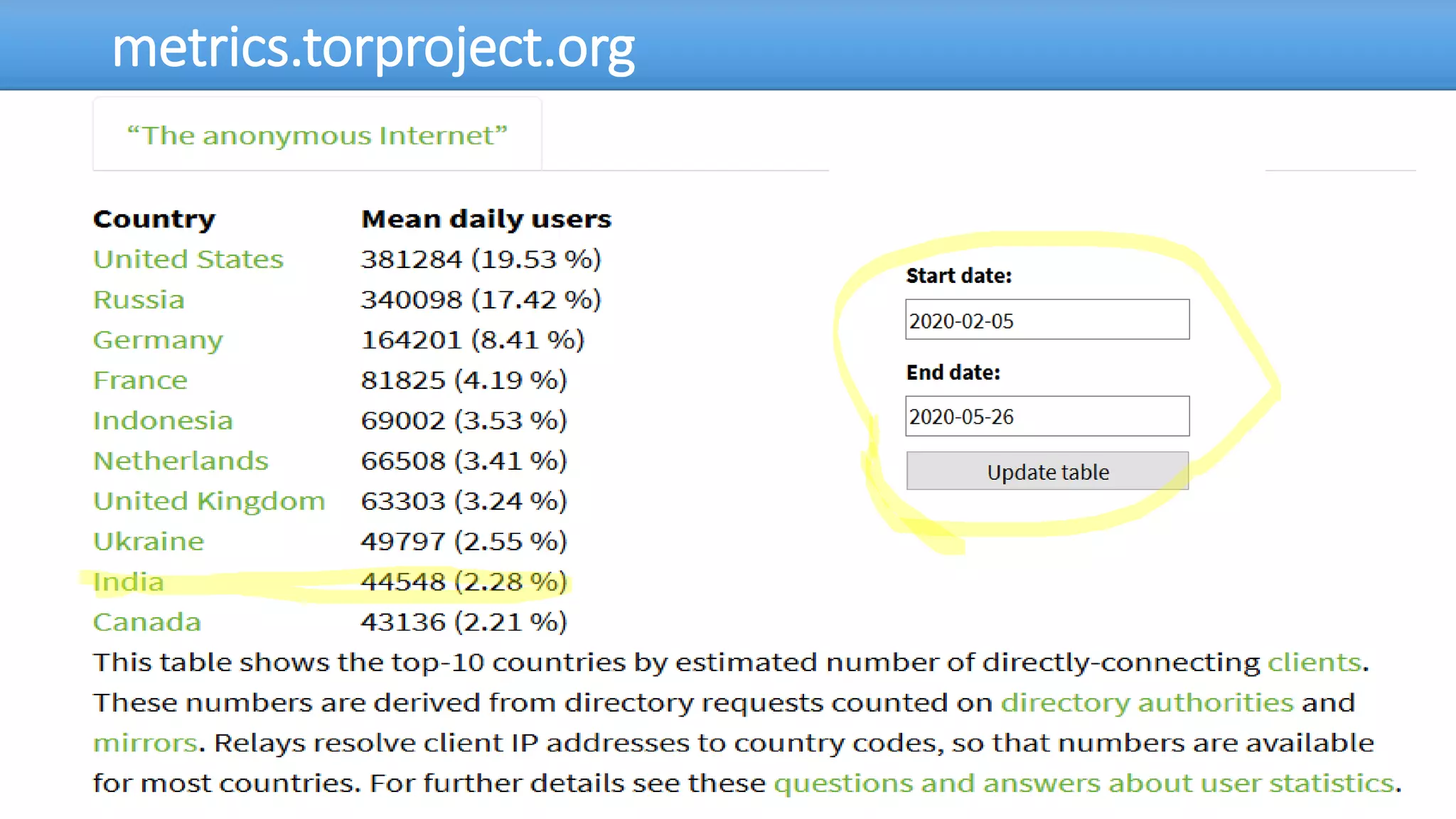
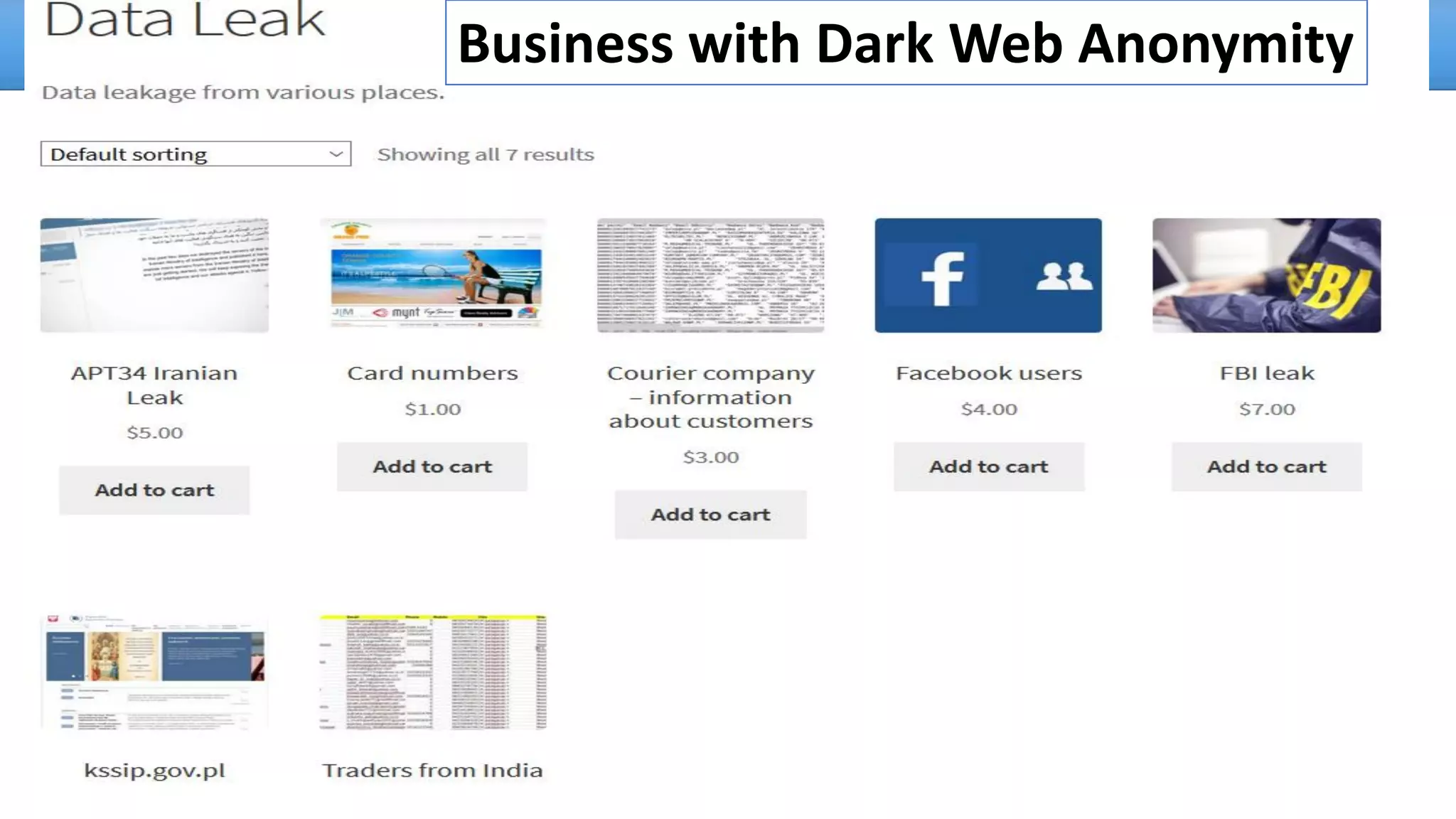
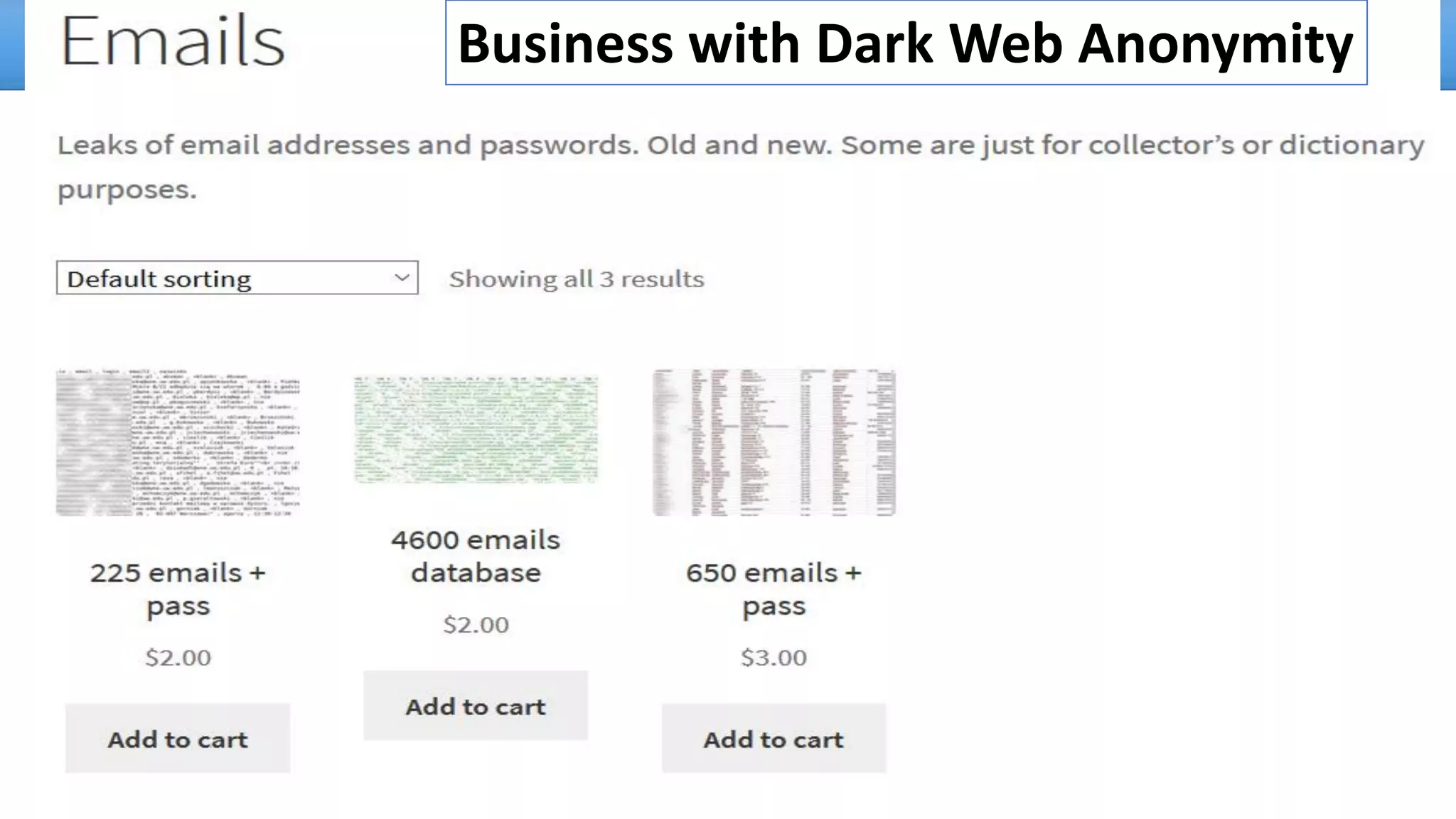
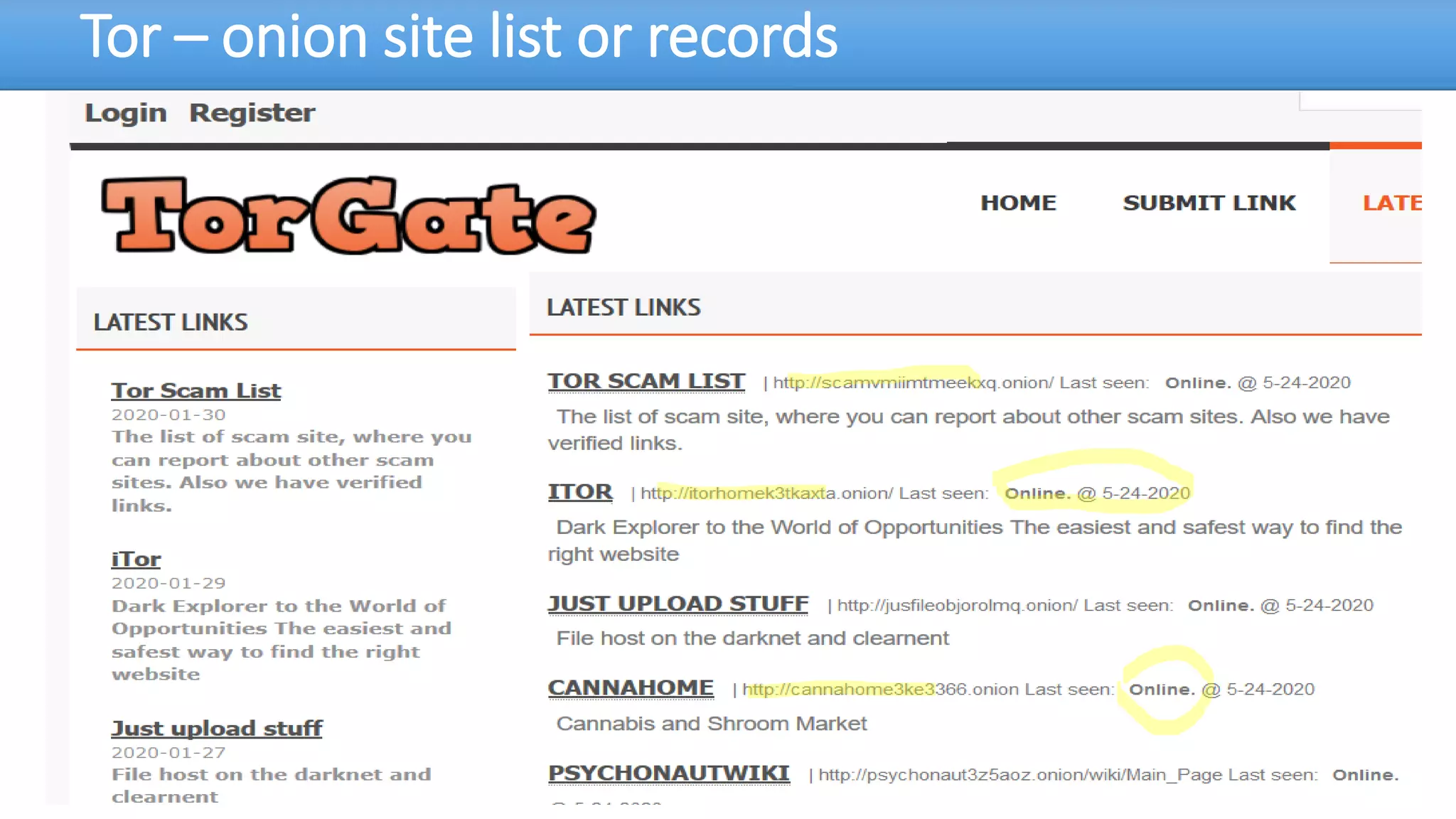
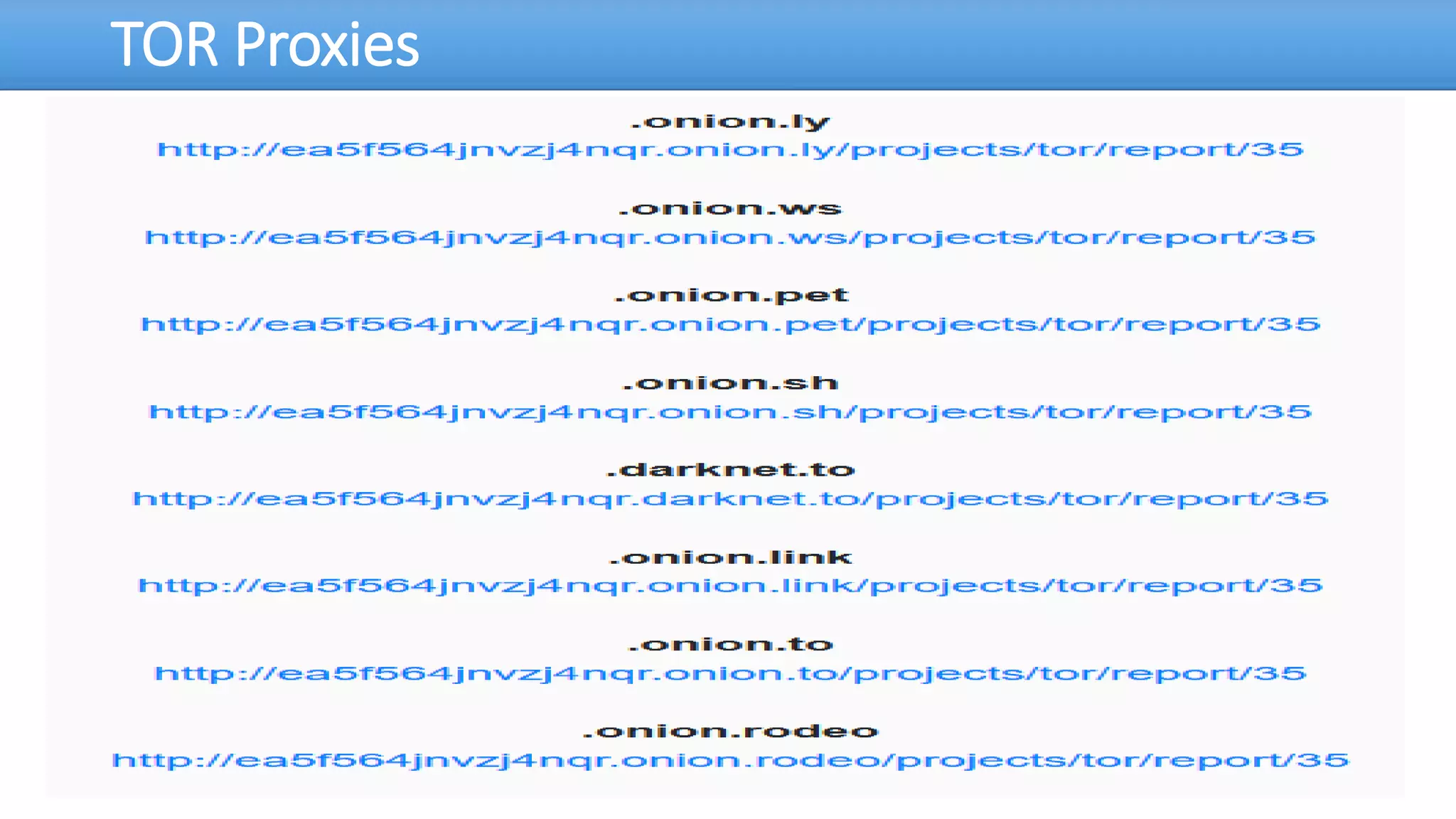
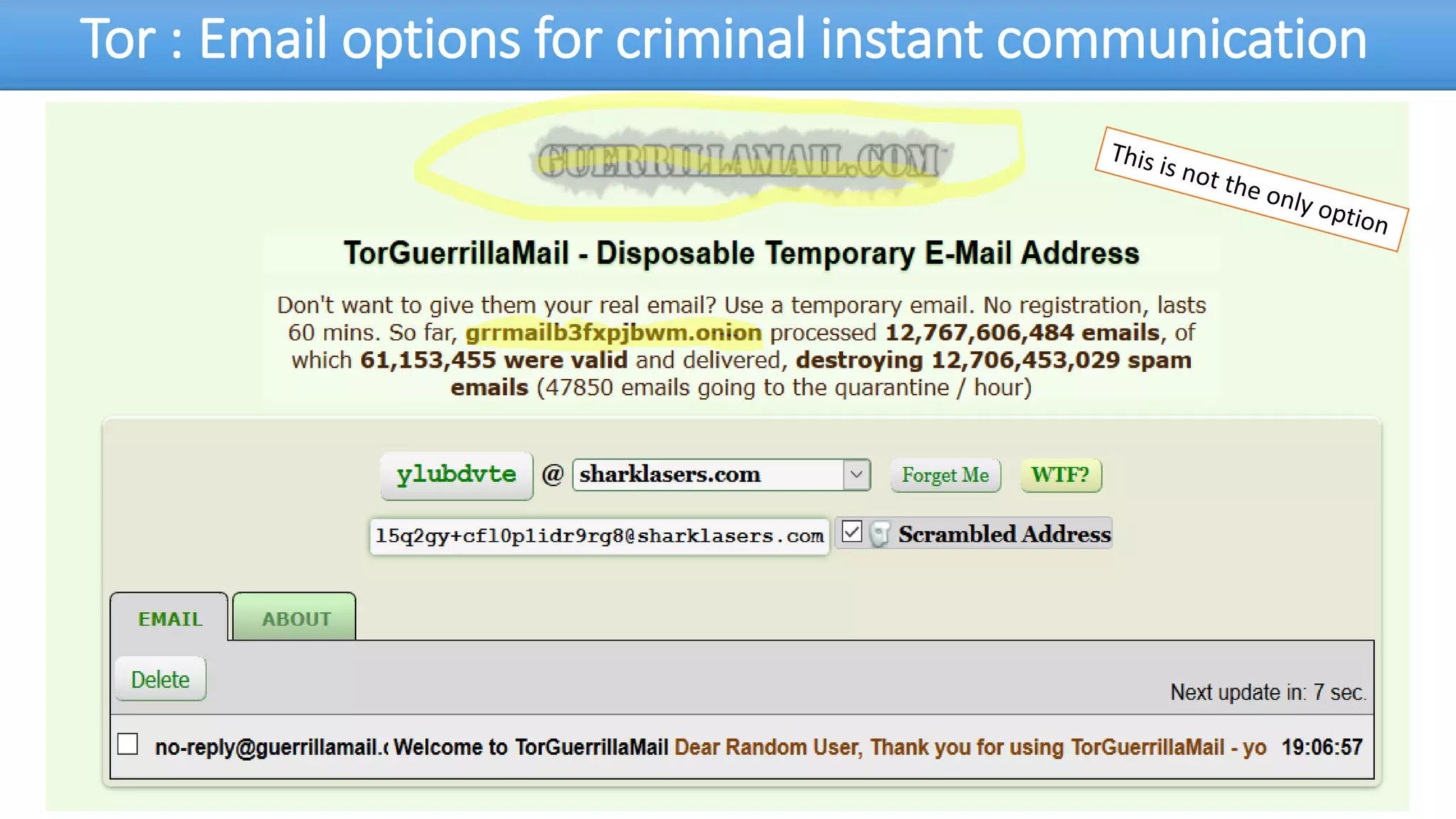
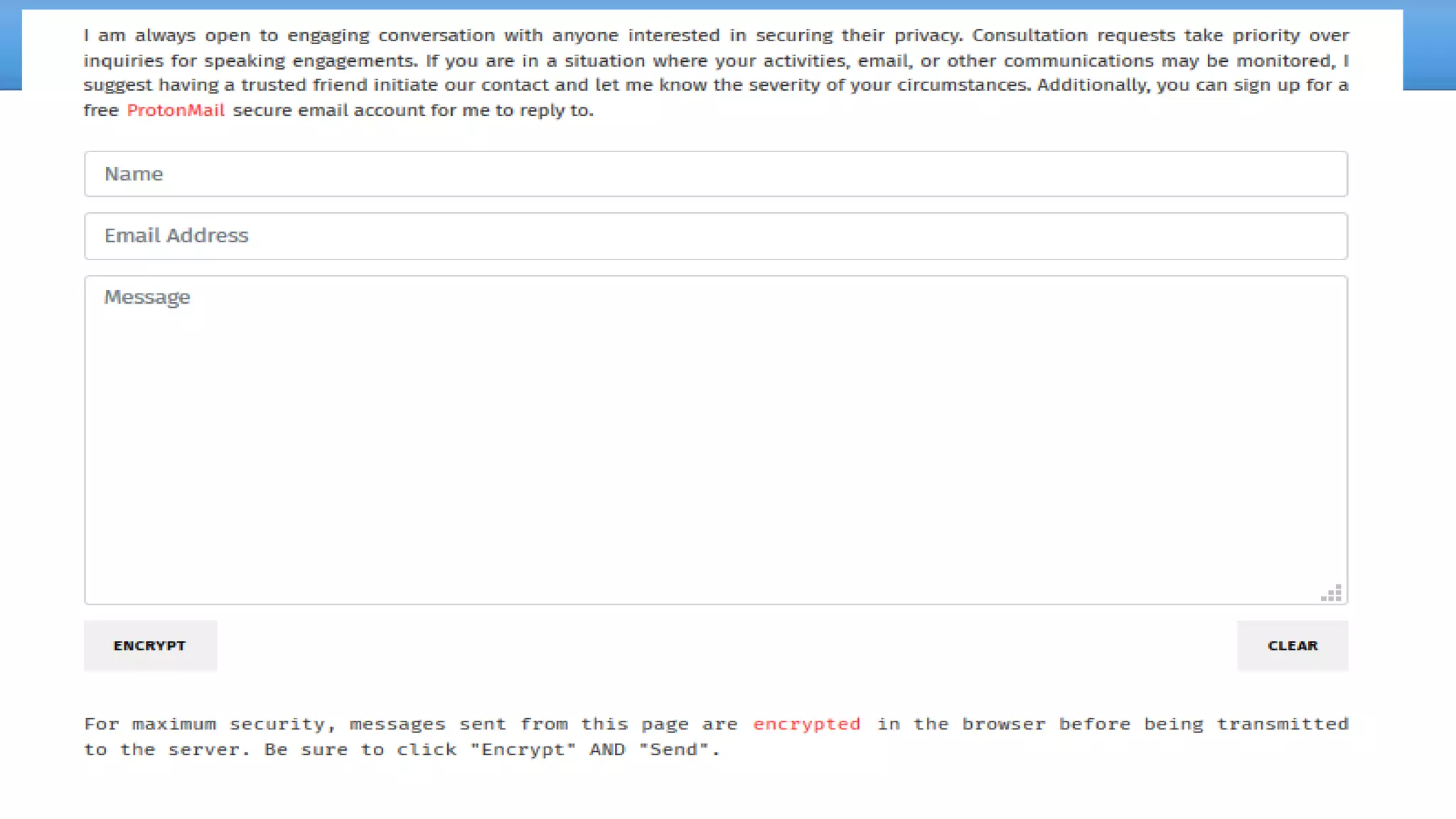
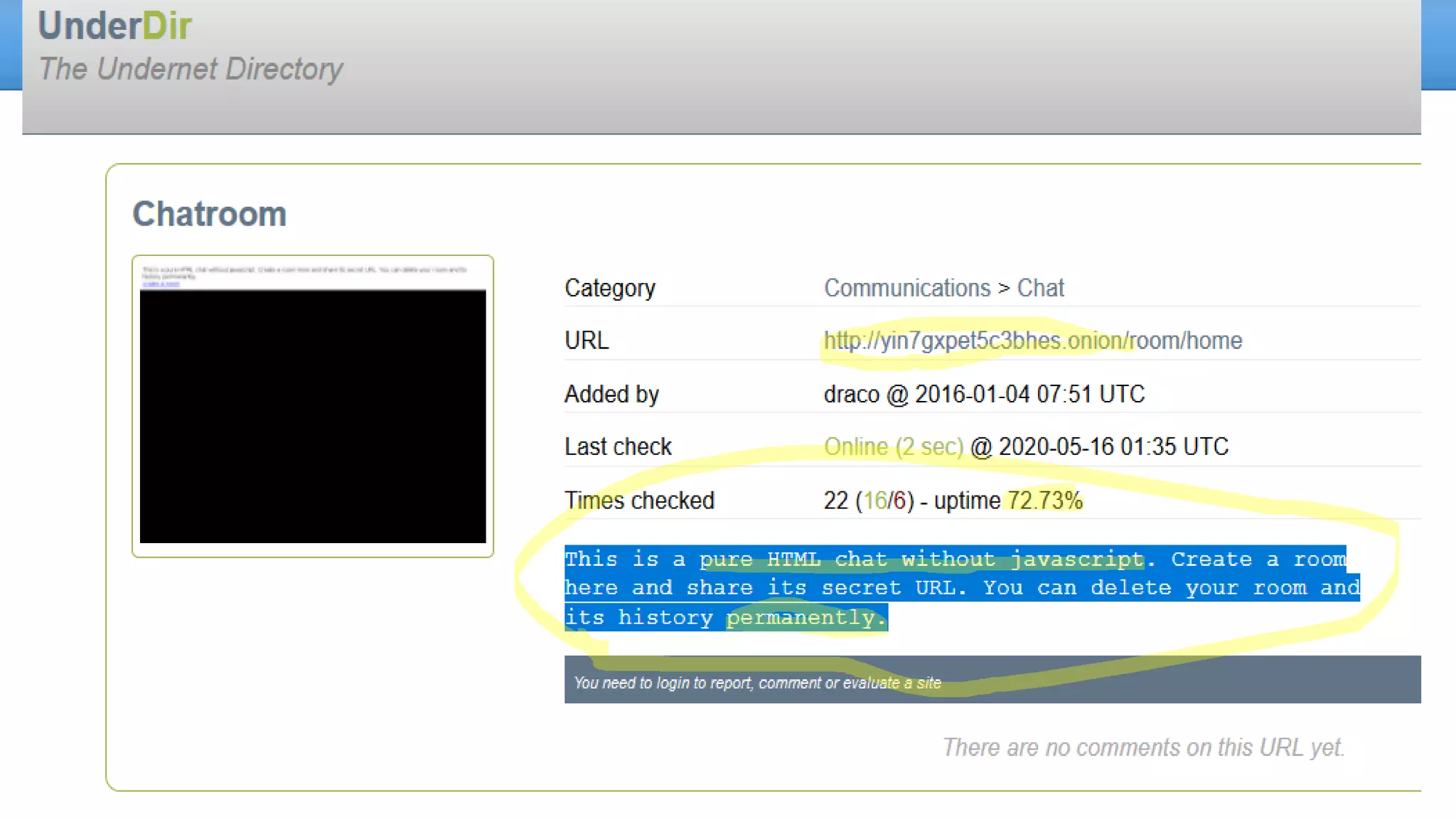
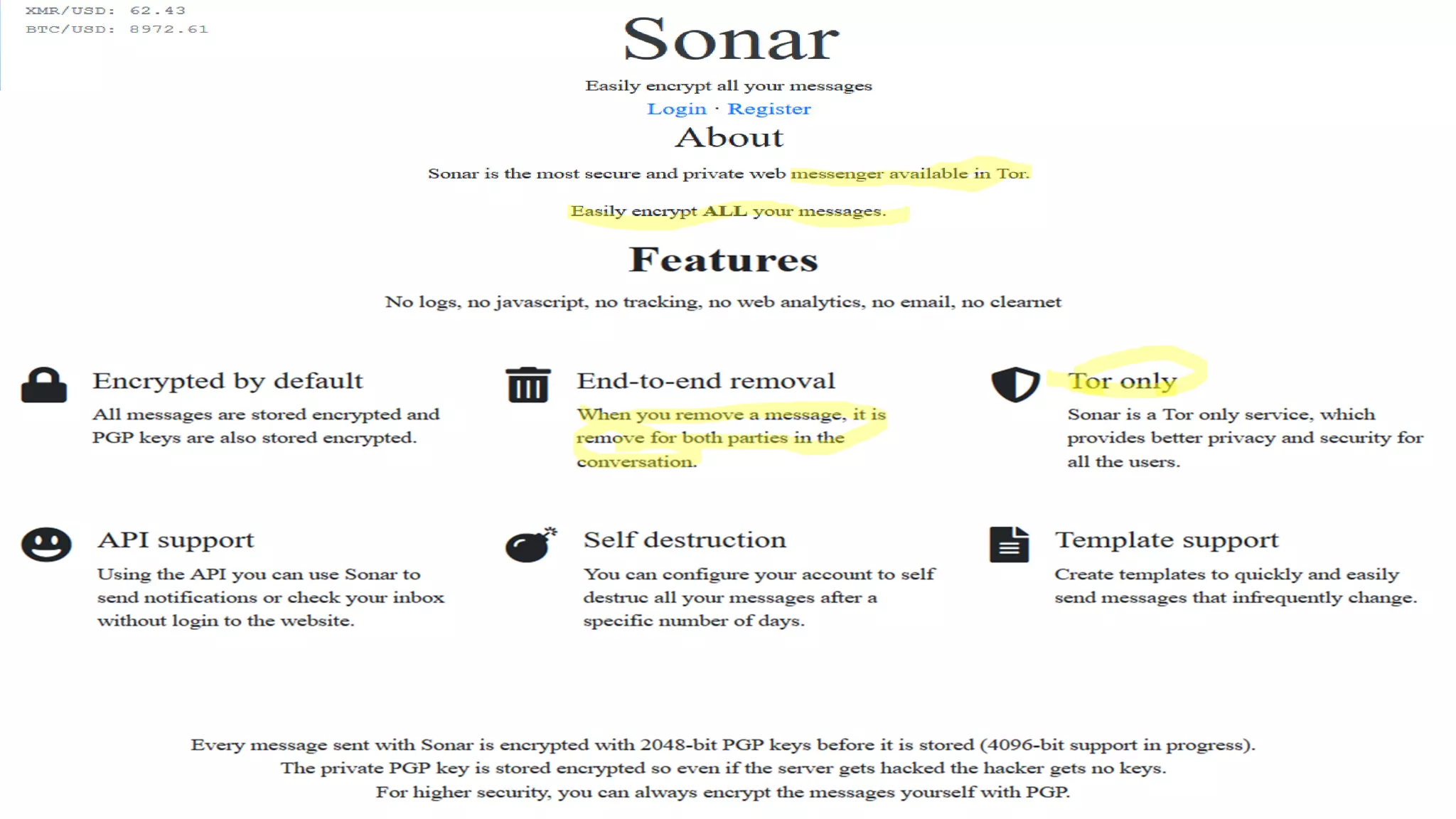
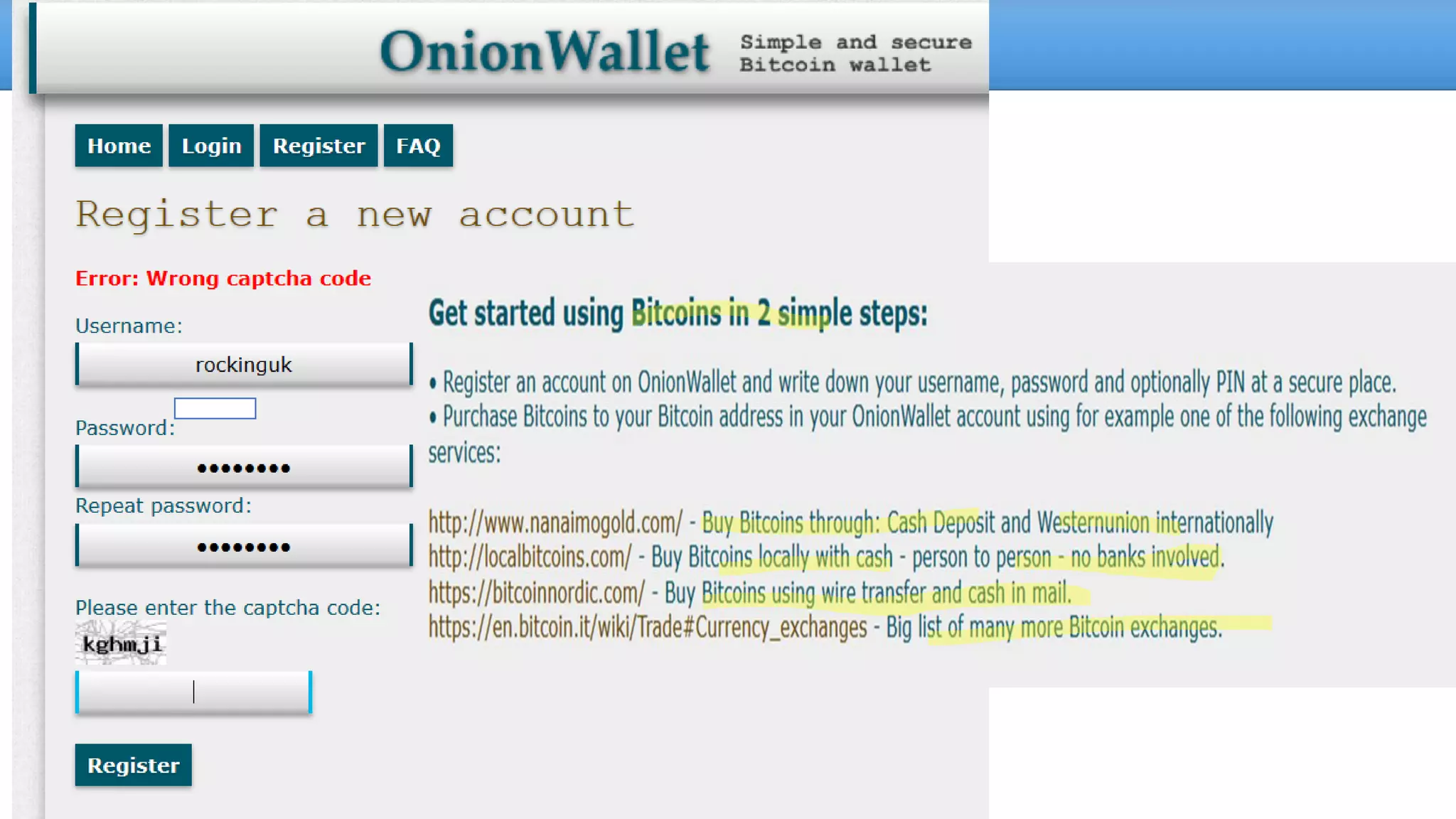
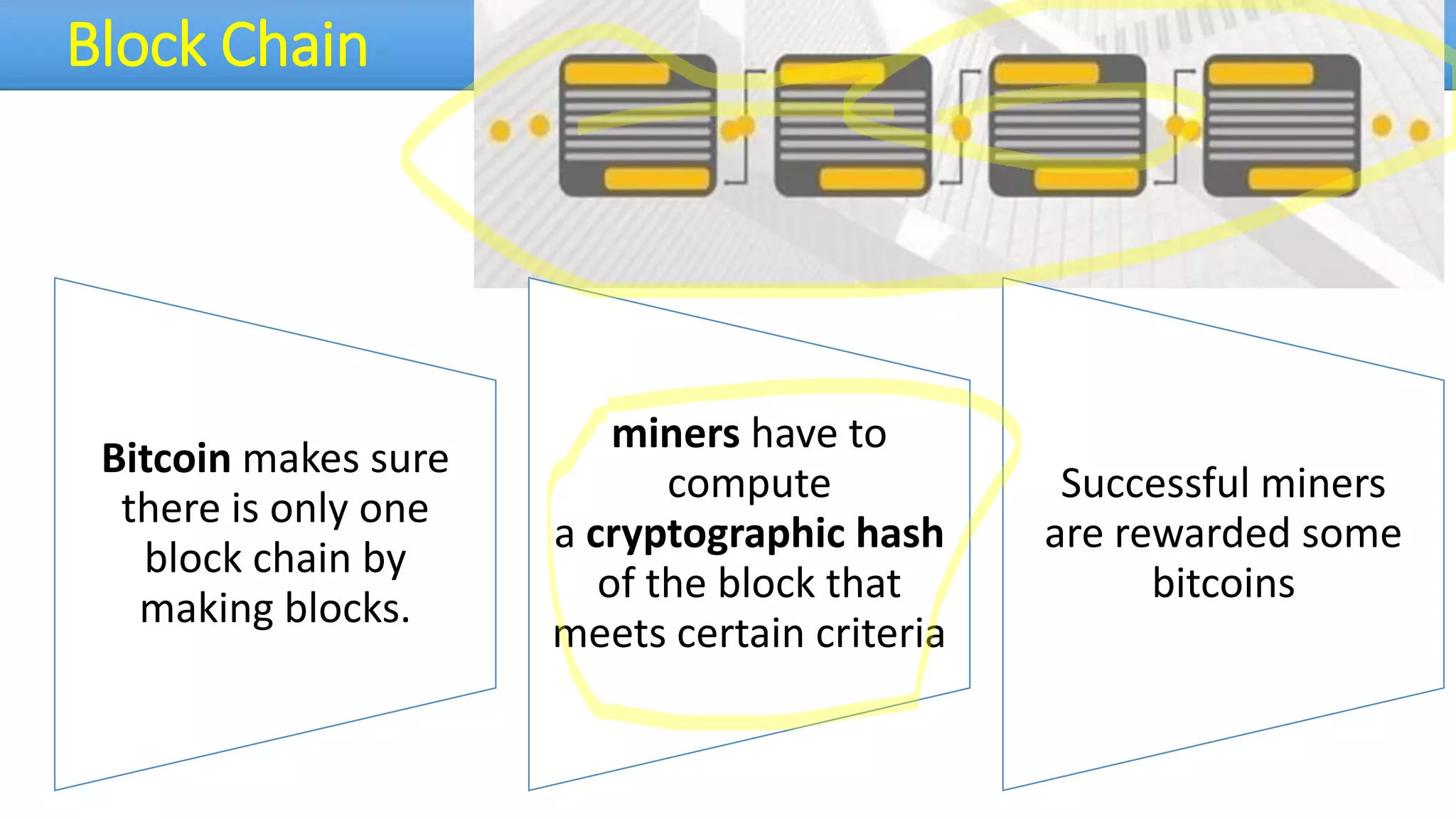
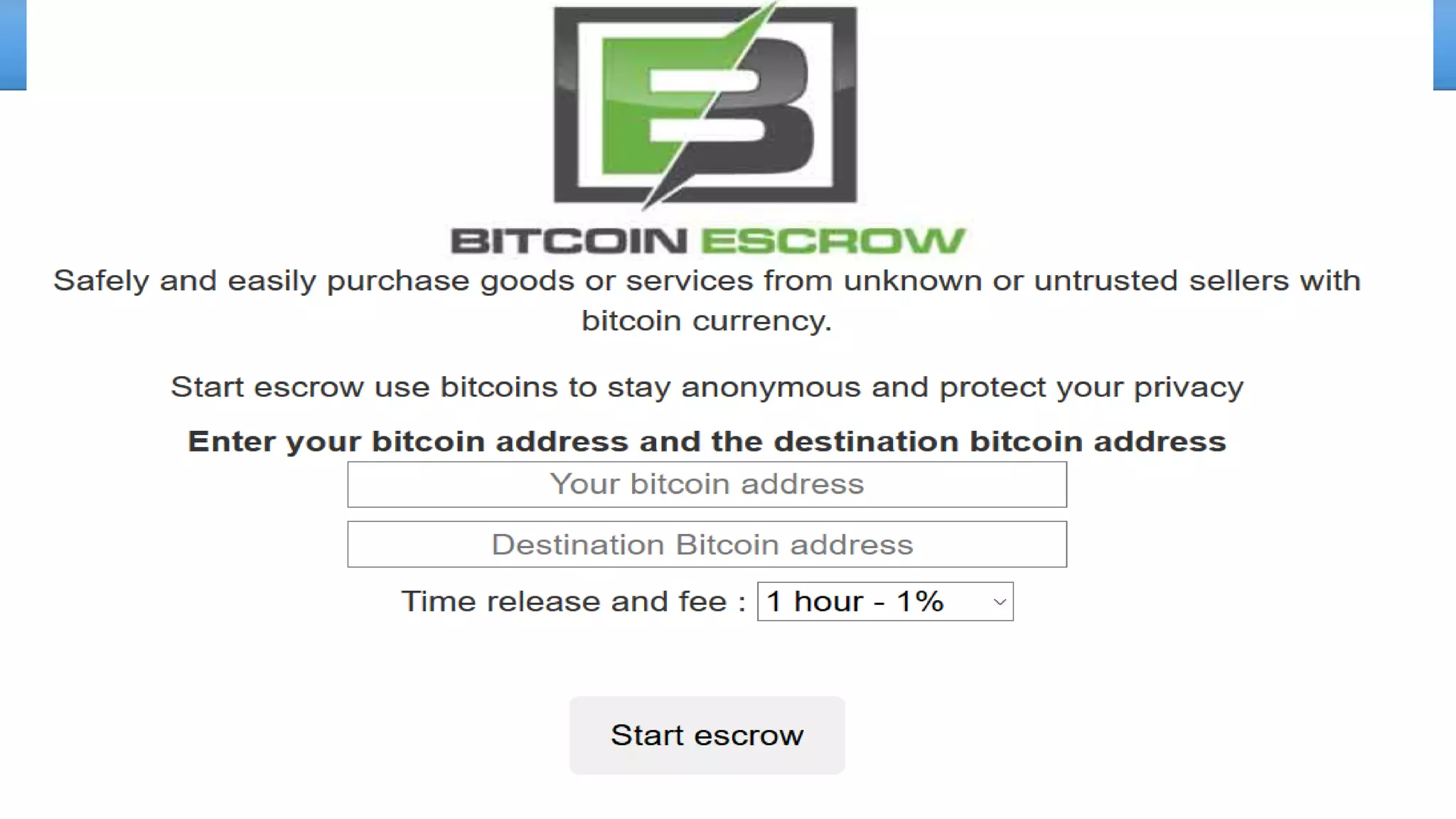
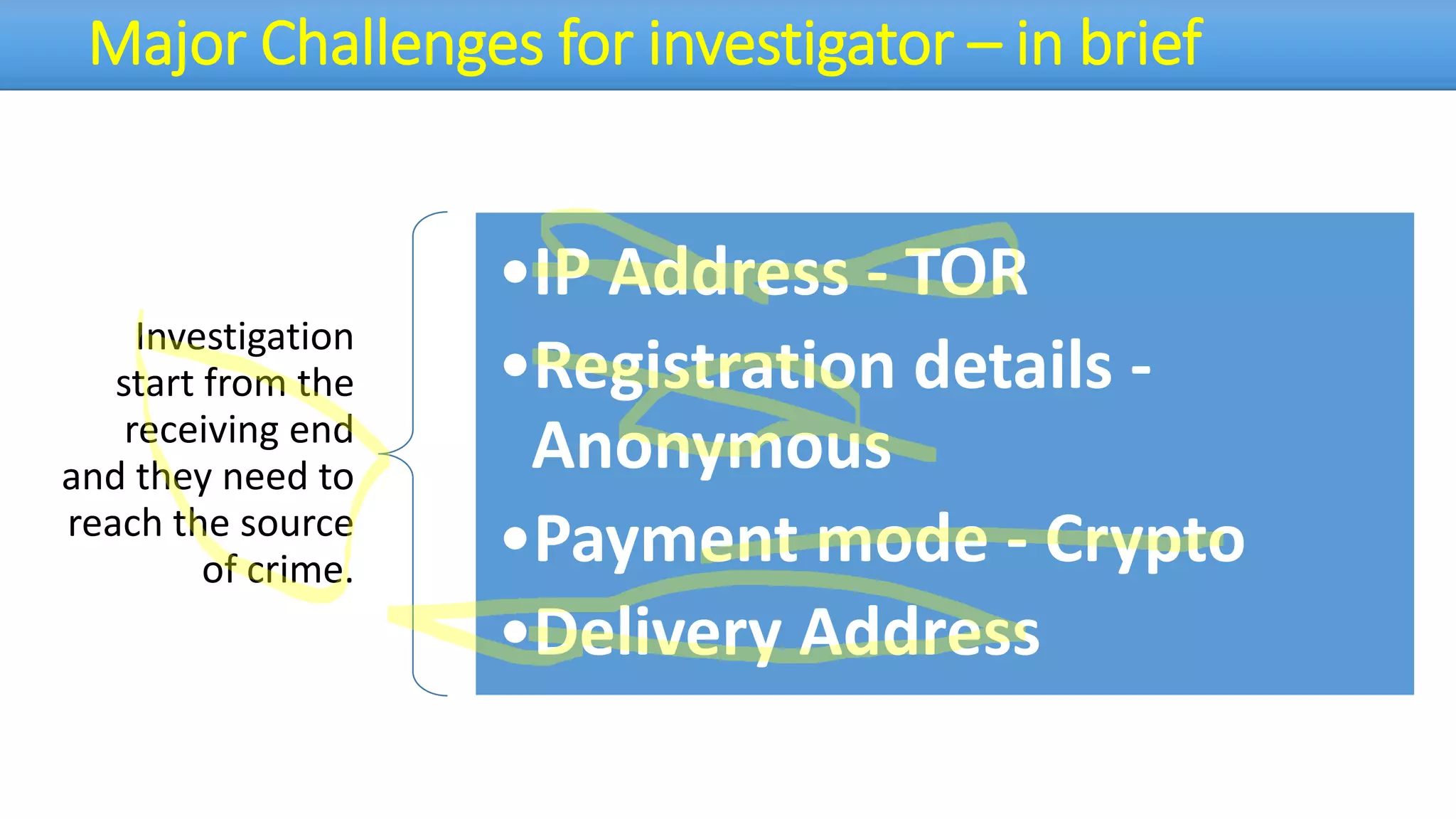
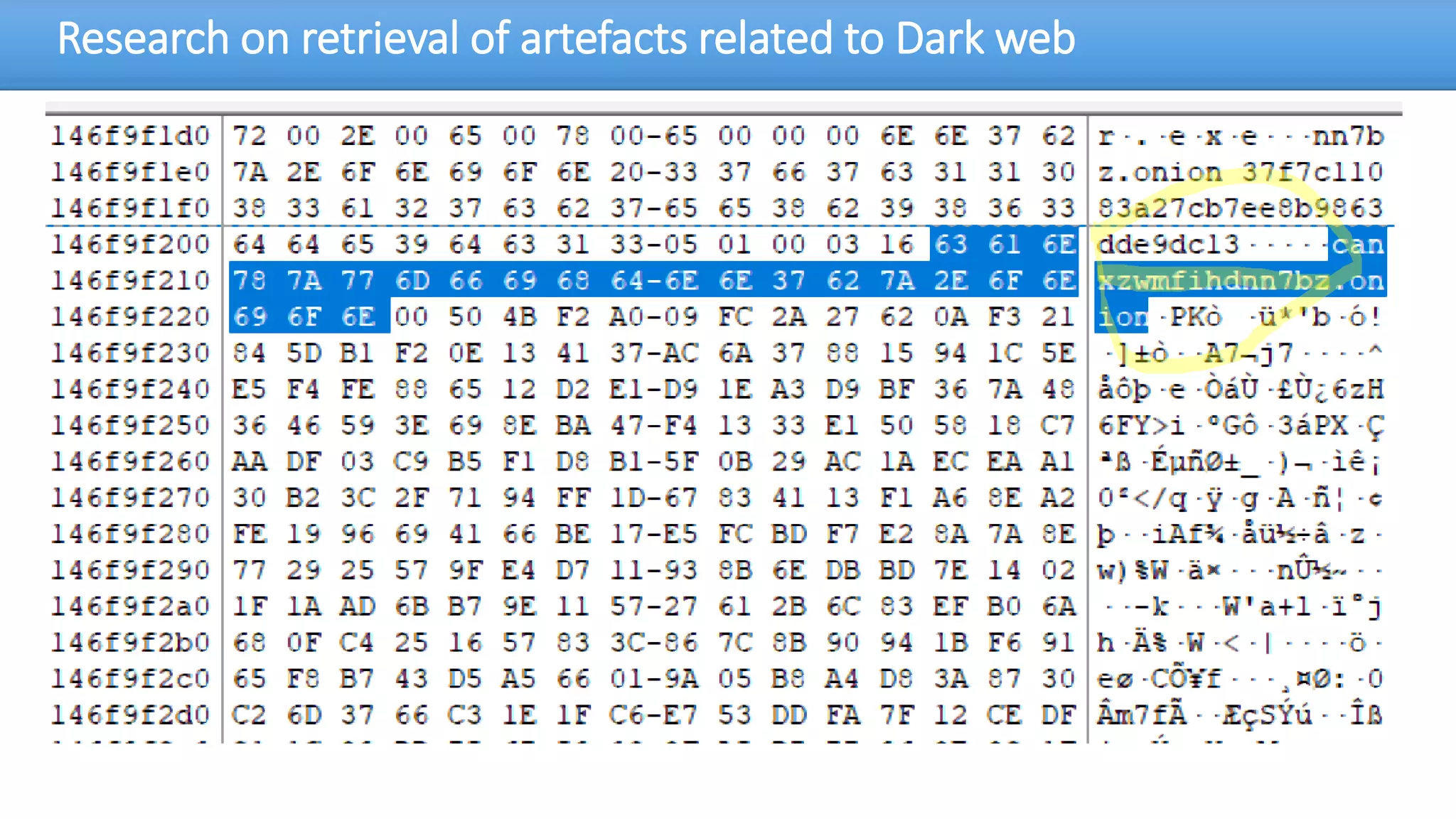
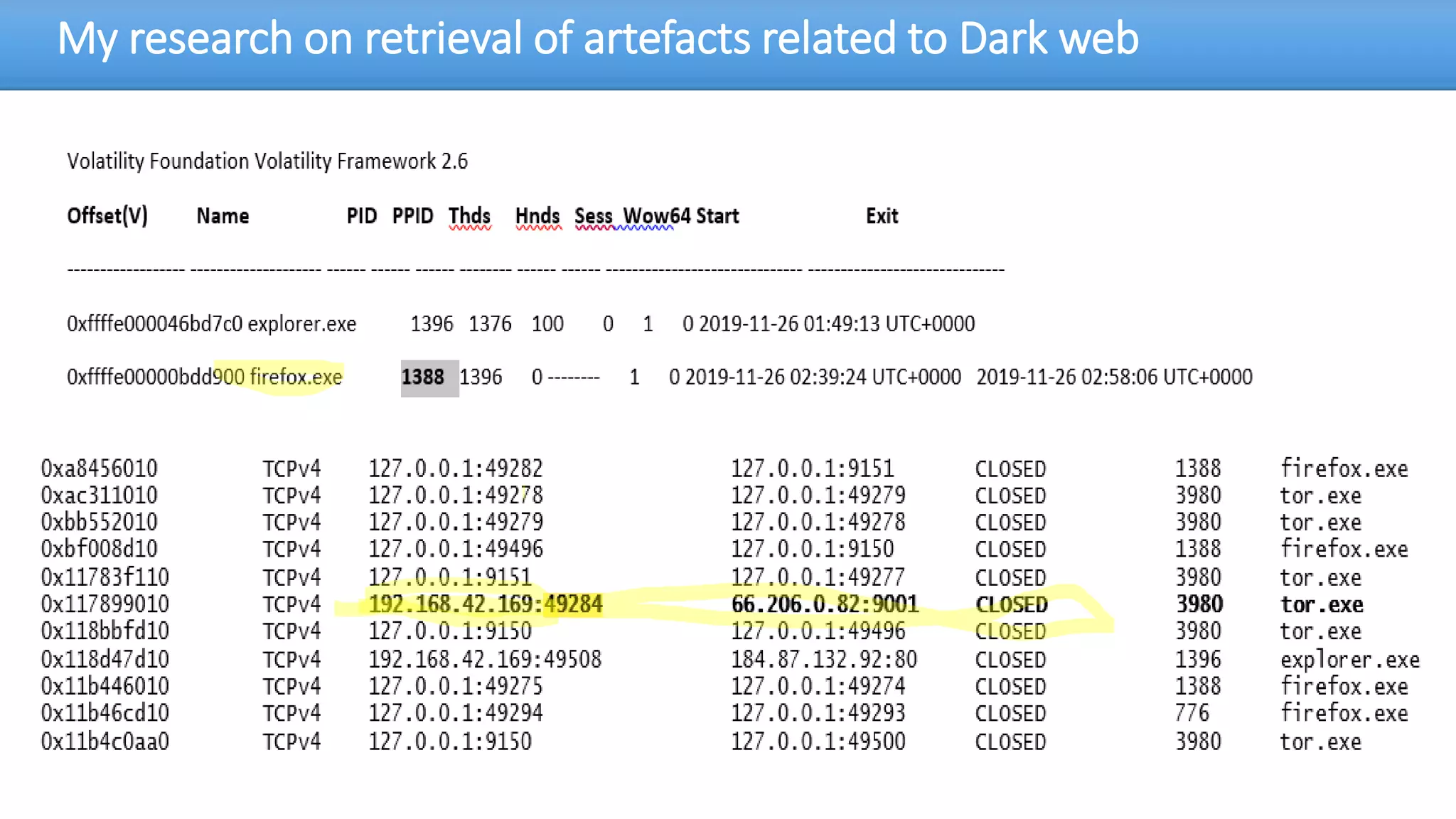
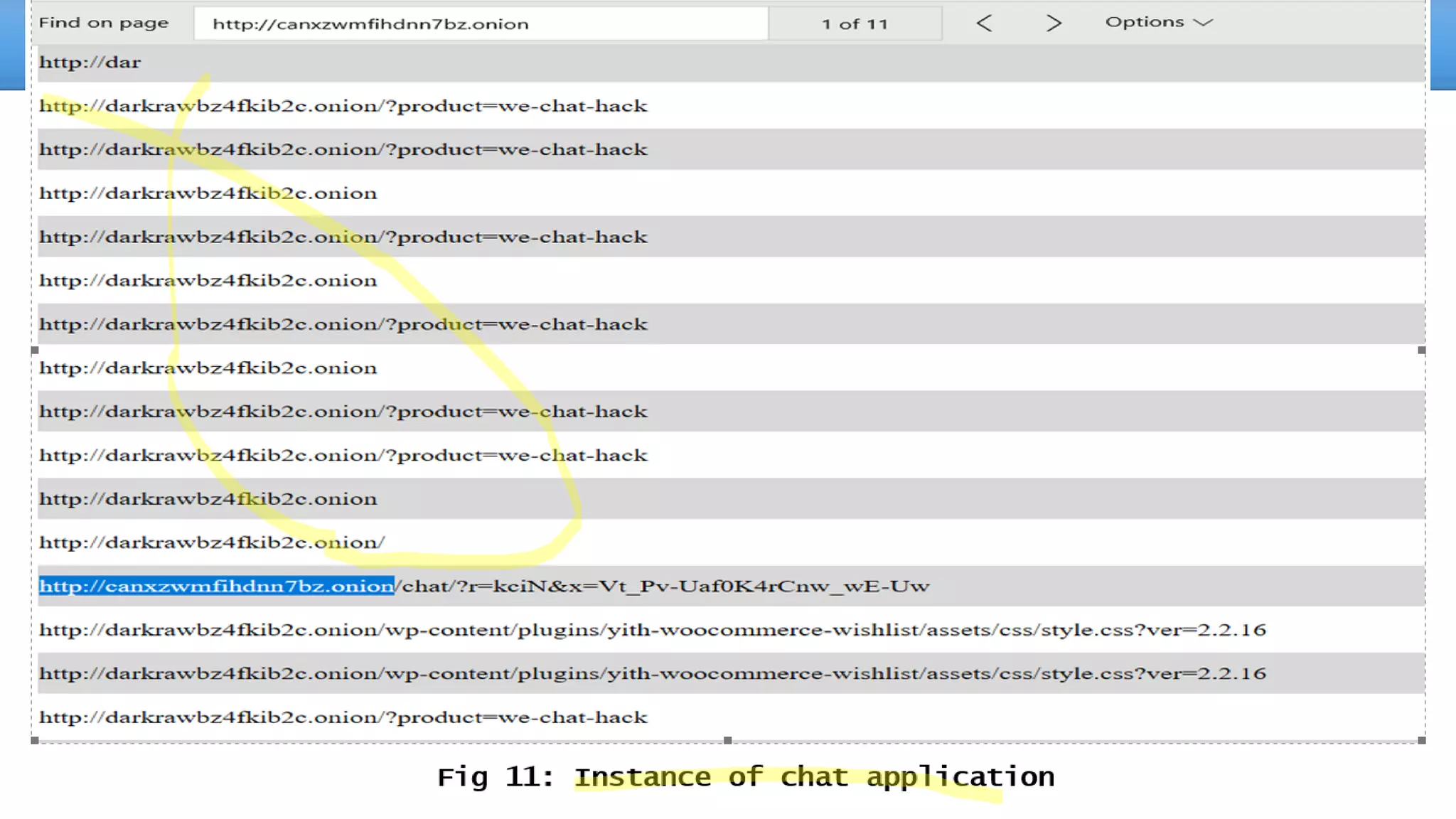
The document discusses the dark web, highlighting its appeal for anonymity and privacy, which attracts both legitimate users such as journalists and criminal activities such as drug trafficking and child pornography. It outlines the challenges law enforcement faces in investigating dark web crimes, including issues of anonymity and the use of cryptocurrencies, as well as the importance of digital forensics. The session aims to improve understanding of the dark web, its implications for privacy, and the difficulties in collecting evidence against criminal elements operating within it.