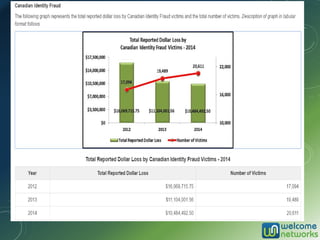
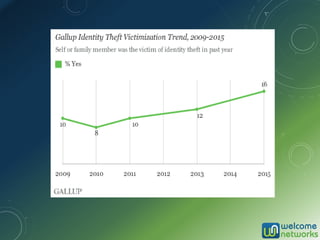
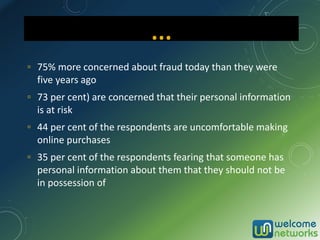
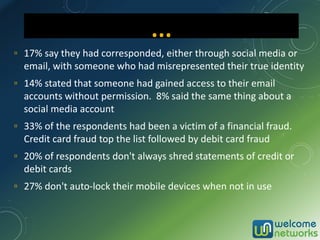
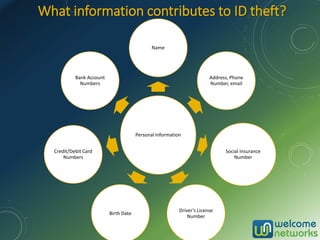
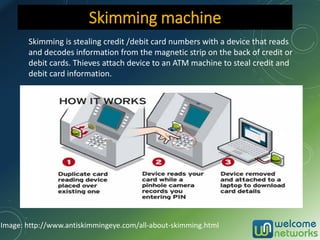
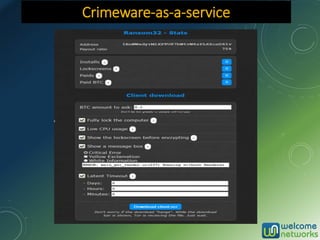
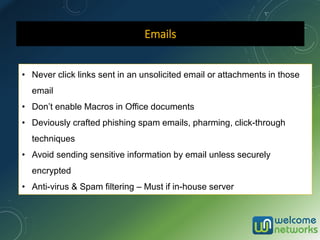
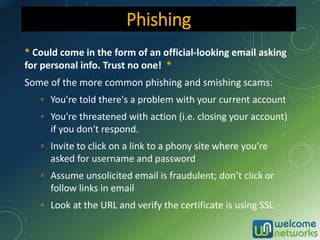
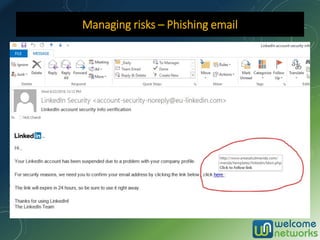
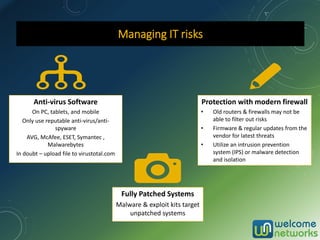
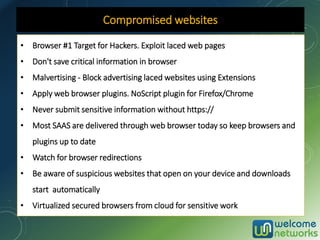
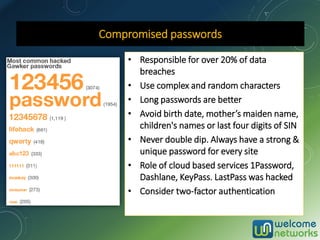
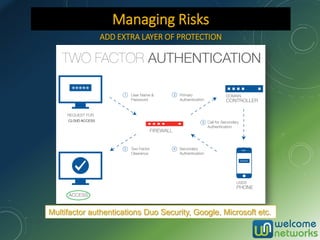
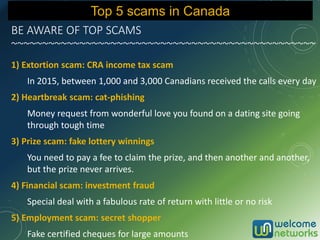
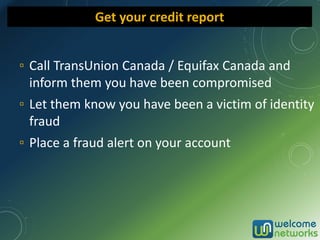
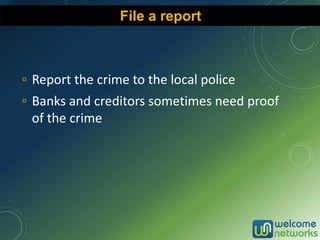
The document discusses the increasing risk of identity theft and how to prevent it, highlighting key statistics and common scenarios. It emphasizes the importance of vigilance and various protective measures, such as securing personal information and utilizing technology safely. The document also outlines the steps to take if one becomes a victim of identity theft, including notifying credit agencies and law enforcement.