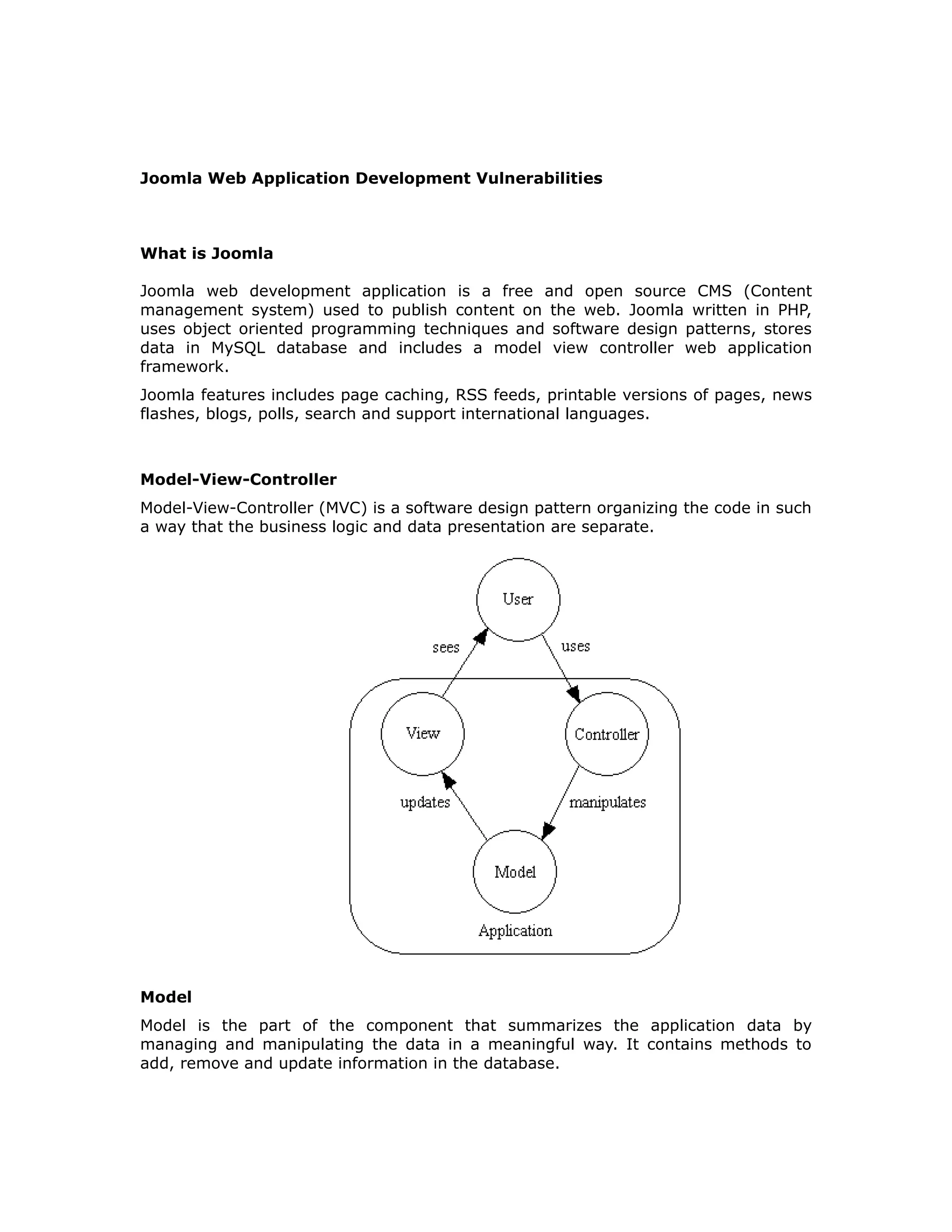
Joomla is a free and open source CMS that uses PHP and MySQL. It is vulnerable to attacks like XSS, SQL injection, file execution, insecure authentication, and failure to encrypt sensitive data. Developers should use safe SQL queries, validate all user input, implement secure session handling, encrypt passwords and sensitive data, and restrict access to privileged URLs and functions.