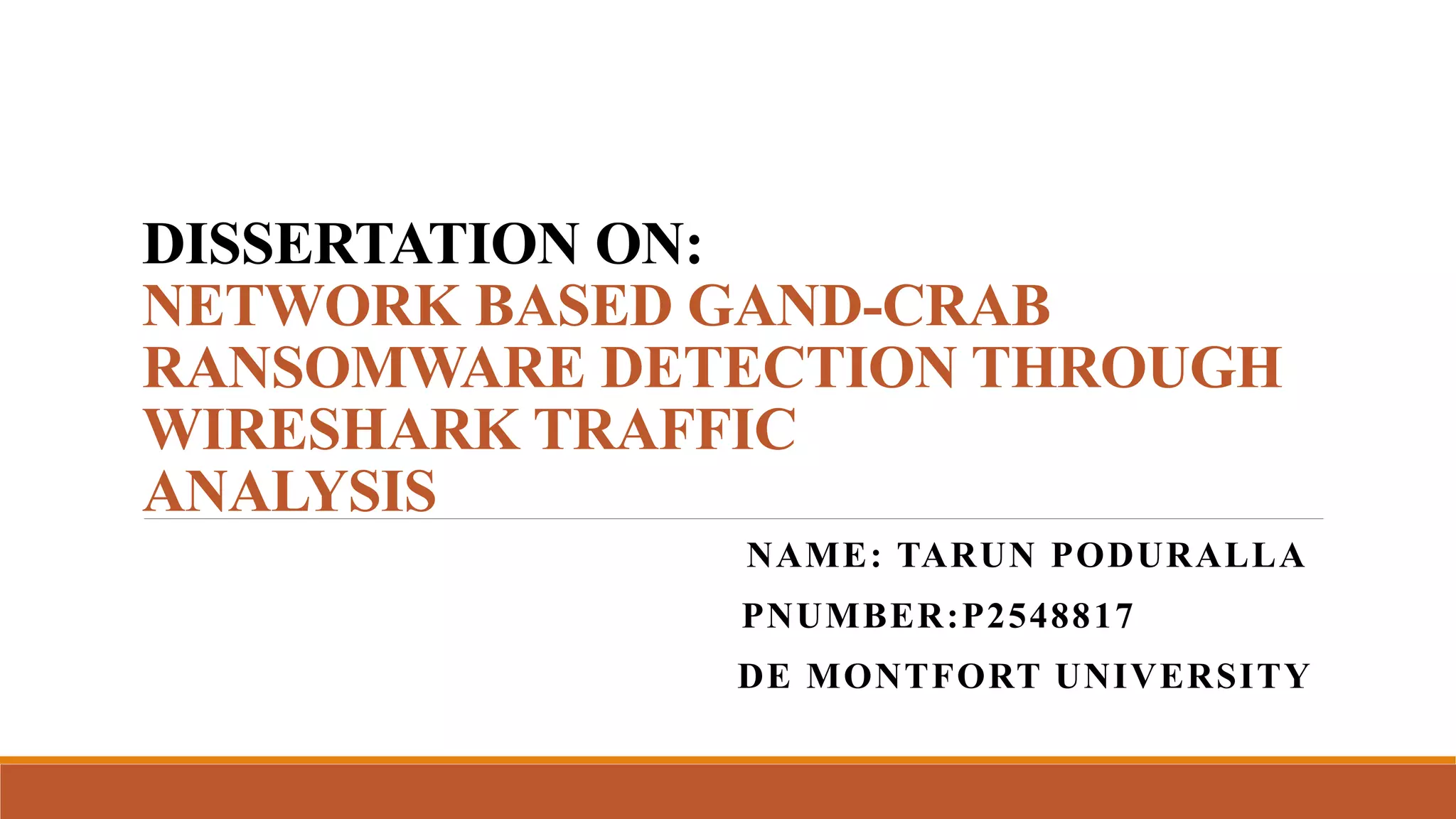
This document is a dissertation analyzing the GandCrab ransomware through network traffic using Wireshark. It outlines the objectives to assess and analyze a ransomware sample in network traffic and the network behavior once ransomware enters a system. The research methodology section describes setting up a test bed environment with 4 systems to execute and monitor the ransomware's network activities by capturing PCAP files with Wireshark for analysis. Key features of the GandCrab PCAP file are then extracted for further research on GandCrab, which spread widely in 2018 as a ransomware-as-a-service.



![Introduction
Project Motivation:
•WannaCry attack that affected the NHS and brought down the employee to pen and paper is one
of the motivational elements for studying malware-based project.
•Secondly the recent malware attacks that are being attempted on many systems in the form of
social engineering attack where the document related to cure for COVID-19 contained malware to
hit the target [1] motivated me to go for this malware-based project [1].
Project Objective:
•The main objective of this project is to produce standard project which will explain the behaviour
of the malware.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-5-320.jpg)
![2.LITERATURE REVIEW
Types of Ransomware: The ransomware encrypt the files and tries to infect the drives on the
network and once the network is infected, the whole section of a company could be brought down
by the attack . The crypto ransomware has been categorised as three types.[1]
1. Symmetrical Cryptosystem Ransomware : This deals with the concept of symmetric key
cryptography, though it could be mitigated by reverse engineering to obtain the secret key but,
the normal process gets distorted for few times.
2. Asymmetrical Cryptosystem Ransomware: These effects the system when the command
and control (c & C) server communicates with the system. The private key is withheld with
the adversary, and hence the reverse engineering fails to get the key. The adversary is left with
no other choice than to pay for ransom.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-6-320.jpg)

![Figure.1 [1] Crypto ransomware network communications(a) Symmetrical encryption, (b) Asymmetrical encryption](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-8-320.jpg)


![RANSOMWARE RELATED
BACKGROUND RESEARCH:
Some of the deadliest ransomwares are, Bad Rabbit, Ryuk, Troldesh, Locky and many others.
1. Bad Rabbit: This ransomware was first seen in the year 2017 and it used a method called
“drive-by” which is a flavour of Petya and WannaCry Malware.
•This Ransomware mainly attacks through vulnerable websites through fake Adobe Flash
Updates[ ] by manipulating users to click on fake advertisements to update Flash Player.
2. RYUK: Ryuk was first discovered in August 2018 but based on older Ransomware called
Hermes which was sold on underground cyber forums in 2017. [ ] It initiates through either
Remote Desktop Protocol (RDP) or phishing emails.
•This ransomware spreads through macros in word .doc](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-12-320.jpg)
![RANSOMWARE RELATED
BACKGROUND RESEARCH:
3. Troldesh: The Troldesh ransomware is also known as Shade. Which often uses a PHP file
as a transfer tool for loading the host.
Malware Dropper (It is a trojan that is designed to install some sort of malware program).
hxxp://doolaekhun[.]com/cgi-bin/[redacted].php
•This kind of affected URL is made spread via malicious emails or using services like social media
and it started spreading through email using infected attachments and links.
•Once we click affected Jscript URL’S as shown above it loads a Jscript file to the victim’s
system. This infected file is Malware Dropper which loads jsp file into victim’s pc then it begins
the process of preparing the download of executable ransomware file.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-13-320.jpg)
![RANSOMWARE RELATED
BACKGROUND RESEARCH:
Locky: The Locky Crypto ransomware was first discovered in the year 2015 [ ].
The ransomware used to enter the victim’s system using the spam emails and then it sends the
attachment in the form of PDF. This in attached PDF is embedded with .DOCM files.
The most significant nature of this ransomware is to check the target hosts. It contains a flag
which checks if the targeted system contains Russian Operating System Language or not. If its
Russian, it does not exploit the or encrypts the system [ ].
The most common symptoms that Locky has infected the system is by sighting the network
speed and system’s speed.
The Locky Ransomware takes advantage of the macro that is usually used to open and doc file.
In Windows based operating system, these options are by default enabled and thus helps the
ransomware to enter the targeted system easily [ ].](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-14-320.jpg)
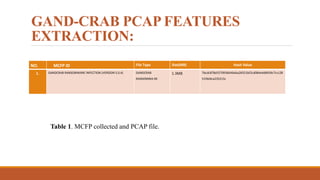
![4. Research Methodology
SETTING UPA GAND-CRAB RANSOMWARE NETWORK TRAFFIC ANALYSIS TEST BED
ENVIRONMENT
Figure.(3) [1] Ransomware Test Bed Environment.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-15-320.jpg)

![Ransomware Testbed Environment:
PC 3 is used as an attacker C&C server.
This is an Asymmetrical Cryptosystem Ransomware attack.
To analyse this network traffic we use WIRESHARK as a Network Traffic Analyser Tool
(NAT).[6]
But to analyse a Ransomware network traffic a packet capture file in extension. PCAP should
be obtained from source. Here we are obtaining Ransomware traffic named GandCrab from
• Malware-traffic-analysis.net [8].
• https://www.malware-traffic-analysis.net/2018/11/02/index.html.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-17-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
GandCrab ransomware was discovered near the end of January 2018 as a part of Ransomware-as-a-
Service (RaaS) and soon became the most popular and widespread ransomware of the year.[7]
GandCrab spread through multiple sources via spam mails and exploit kits. Grandsoft and RIG are
mostly used tools for spreading Gandcrab with high volume of malicious spam mails.
Grandsoft and RIG are an exploit kit which is designed to attack systems silently by utilizing the
vulnerabilities present on victim’s machine while accessing the web. There are three stages in this
Landing page, Exploit, Payload.
Landing Page: It starts with a click on compromised websites by delicately landing into another
webpage after landing into malicious web page the exploit part takes place softly.
Exploit: It uses a vulnerable application in background to run malware on victim’s machine secretly.
Some of the targeted applications include Adobe Flash Player, Java Runtime Environment whose
exploit is a file and web browser, which sends harmful code from with suspicious web traffic. If
Successful next step is payload delivery.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-19-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
Payload: If Exploit becomes successful it sends a payload to infect victim’s system (host). The
payload is a file downloader that retrieves different malware or the meant malware itself.
With a lot of exploit kits, the payload is distributed as encrypted binary code over the network,
which then once on the victim’s machine host, the binary code gets executed and encryption
begins.
GandCrab is a type of ransomware which mostly attacks through emails.[7]
• These emails which contains ZIP archives when opened it has scripts to download GandCrab
ransomware and execute it, when these files are executed, it decodes the url where GandCrab is
hosted then download of malware to the files on disk begins.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-20-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
It was a first ransomware is to use DASH currency as a ransom payment. Most file encrypting
ransomware families have solely used Bitcoin as the ransom payment methodology. Lately, some
ransomware infections are moving to Monero and even Ethereum.
DASH currency is designed around privacy and therefore it has become difficult for
enforcements to trace the house owners of the coins.
Figure. (4) [7] DASH Currency as Payment.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-21-320.jpg)
![Figure. (5) [7] GandCrab Ransomware Logo.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-22-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
How GandCrab encrypts a computer:
• When GandCrab first launched it tries to connect ransomware’s C&C which is Command and Control server
created by ransomware creator. This server is organised in the name Namecoin’s. bit domains [7],it has to instruct a
server name that supports TLD.
• It is done by searching for addresses of following domains using nslookup [insert domain] a.dnspod.com. This
command searches for a.dnspod.com names server, which support the. bit TLD, for one of the domains below.[7]
bleepingcomputer.bit
nomoreransom.bit
esetnod32.bit
emsisoft.bit
gandcrab.bit](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-23-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
If the victim's machine is unable to attach to the C3 server, then the ransomware will not write code to the
pc. It will, though, continue running within the background trying to get the ip address for C3 and connect to
it.
Once it's able to resolve the domain connection, it'll connect with the C3 IP address. It is not proverbial
now what knowledge is being sent and retrieved, however the C3 is presumably sending the general public
key that can encrypt the files.
During this method, the ransomware connects to ip address below to determine the public IP
address of the victim http://ipv4bot.whatismyipaddress.com/ .[7]
Before GandCrab encrypts the victim's files it will 1st check for sure processes and terminate them. This
may shut any file handles that are open by these processes in order that they will be properly encrypted.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-24-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
According to researcher Vitali Kremez, the list of processes that are terminated are:
Figure. (6) [7 ]The list of Terminated Processes.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-25-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
GandCrab will now begin to encrypt the victim's files and will target only certain file extensions.
According to Researcher Pepper Potts [].
While encrypting files, Kremez's analysis showed that GandCrab will skip any files whose full pathname
contain following strings:
ProgramData, Program Files, Tor Browser, Ransomware, All Users, Local Settings,
desktop.ini, autorun.inf, ntuser.dat, iconcache.db, bootsect.bak, boot.ini, ntuser.dat.log,
thumbs.db, GDCB-DECRYPT.txt, .sql](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-26-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
After Encrypting files, the ransomware will add .GDBC extension to encrypted file’s name. For example
t.jpg would be encrypted and renamed as t.jpg.GDBC.
Figure. 7 [7] Encrypted GDBC files.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-27-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
At some point, the ransomware relaunches itself using the command
"C:Windowssystem32wbemwmic.exe" process call create "cmd /c start
%Temp%[launched_file_name].exe". If a user does not respond Yes to the below prompt, it
will continuously display the UAC prompt.
Figure.8 [7] UAC Prompt.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-28-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
When Ransomware finished encrypting the system, victim receives the Ransom note located on
the desktop screen. This ransom note will be in GDBC-DECRYPT.txt format and contains
attack information of the victim’s files and secure TOR website gateways will be listed to open
payment site.
Figure. (9) [7] GandCrab
GDBC-DECRYPT.txt Ransom
Note](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-29-320.jpg)
![GANDCRAB RANSOMEWARE
ATTACK RESEARCH:
When access the listed website, a website named GandCrab Decryptor will appear. This website
shows ransom note information, a DASH link to make payment and few other options as below.
Figure.10 [7] GandCrab Decryptor.](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-30-320.jpg)
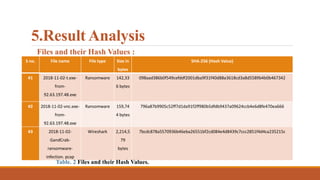
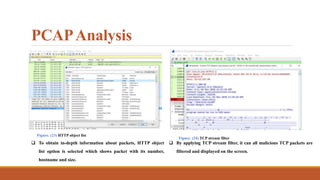
![Ransomware File Analysis
Figure. 12 [5] Analysis on vnc.exe file
Figure. 13 [5] Analysis on t.exe file](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-35-320.jpg)
![Different Antivirus Ratings
Figure. (15) [5] Different Antivirus Ratings.(t.exe)
Figure. (14) [5] Different Antivirus Ratings.(vnc.exe)](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-36-320.jpg)
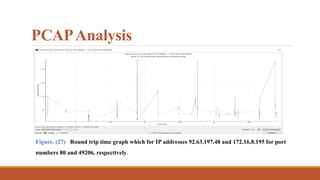
![Falcon Sandbox Reports
Figure. (16) [5] Second malicious capture
(vnc.exe)
Figure. (17 ) [5] Second malicious capture (t.exe)](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-37-320.jpg)








![7. References
6. M. M. Ahmadian, H. R. Shahriari and S. M. Ghaffarian, "Connection-monitor & connection-breaker: A
novel approach for prevention and detection of high survivable ransomwares",Proc. 12th Int. Iranian Soc.
Cryptol. Conf. Inf. Secur. Cryptol. (ISCISC), pp. 79-84, Sep. 2015
7. https://www.bleepingcomputer.com/news/security/gandcrab-ransomware-distributed-by-exploit-kits-
appends-gdcb-extension/
8. "Malware-Traffic-Analysis.net - 2018-11-02 - GandCrab ransomware infection (version 5.0.4)", Malware-
traffic-analysis.net, 2021. [Online]. Available: https://www.malware-traffic-
analysis.net/2018/11/02/index.html. [Accessed: 25- Jun- 2021].](https://image.slidesharecdn.com/gandcrabransomwareanalysis-210706193433/85/Gand-crab-ransomware-analysis-49-320.jpg)