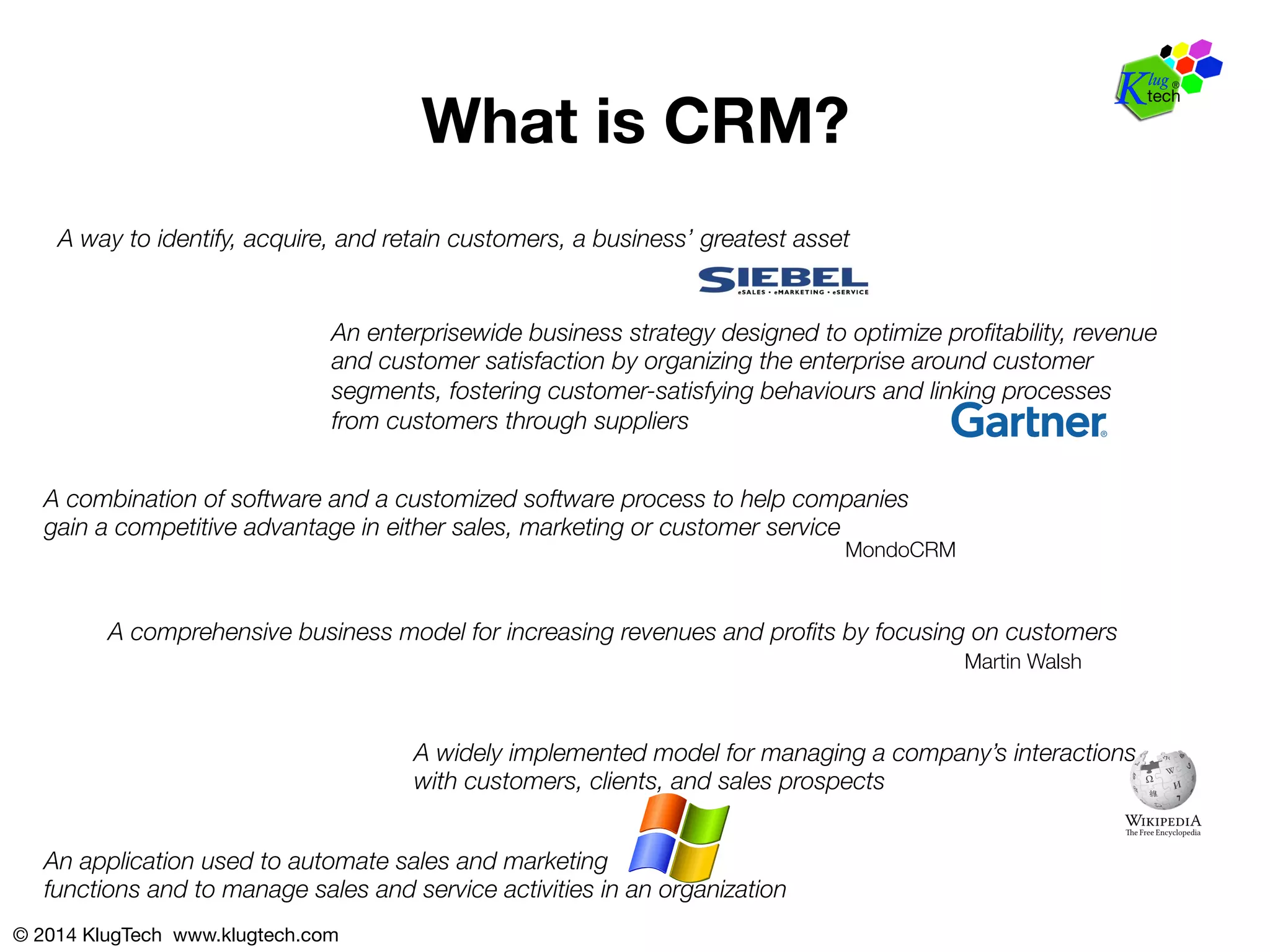
The document discusses customer relationship management (CRM) systems and the importance of securing sensitive customer data. It notes that while CRM systems aim to optimize customer satisfaction, many companies do not adequately protect private customer information. The document advocates for CRM systems that limit data access, encrypt data storage, and divide data across secure databases in order to responsibly manage the sensitive customer information entrusted to companies.






![All [too] Powerful
Does a single person really need access to the whole database?
© 2014 KlugTech www.klugtech.com
Limit access
Prevent database downloads](https://image.slidesharecdn.com/safe-crm-140906061130-phpapp01/75/Secure-CRM-Management-10-2048.jpg)