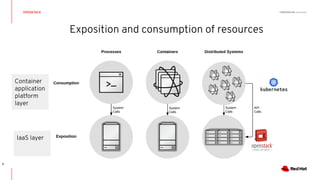
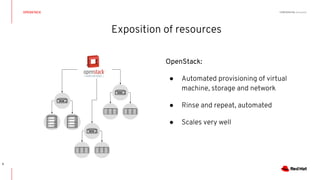
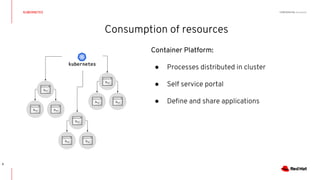
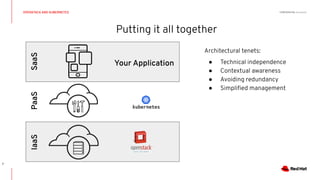
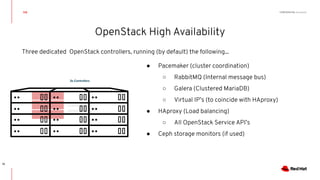
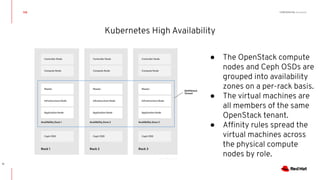
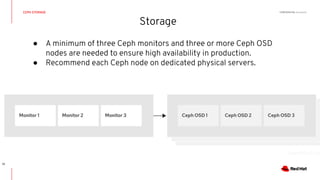
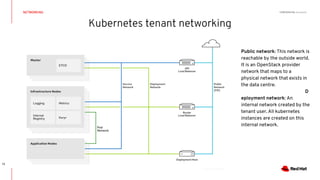
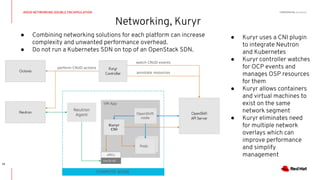
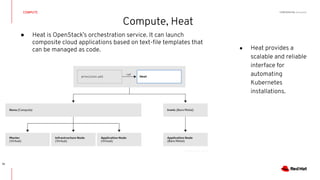
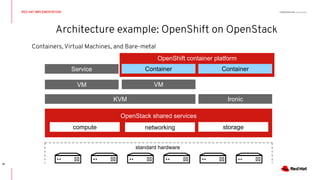
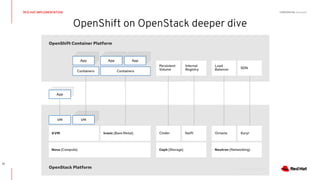
This document discusses running Kubernetes on OpenStack at scale. It describes how OpenStack provides automated provisioning of infrastructure resources, while Kubernetes provides a container platform for consuming those resources. The advantages of combining these technologies include fully automated infrastructure, consistent management experience, isolation for workloads, and leveraging existing plugins. It provides an example architecture using Red Hat OpenShift on OpenStack with key components like Ceph storage, Neutron networking integrated via Kuryr, and Heat for orchestration.