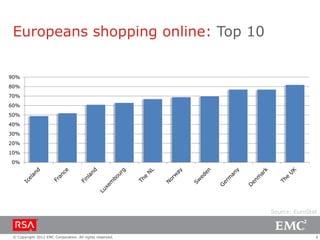
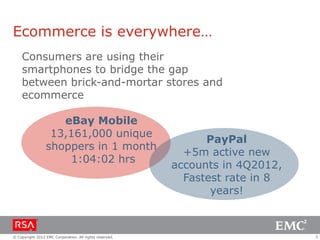
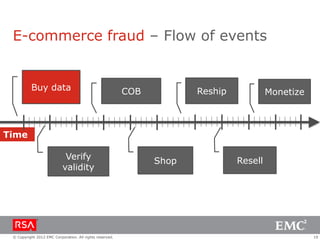
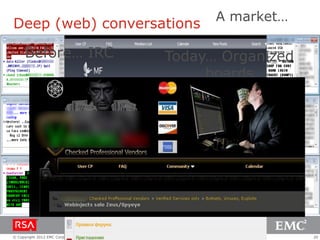
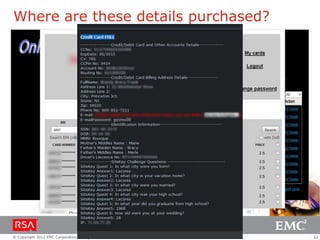
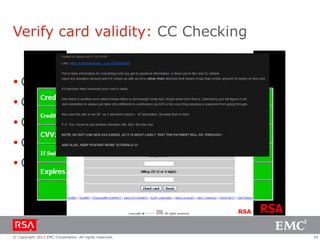
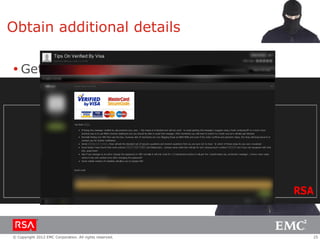
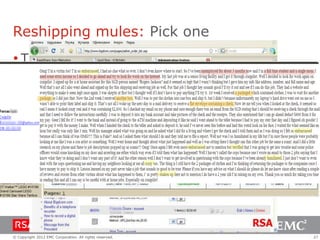
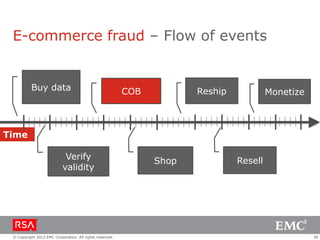
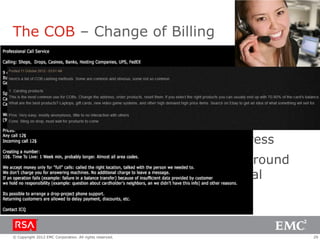
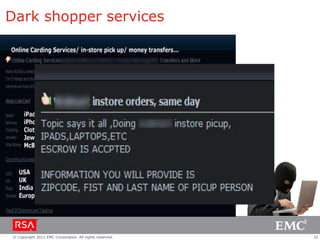
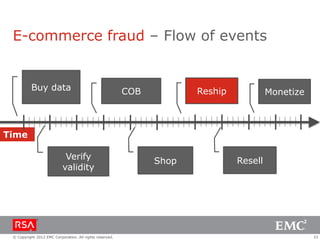
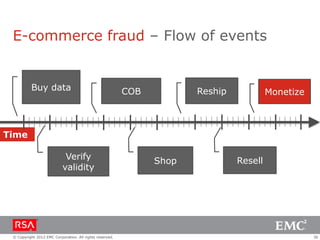
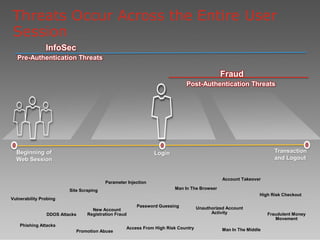
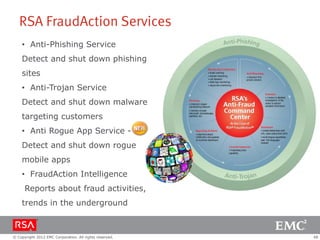
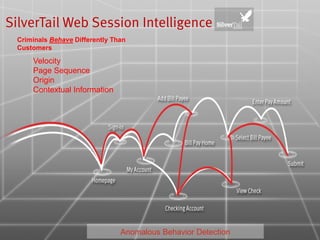
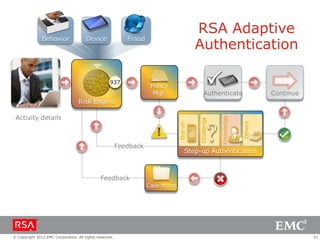
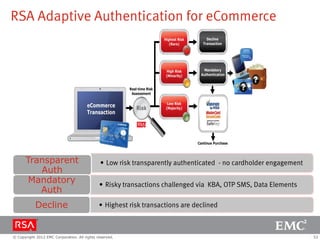
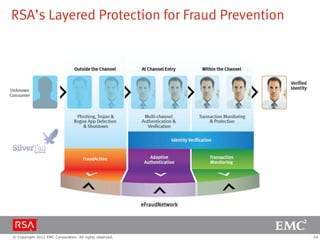
The document discusses e-commerce fraud trends in 2013, highlighting the significant financial losses incurred by retailers due to cybercrime, particularly in the UK and Ireland. It delves into the methods used by fraudsters, including phishing, data trafficking, and the exploitation of payment systems, while also outlining strategies for prevention and protection against such fraud. The content emphasizes the importance of user vigilance and cooperative measures by banks and retailers to mitigate risks associated with e-commerce fraud.