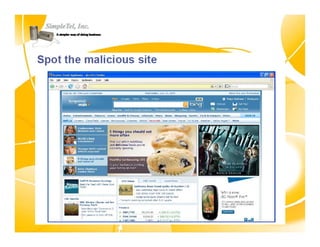
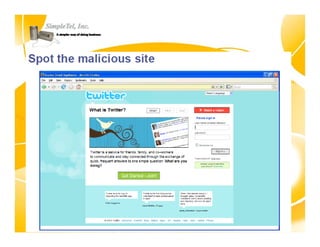
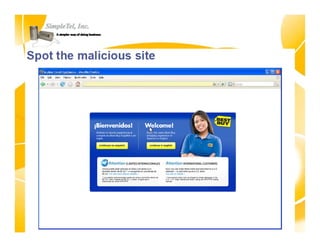
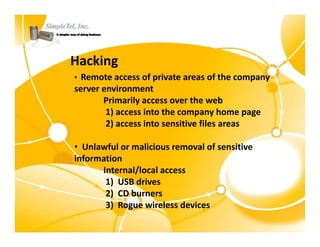
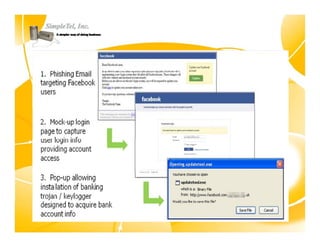
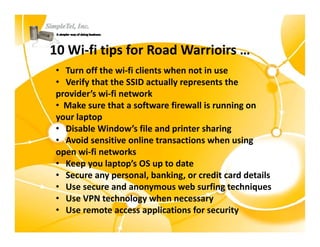
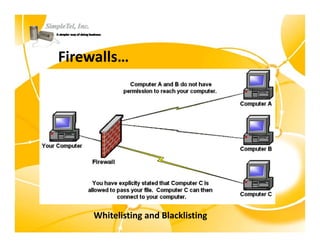
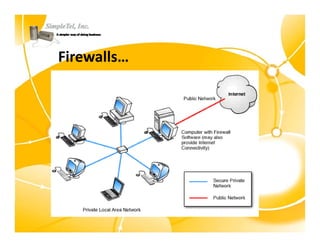
This document discusses identity theft and provides an overview of protection methods. It begins by defining identity theft as the compromise and fraudulent use of personal data like date of birth, social security number, financial information, and contact details. It then evaluates criminal methodologies such as hacking, malware, keyloggers, and phishing scams that thieves use. Finally, it considers protective solutions like firewalls, antivirus software, endpoint security, and using cloud services to secure systems and monitor unauthorized data transfers.