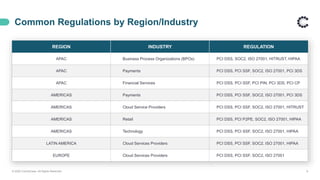
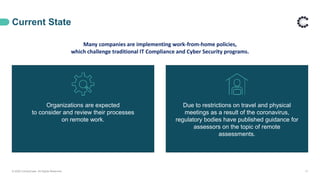
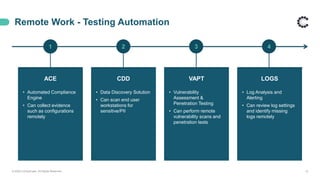
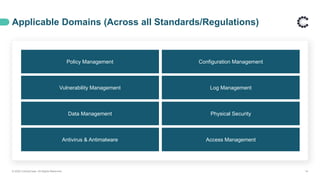
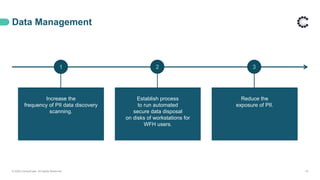
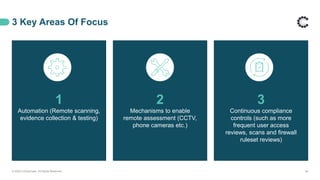
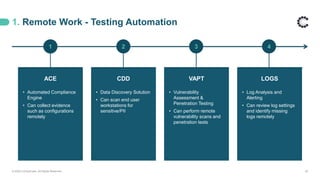
ControlCase offers certification and continuous compliance services, leveraging a remote assessment methodology to enhance efficiency and reduce costs while ensuring IT compliance in various regulatory environments. The document discusses the implications of remote work on compliance and cybersecurity, advocating for effective management through automation, continuous monitoring, and specific controls—particularly in Zero Trust environments. It highlights the importance of adapting compliance efforts to accommodate remote work challenges, emphasizing tools and strategies for successful assessments and ongoing compliance management.