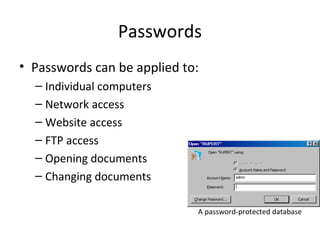
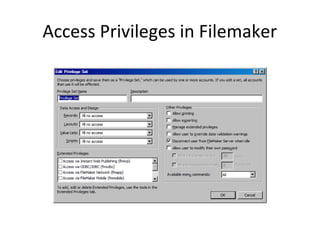
This document summarizes various methods for protecting data security. It discusses procedures like using passwords, biometric identification, encryption, and access hierarchies to restrict data access. It also covers consequences of not protecting data like loss of trade secrets, privacy violations, loss of reputation, income loss, and potential legal prosecution. The document recommends regular backups stored offsite, using virus scanners and firewalls, and properly disposing of or destroying old storage devices.