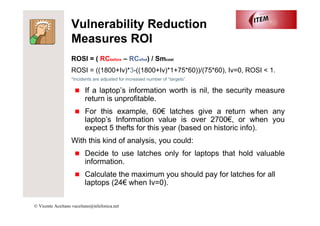
The document discusses return on security investment (ROSI) and making security decisions based on hard data rather than fear or random choices. It outlines two types of security measures - vulnerability reduction, which aims to prevent incidents, and impact reduction, which limits maximum loss. Vulnerability reduction ROI can be calculated by comparing risk costs before and after investing in a measure. Impact reduction provides efficiency but not a direct ROI. Gathering information on past incidents is important for making data-driven security choices.