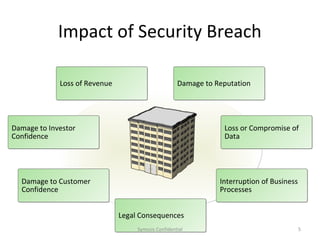
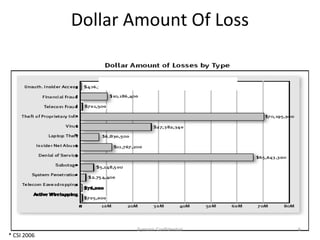
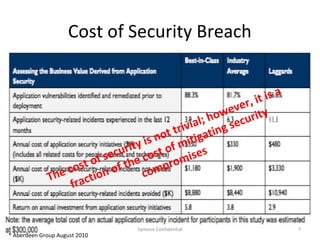
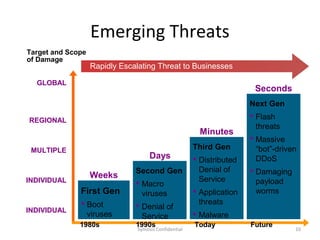
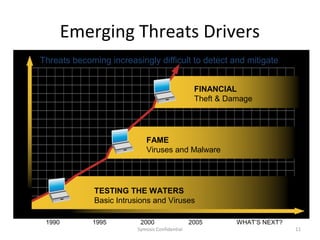
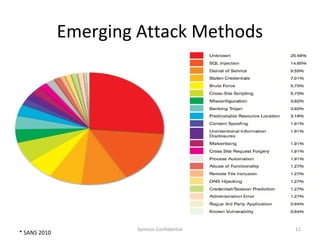
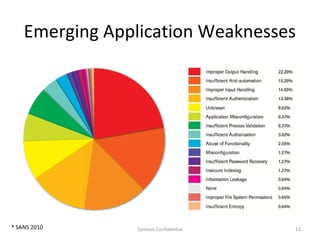
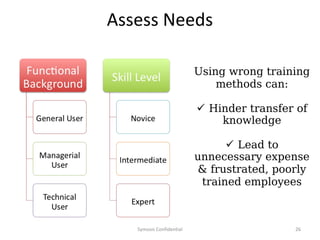
The document outlines the importance of maximizing the return on investment (ROI) from security training, detailing the business cases for security, the impact of breaches, and emerging threats. It provides a framework for building effective training programs, including defining objectives, assessing needs, and evaluating key success factors. Case studies illustrate successful implementations of security training in various industries to enhance awareness and compliance.