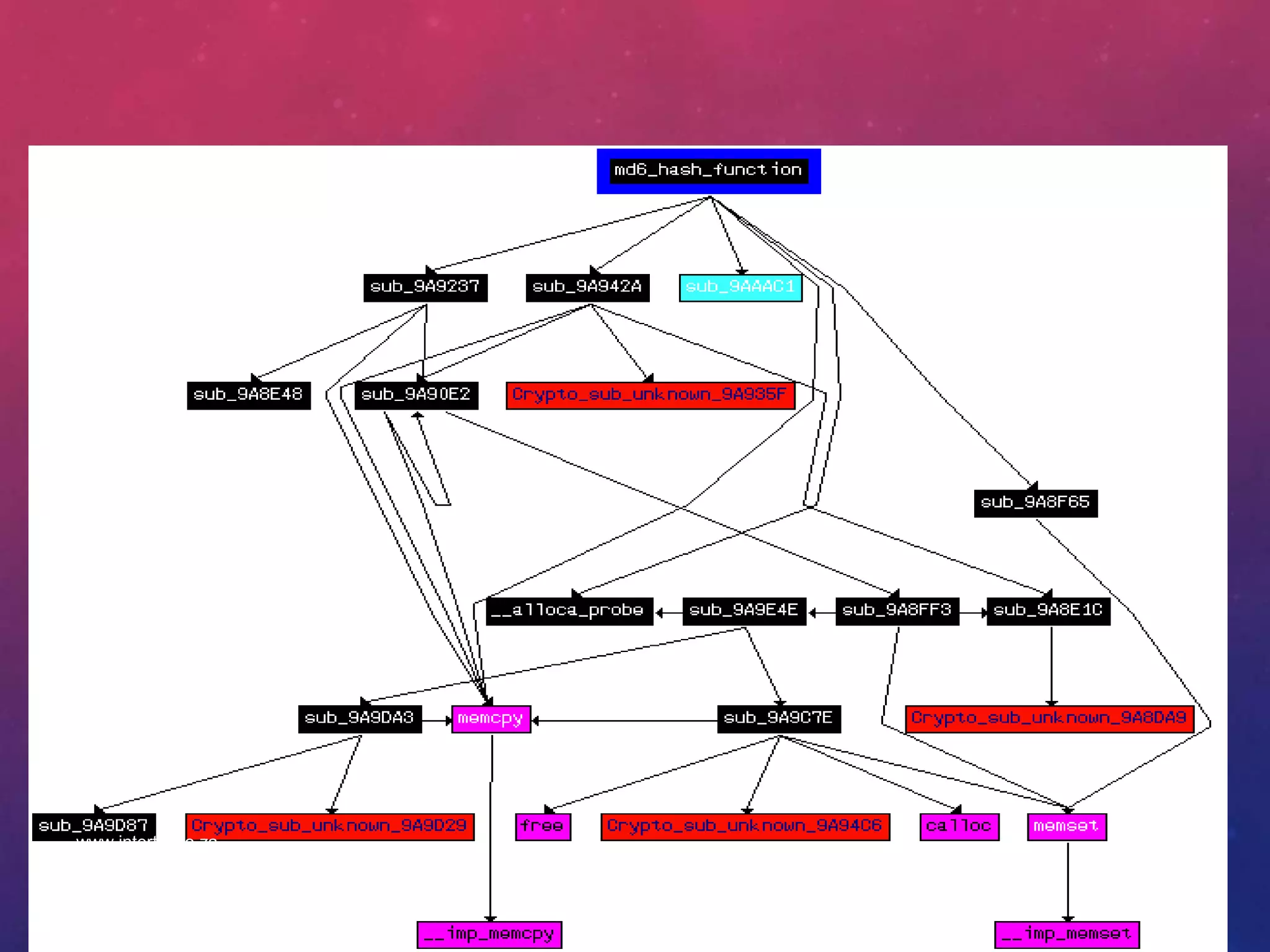
The document discusses challenges in malware analysis and describes a system for automated static malware analysis. It outlines techniques for capturing malware, disassembling malware binaries, resolving obfuscated API calls, and handling obfuscation techniques used by malware authors to evade analysis. The system aims to unpack malware, recover the original program structure, and produce a higher-level representation to facilitate understanding the malware's purpose and functionality.

















![EXAMPLES OF DISASSEMBLY PROBLEMS (THE STORM WORM)
Data hidden as code:
ArcadeWorld.exe:0042BDB0 mov eax, 0
ArcadeWorld.exe:0042BDB5 test eax, eax
ArcadeWorld.exe:0042BDB7 jnz short loc_42BDD8; unreachable code
ArcadeWorld.exe:0042BDD8 loc_42BDD8: ; CODE
XREF: 0042BDB7
ArcadeWorld.exe:0042BDD8 lea edx, [ebp+401C42h]
ArcadeWorld.exe:0042BDDE lea eax, [ebp+40B220h]
ArcadeWorld.exe:0042BDE4 push eax
ArcadeWorld.exe:0042BDE5 push 8A20h
ArcadeWorld.exe:0042BDEA push edx
ArcadeWorld.exe:0042BDEB call near ptr unk_42BF7D
ArcadeWorld.exe:0042BDF0 pusha
ArcadeWorld.exe:0042BDF1 mov edi, [ebp+40C067h]
ArcadeWorld.exe:0042BDF7 add edi, [ebp+40C03Fh]
ArcadeWorld.exe:0042BDFD lea esi, [ebp+40BFBFh]
0042BDD8 8D 95 42 1C 40 00 8D 85 20 B2 40 00 50 68 20 8A ìòB.@.ìà ¦@.Ph è
0042BDE8 00 00 52 E8 8D 01 00 00 60 8B BD 67 C0 40 00 03 ..RFì...`ï+g+@..
0042BDF8 BD 3F C0 40 00 8D B5 BF BF 40 00 B9 74 00 00 00 +?+@.ì¦++@.¦t...
0042BE08 68 00 20 00 00 57 E8 26 FF FF FF F3 A4 8D 85 AF h. ..WF& =ñìà»
0042BE18 BF 40 00 8B 9D 3F C0 40 00 FF B5 43 C0 40 00 FF +@.ï¥?+@. ¦C+@.
0042BE28 B5 37 C0 40 00 6A 01 50 53 E8 9E 00 00 00 FF B5 ¦7+@.j.PSFP... ¦
0042BE38 6B C0 40 00 FF B5 3F C0 40 00 E8 DE FD FF FF 8B k+@. ¦?+@.F¦² ï
0042BE48 85 18 B2 40 00 85 C0 74 1C FF B5 18 B2 40 00 FF à.¦@.à+t. ¦.¦@.
0042BE58 B5 57 C0 40 00 FF B5 3F C0 40 00 E8 E7 10 00 00 ¦W+@. ¦?+@.Ft...
0042BE68 E8 3F FE FF FF 53 E8 E5 04 00 00 E8 14 00 00 00 F?¦ SFs...F....
0042BE78 5C 64 6C 6C 63 61 63 68 65 5C 74 63 70 69 70 2E dllcachetcpip.
0042BE88 73 79 73 00 E8 16 0A 00 00 E8 13 00 00 00 5C 64 sys.F....F....d
www.intertel.co.za](https://image.slidesharecdn.com/malware-presentation-2-160305112124/75/Reverse-Engineering-Malware-A-Practical-Guide-28-2048.jpg)


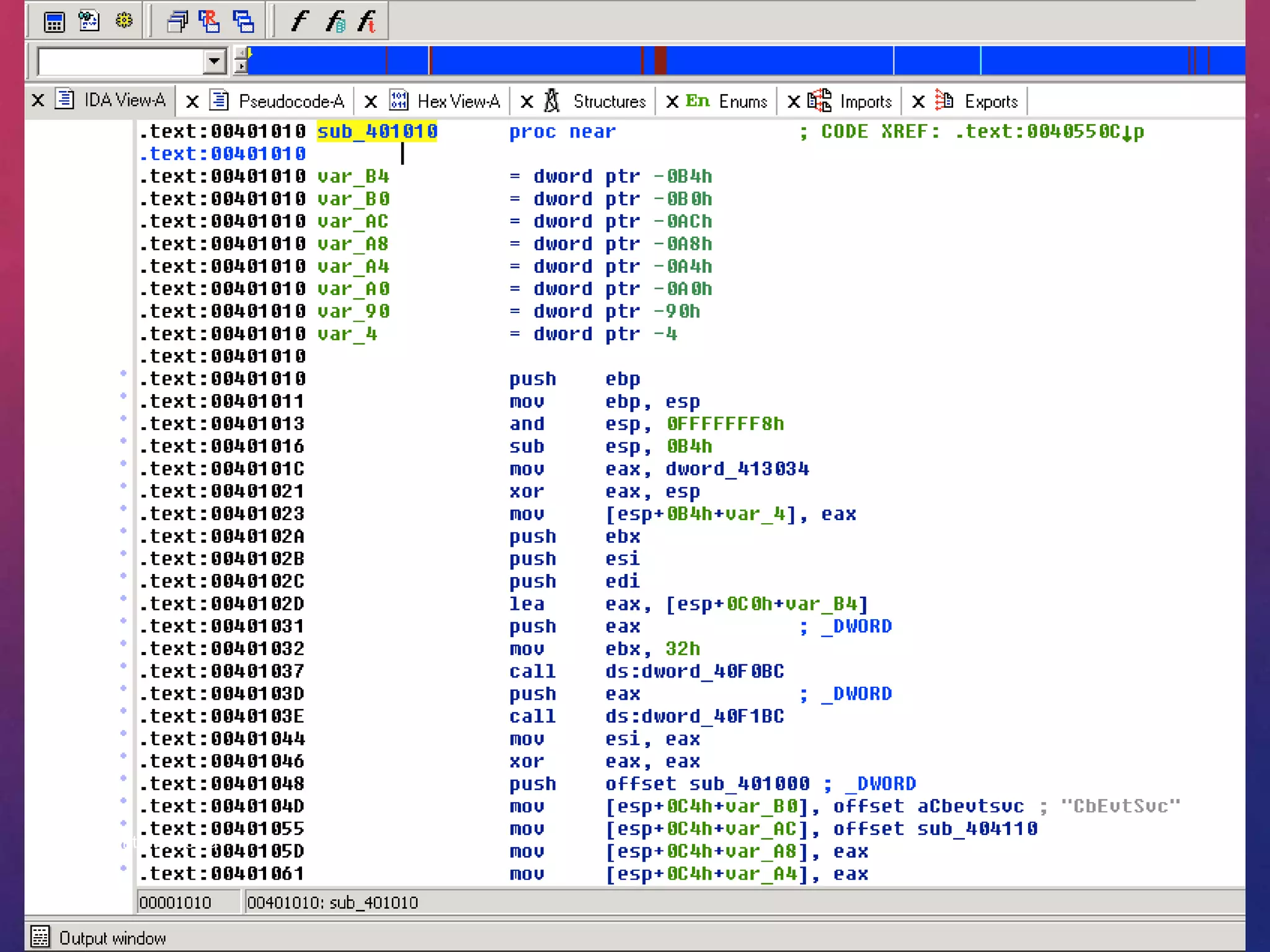
![CONSEQUENCE OF FAILURE TO IDENTIFY APIS
...
.text:004011A7 push offset unk_40A2DC ; arg 1
.text:004011AC xor ebx, ebx
.text:004011AE call dword ptr unk_40A0E4 .data:0040A0E4 00000000
.text:004011B4 mov edi, eax
.text:004011B6 cmp edi, ebx
.text:004011B8 jz short loc_401211
.text:004011BA push esi
.text:004011BB mov esi, dword ptr unk_40A0E8
.text:004011C1 push offset unk_40A2C4 ; arg 2
.text:004011C6 push edi ; arg 1
.text:004011C7 call esi ; unk_40A0E8 .data:0040A0E8 00000000
.text:004011C9 push offset unk_40A2AC
.text:004011CE push edi
.text:004011CF mov dword_433480, eax
...
...
.text:00401132 lea eax, [ebp+var_4]
.text:00401135 push eax
.text:00401136 push ebx
.text:00401137 push 0
.text:00401139 mov [ebp+var_4], esi
.text:0040113C call dword_433480
.text:00401142 test eax, eax
…
Name of a library
Load library call (LoadLibrary)
Name of the library function
Name of the library
API call to get the address
Of the loaded library function
(GetProcAddress)
library function call
www.intertel.co.za](https://image.slidesharecdn.com/malware-presentation-2-160305112124/75/Reverse-Engineering-Malware-A-Practical-Guide-36-2048.jpg)
![FAILURE TO PERFORM CONTROL FLOW
ANALYSIS
• CreateThread
.text:009A3A4C push eax
.text:009A3A4D xor eax, eax
.text:009A3A4F push eax
.text:009A3A50 push eax
.text:009A3A51 push offset dword_9A3939
.text:009A3A56 push eax
.text:009A3A57 push eax
.text:009A3A58 call [ebx]
.data:009A3939 xxxxxxx
• Starting Services
• Thread synchronization
• Critical sections
• Callback functions
Location of the start address of a thread
Call to CreateThread
www.intertel.co.za](https://image.slidesharecdn.com/malware-presentation-2-160305112124/75/Reverse-Engineering-Malware-A-Practical-Guide-37-2048.jpg)

![ADVANCED API RESOLUTION: TYPE INFERENCE FOR BINARY PROGRAM ANALYS
• Use type inference as a single solution to solve three fundamental problems:
• Identifying API and function calls (call and jump targets)
• Building a precise CFG
• Recovering user-defined types for proper decompilation
• For Windows Executable files:
• Integers: object handles, addresses, IP address, ports, etc
• Strings: file names, service names, etc
• Structures: sockaddr
struct sockaddr_in {
short sin_family;
u_short sin_port;
struct in_addr sin_addr;
char sin_zero[8];
};
www.intertel.co.za](https://image.slidesharecdn.com/malware-presentation-2-160305112124/75/Reverse-Engineering-Malware-A-Practical-Guide-39-2048.jpg)
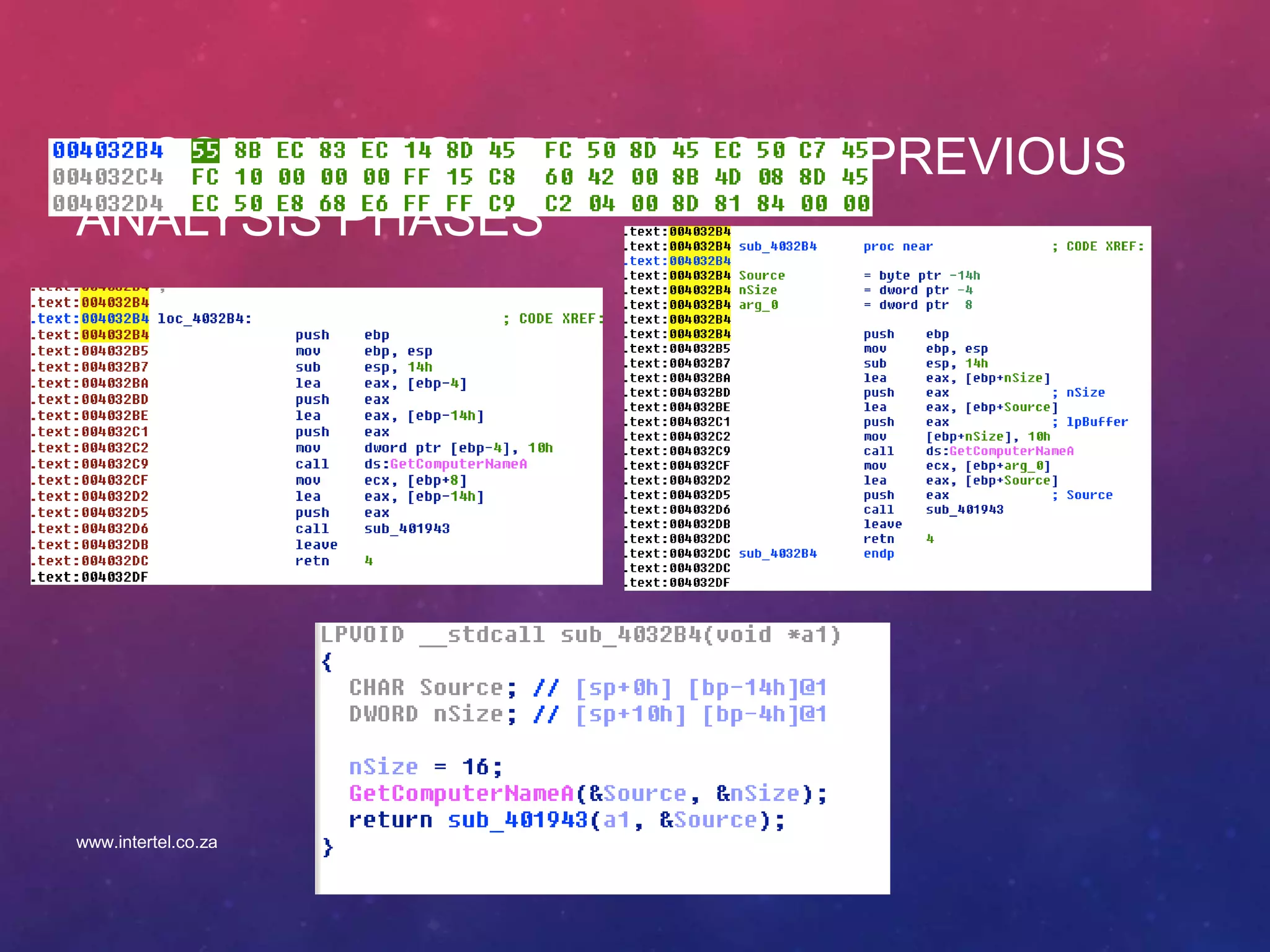
![TYPE PROPAGATION AND MATCHING
• Type propagation using dataflow analysis
• Propagation of return values and arguments of functions
sub_403649 proc near
...
.text:00403649 arg_0 = dword ptr 8
.text:00403649 arg_4 = dword ptr 0Ch
.text:00403649 arg_8 = dword ptr 10h
.text:00403649 arg_C = dword ptr 14h
...
.text:00403668 xor ebx, ebx
...
.text:00403704 mov esi, ds:dword_40A06C
.text:0040370A push ebx ; arg 7 type(f,7) = type (ebx)
.text:0040370B mov edi, 80h
.text:00403710 push edi ; arg 6 type(f,6) = type (edi)
.text:00403711 push 4 ; arg 5 type(f,5) = union(int,char)
.text:00403713 push ebx ; arg 4 type(f,4) = type (ebx)
.text:00403714 push 2 ; arg 3 type(f,3) = union(int,char)
.text:00403716 push 2 ; arg 2 type(f,2) = union(int,char)
.text:00403718 push [ebp+arg_4] ; arg 1 type(f,1) = type([ebp+arg_4])
.text:0040371B mov [ebp+var_18], ebx
.text:0040371E call esi ; dword_40A06C type(ret(f)) = type(eax)
...
There is only one API that has
7 arguments such that the seventh
and third and first one can be
pointers and all others are not.
HANDLE WINAPI CreateFile(
__in LPCTSTR lpFileName,
__in DWORD dwDesiredAccess,
__in DWORD dwShareMode,
__in LPSECURITY_ATTRIBUTES lpSecurityAttributes,
__in DWORD dwCreationDisposition,
__in DWORD dwFlagsAndAttributes,
__in HANDLE hTemplateFile
);
www.intertel.co.za](https://image.slidesharecdn.com/malware-presentation-2-160305112124/75/Reverse-Engineering-Malware-A-Practical-Guide-40-2048.jpg)