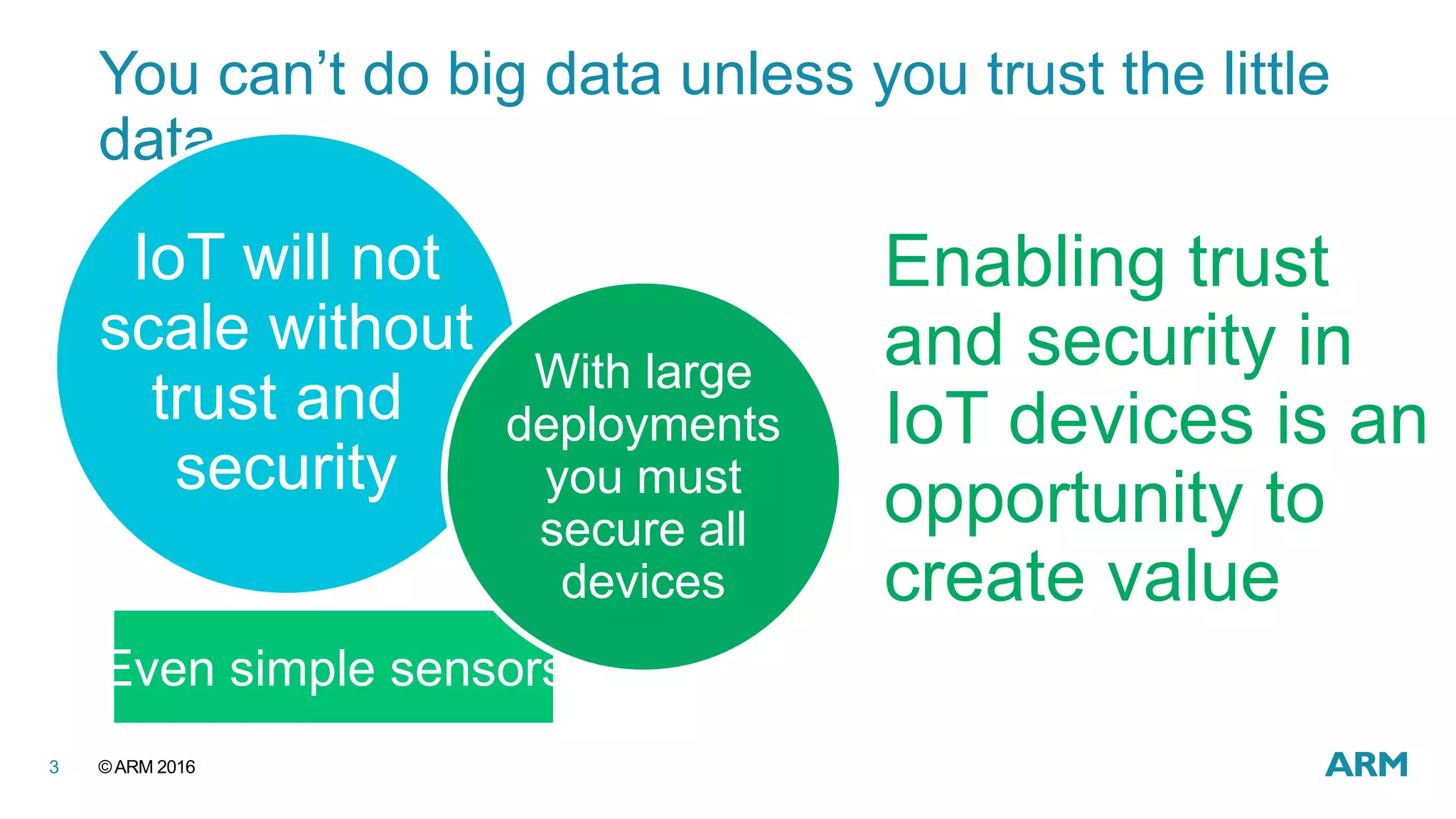
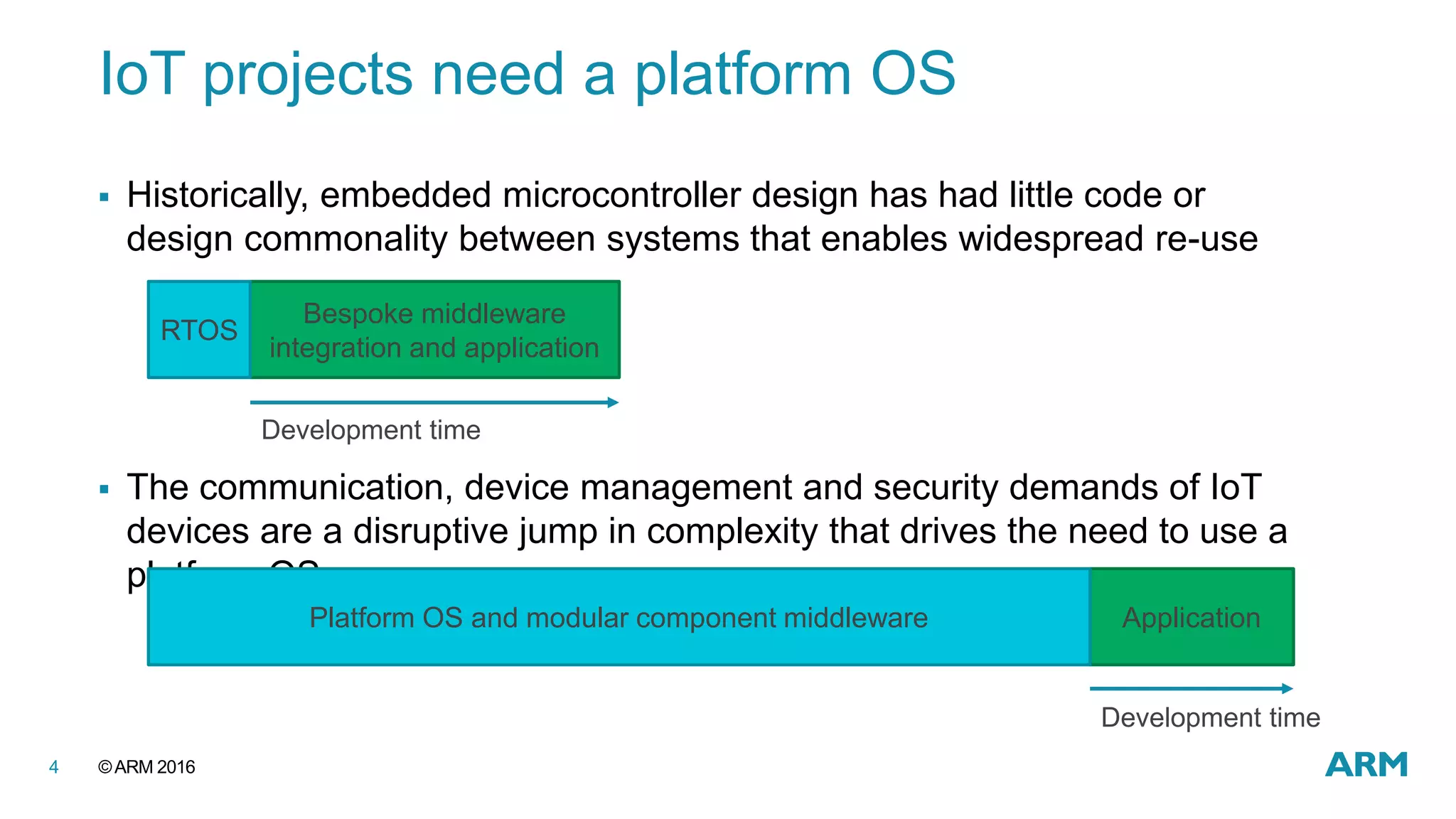
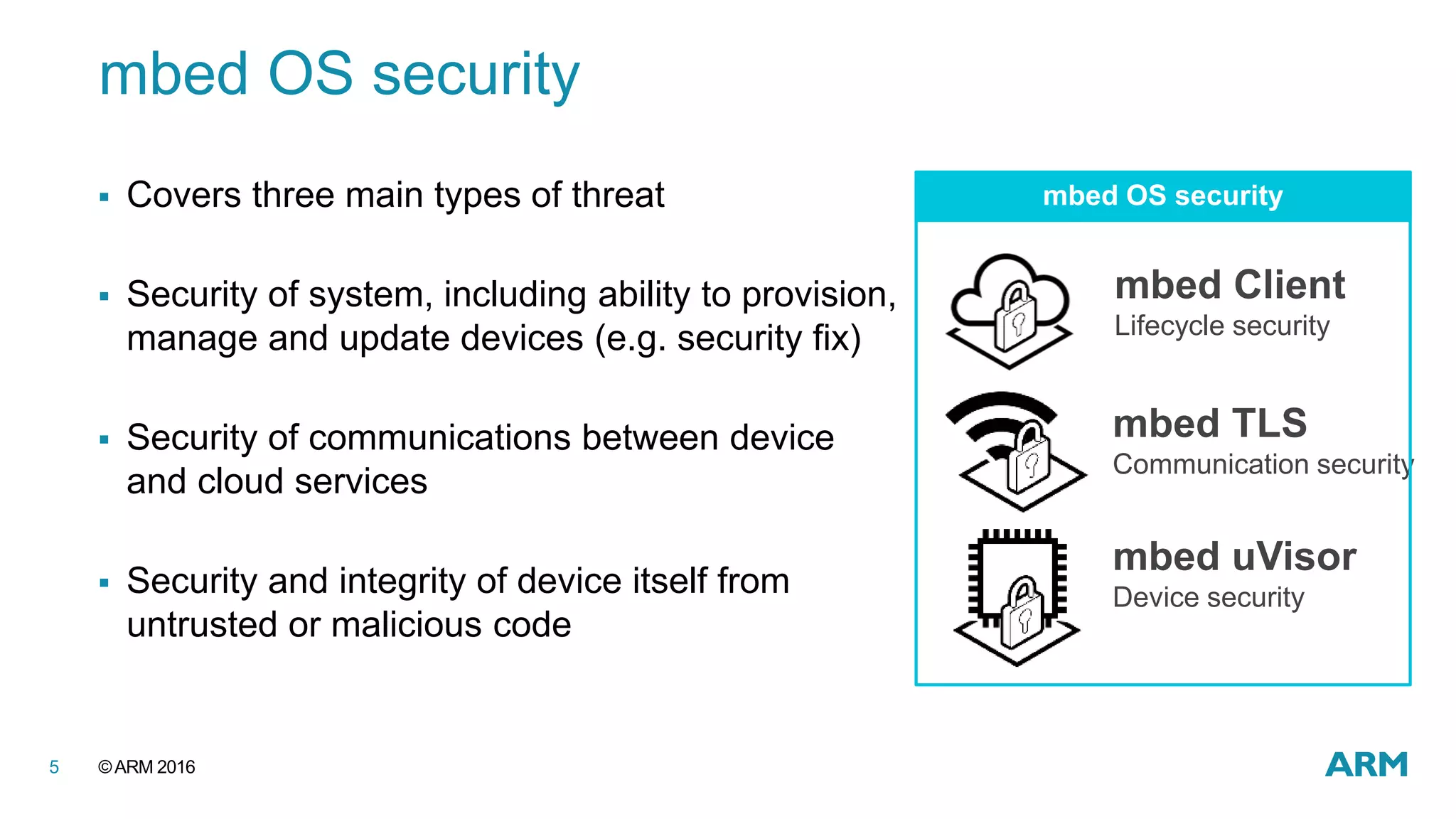
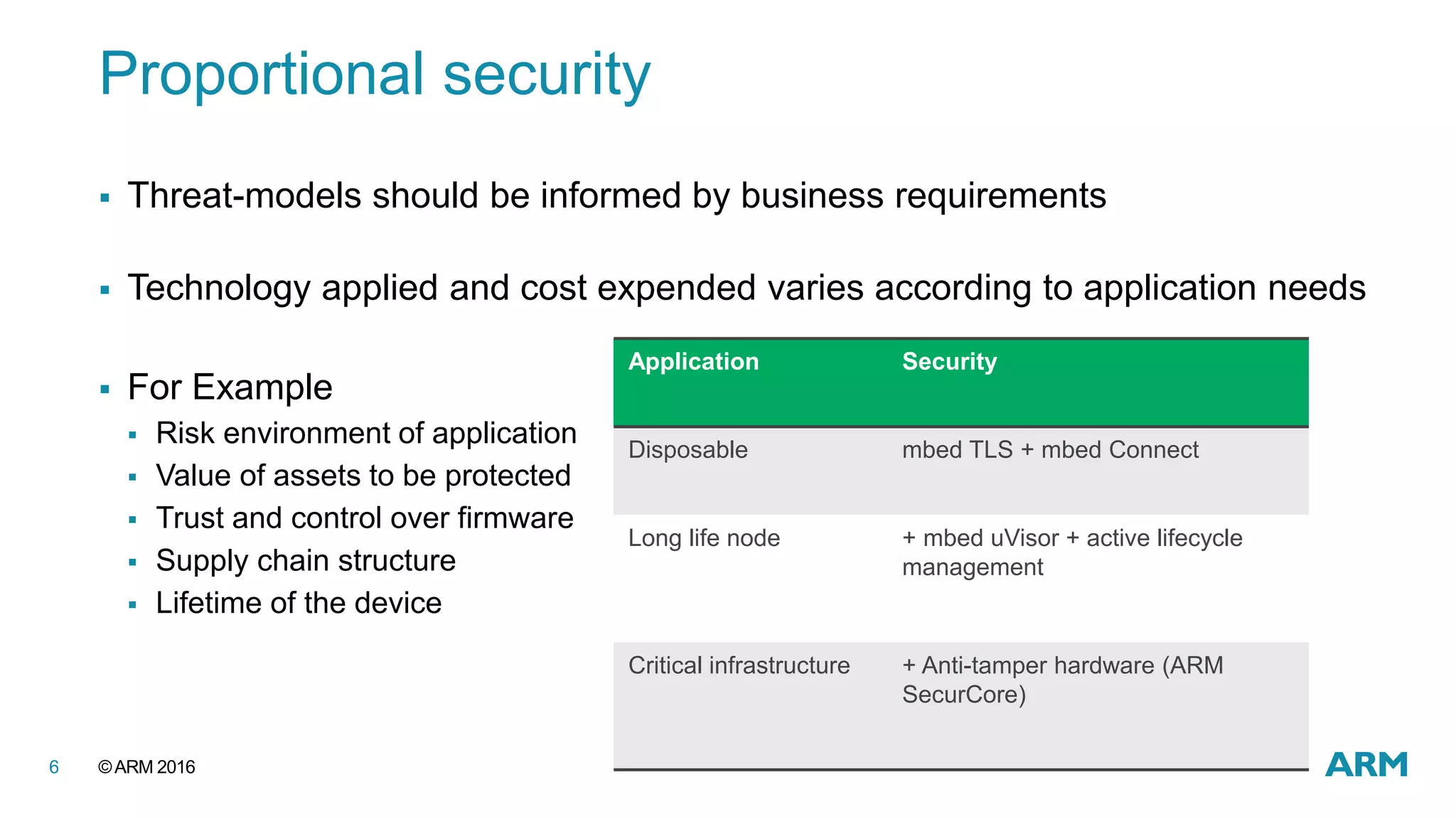
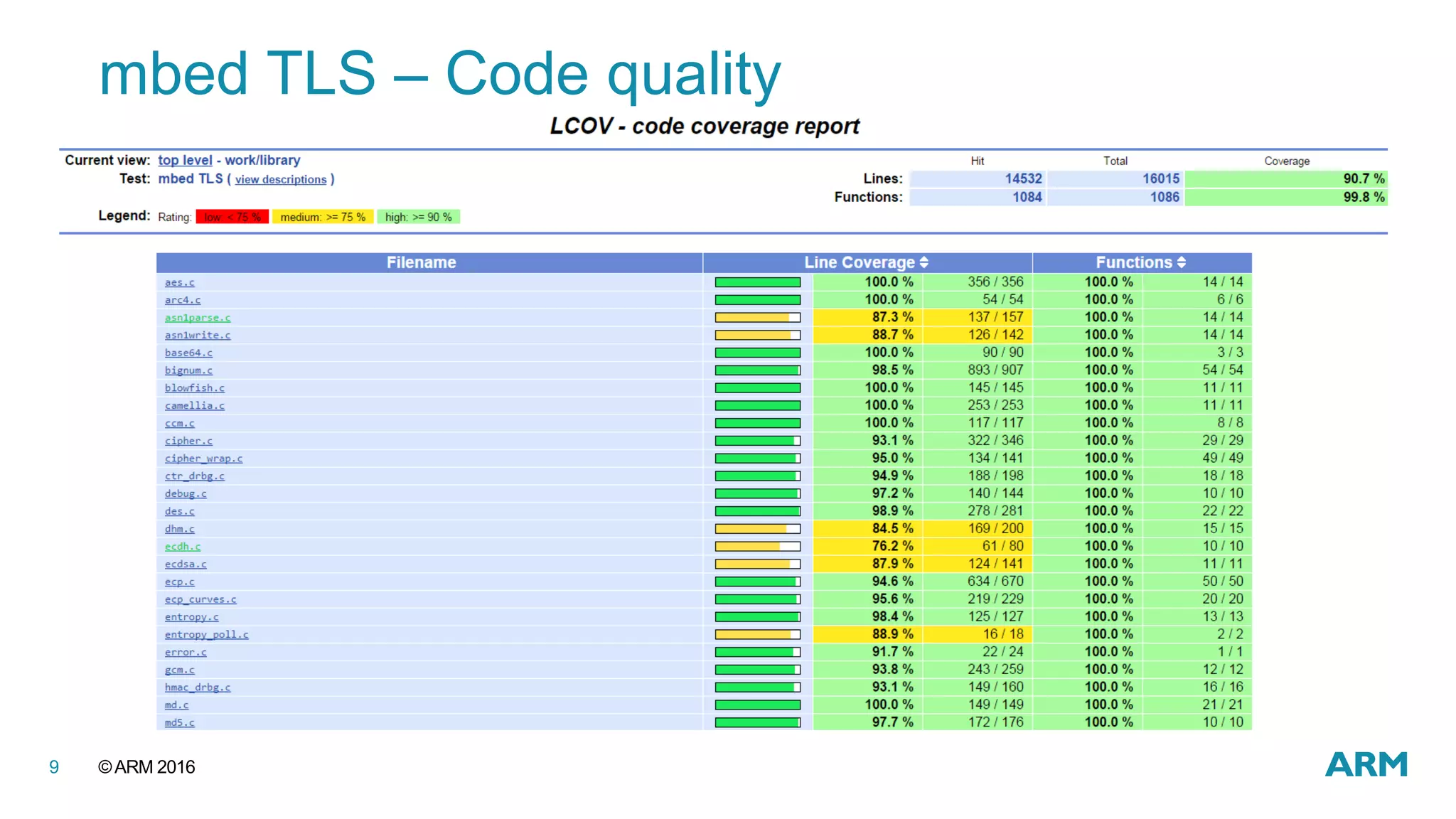
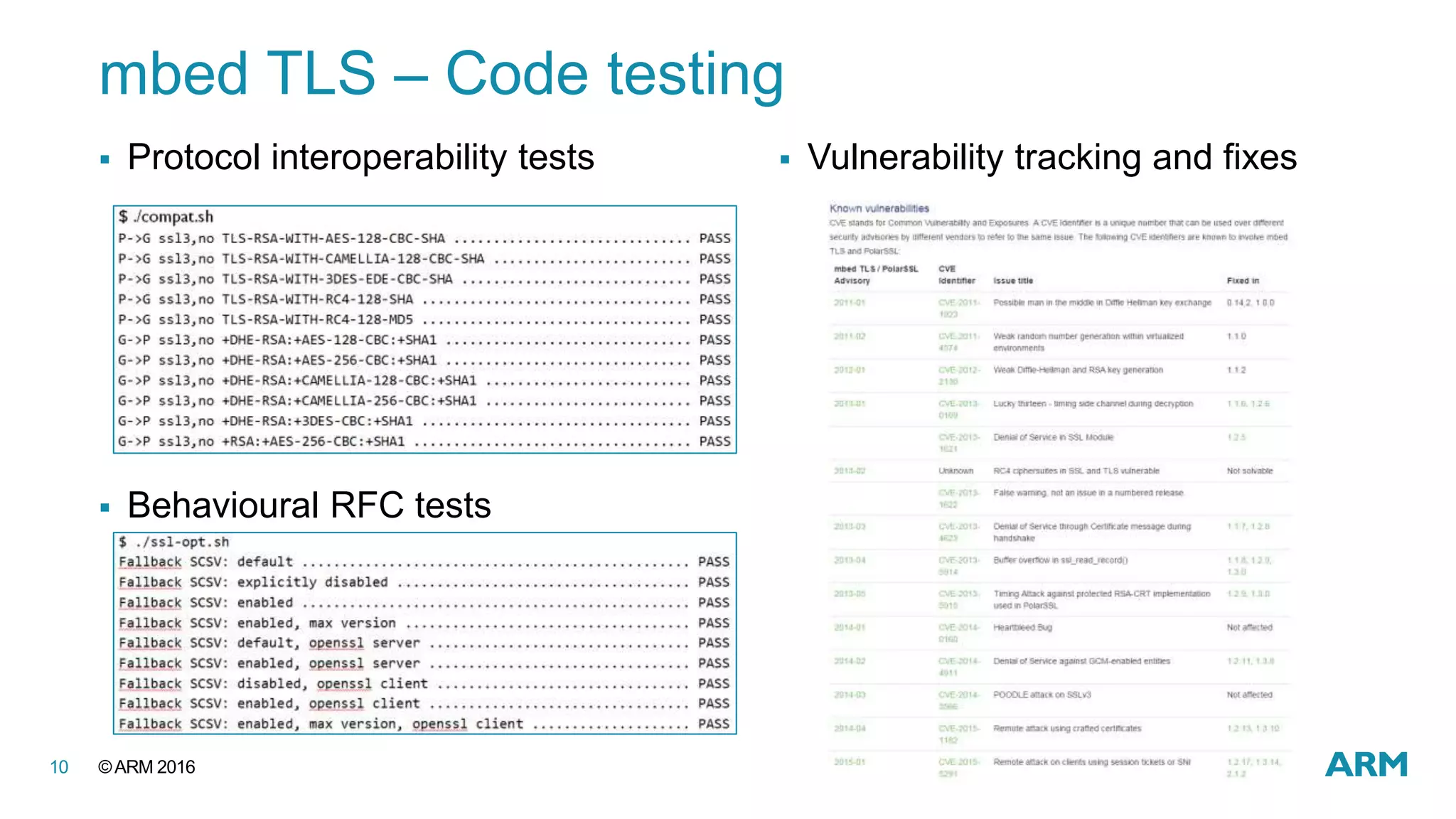
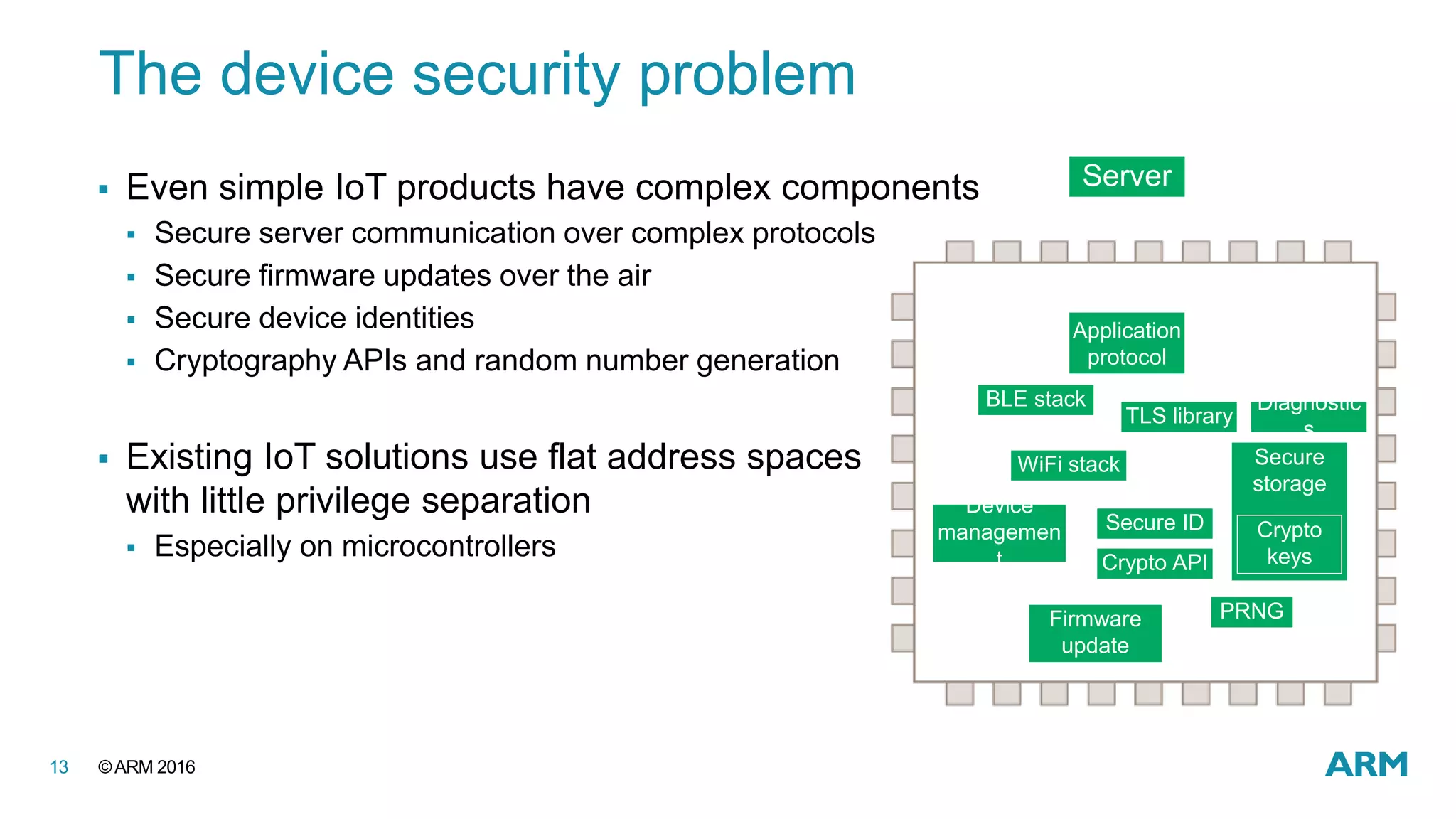
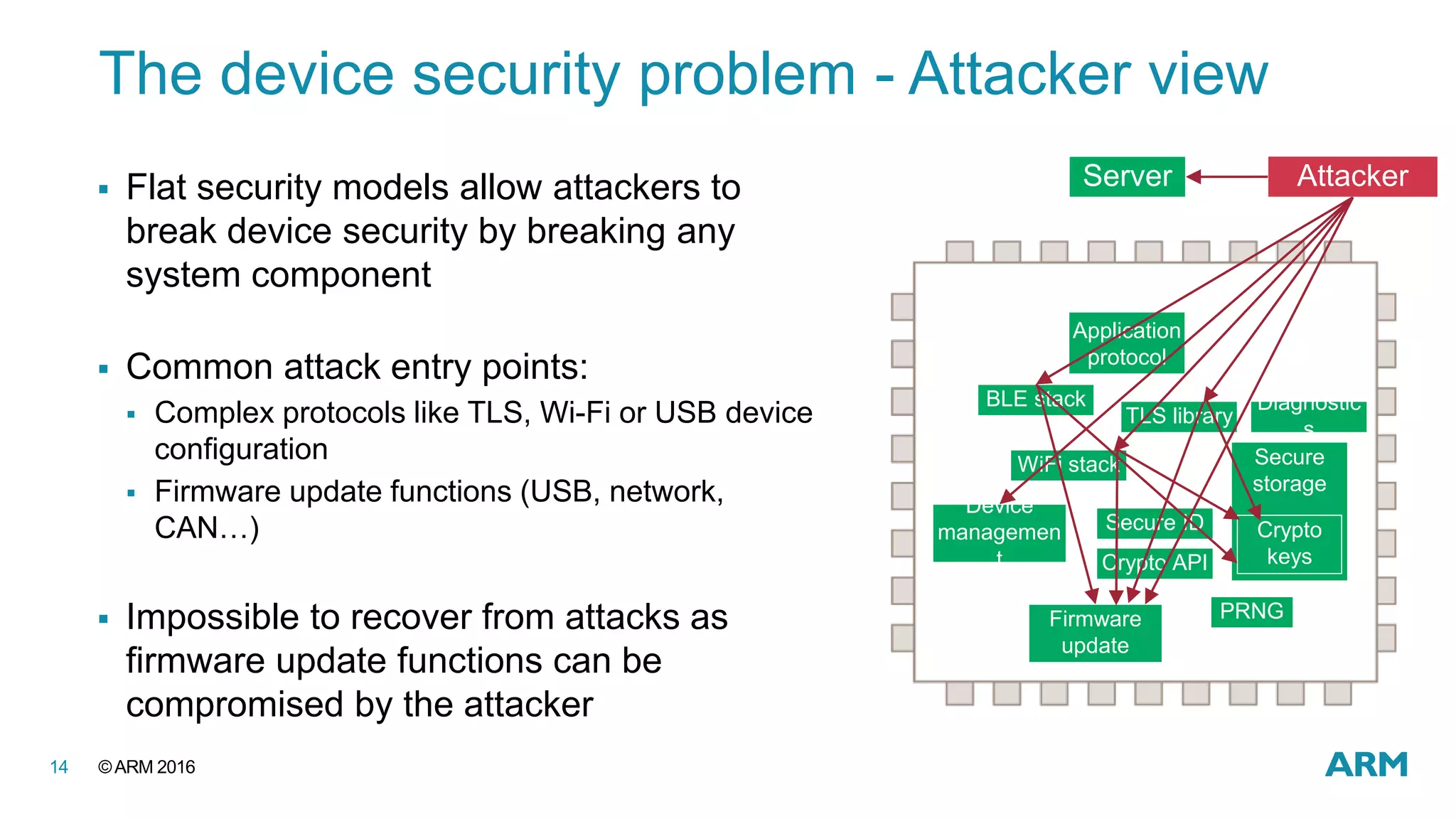
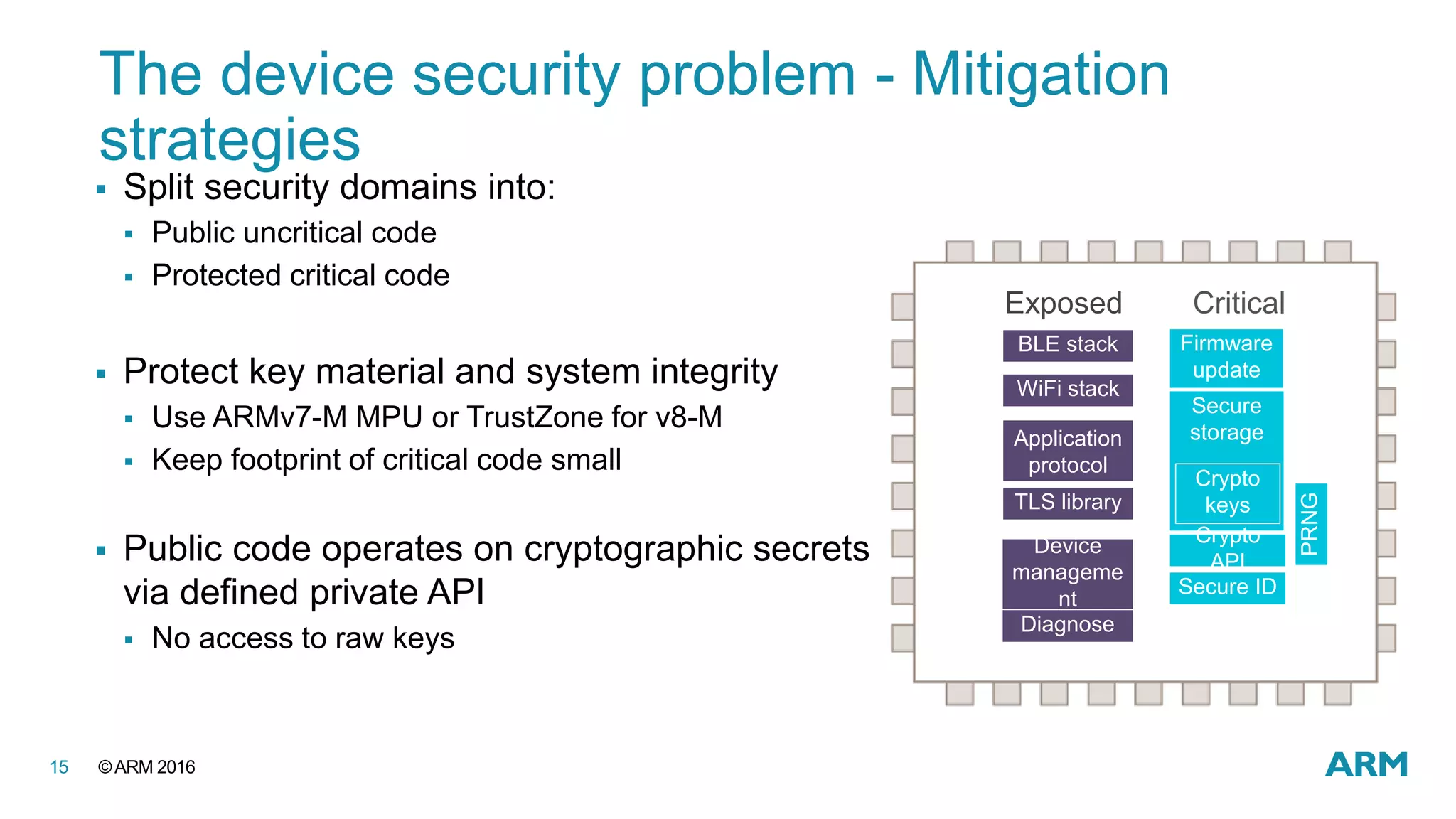
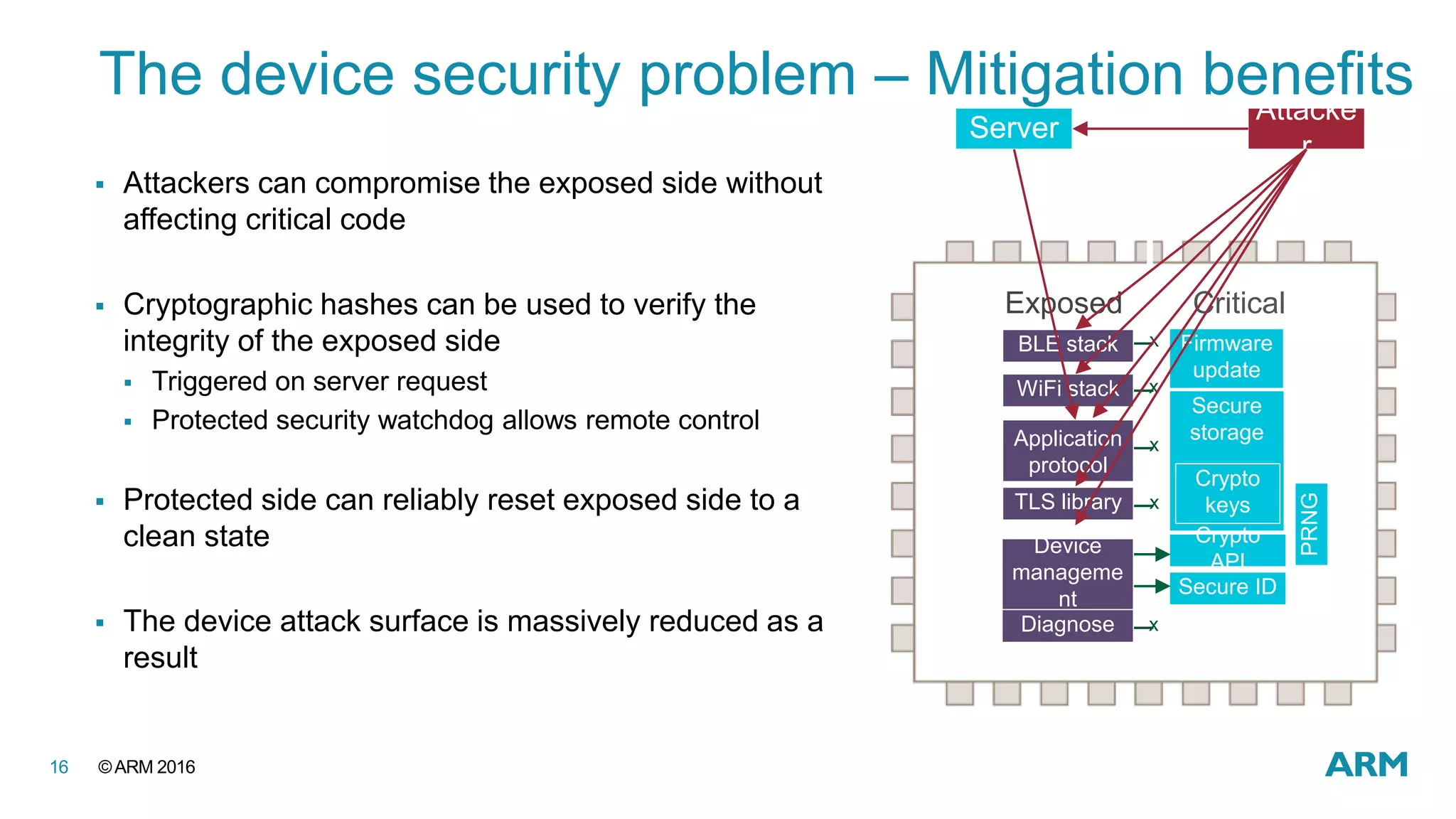
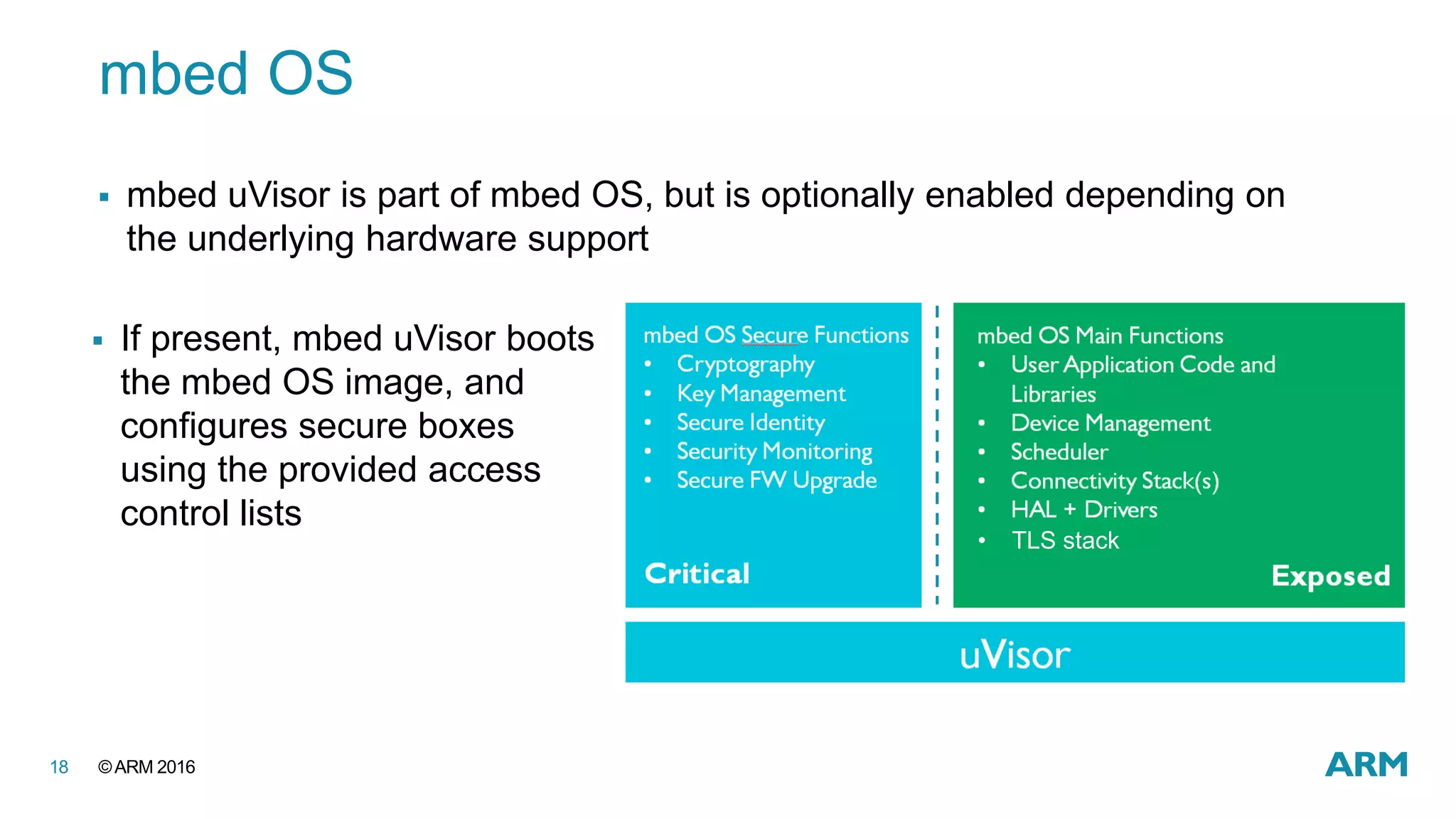
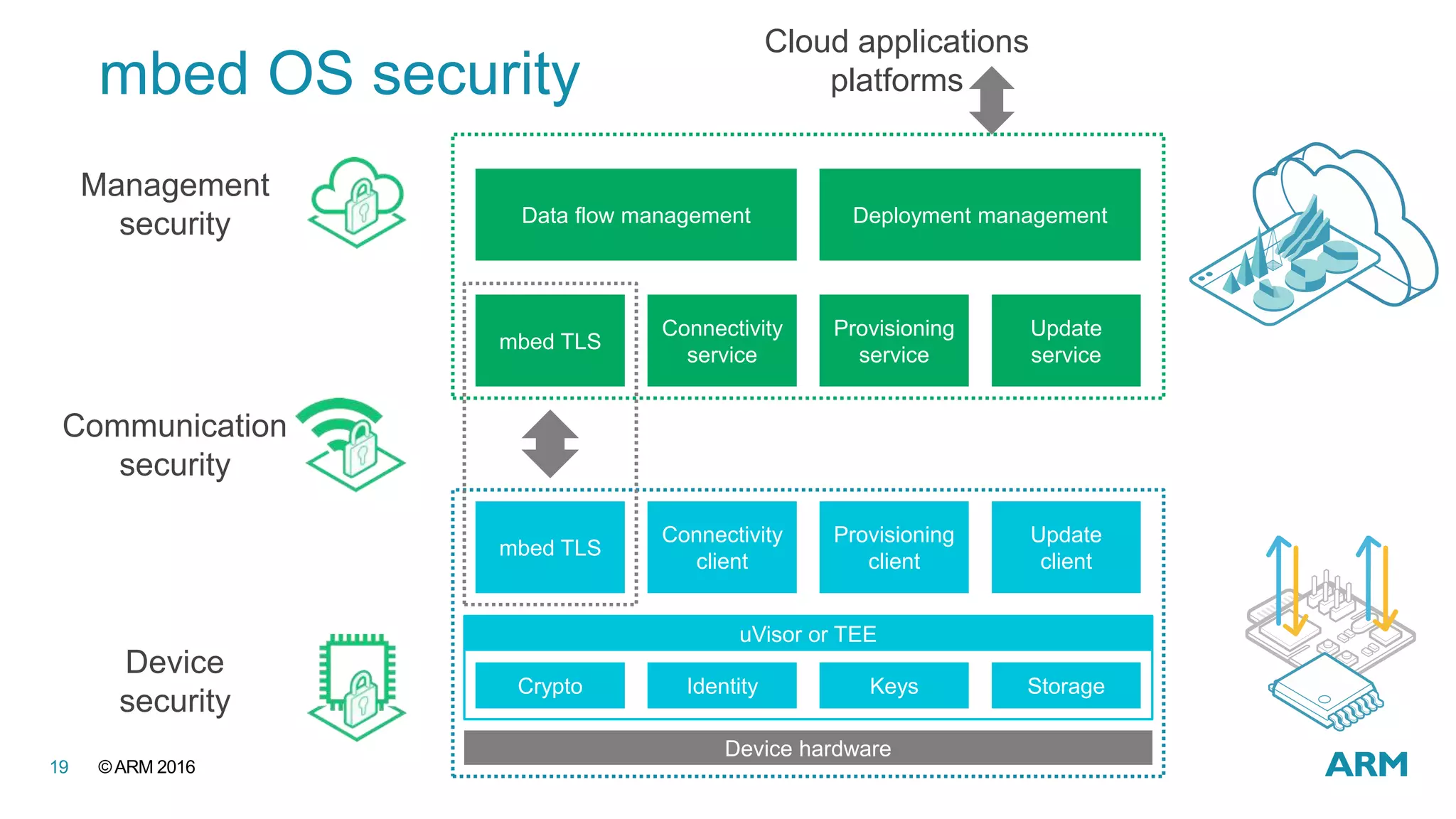
This document discusses securing IoT devices using the mbed ecosystem. It notes that IoT security is an important issue as vulnerabilities have been found in deployed systems. The mbed OS provides security for IoT devices through mbed TLS for secure communications, mbed uVisor for device security through isolation, and lifecycle management features. It argues that a platform OS like mbed OS is needed to address the complex security demands of IoT. The document outlines the security features and benefits provided by mbed TLS, mbed uVisor, and how they integrate with mbed OS to deliver comprehensive security for IoT products.