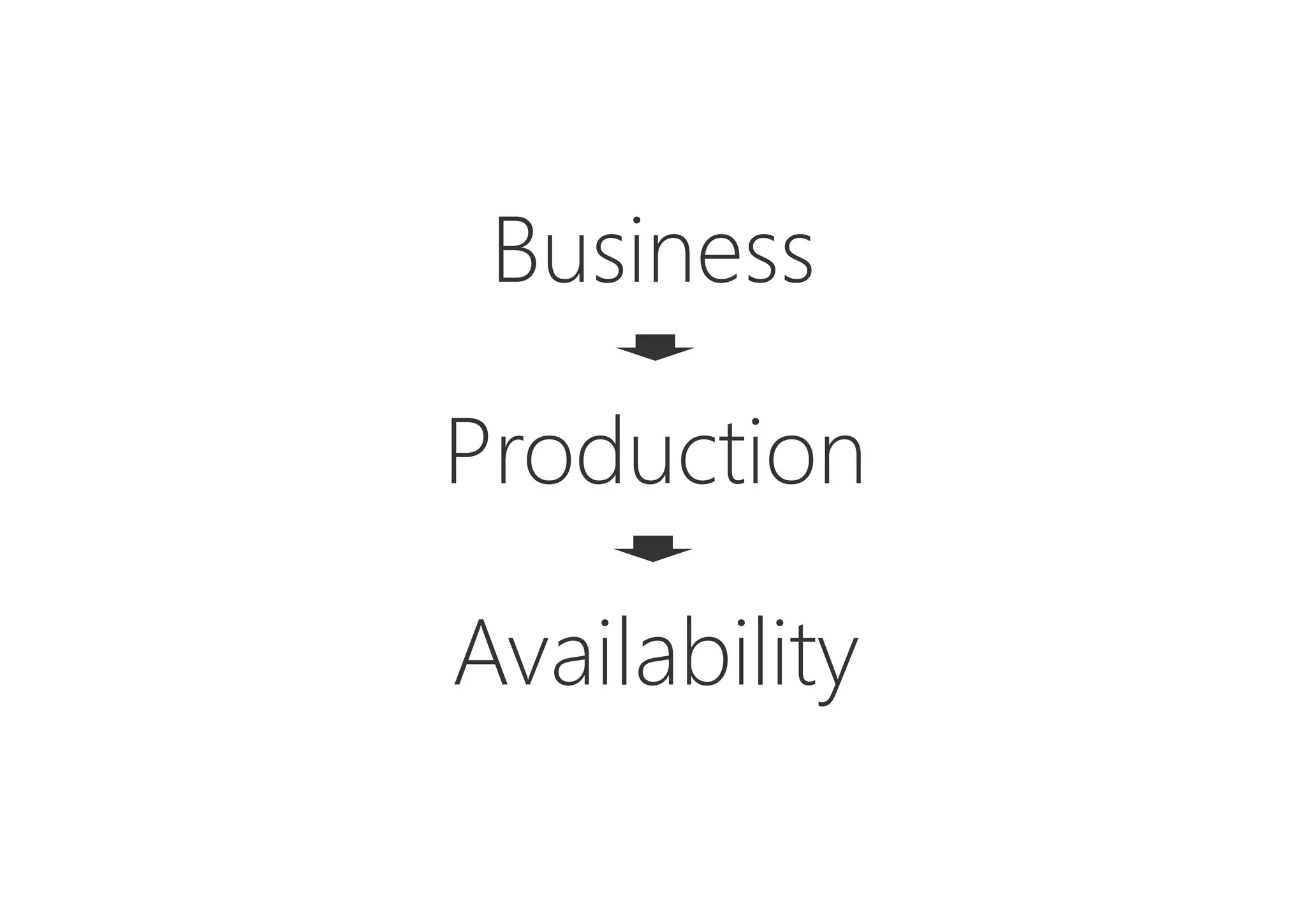
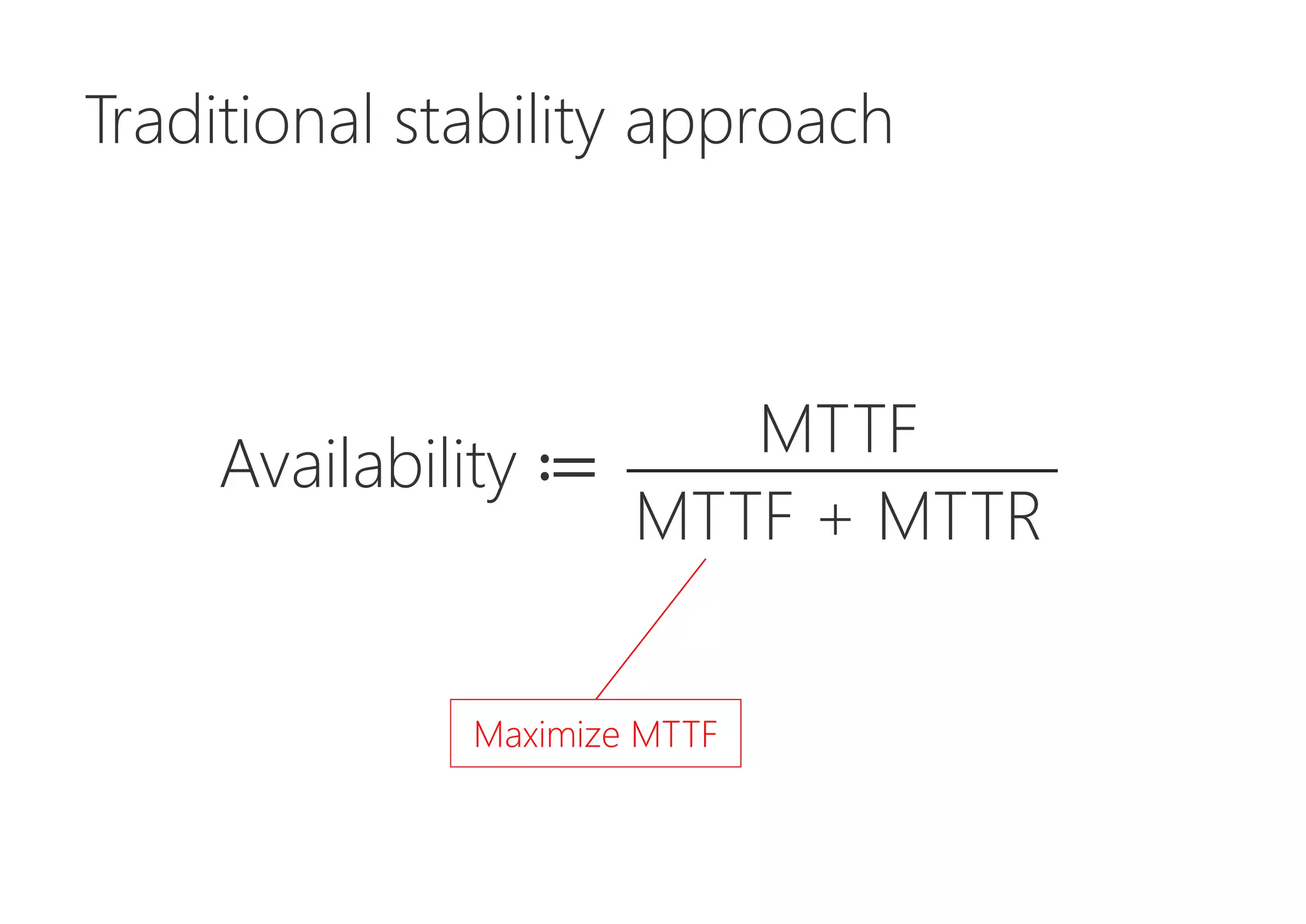
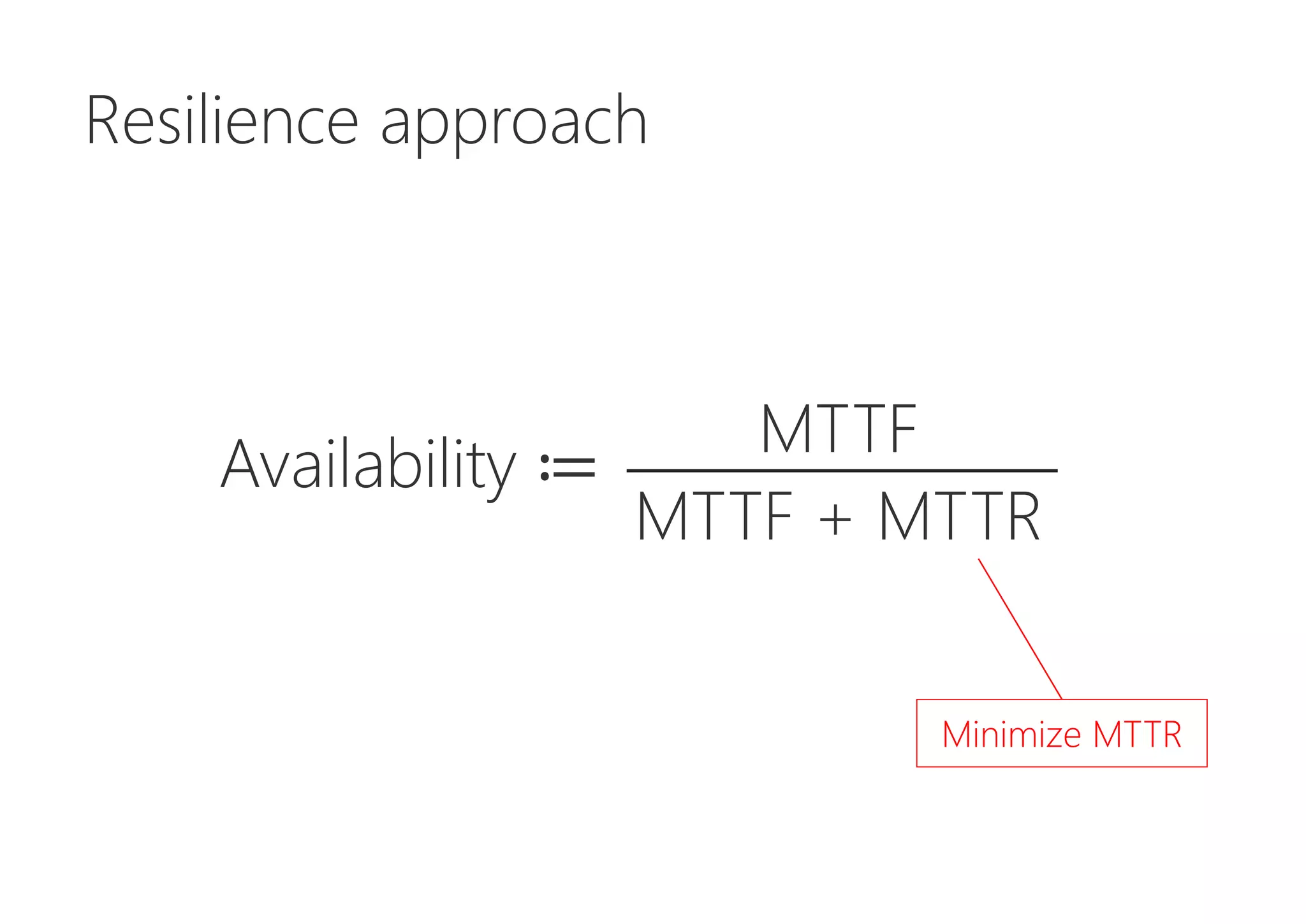
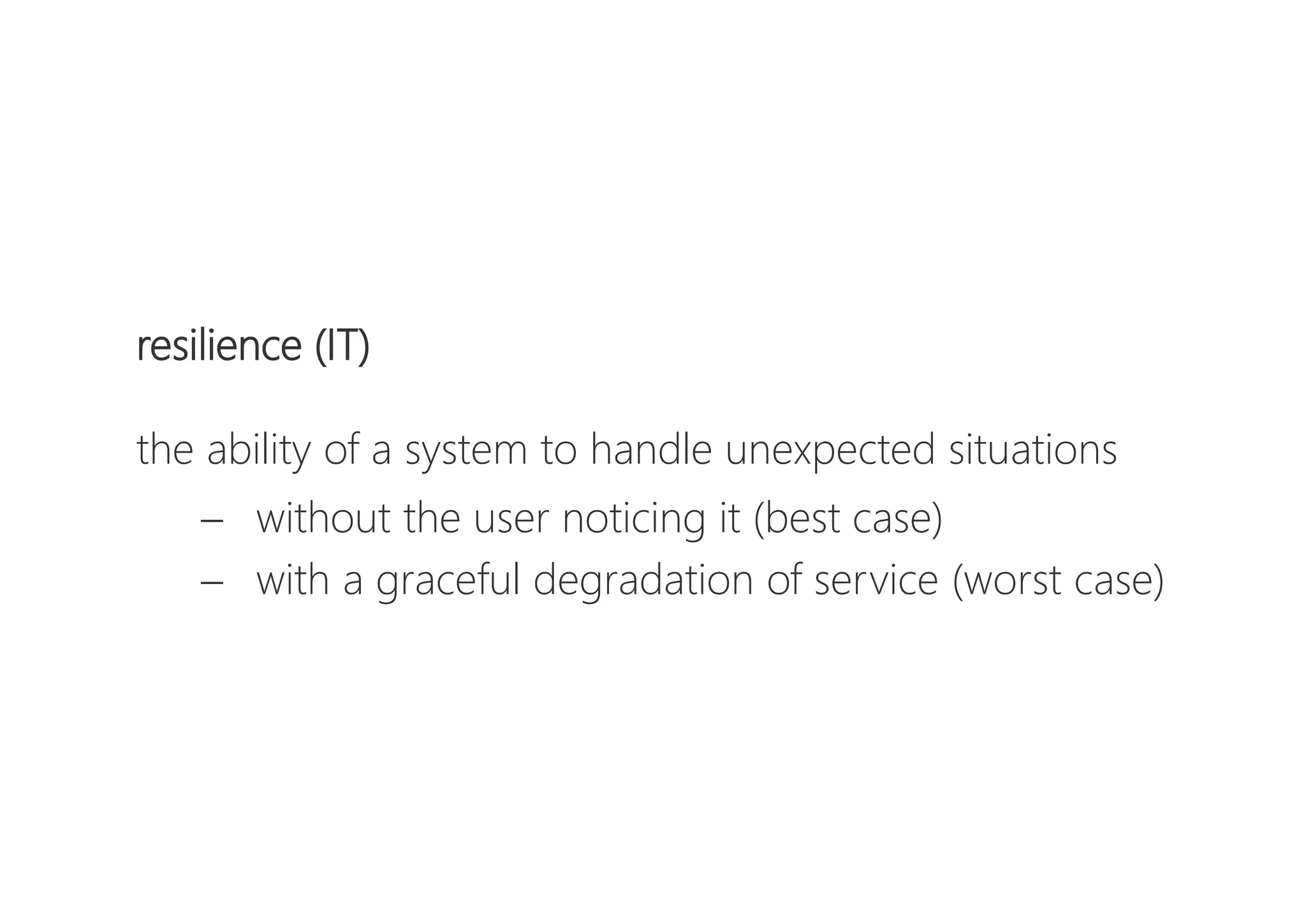
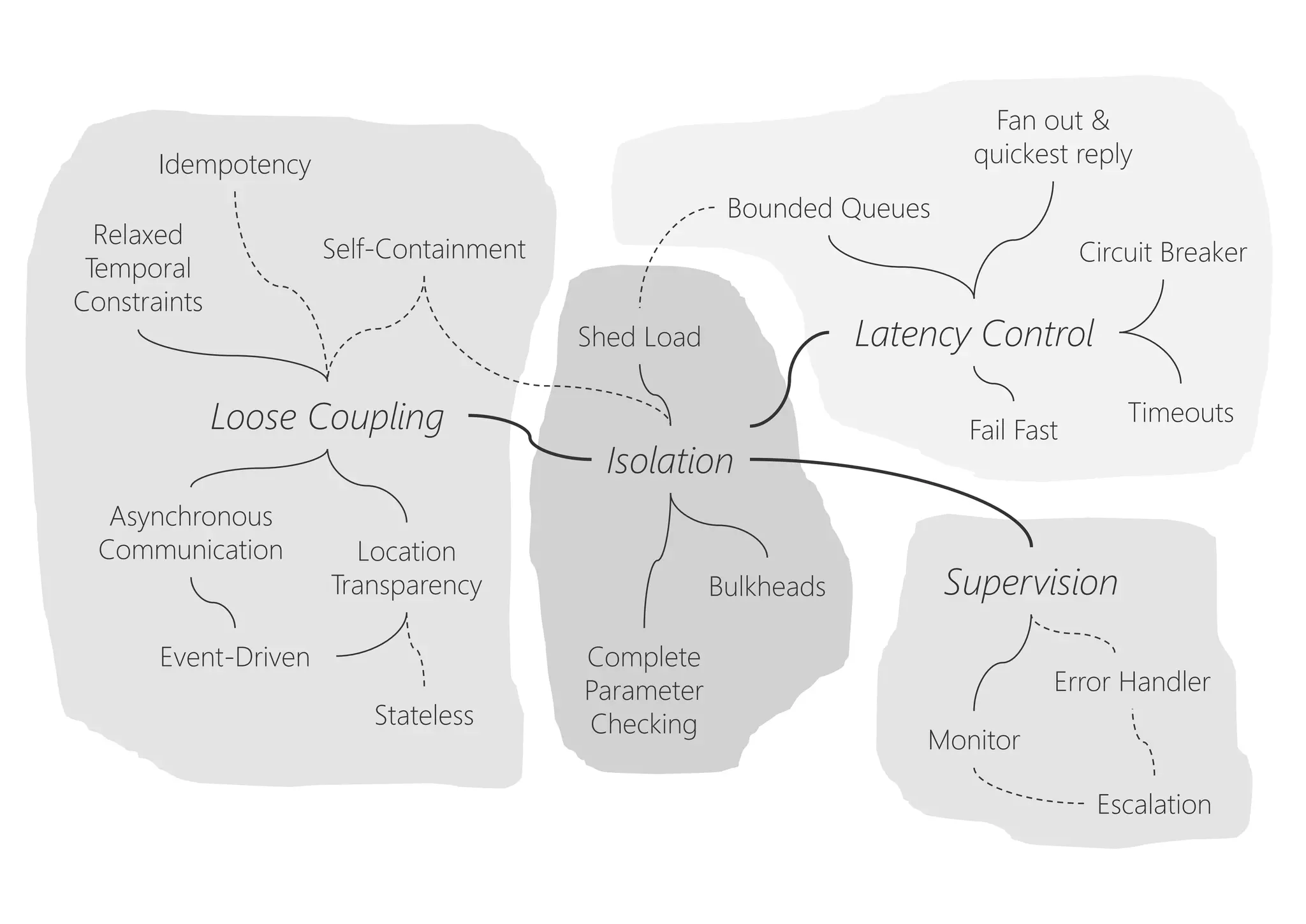
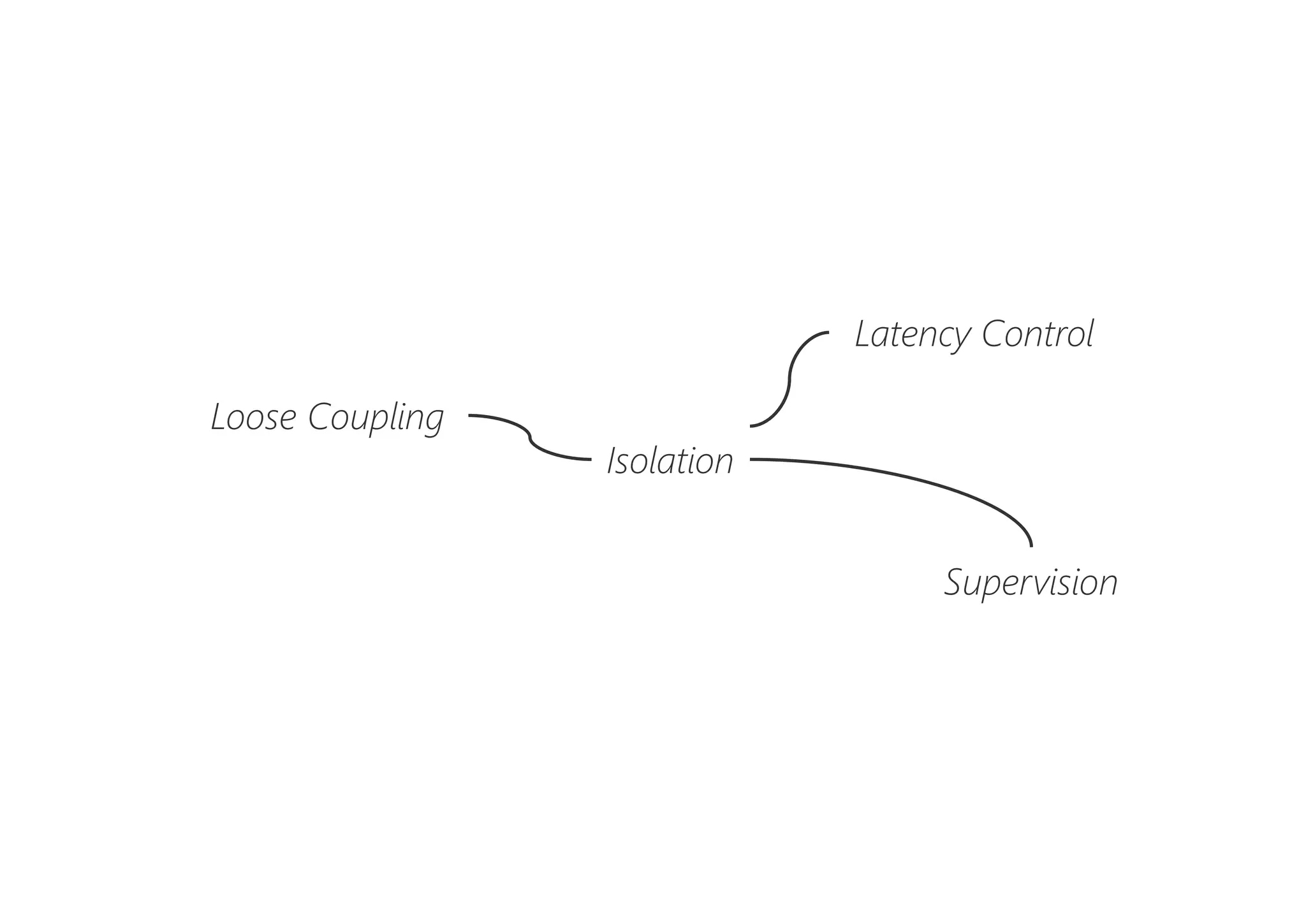
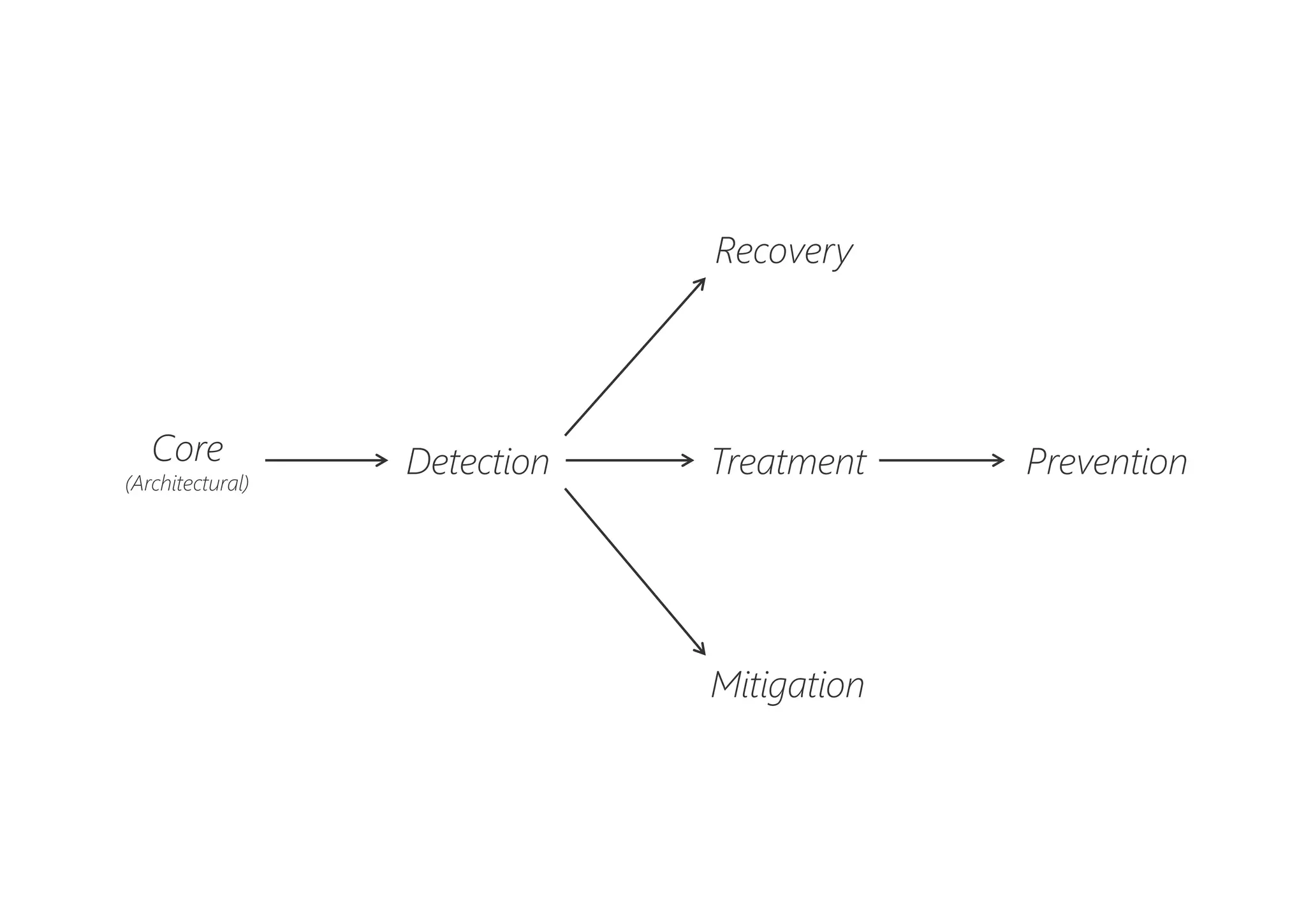
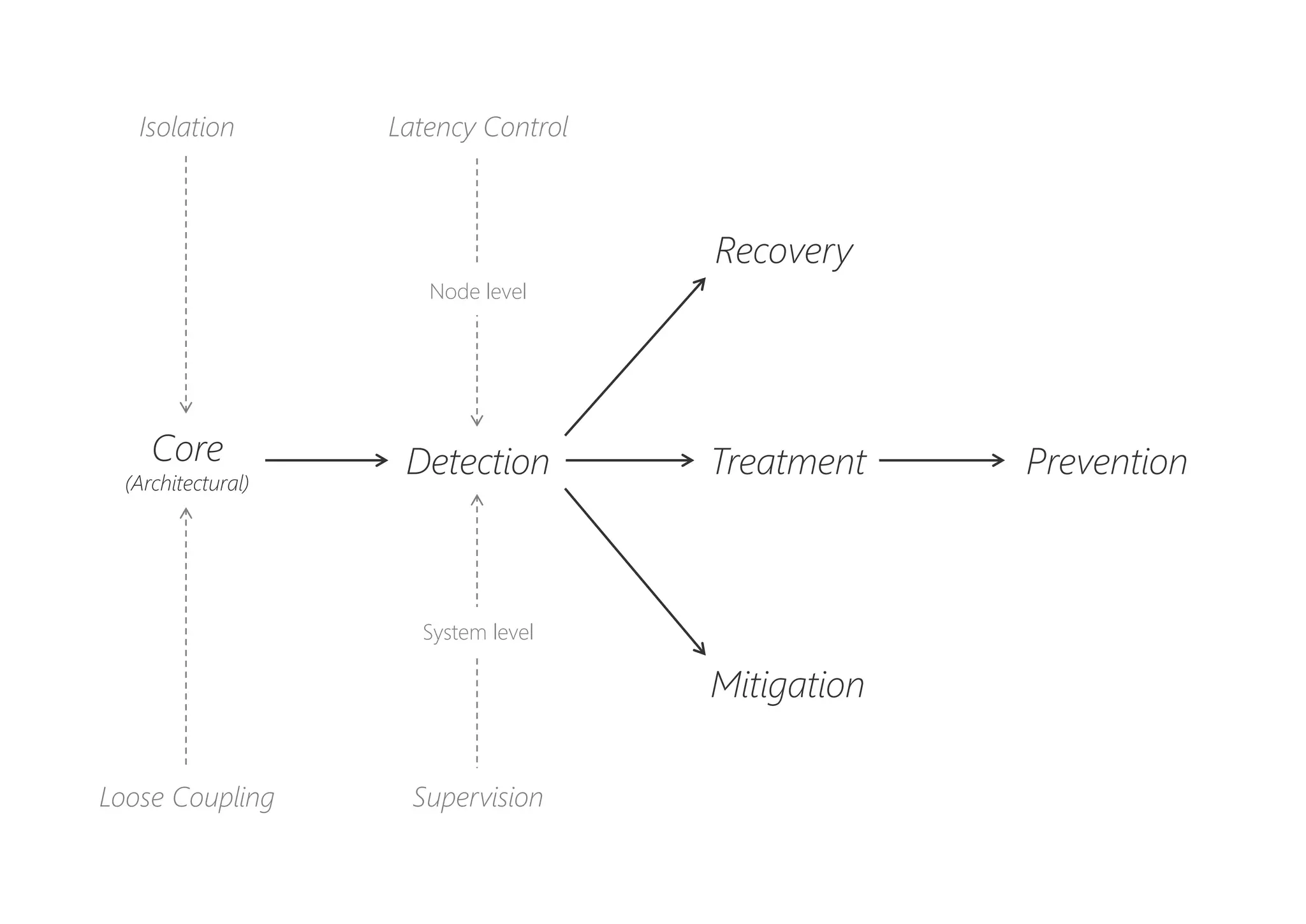
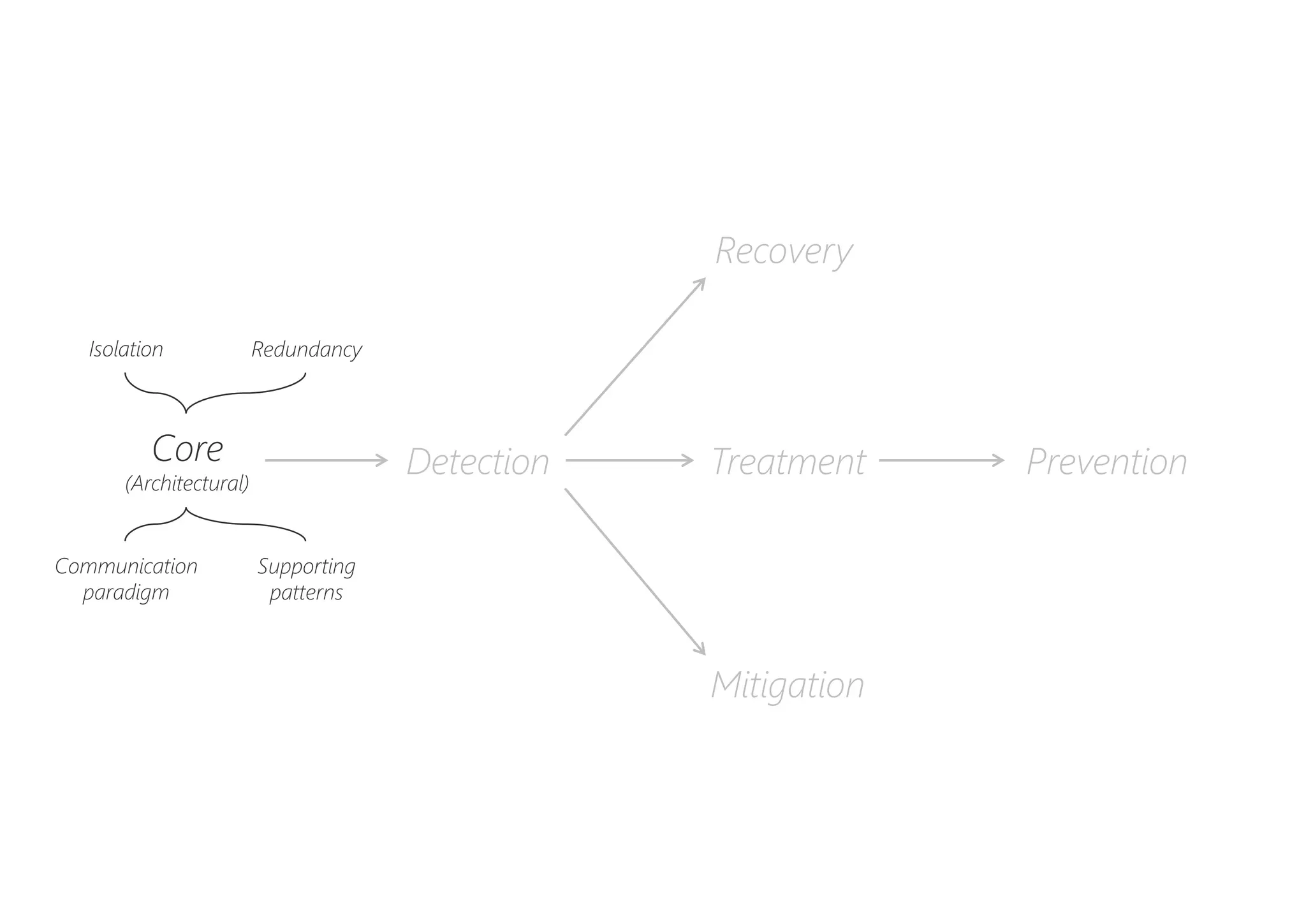
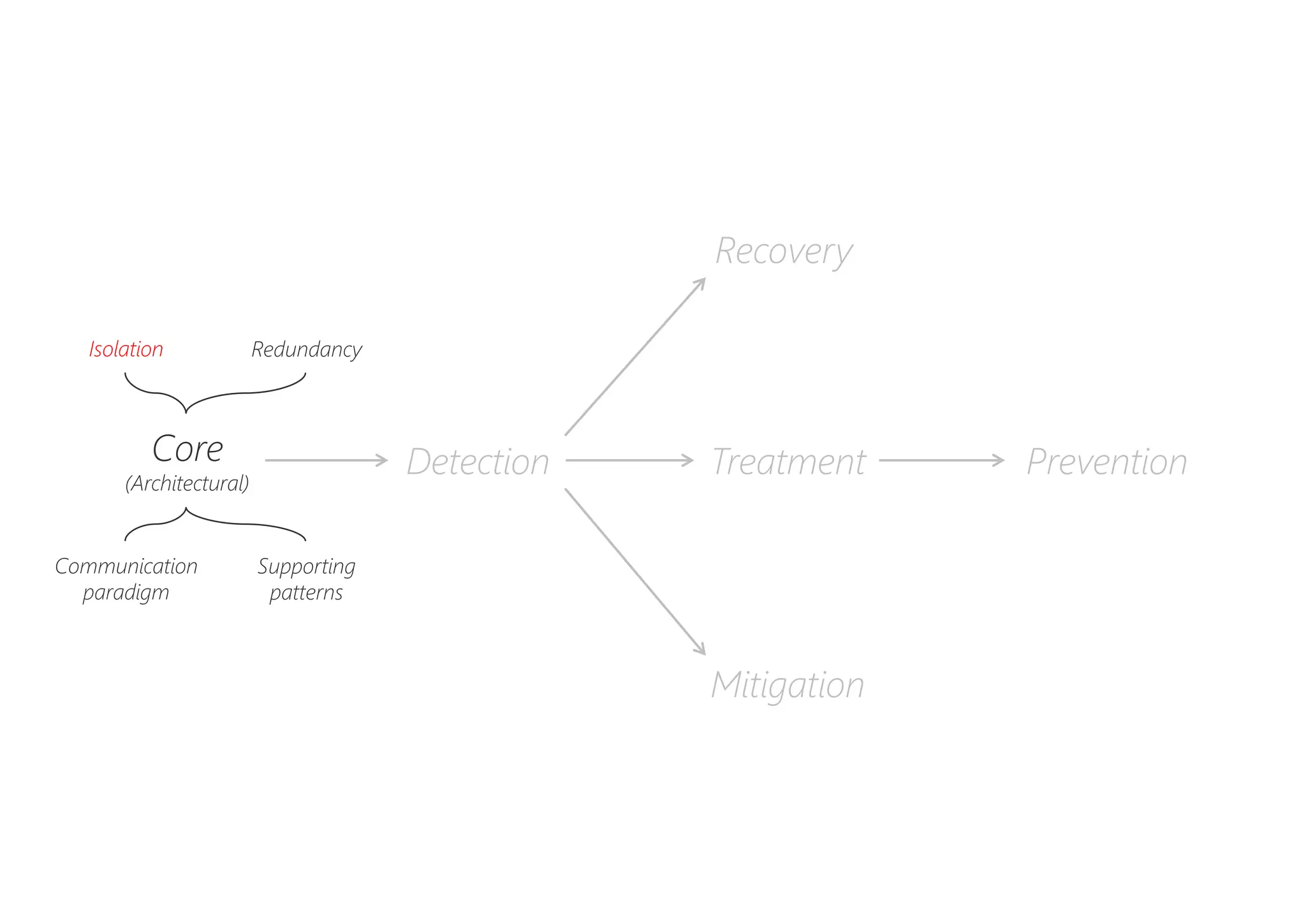
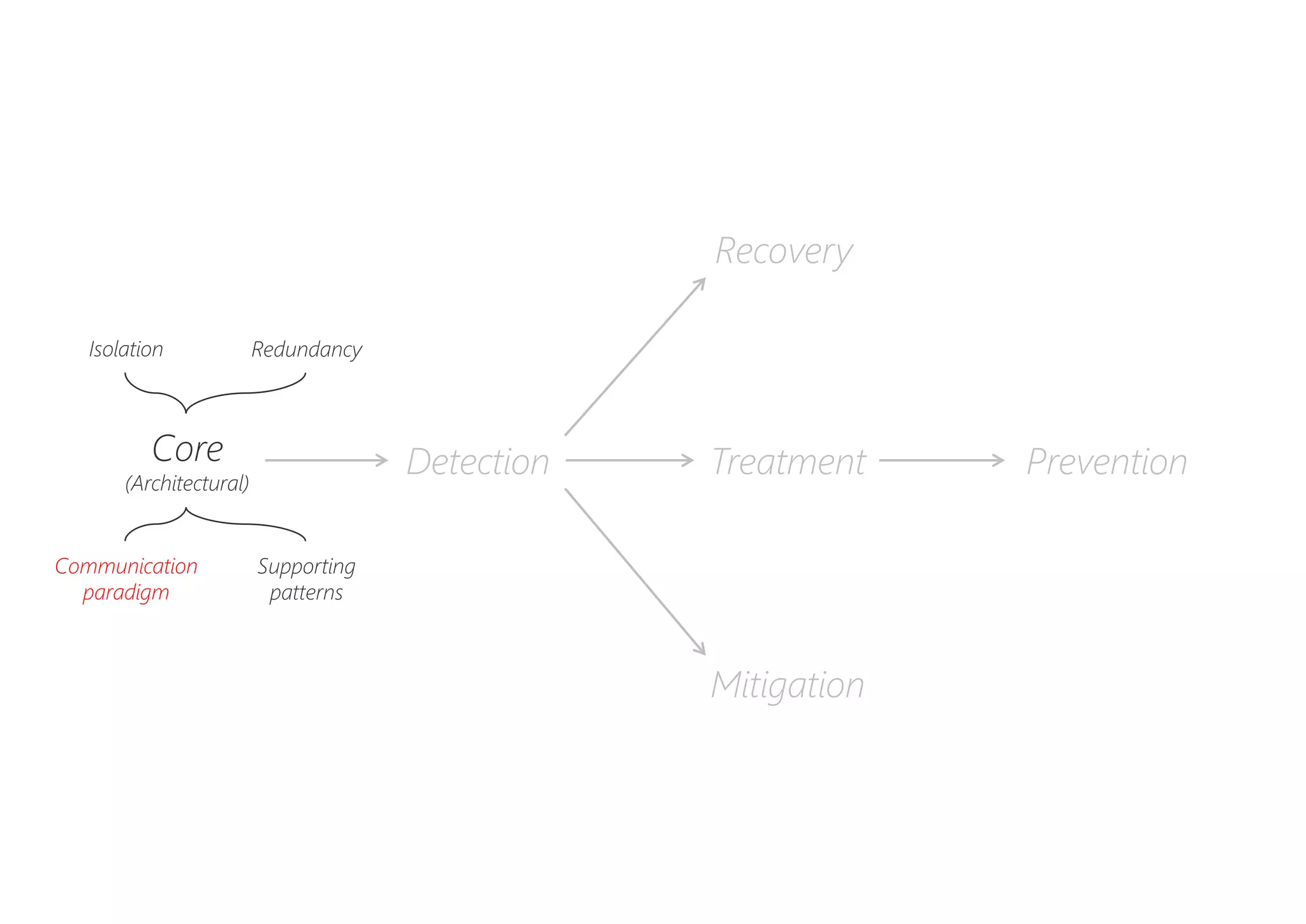
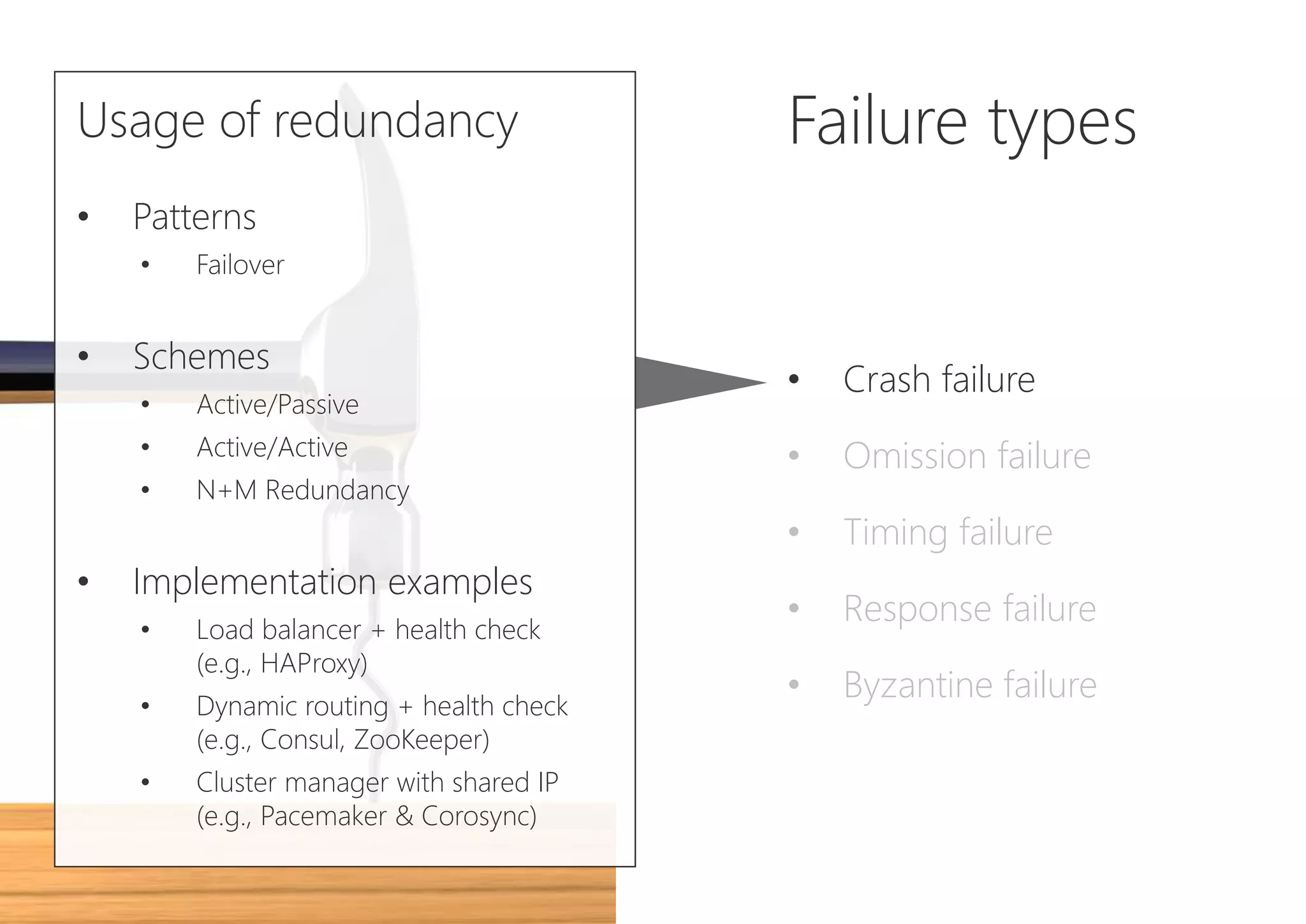
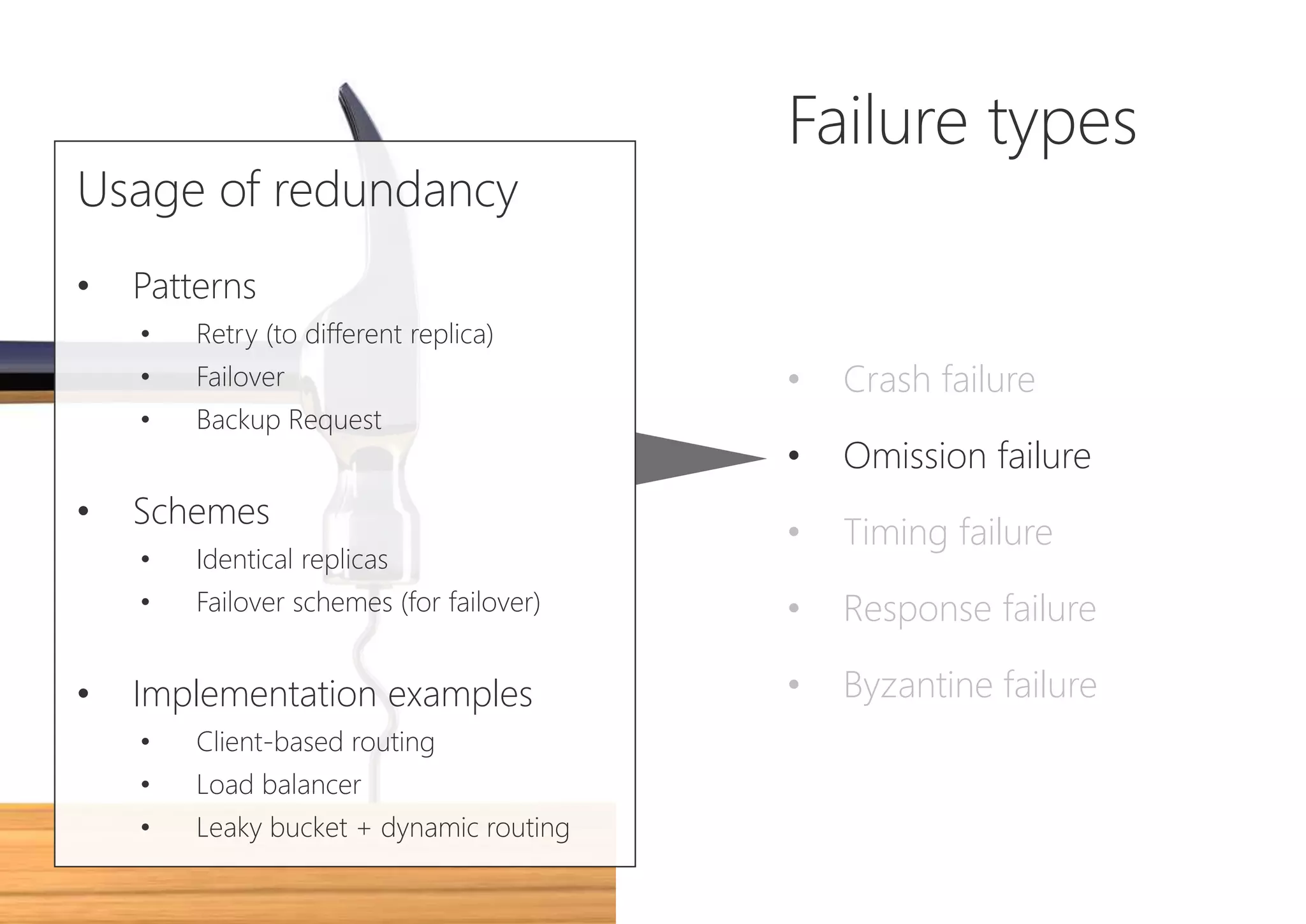
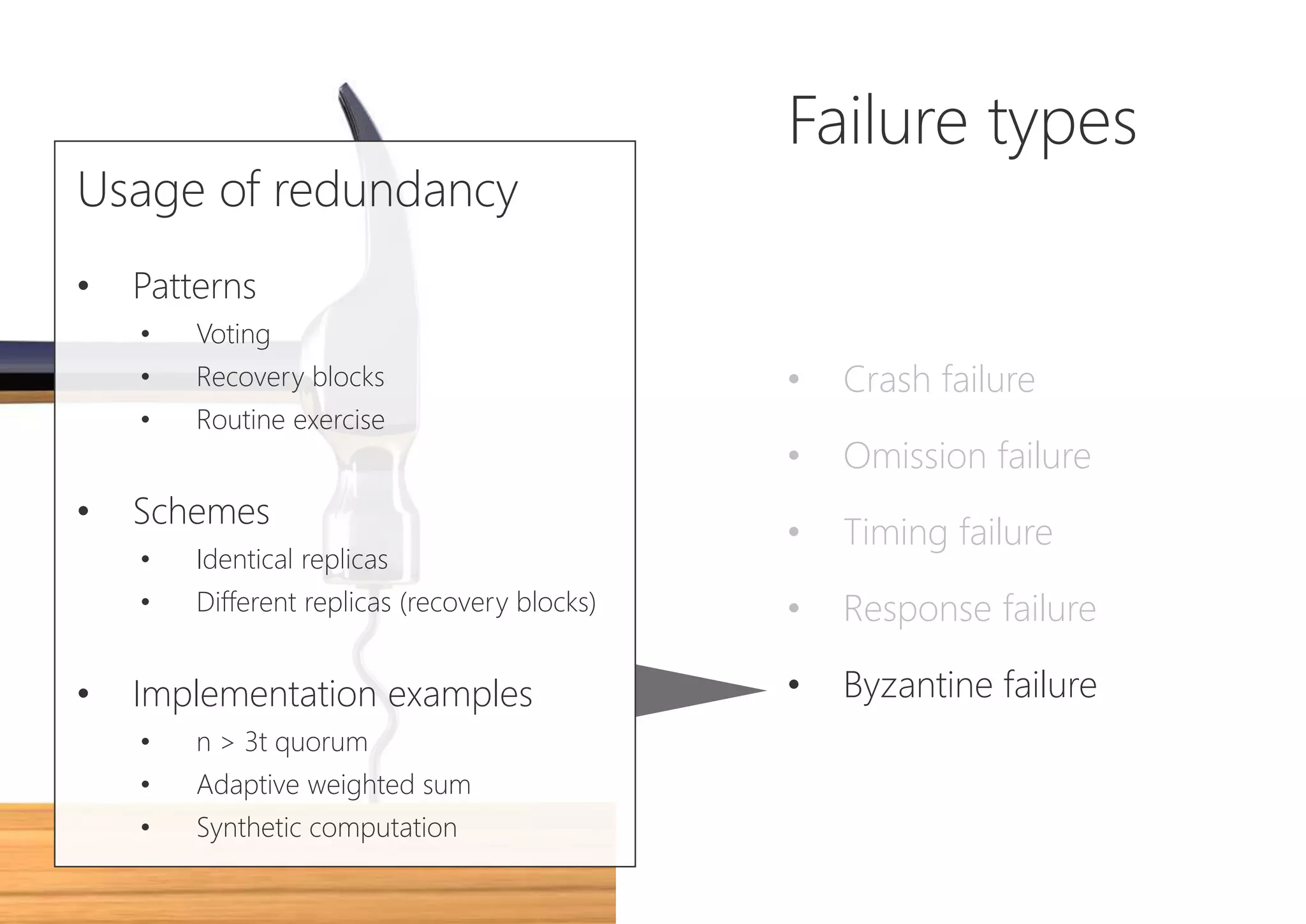
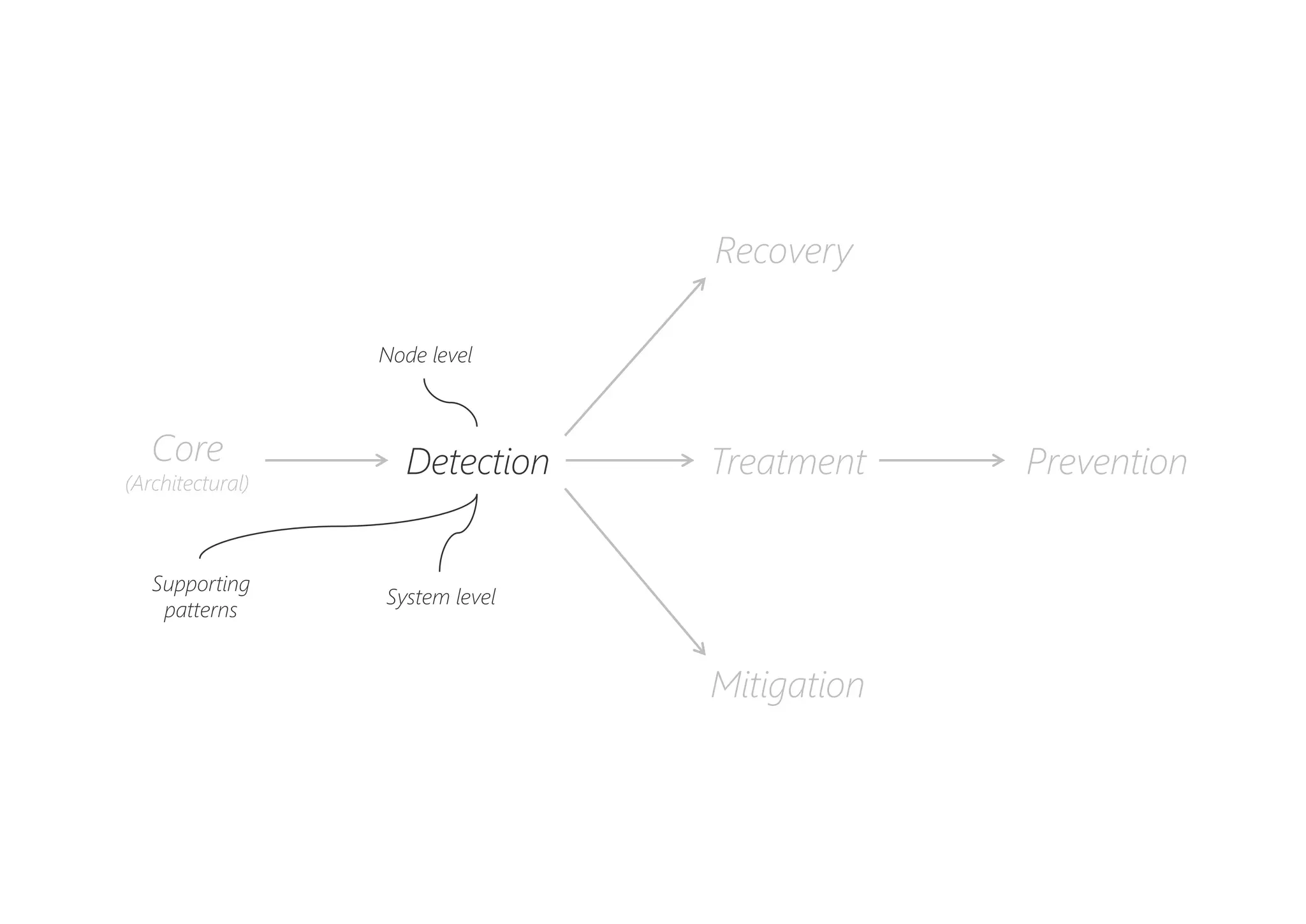
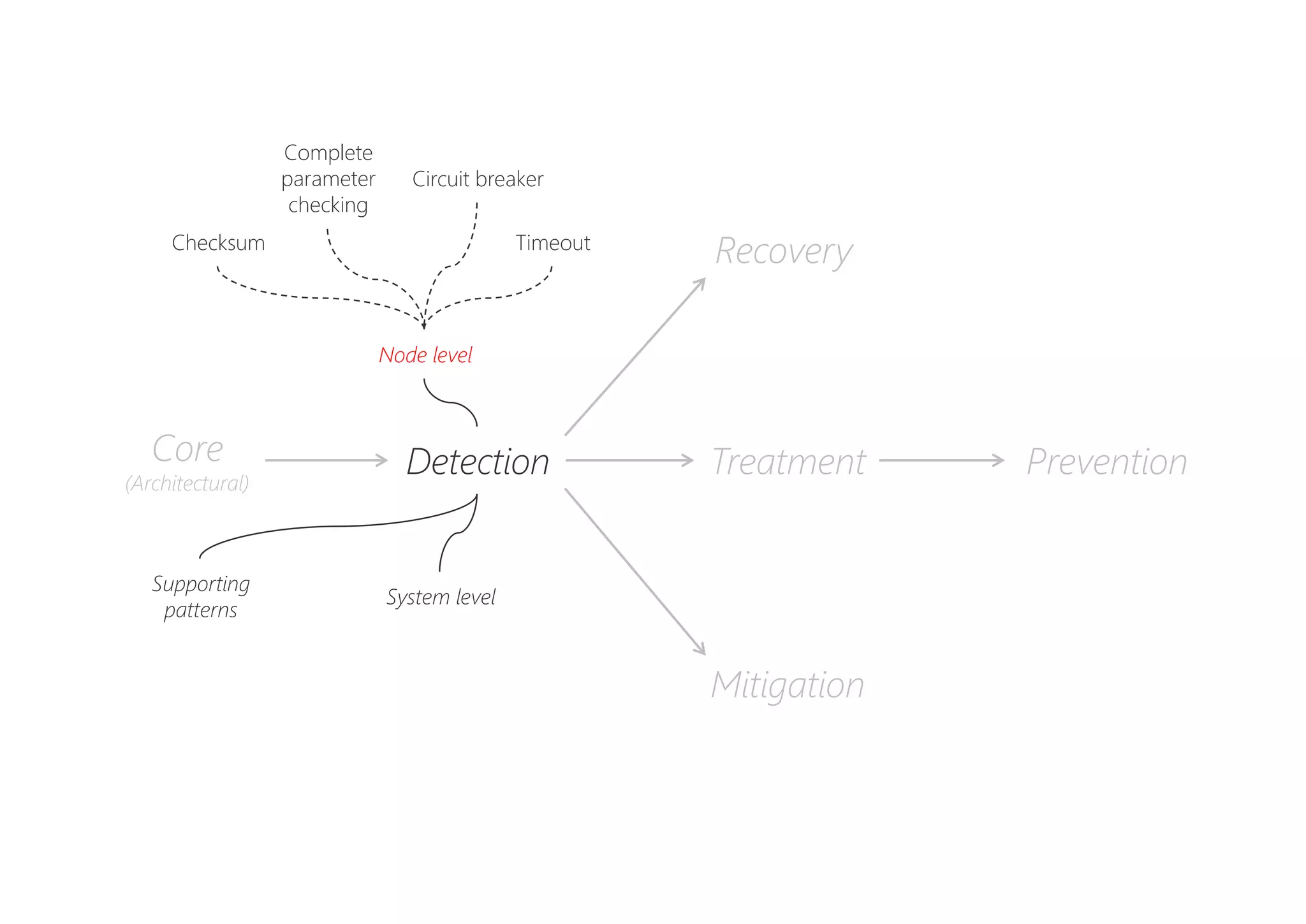
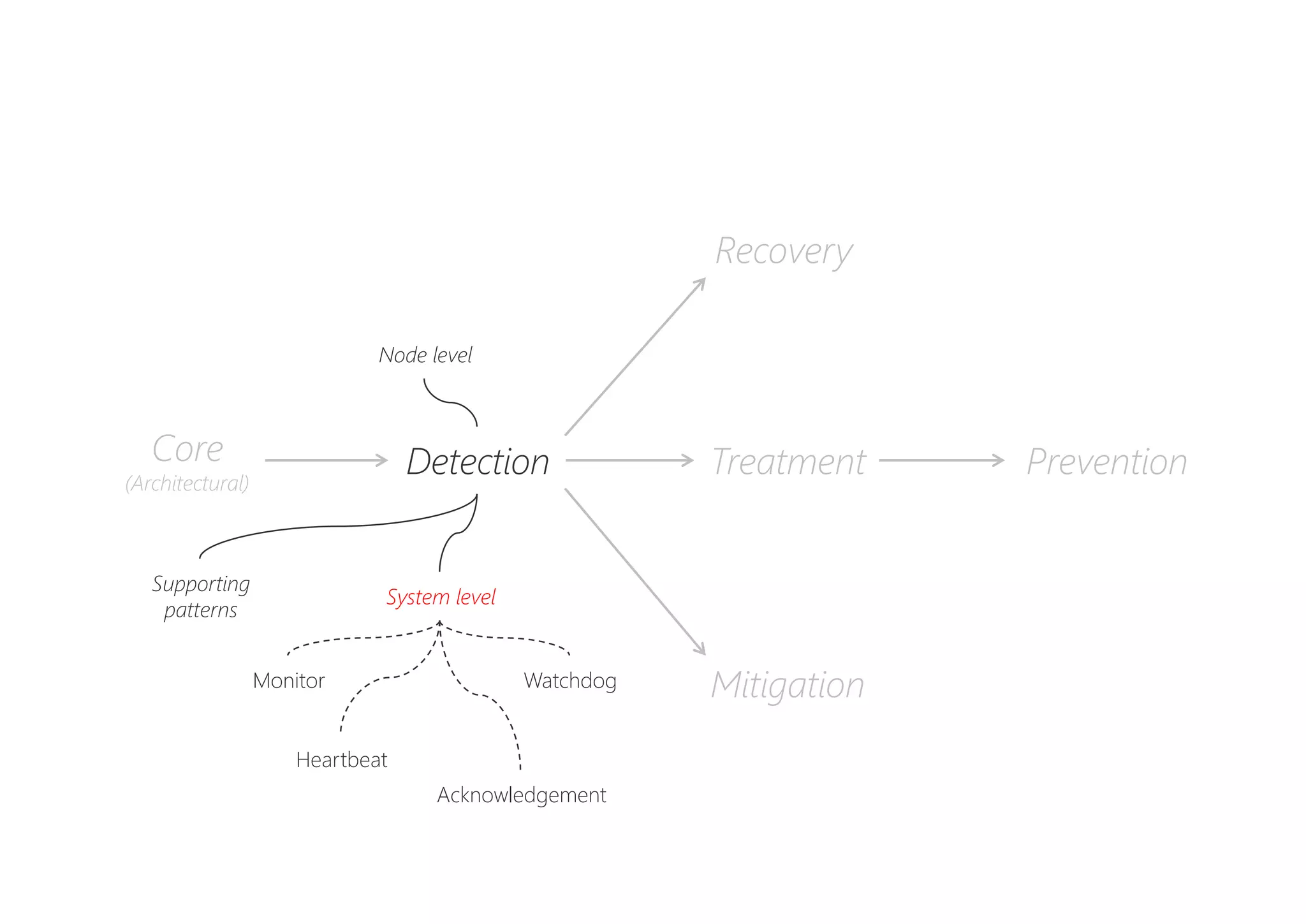
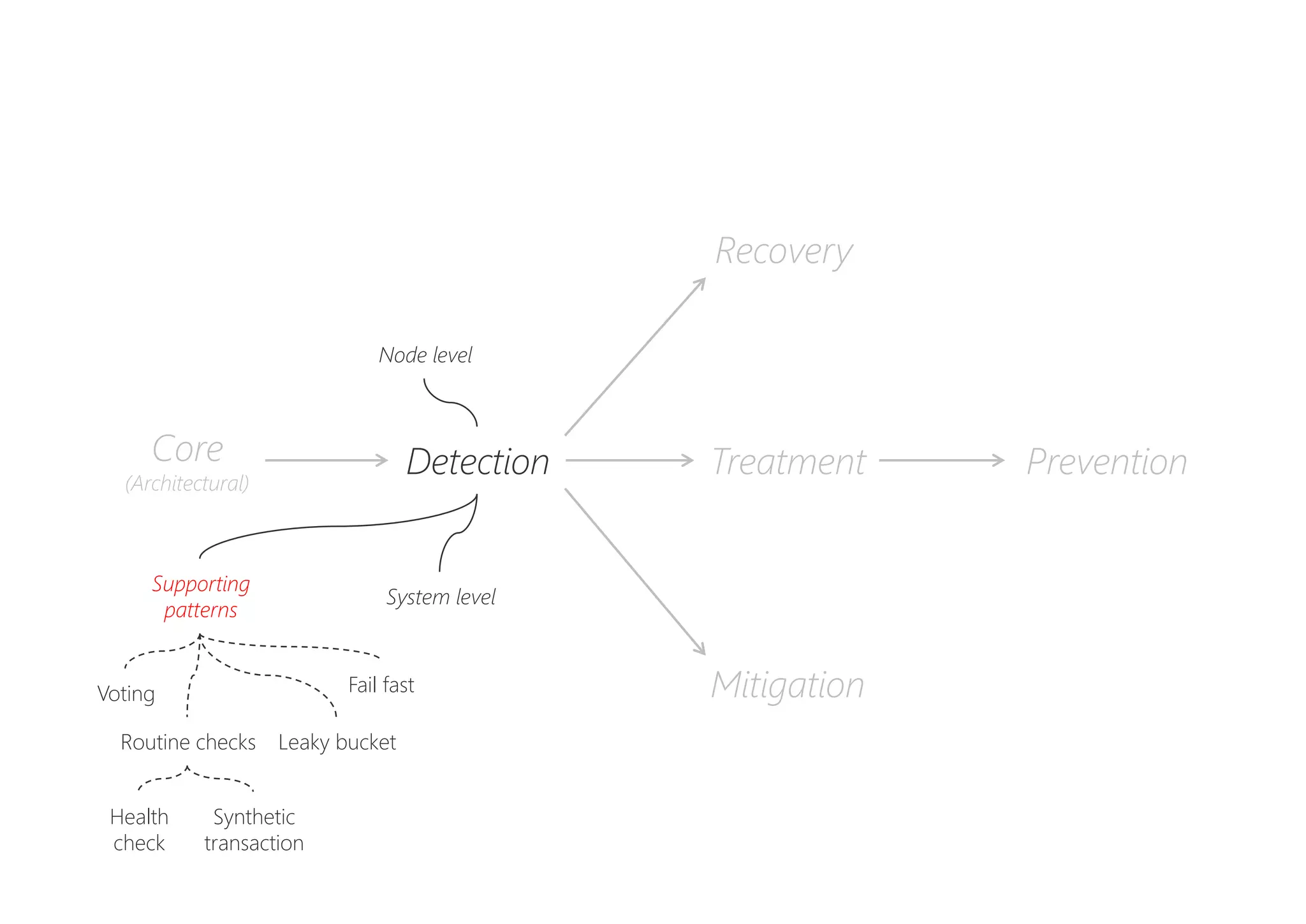
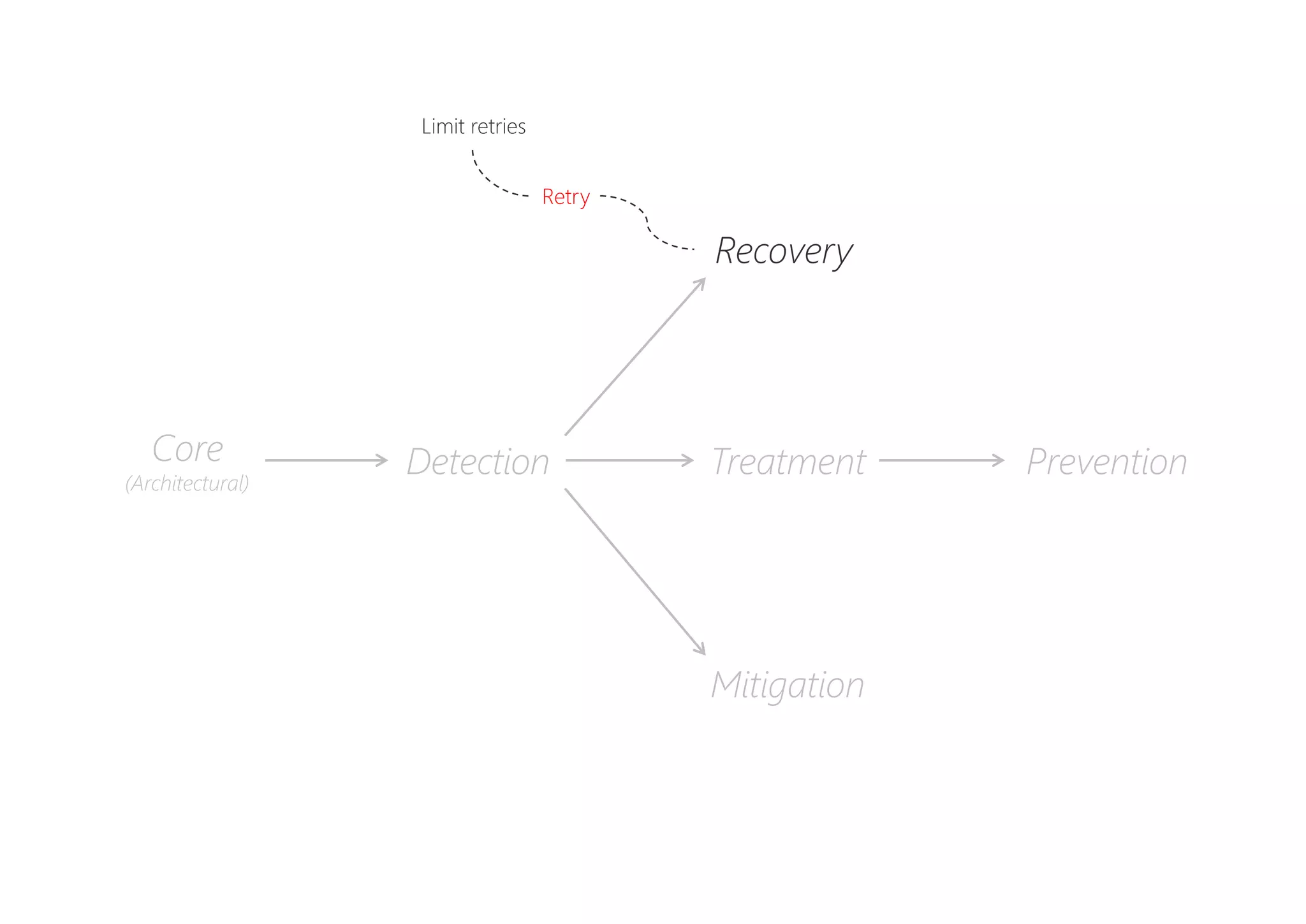
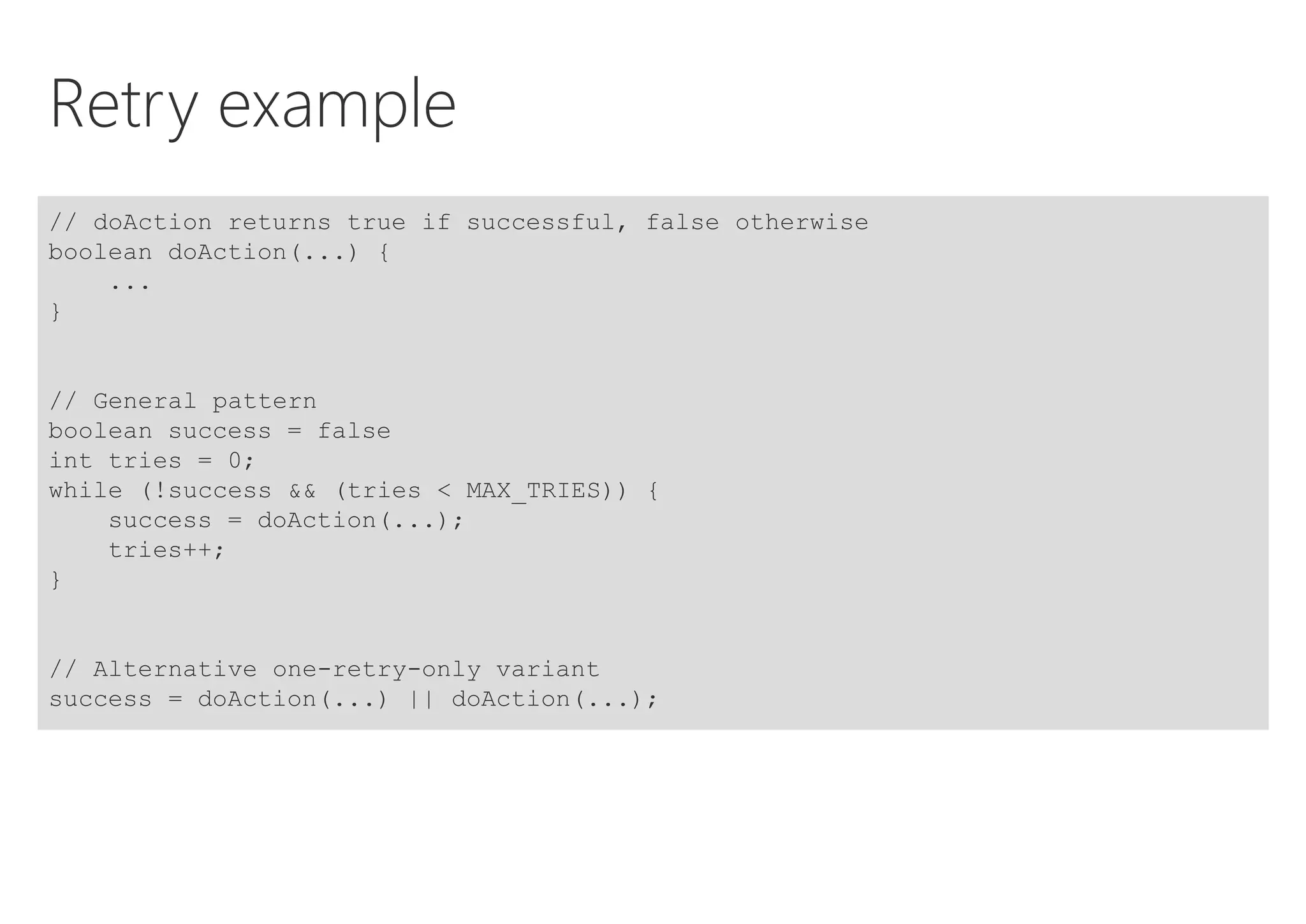
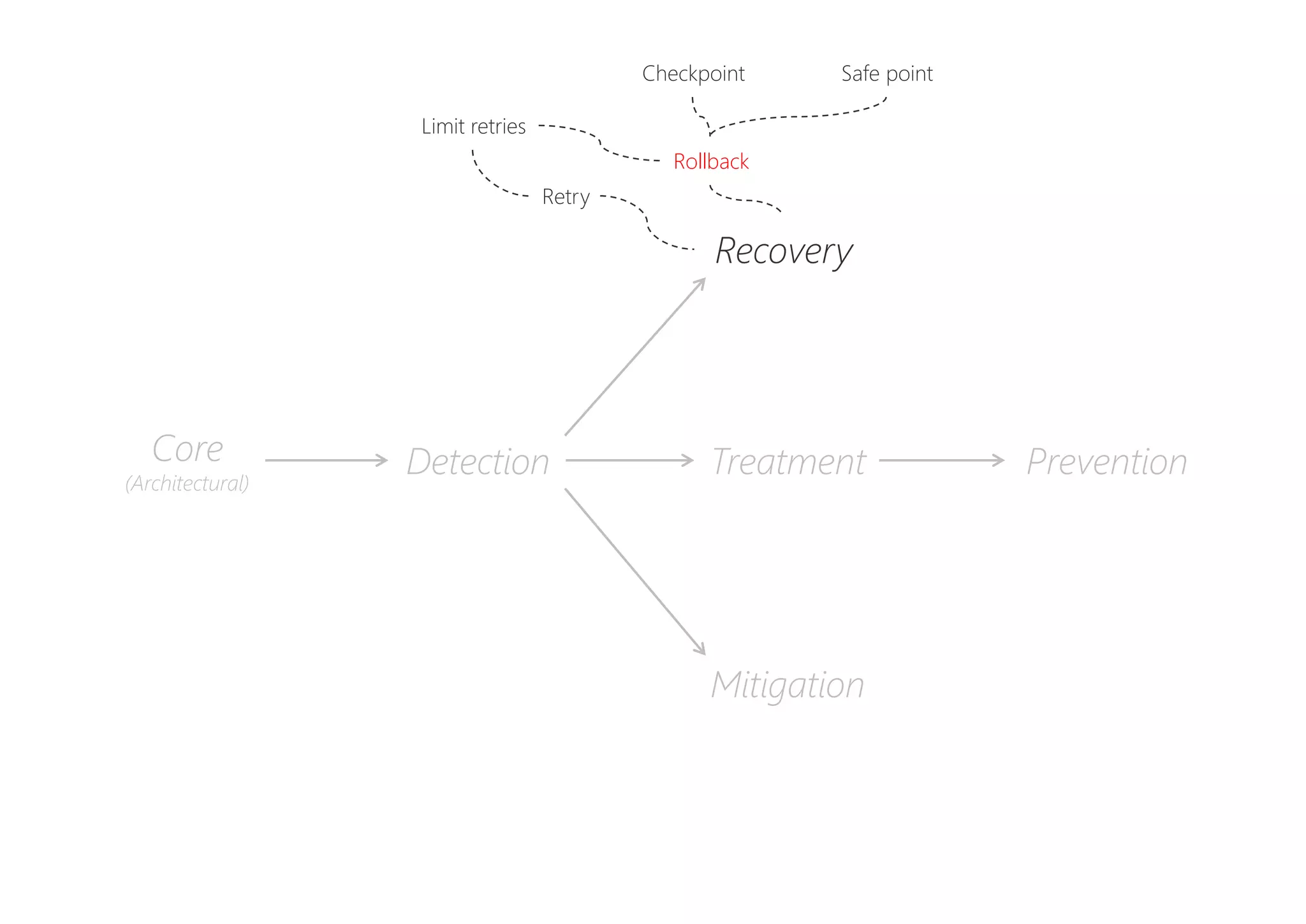
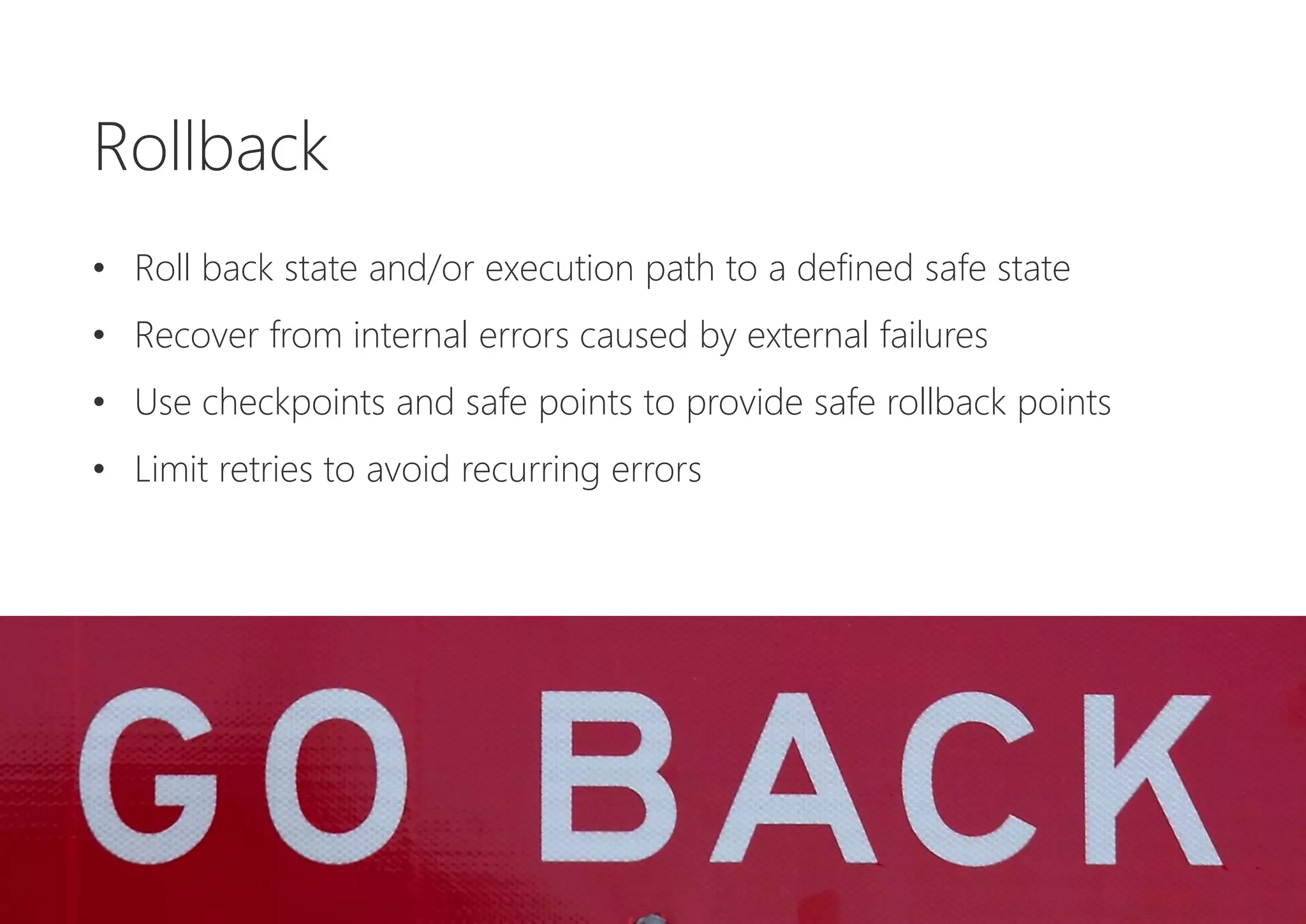
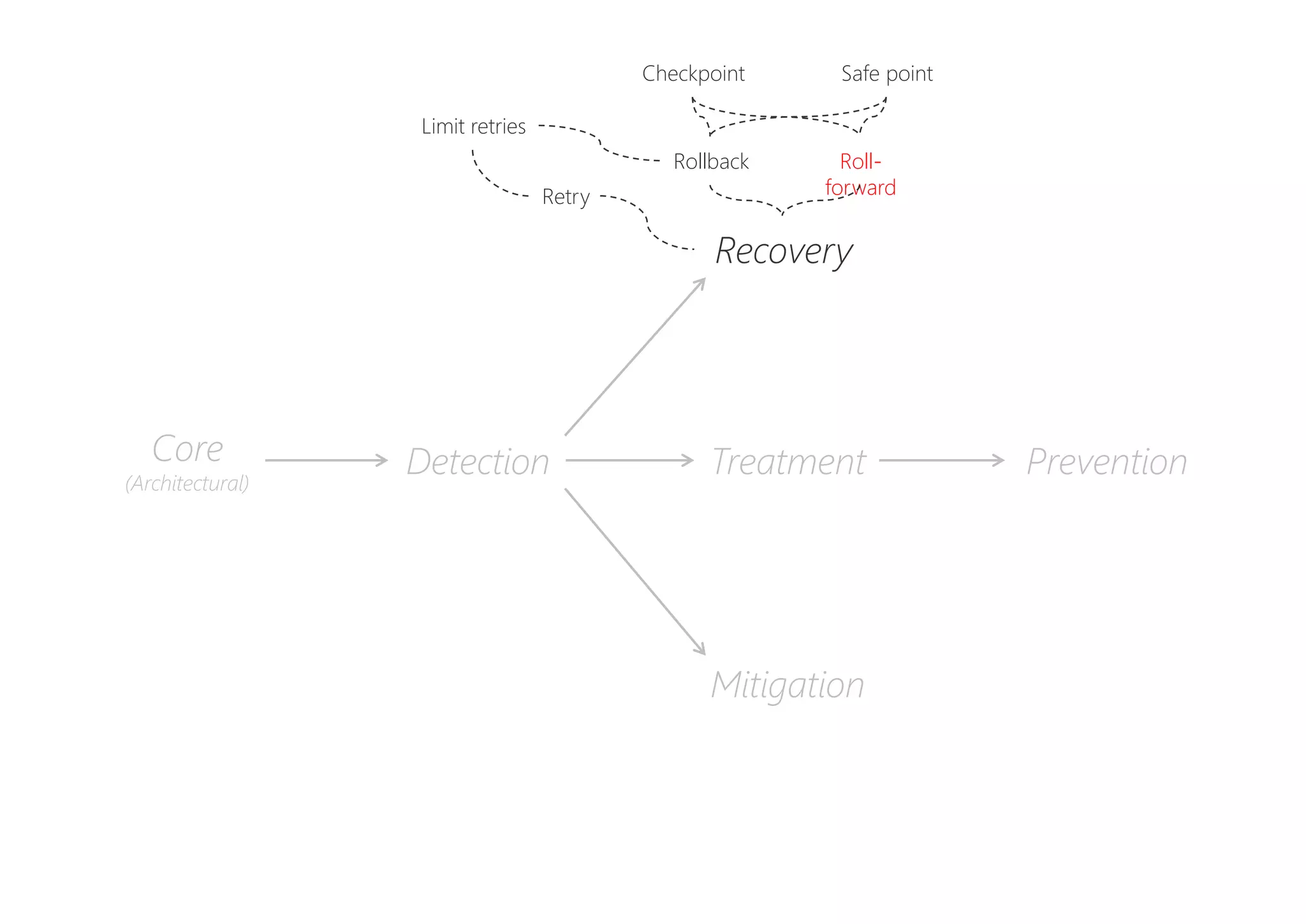
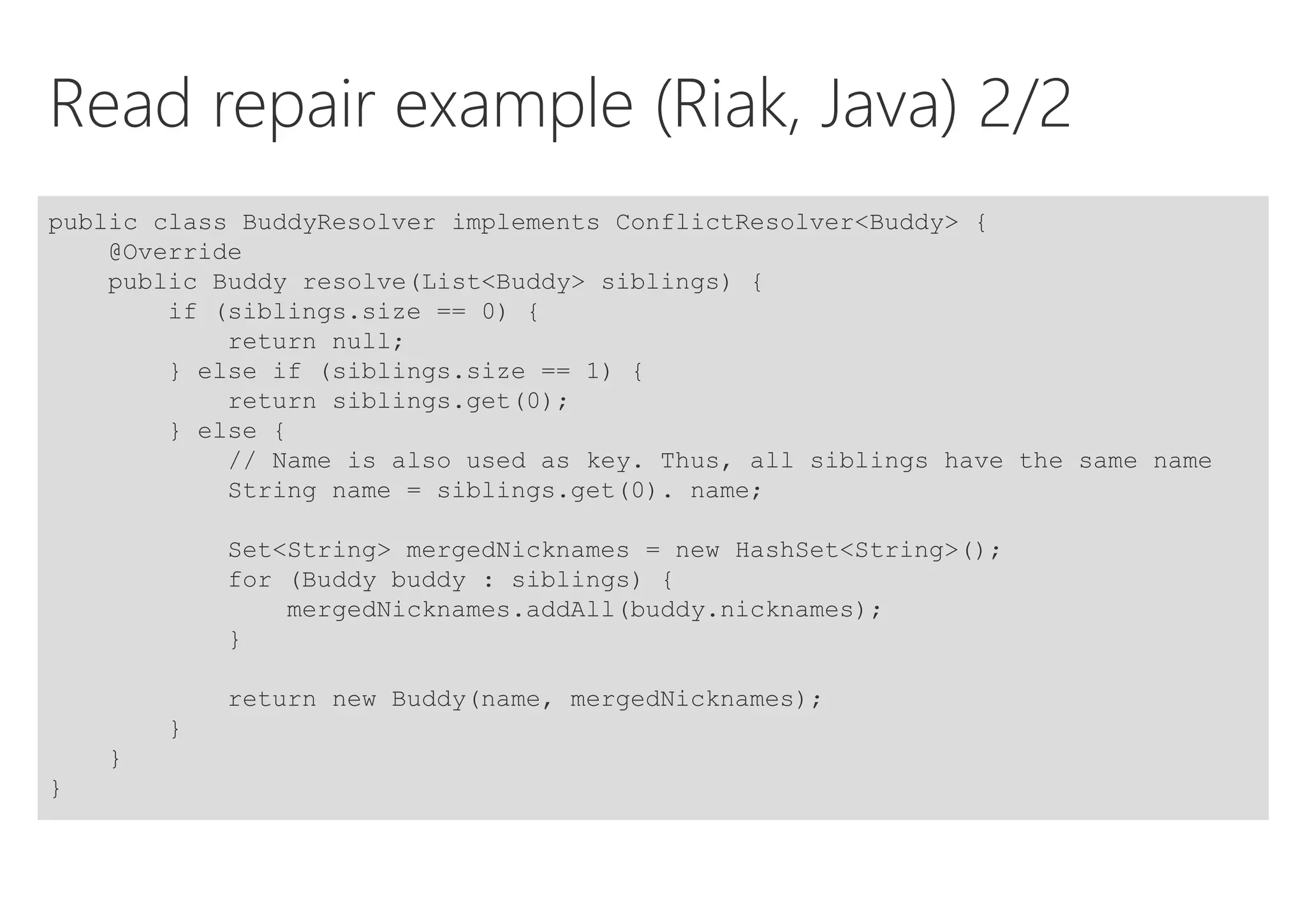
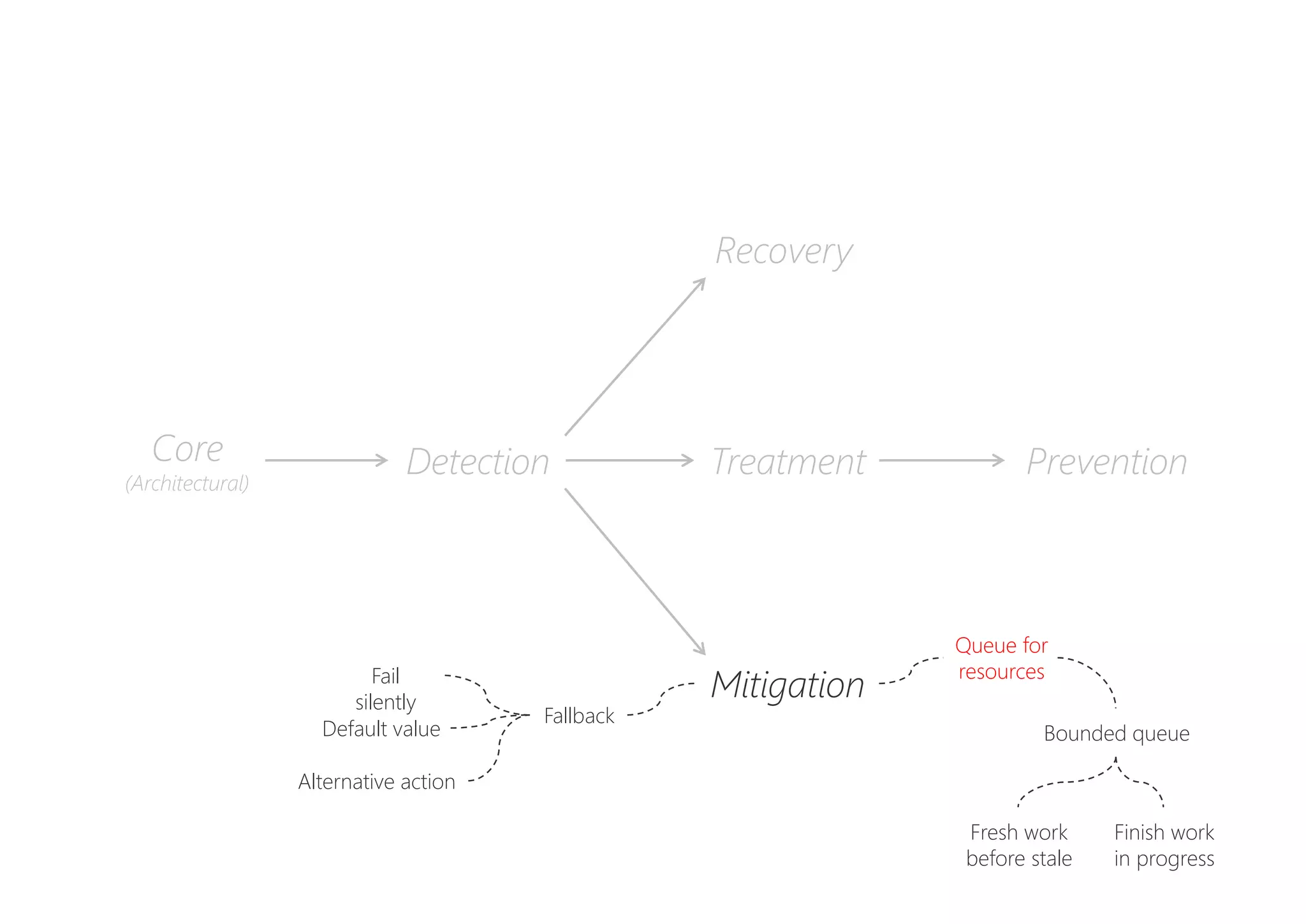
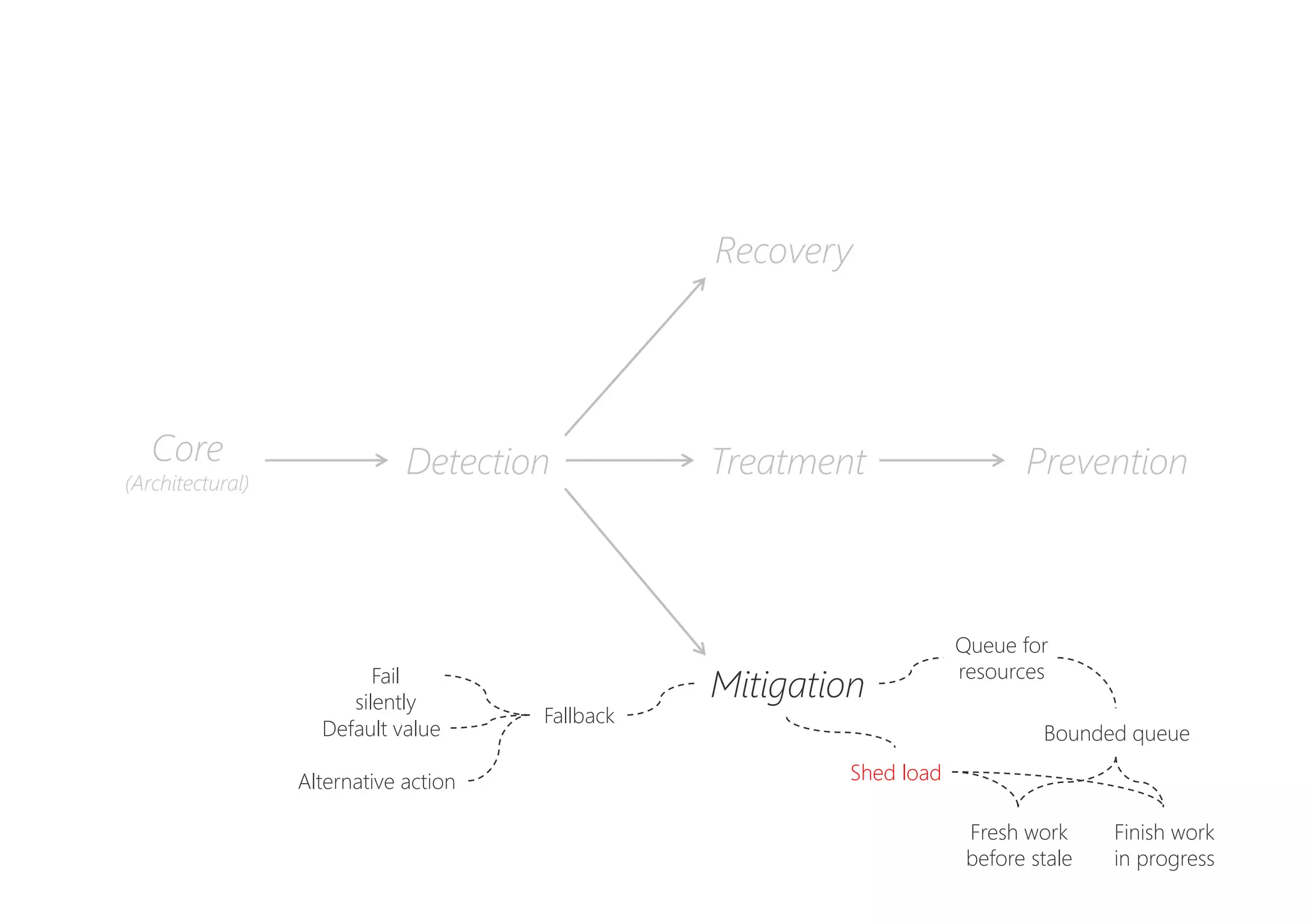
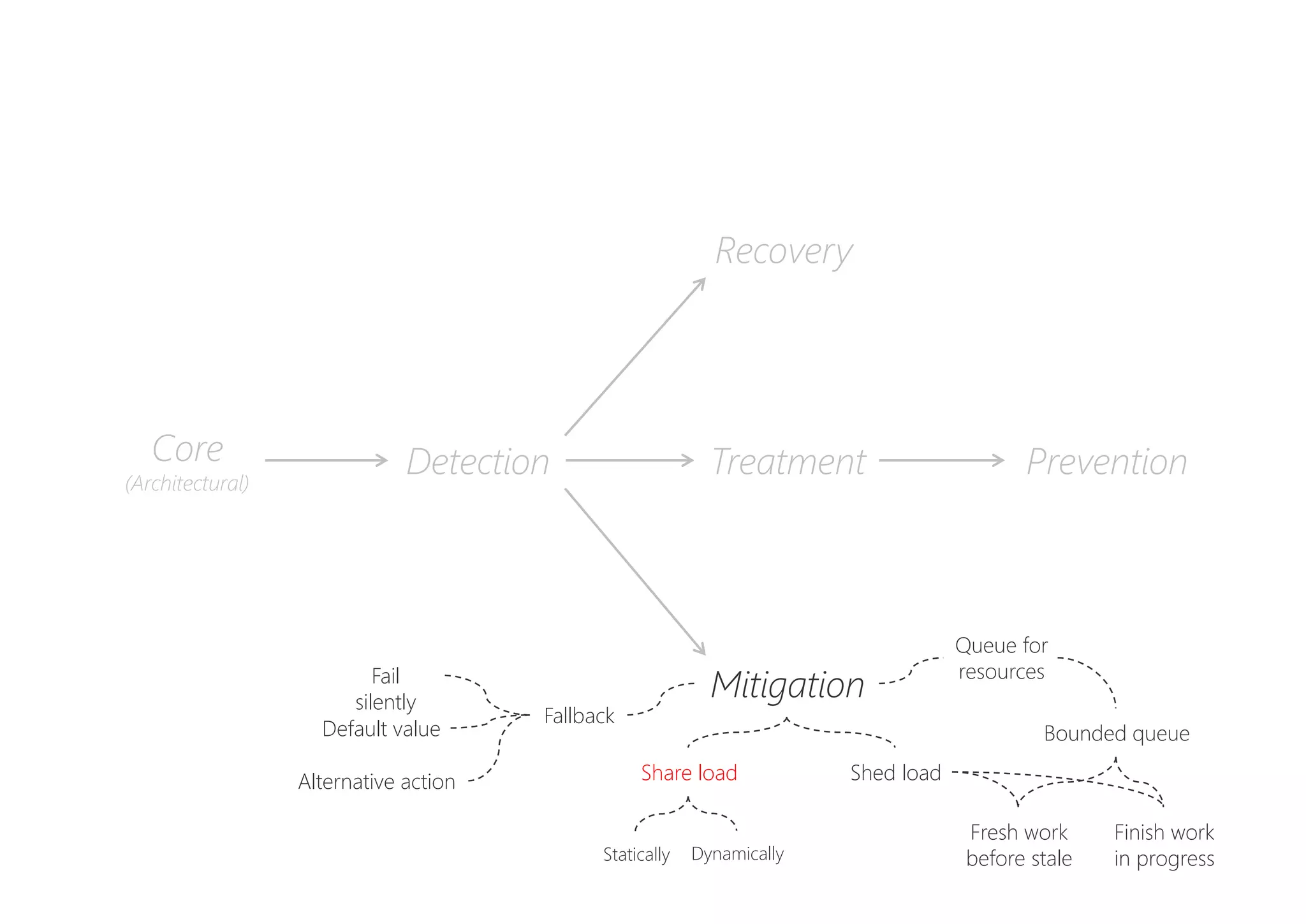
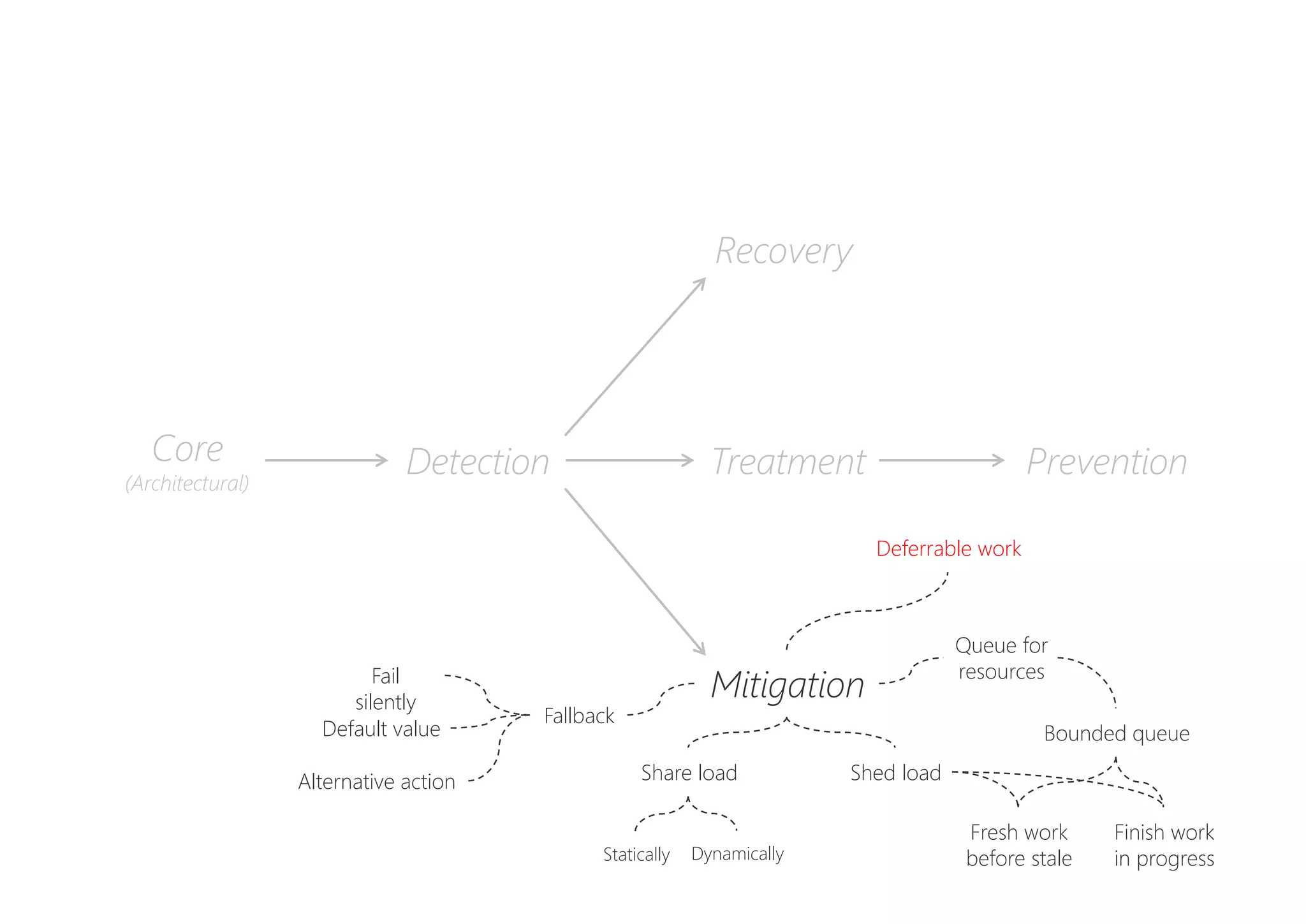
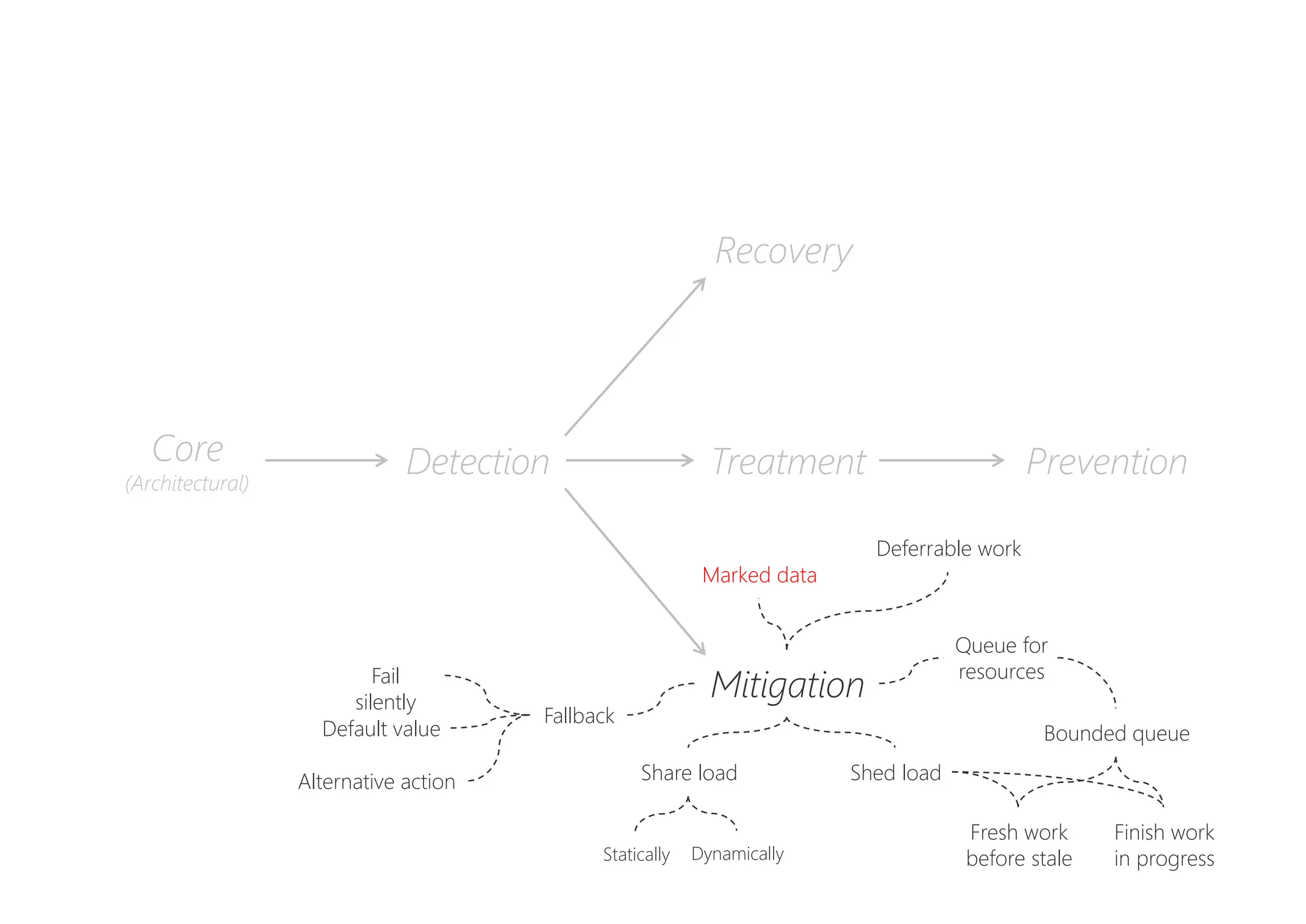
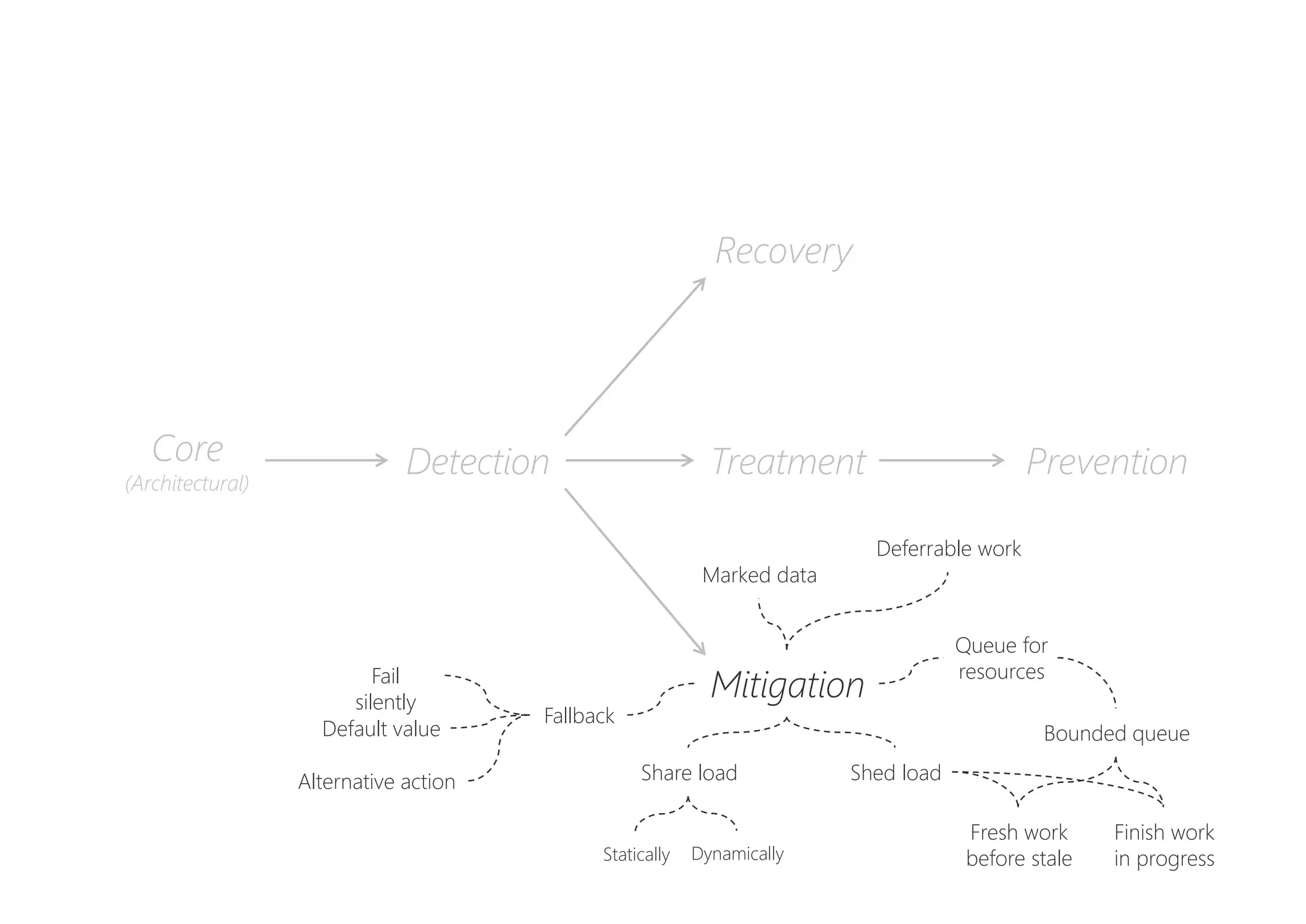
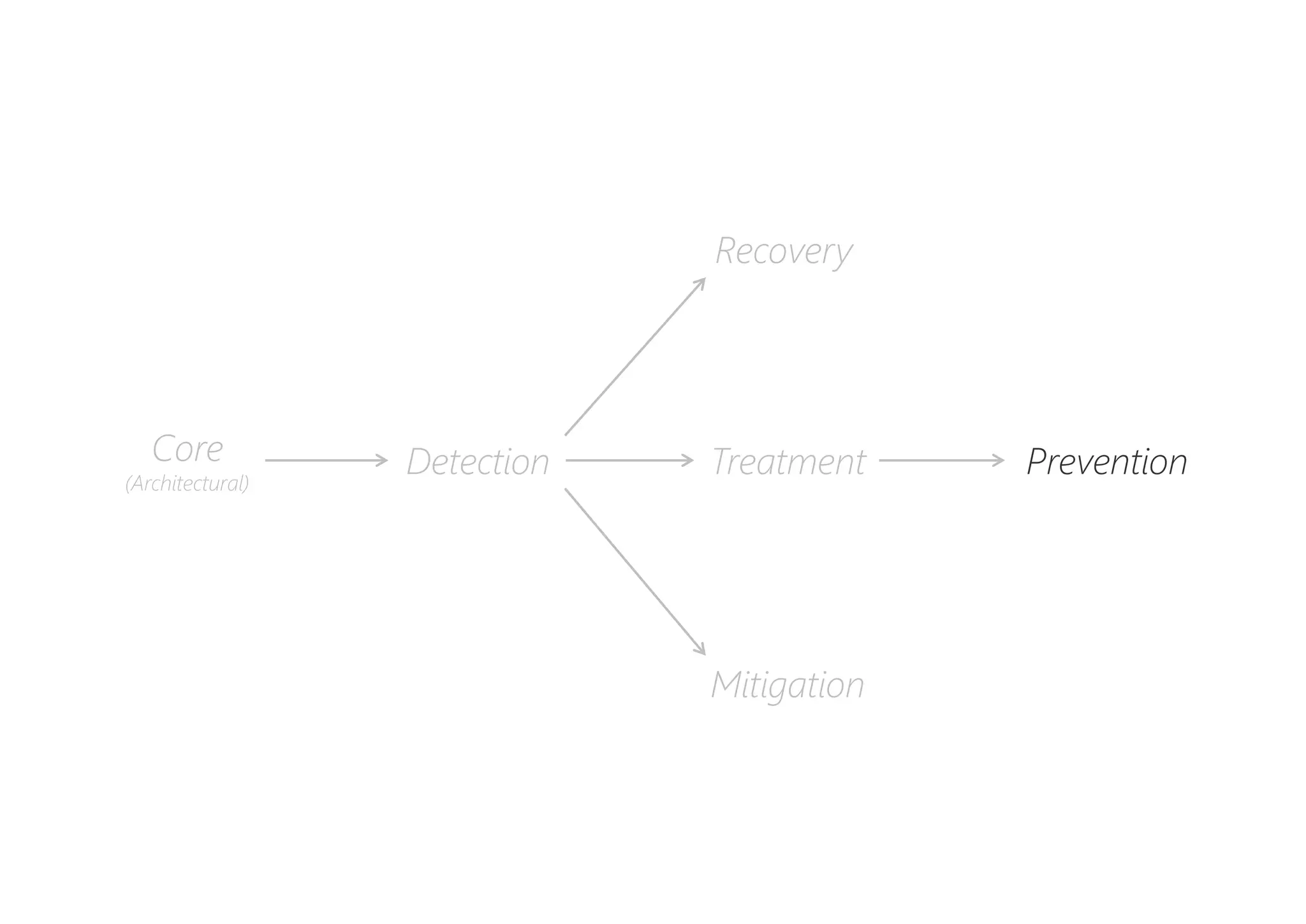
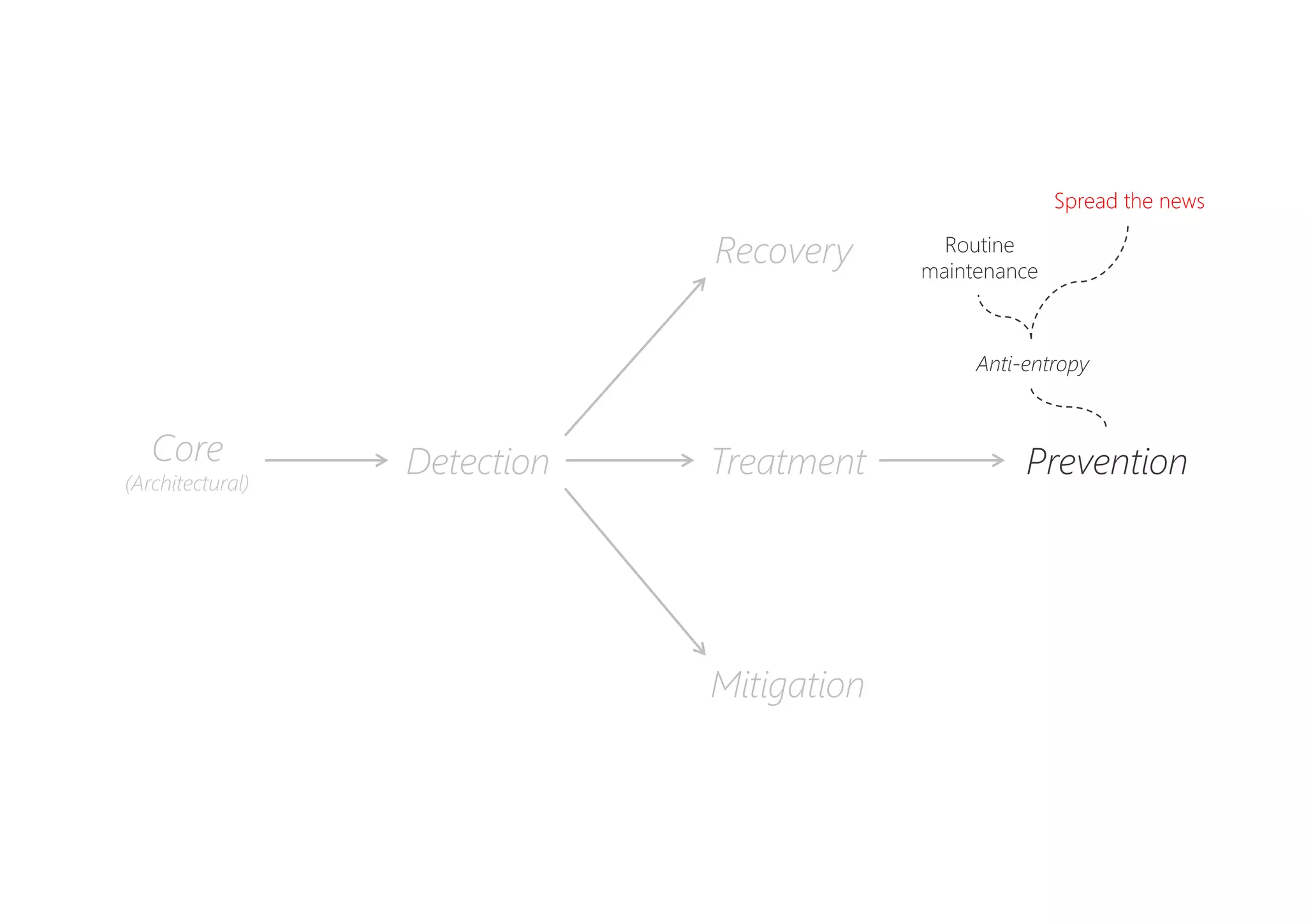
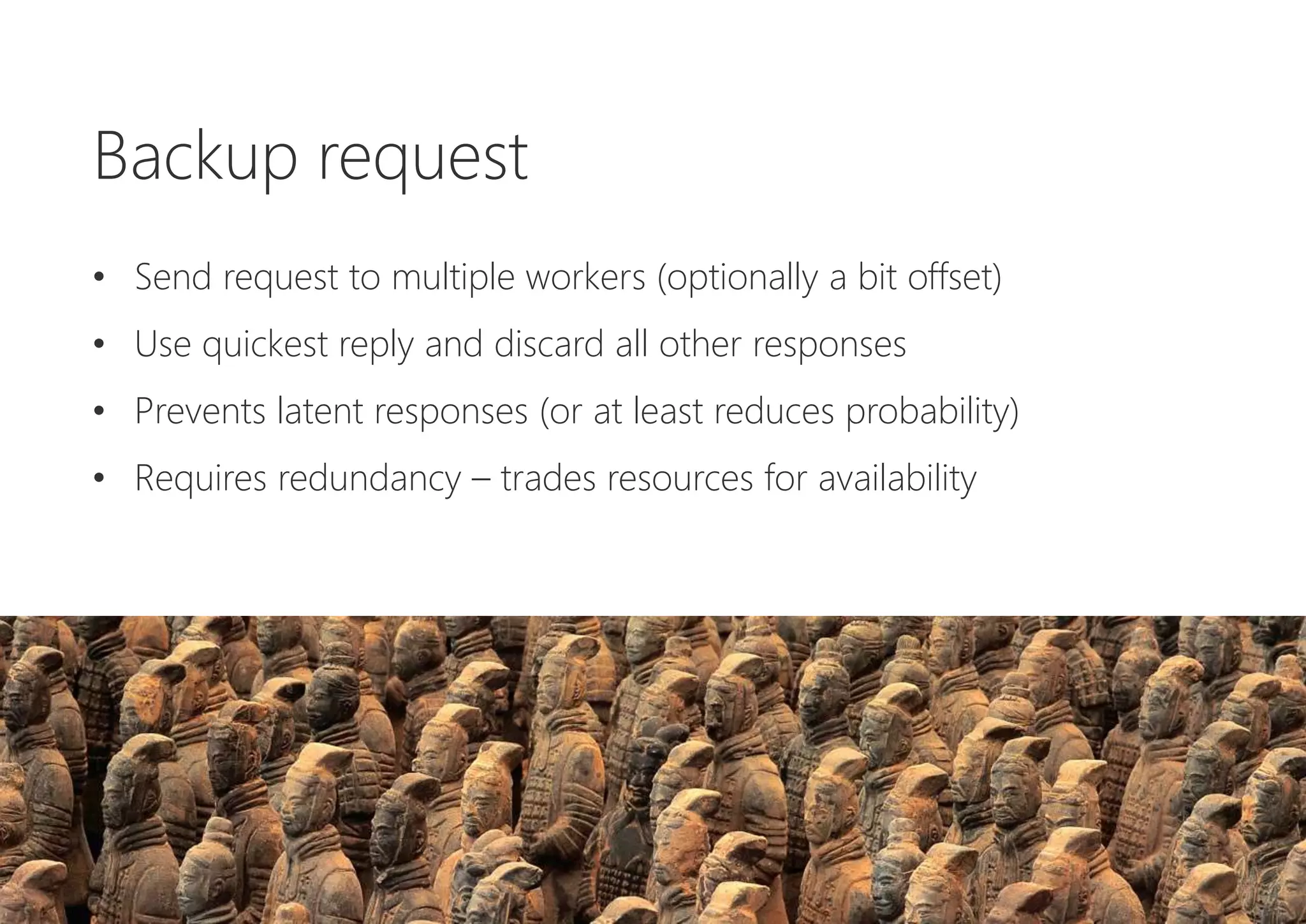
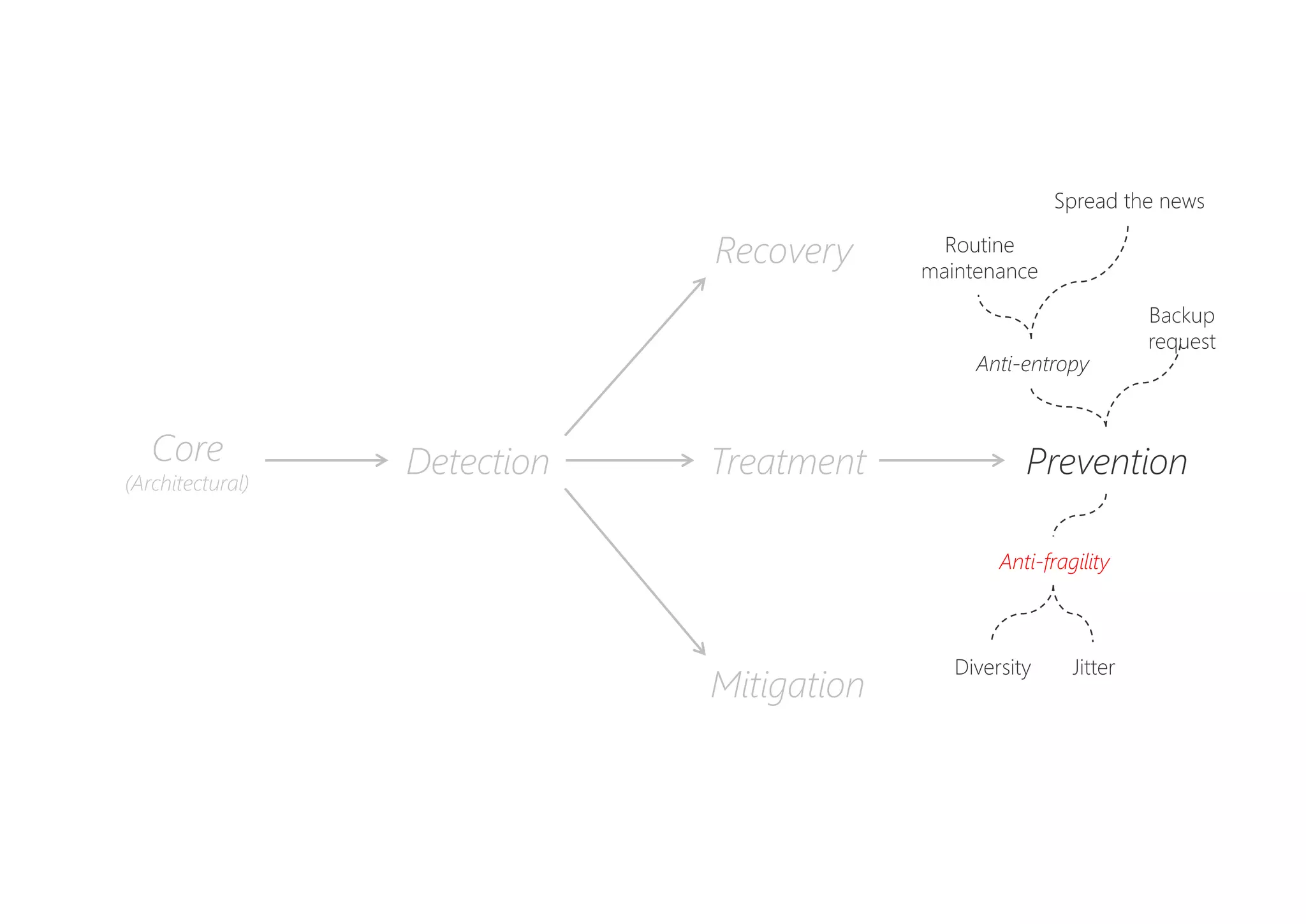
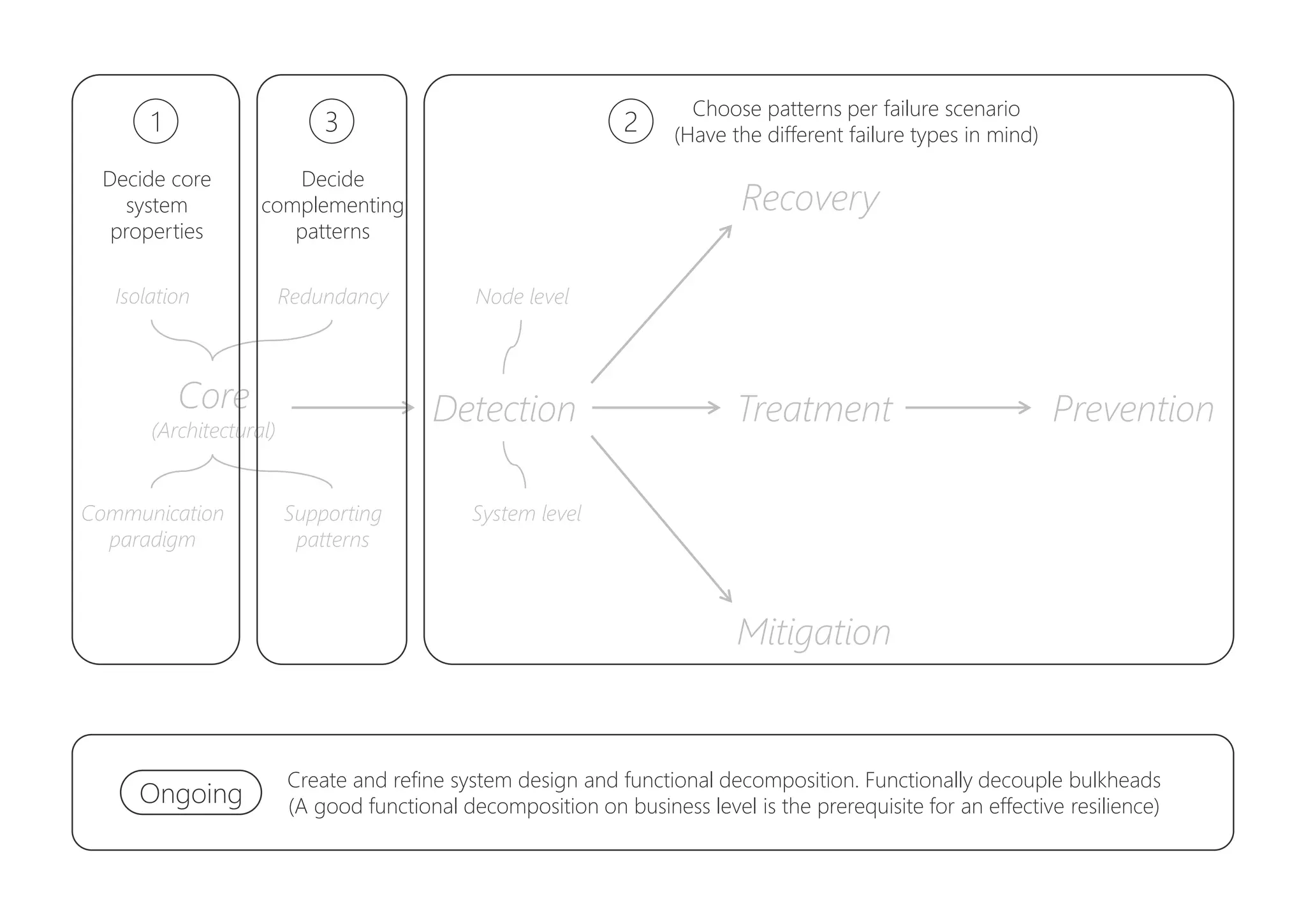
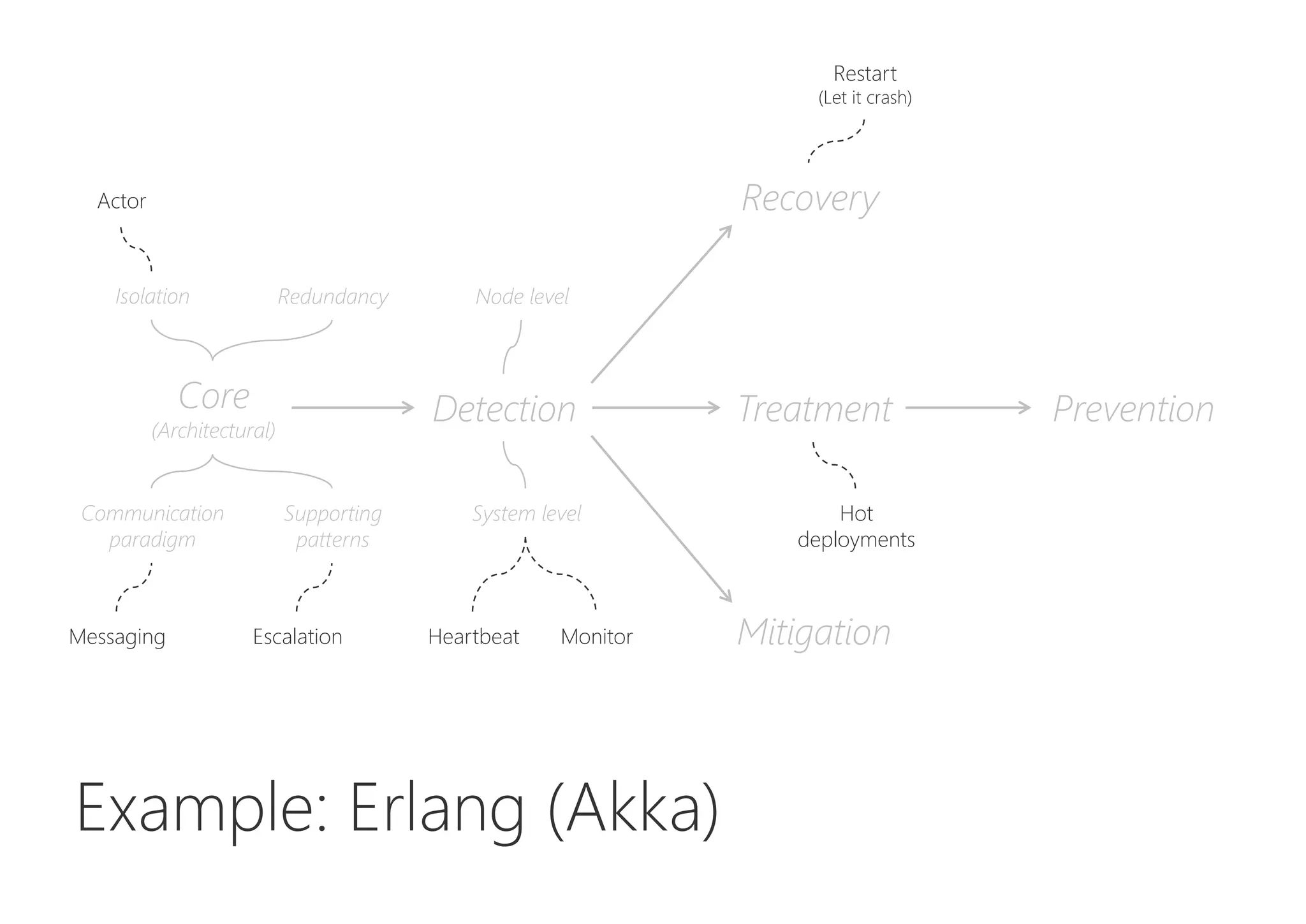
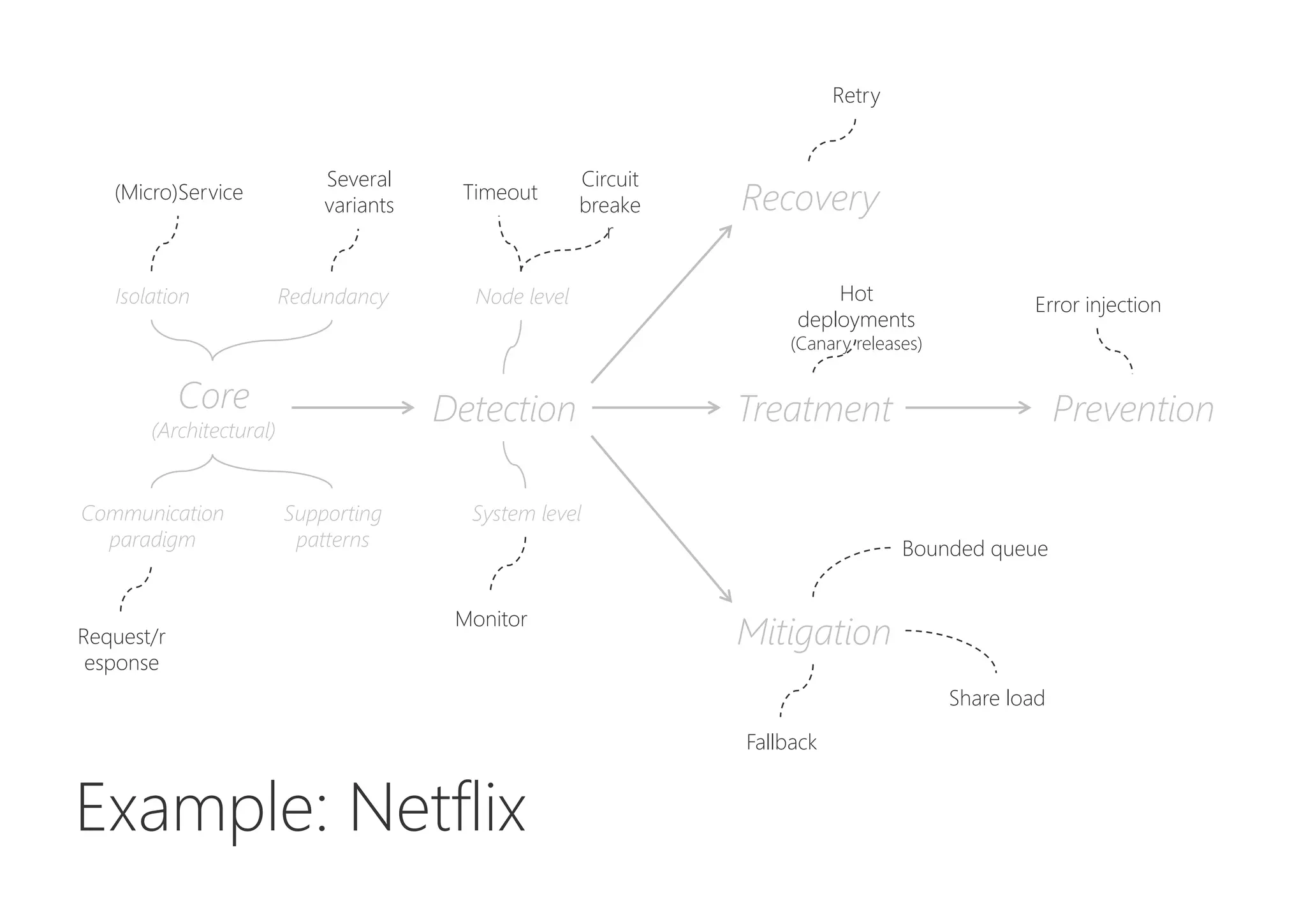
The document discusses resilience in software systems, emphasizing that failures are common in complex distributed environments and should be embraced rather than avoided. It introduces various resilience patterns and strategies, such as redundancy, failover, and dynamic load sharing, as well as methods to recover from and mitigate failures. The text aims to provide a comprehensive understanding of how to design resilient systems through thoughtful architectural decisions and pattern selection.