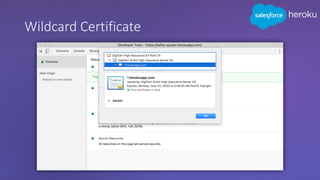
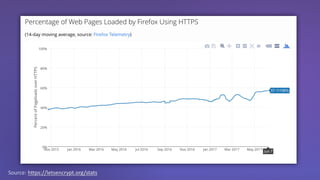
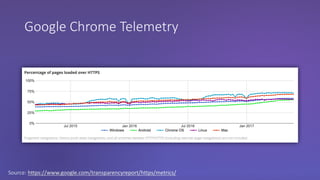
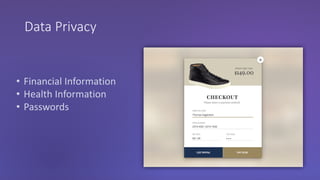
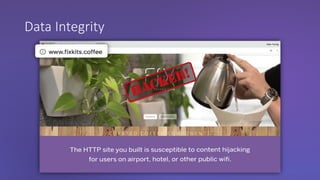
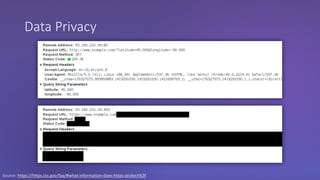
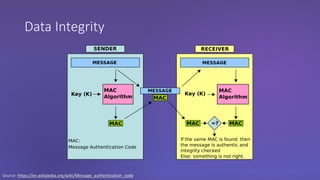
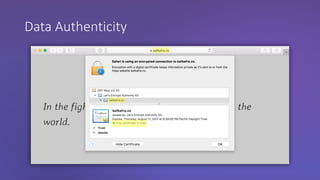
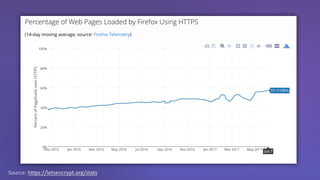
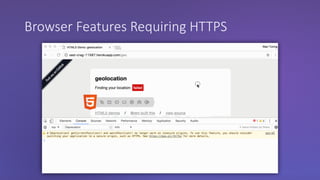
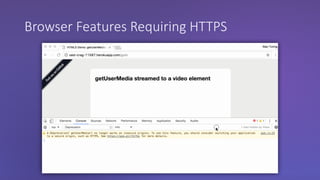
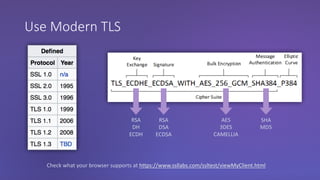
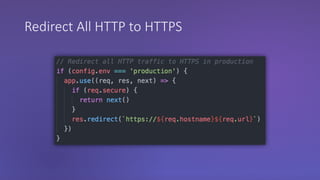
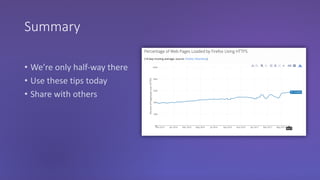
The webinar discusses the importance of HTTPS for web security, emphasizing the need for automated, free, and easily accessible certificates through initiatives like Let's Encrypt. It highlights the risks of data privacy and integrity, and provides practical tips for developers to implement HTTPS effectively. The session concludes with the message that server authentication and integrity are critical for the web's continued success and encourages sharing knowledge with others.