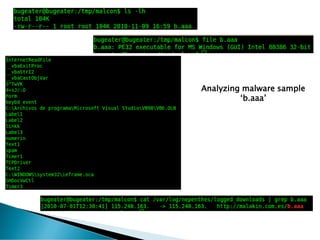
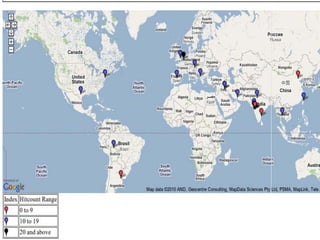
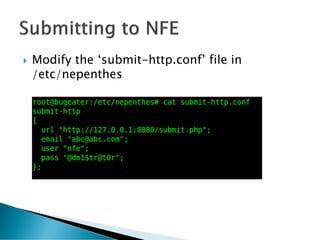
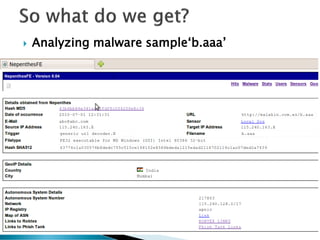
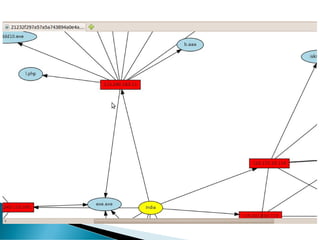
The document discusses the implementation and functionality of the Nepenthes honeypot, a system designed to attract and analyze cyber-attacks. It highlights the use of Nepenthesfe, a front-end tool for automated malware analysis, detailing its capabilities in data collection, visualization, and integration with various analysis tools. Additionally, it outlines the required packages and configuration necessary for setting up the Nepenthes honeypot sensor for effective malware monitoring and reporting.