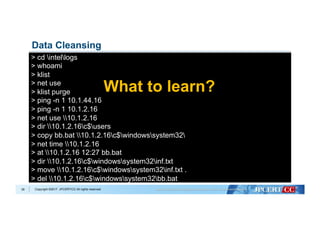
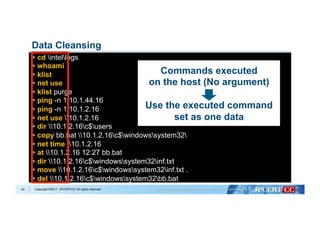
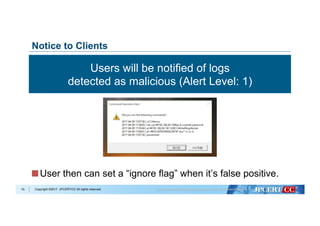
Remove unnecessary data
Remove ping commands
Remove IP addresses
Remove drive letters
40
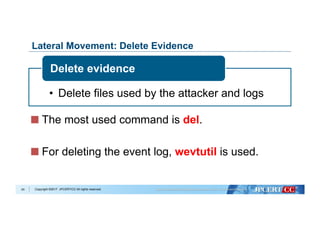
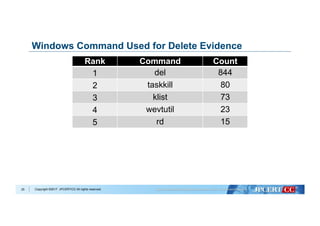
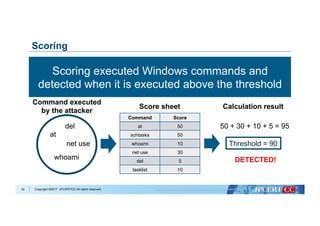
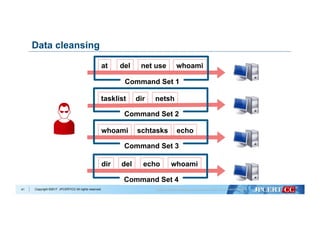
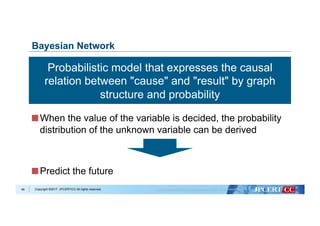
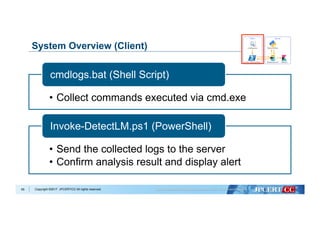
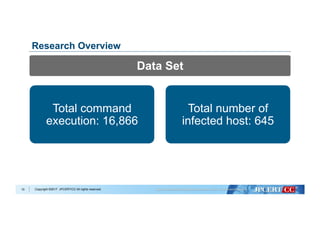
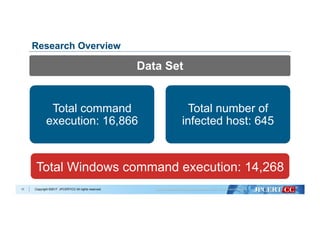
Data Cleansing
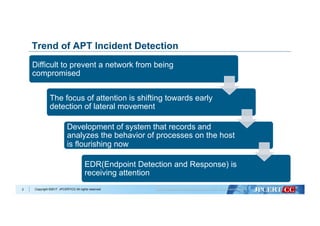
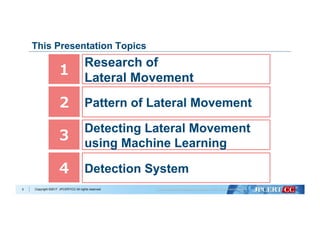
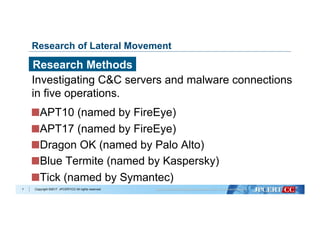
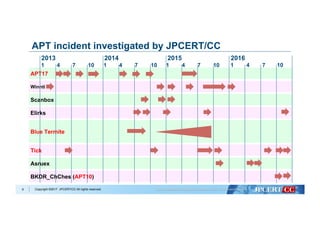
�Copyright ©2017 JPCERT/CC All rights reserved.
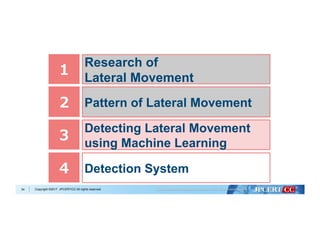
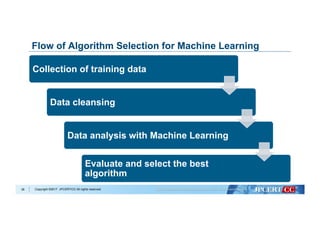
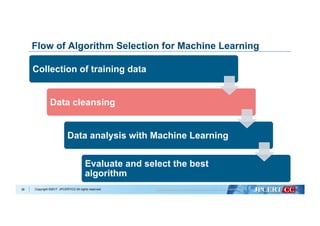
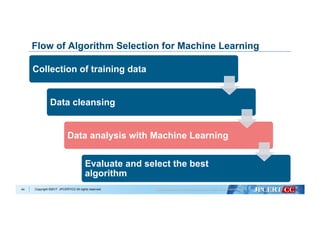
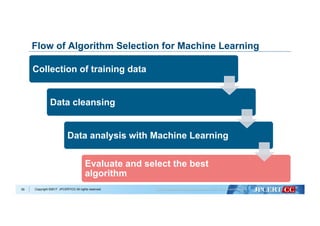
Collection of training data
Data cleansing
Data analysis with Machine Learning
Evaluate and select the best
algorithm
41
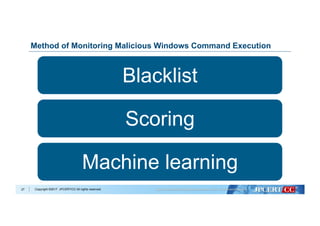
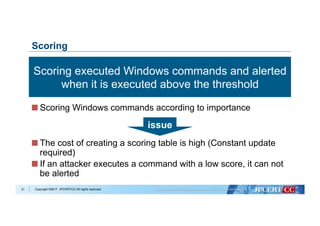
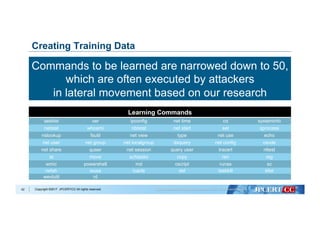
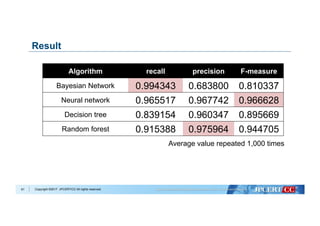
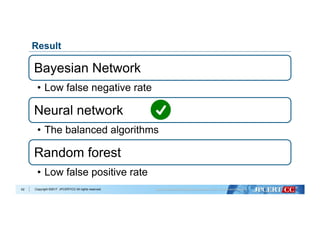
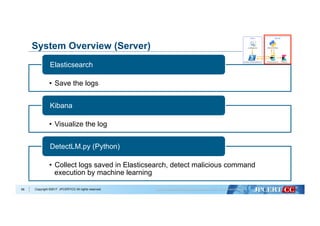
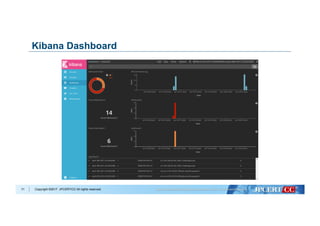
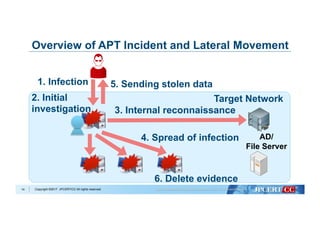
Flow of Algorithm Selection for Machine Learning
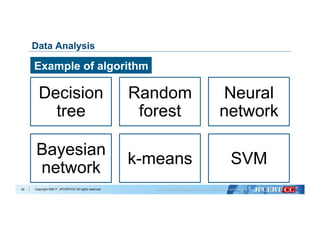
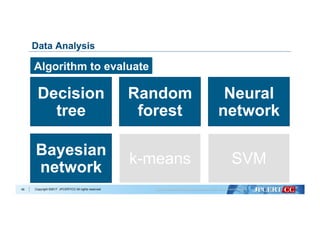
Data analysis with Machine Learning algorithms:
- Decision Tree
- Naive Bayes
- k-Nearest Neighbors
- Logistic Regression
- Support Vector Machine
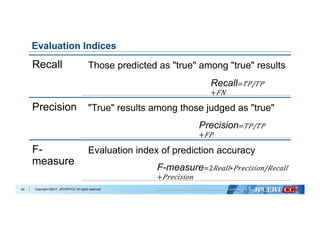
Evaluate based on:
- Accuracy
- Recall
- Precision
- F1 Score
Select algorithm with best performance











![Copyright ©2017 JPCERT/CC All rights reserved.
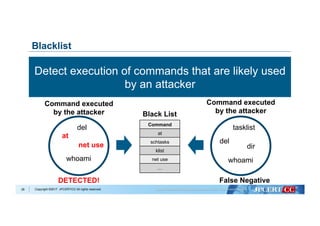
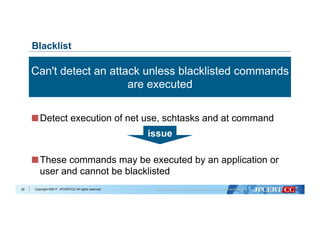
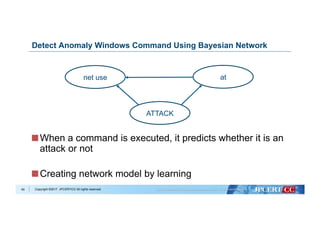
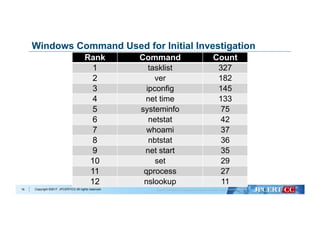
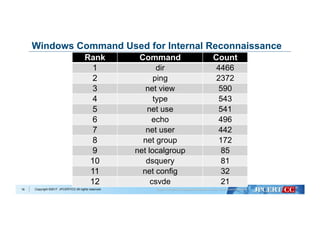
Remote Command Execute Used Windows Command
22
at command
> at [IP Address] 12:00 cmd /c "C:windowstemp
mal.exe"
schtasks command
> schtasks /create /tn [Task Name] /tr C:1.bat /sc
onstart /ru System /s [IP Address]](https://image.slidesharecdn.com/shuseitomonagapacsec20171026-171031100340/85/Shusei-tomonaga-pac_sec_20171026-23-320.jpg)
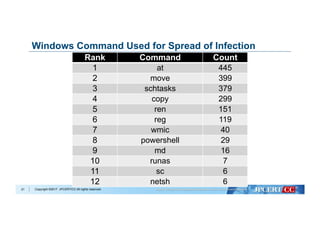
![Copyright ©2017 JPCERT/CC All rights reserved.
Remote Command Execute Used Windows Command
23
wmic command
> wmic /node:[IP Address] /user:”[User Name]” /
password:”[PASSWORD]” process call create
“cmd /c c:WindowsSystem32net.exe user”](https://image.slidesharecdn.com/shuseitomonagapacsec20171026-171031100340/85/Shusei-tomonaga-pac_sec_20171026-24-320.jpg)