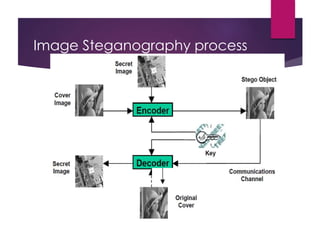
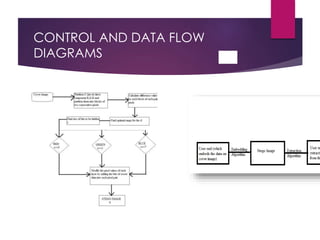
This document discusses an adaptive pixel value differencing (PVD) based secret data hiding technique. It begins with an introduction to steganography and some common steganography techniques. The proposed method aims to embed most data into edged areas of an image since there are larger pixel differences, increasing embedding capacity. It implements a PVD-based embedding and extraction algorithm. Experimental results on Lena and Baboon images show increased payload and acceptable stego image quality compared to LSB substitution. The proposed method effectively and efficiently embeds hidden information imperceptibly into cover images.