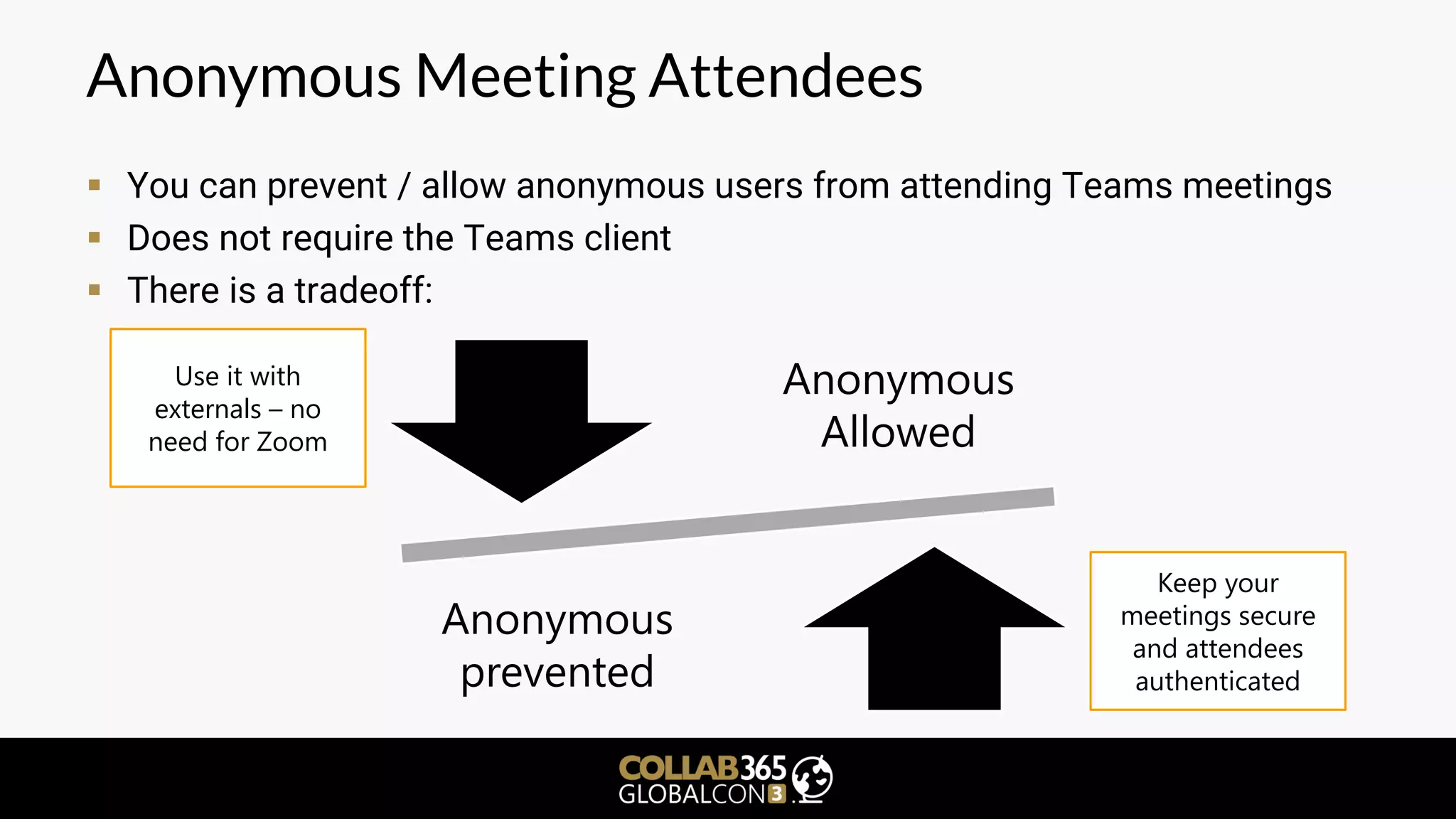
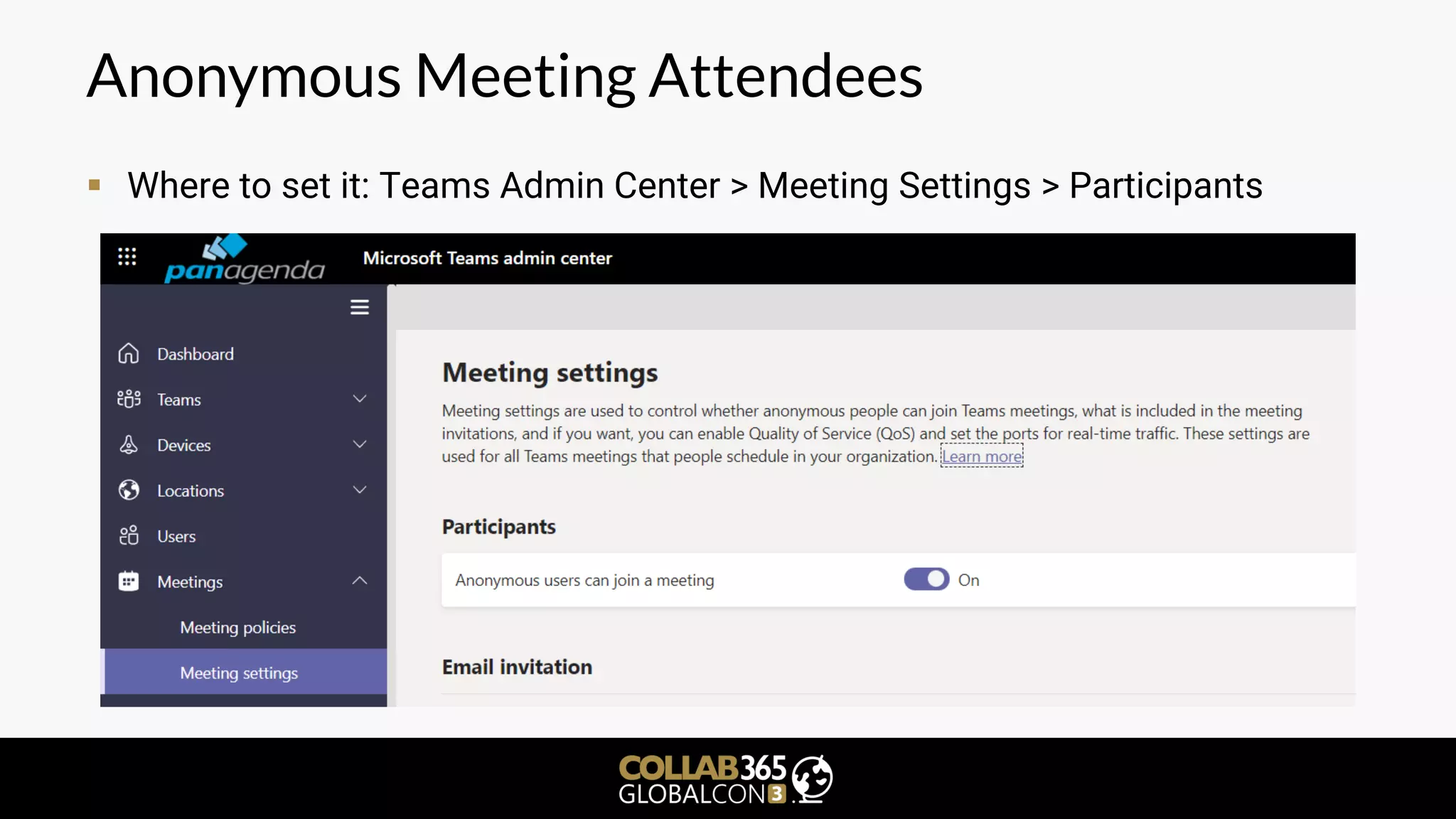
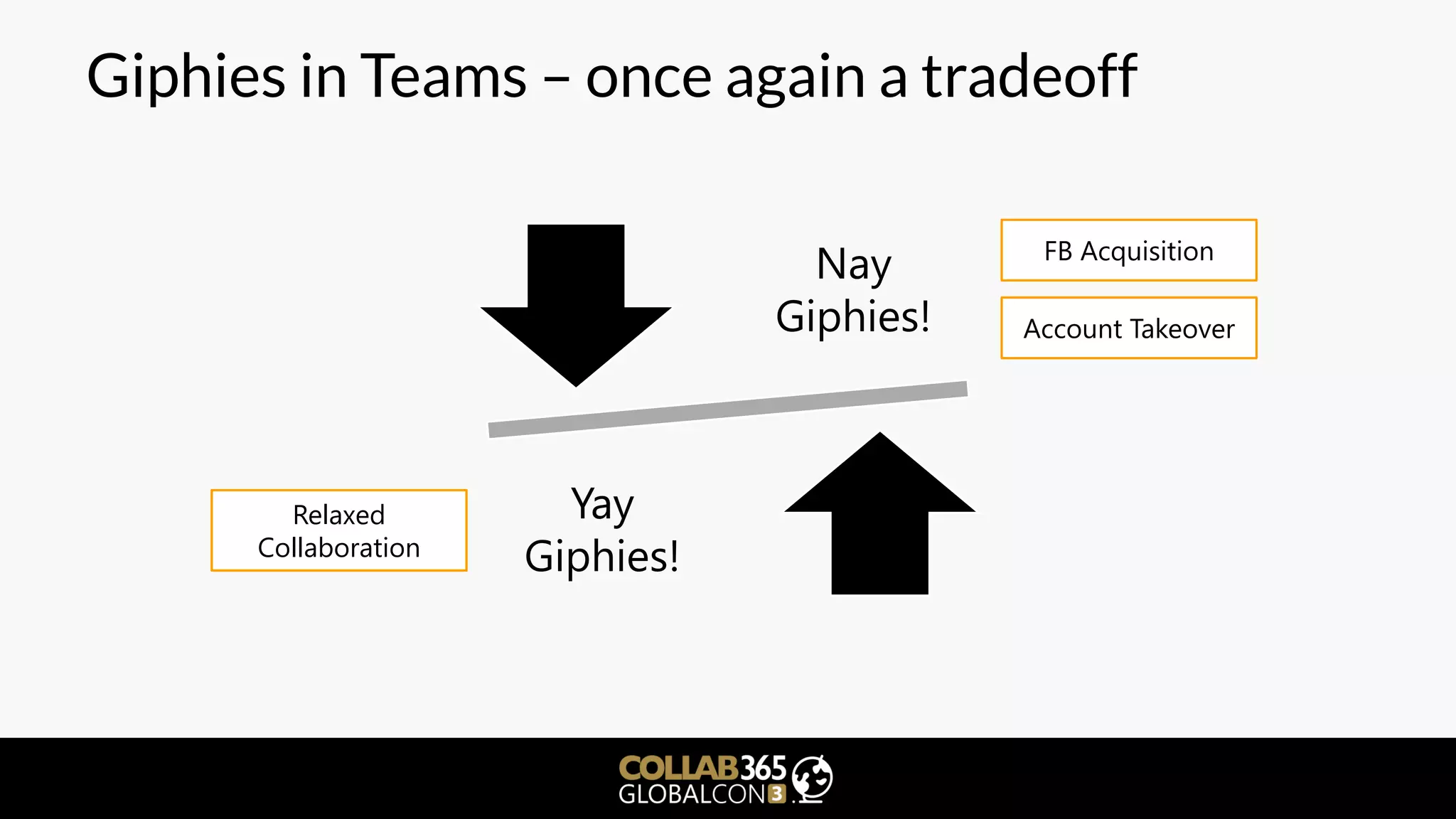
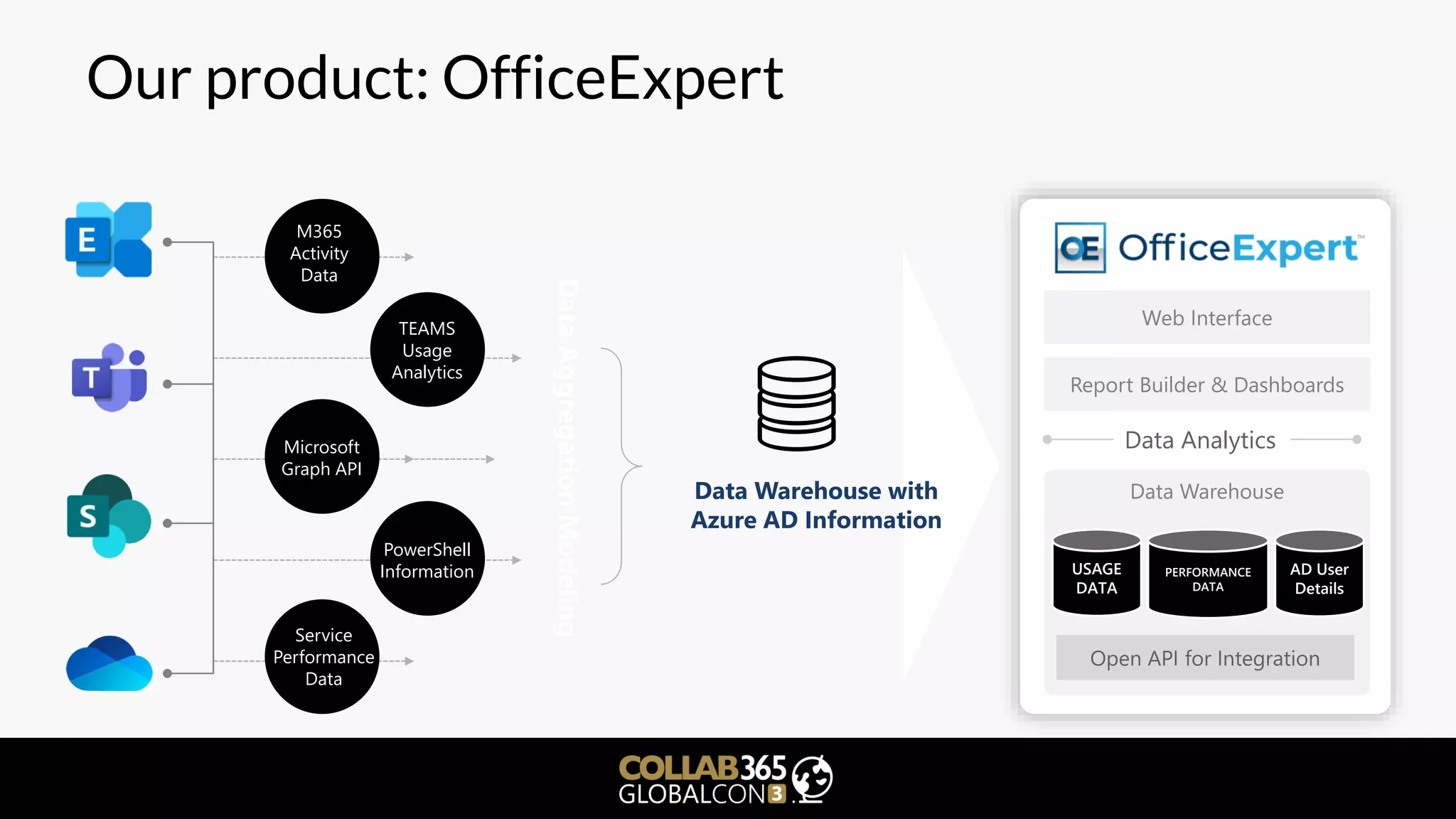
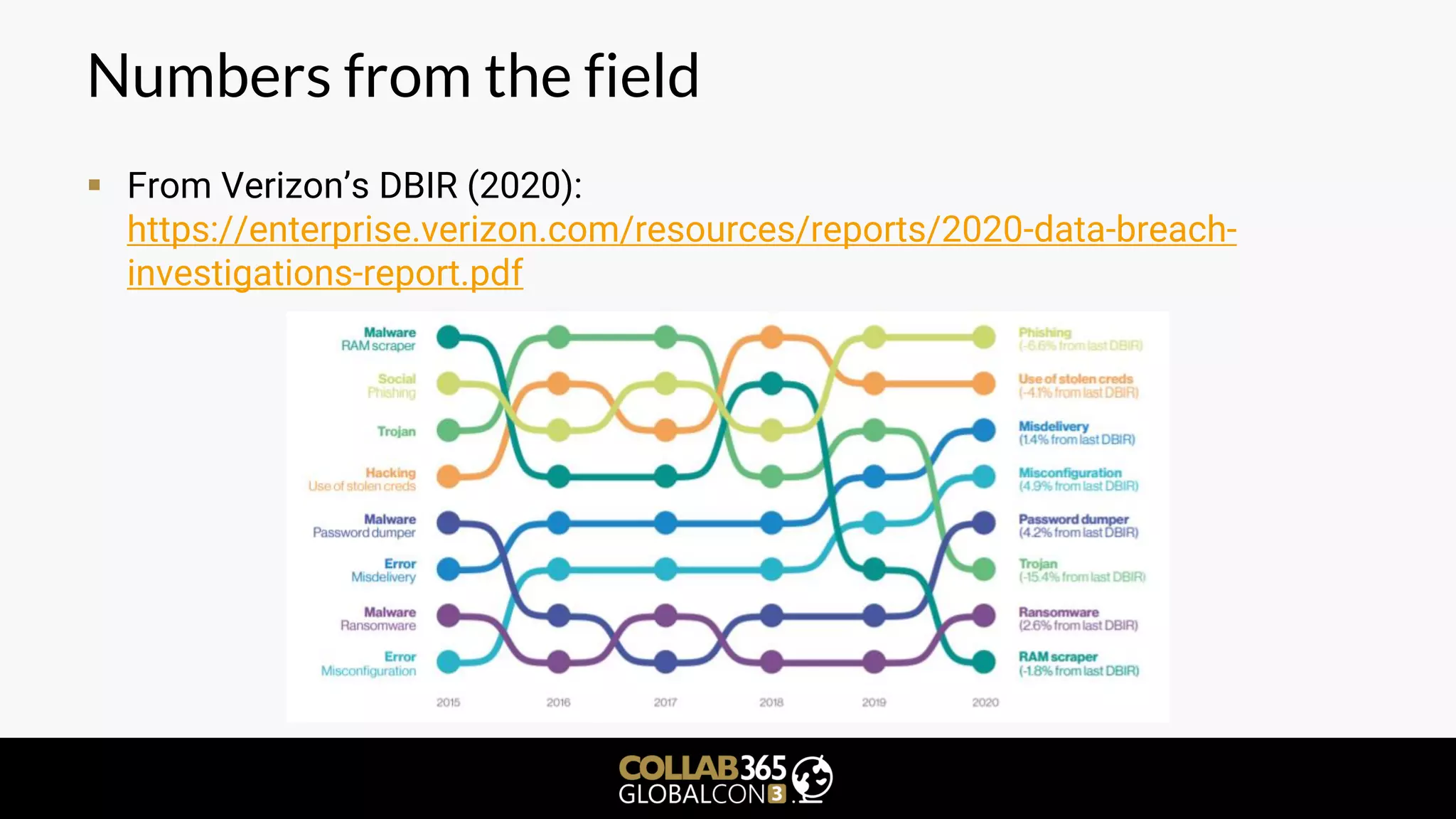
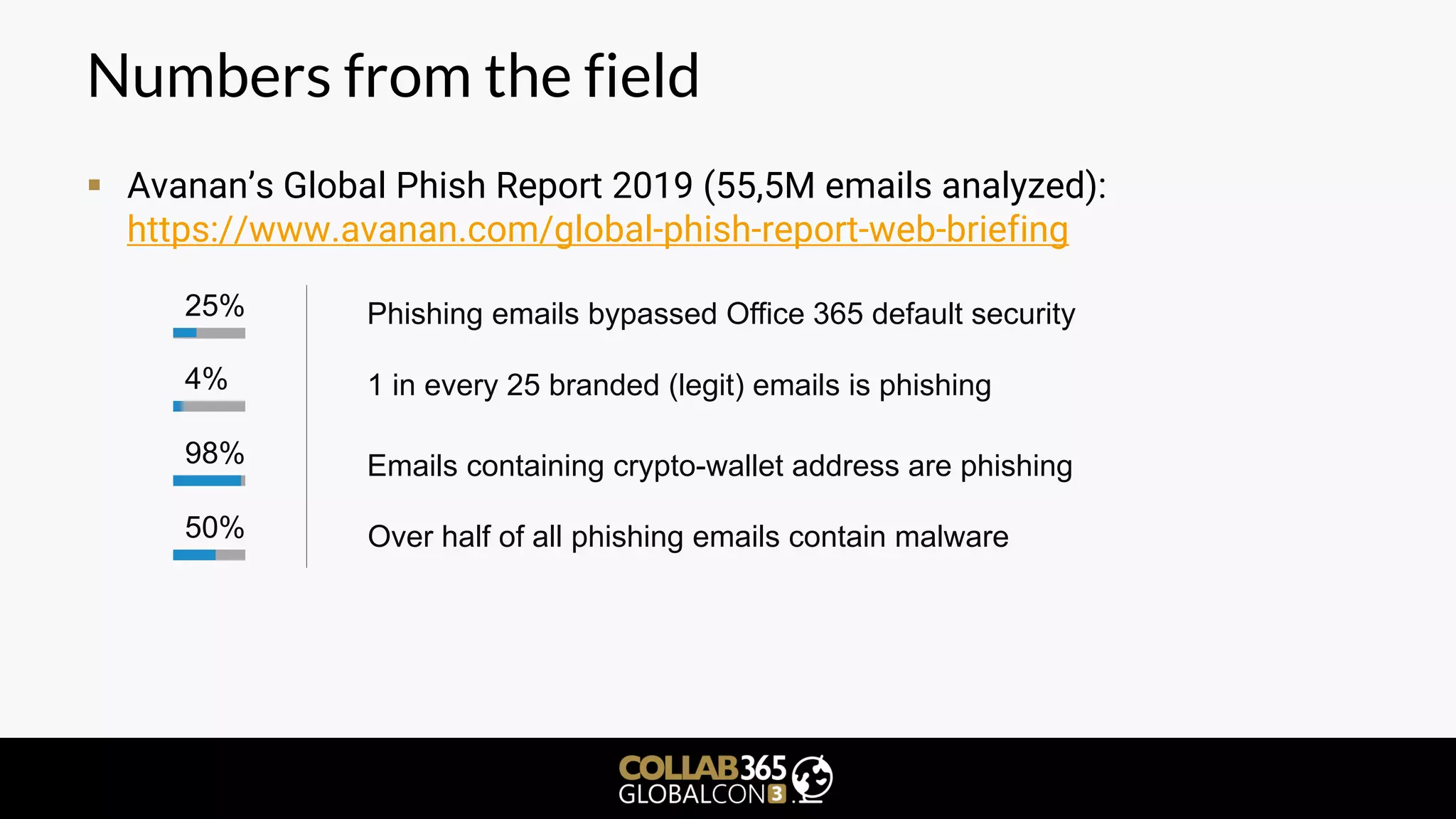
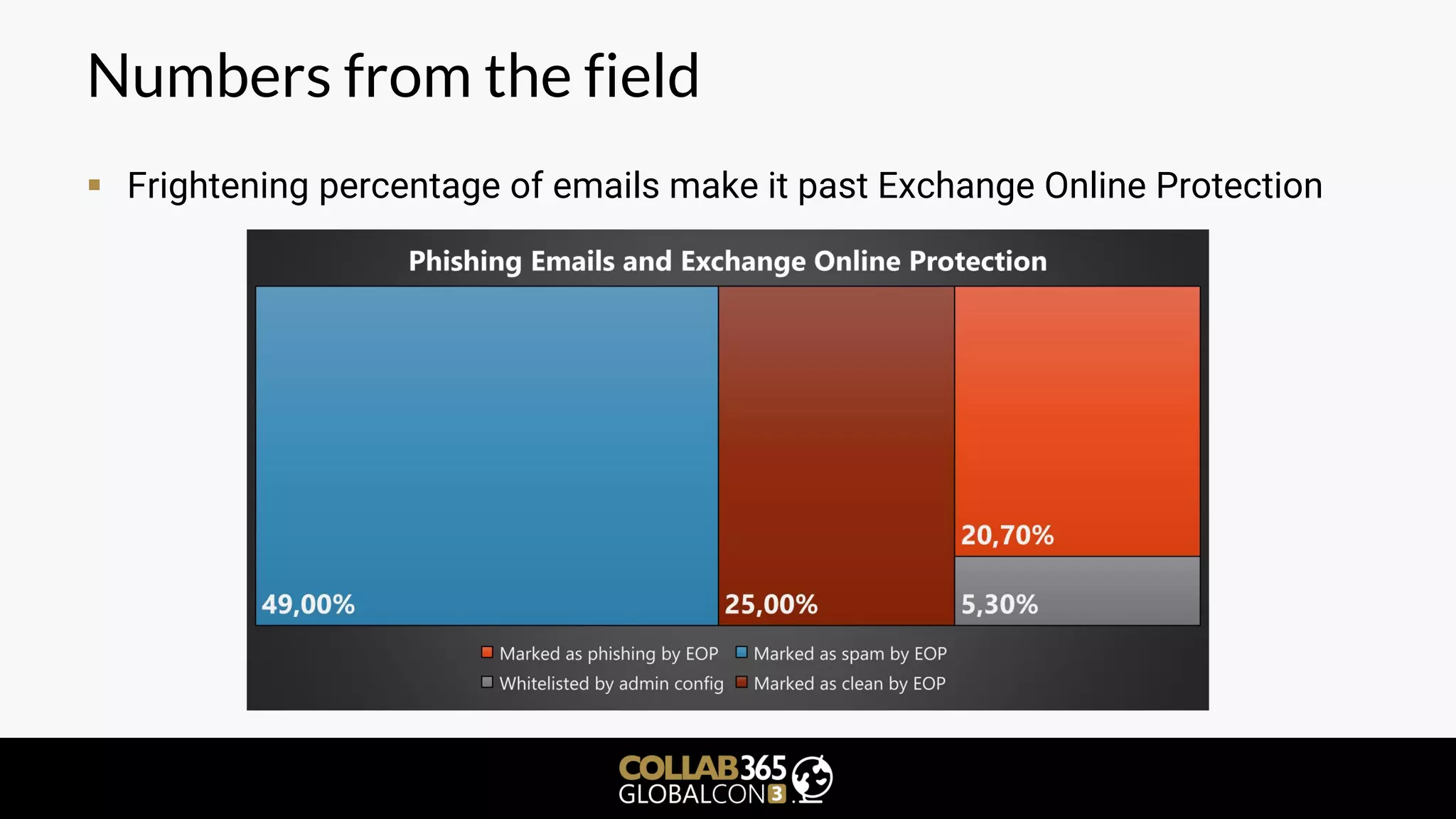
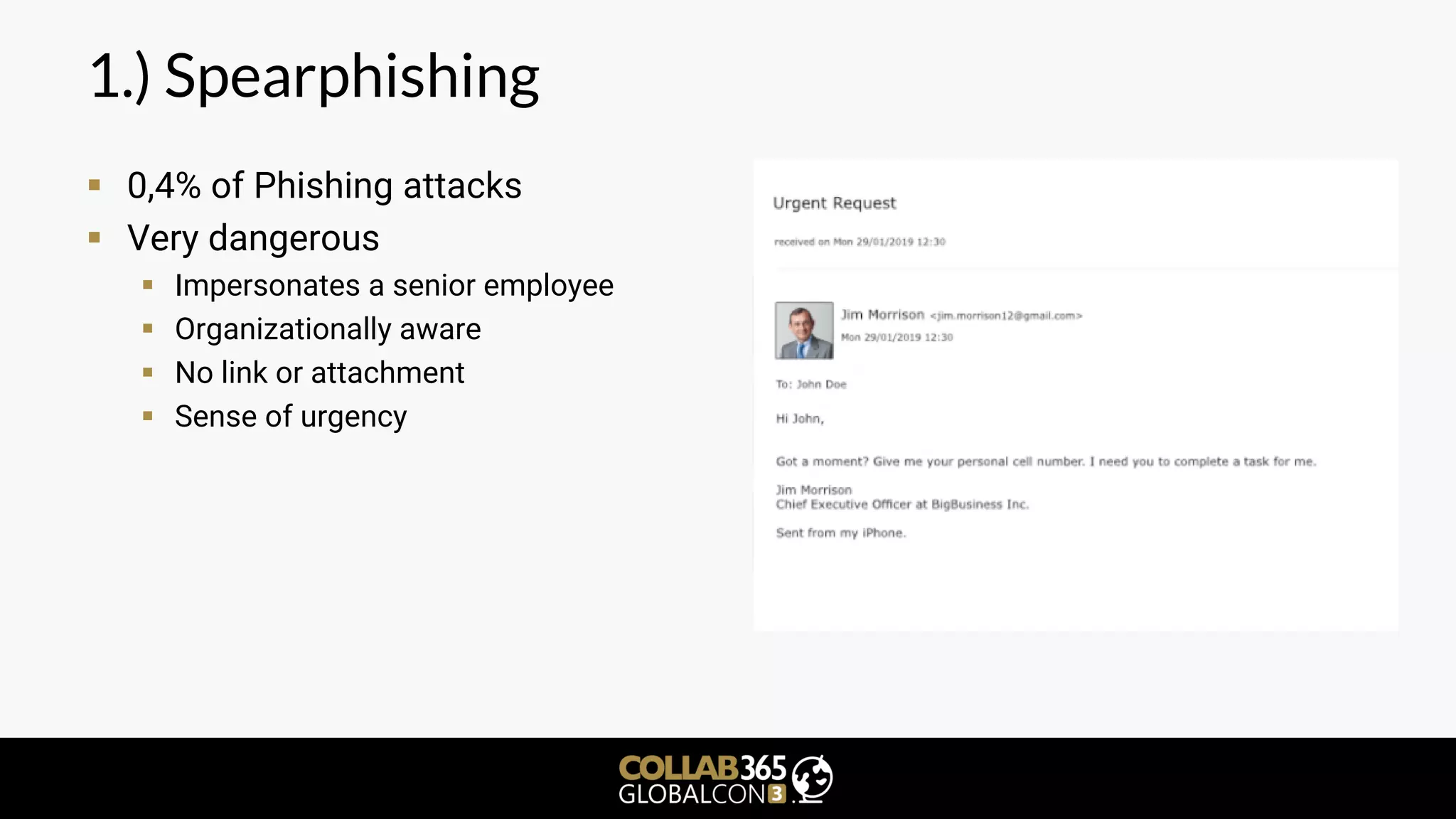
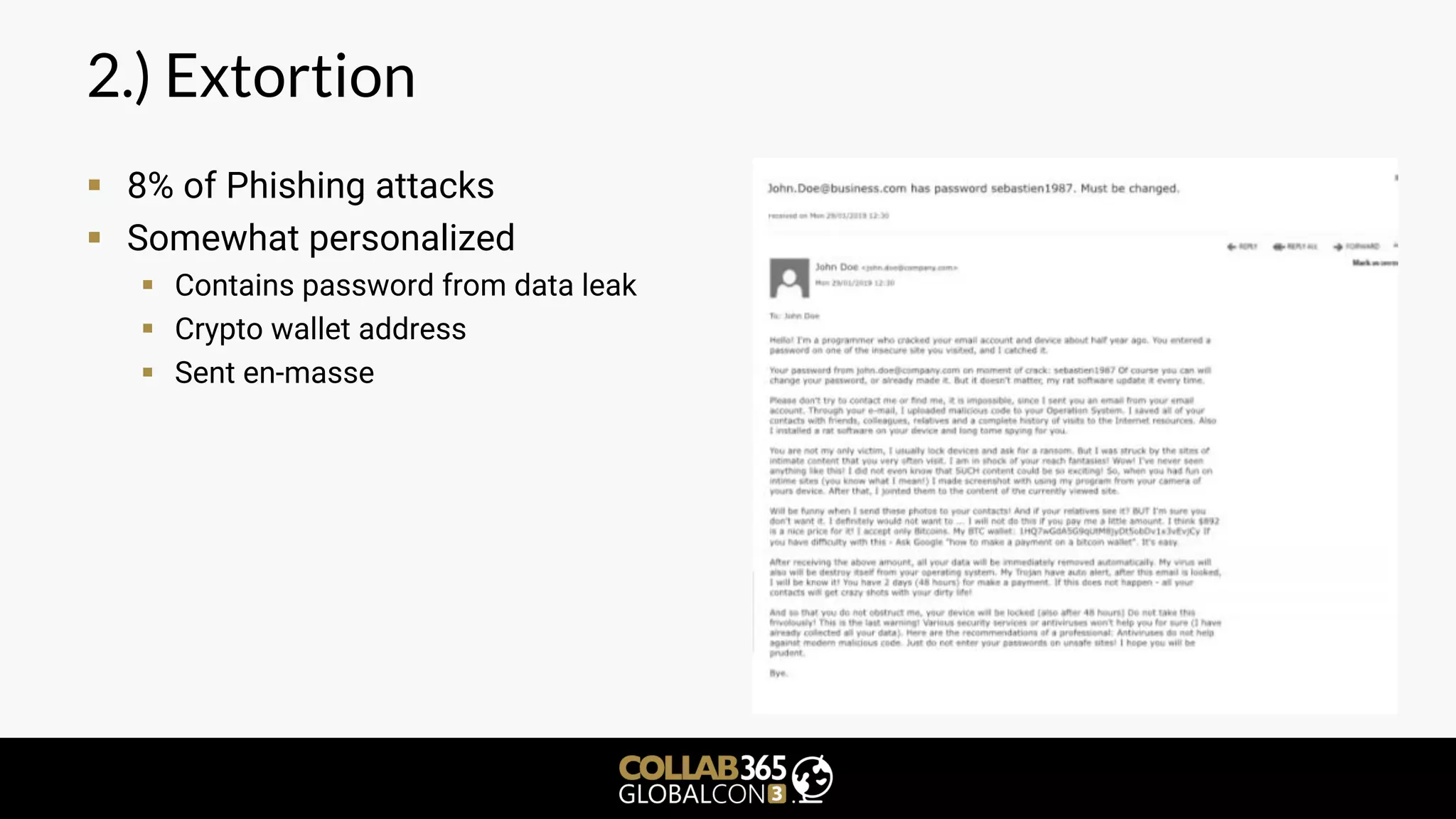
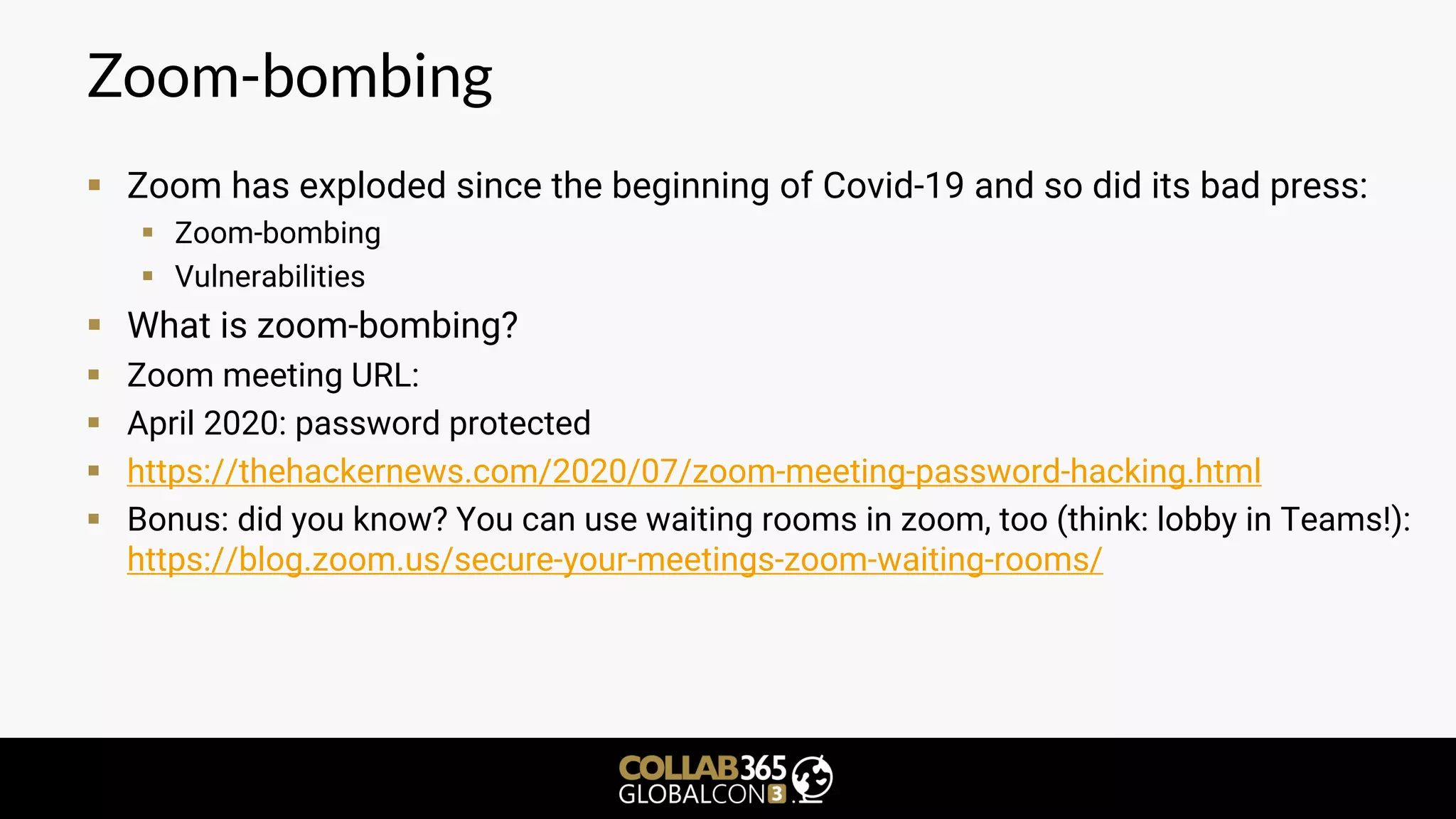
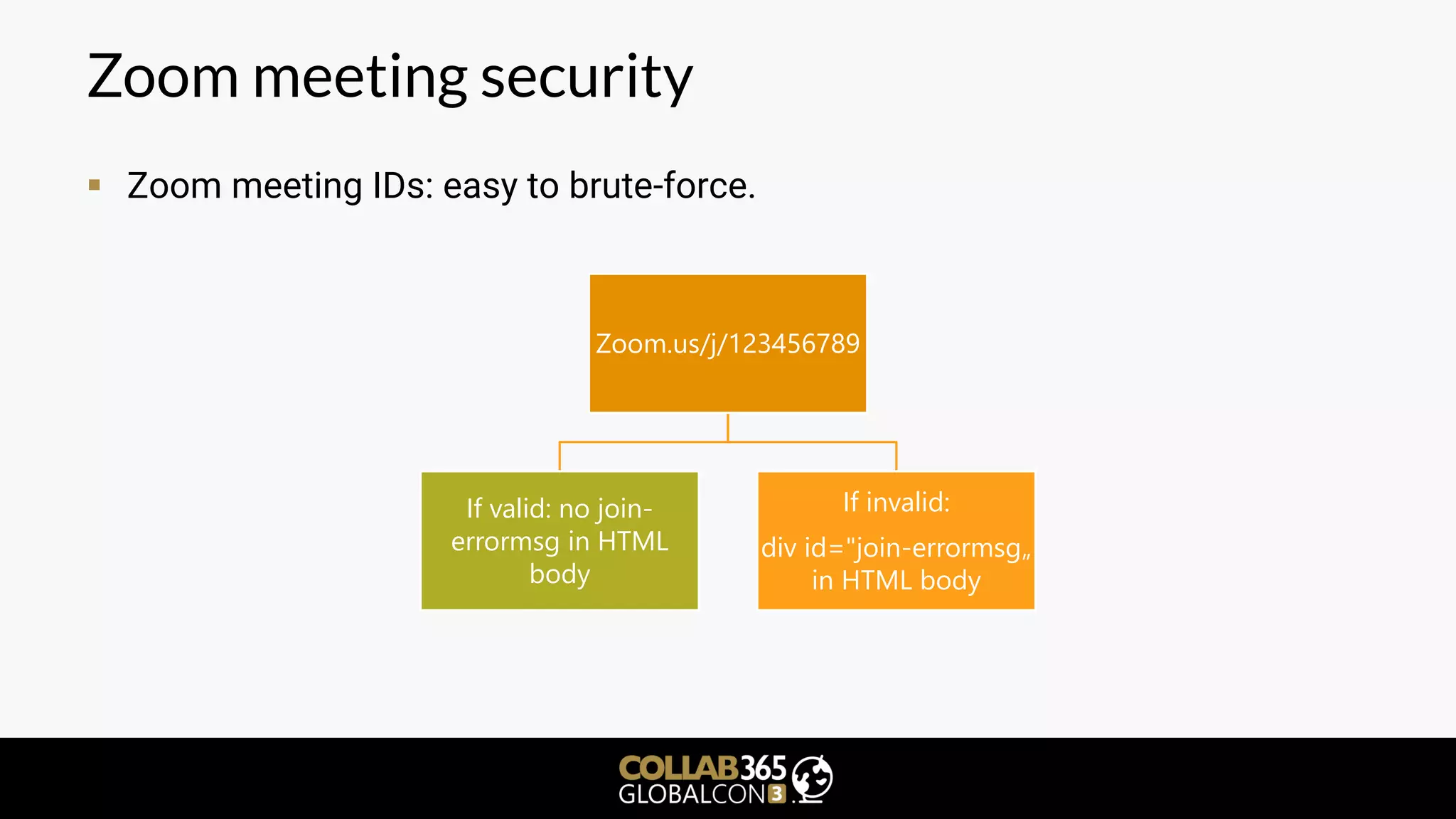
The document is a cybersecurity presentation by Ben Menesi focused on defending Microsoft Teams against threats such as phishing, illicit consent grants, and cross-platform issues. It provides statistics on email security, outlines types of phishing attacks, and suggests best practices for organizations, including educating users and configuring settings to secure Teams meetings. Additional discussion includes the comparative security of Teams versus other platforms like Zoom and recommendations for managing third-party applications and minimizing risks.


















![Decoding Teams Meeting URLs
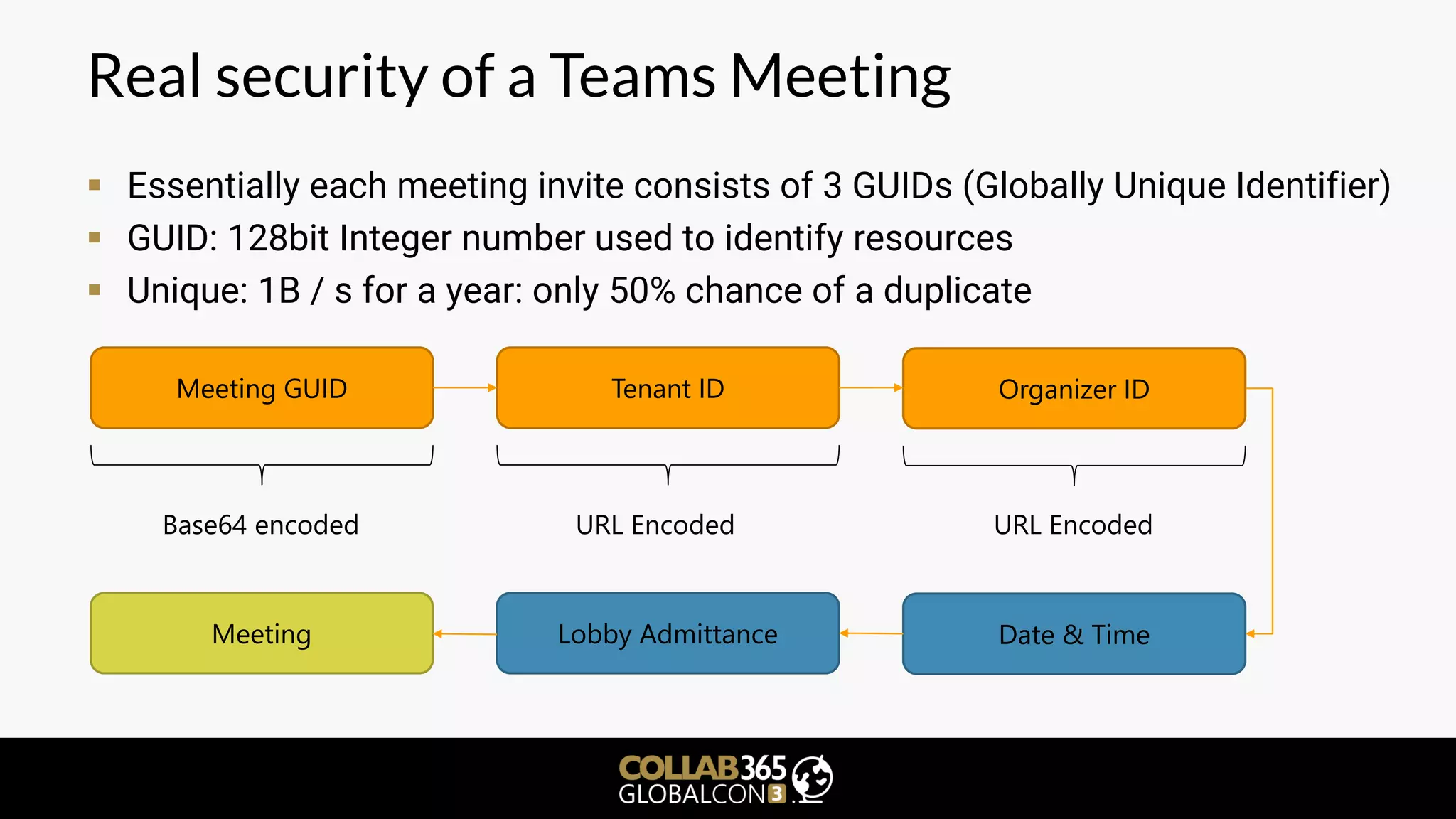
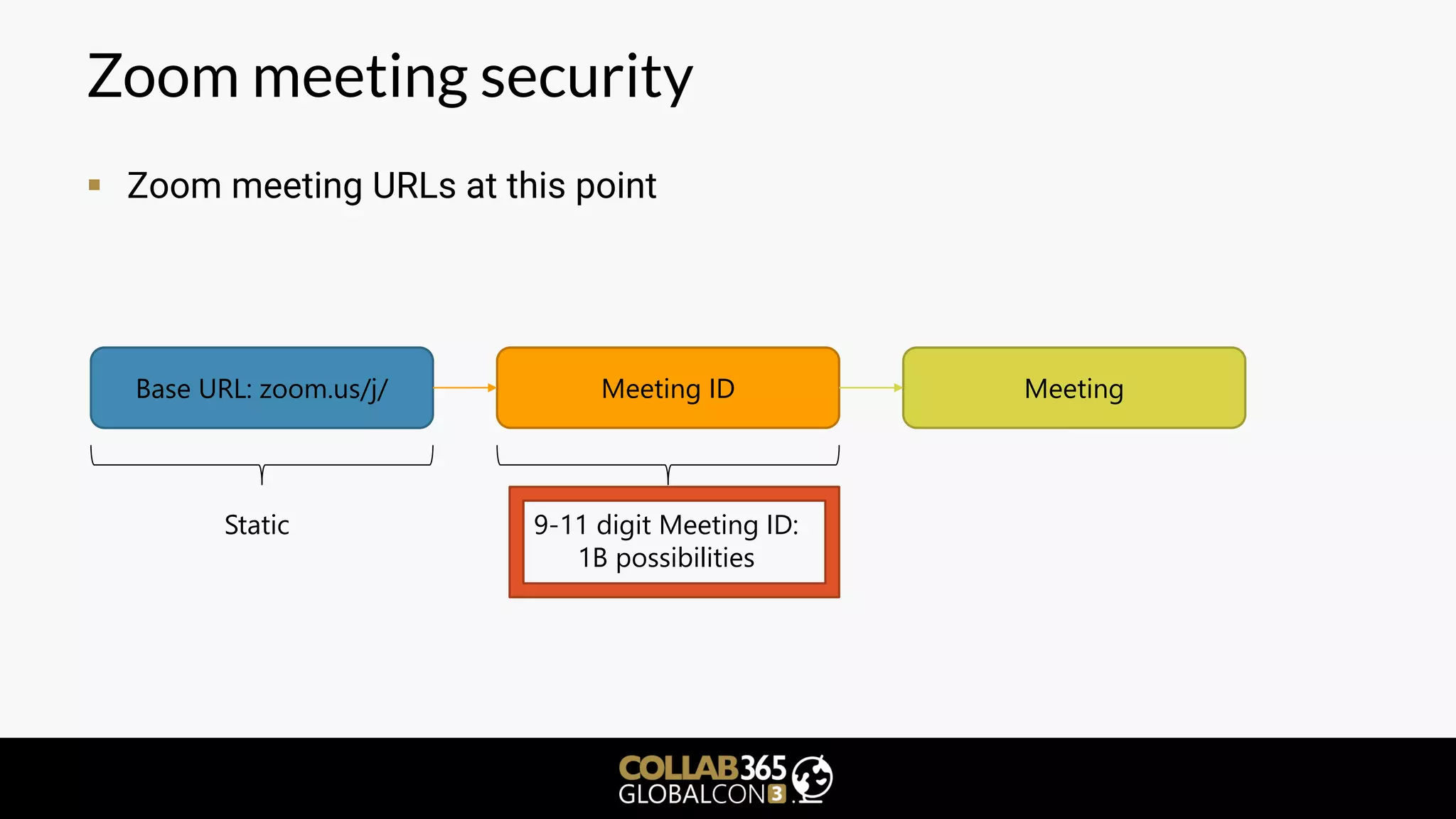
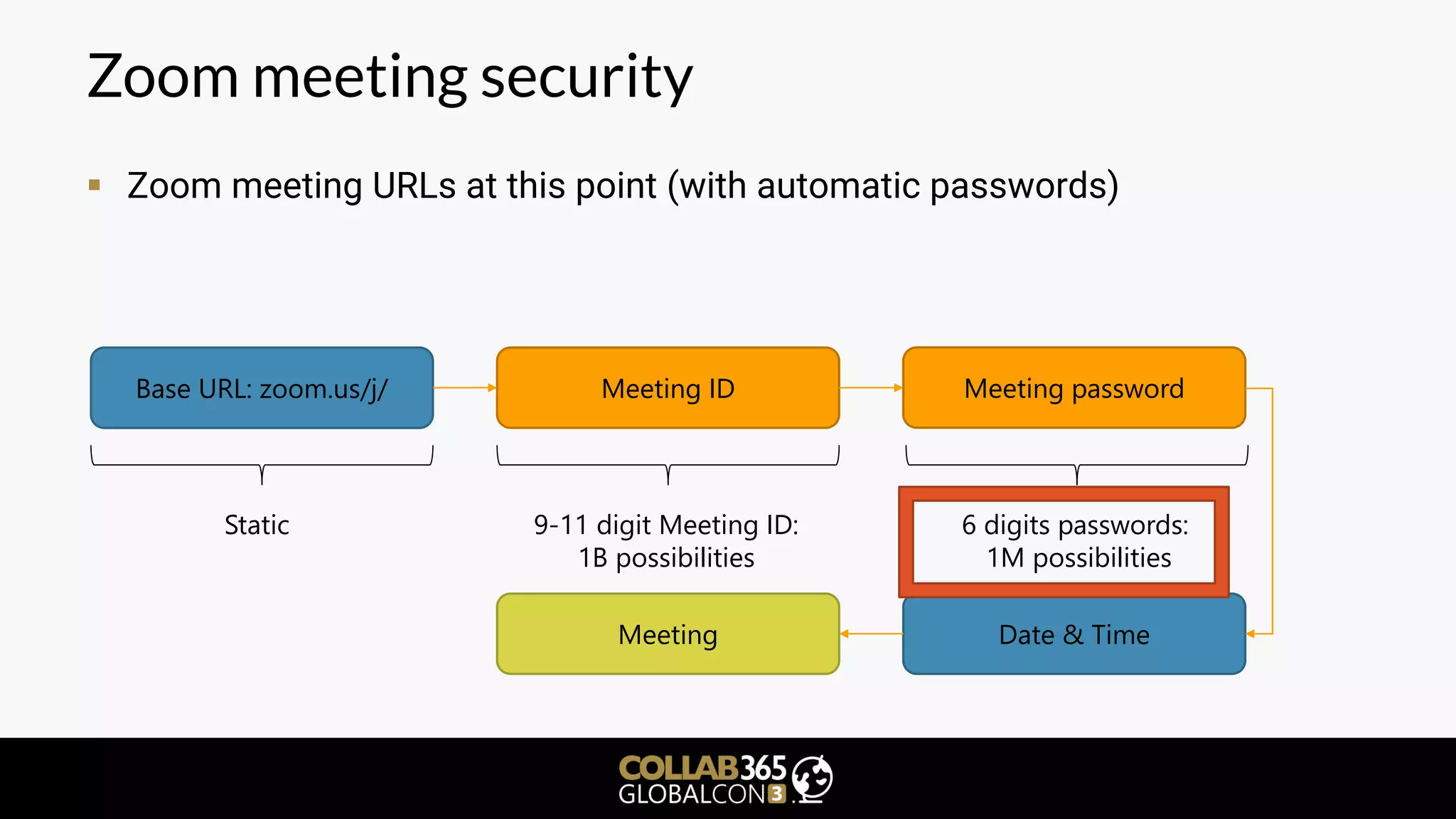
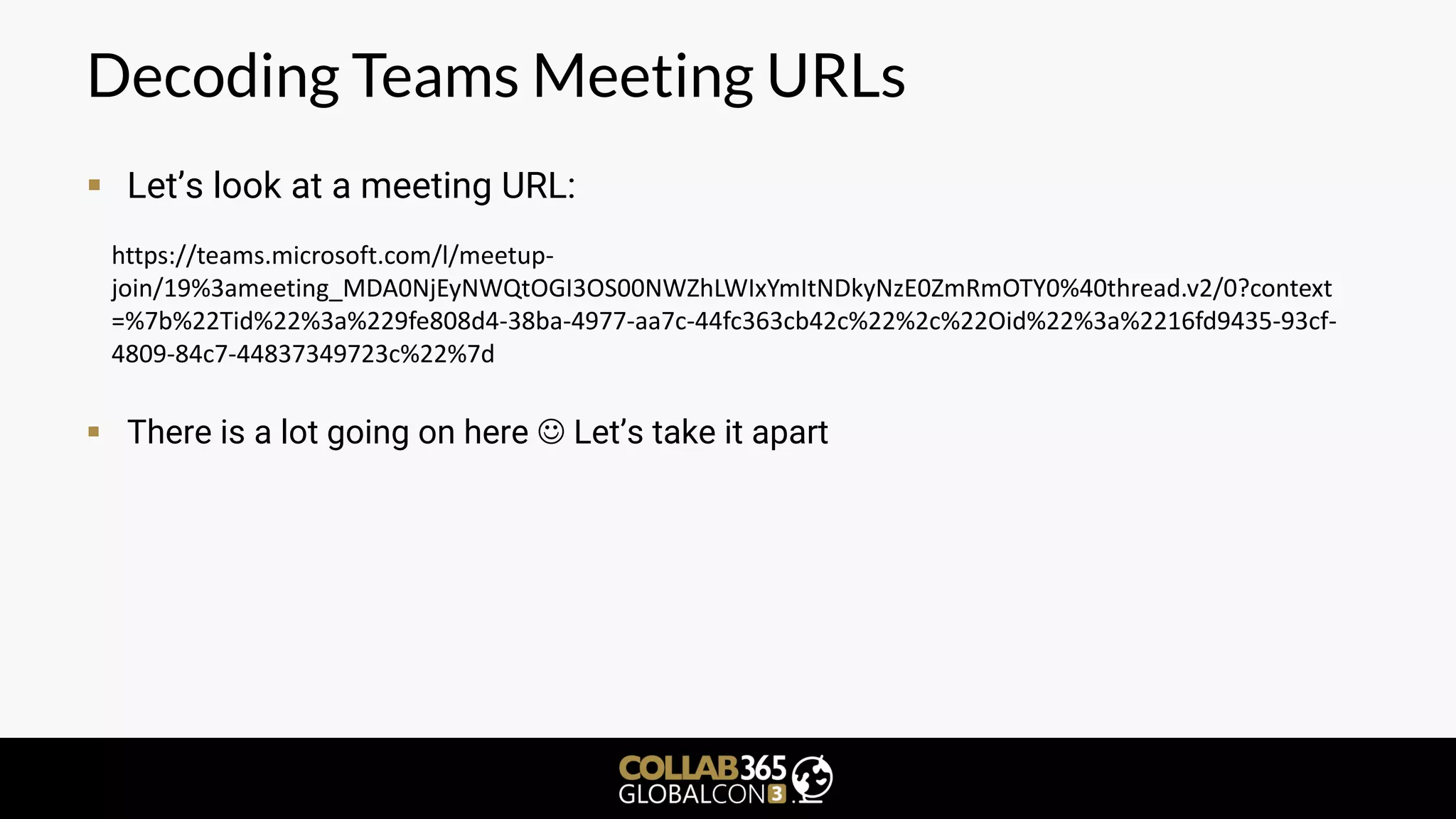
▪ What is a meeting join URL made of?
▪ Points 1 and 3 always appear to be the same
▪ Point 2: meeting resource ID (Base64 encoded): 3c9462ca-c7a4-42b7-9ad2-
e2a22e466cf0
▪ Point 3: static values
▪ Point 4: Organizer context (TiD: TenantID [GUID], OiD: Organizer ID [GUID])
1.) Base: https://teams.microsoft.com/l/meetup-join/19%3
2.) Meeting ID: ameeting_MDA0NjEyNWQtOGI3OS00NWZhLWIxYmItNDkyNzE0ZmRmOTY0%40
3.) Thread version: thread.v2/0?
4.) Context: context=%7b%22Tid%22%3a%229fe808d4-38ba-4977-aa7c-
44fc363cb42c%22%2c%22Oid%22%3a%2216fd9435-93cf-4809-84c7-44837349723c%22%7d](https://image.slidesharecdn.com/benmenesiteamssecurityglobalcon3v1-200911155457/75/Protecting-Microsoft-Teams-from-Cyber-Security-Threats-a-Practical-Guide-58-2048.jpg)