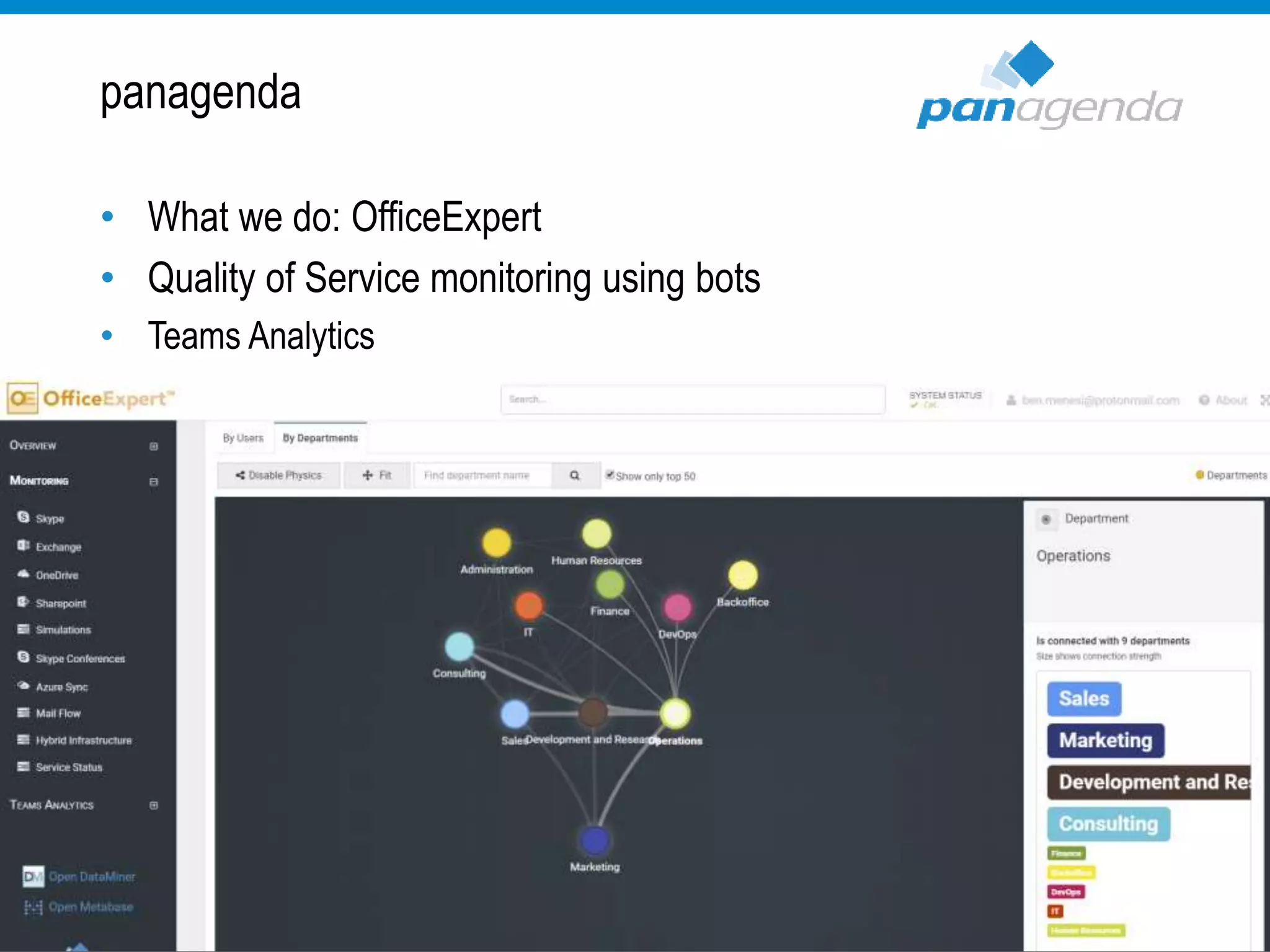
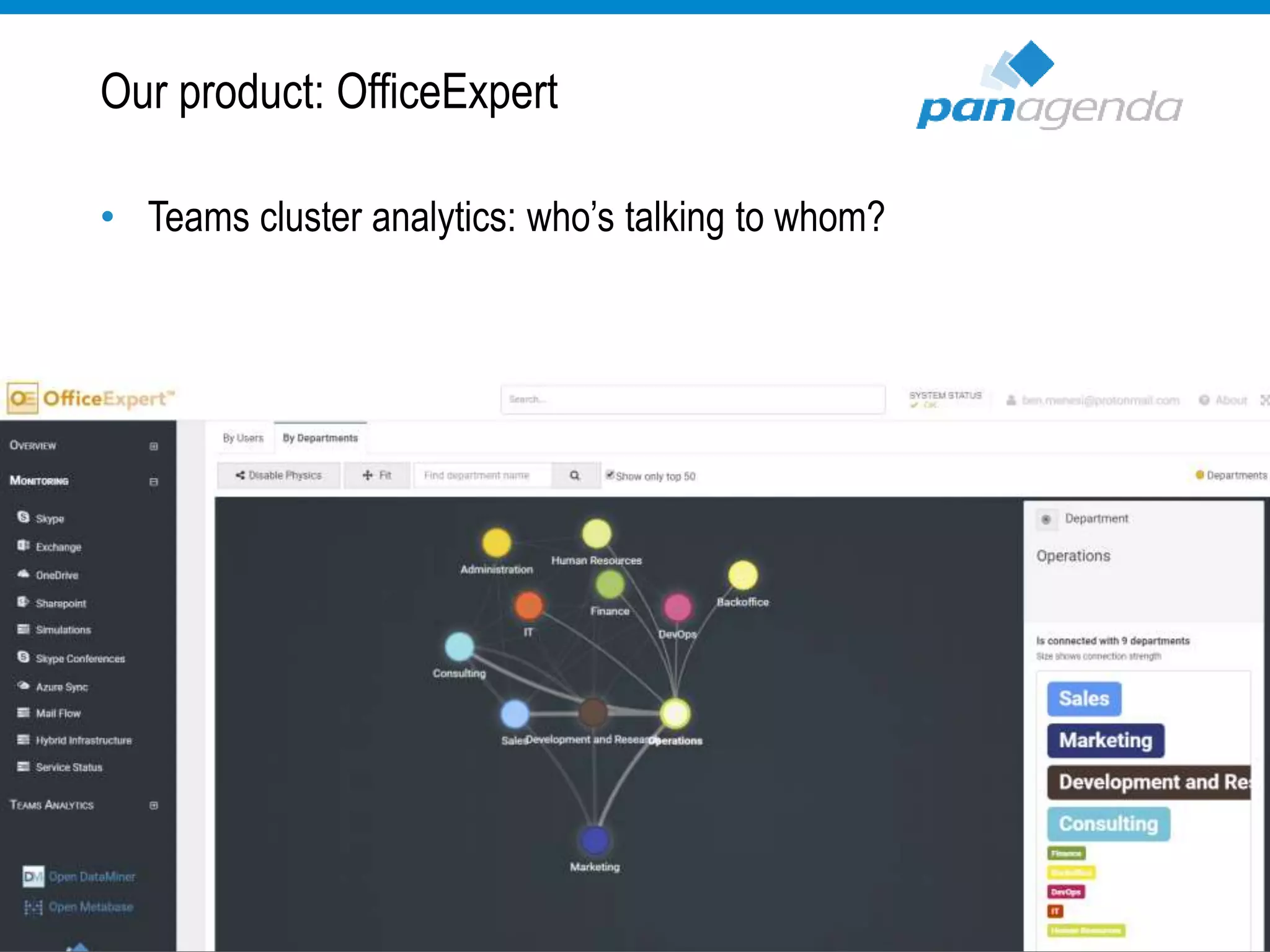
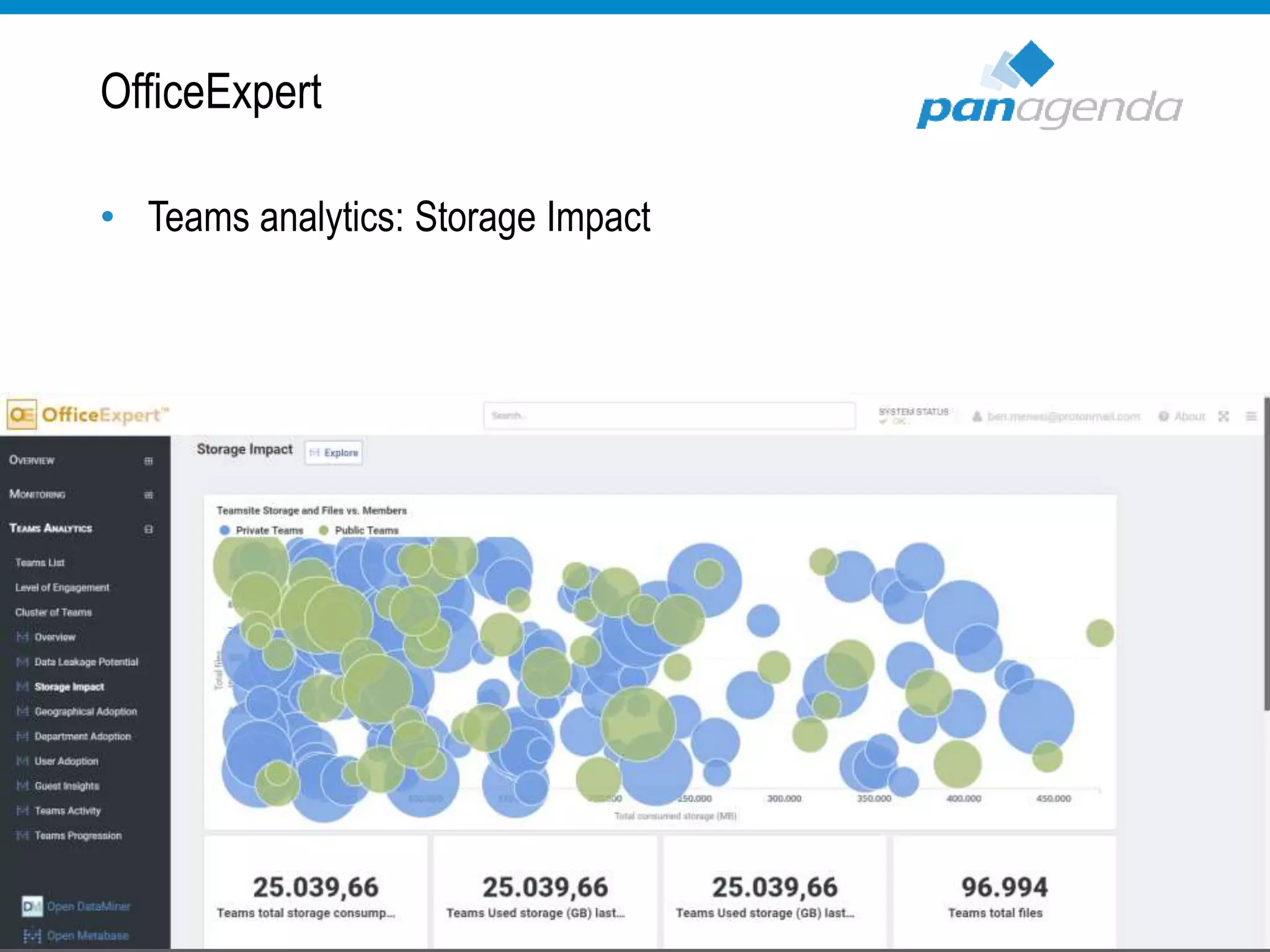
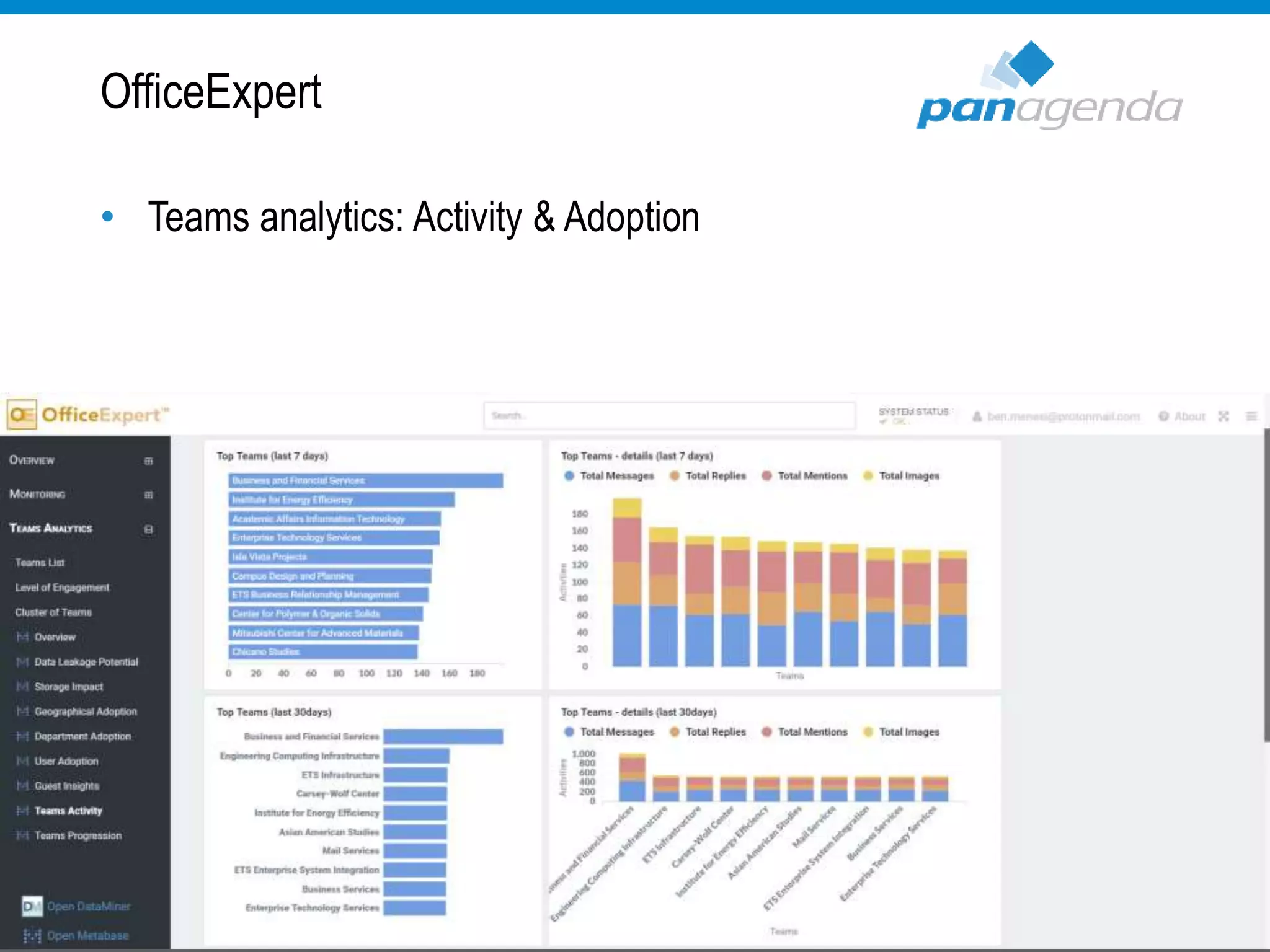
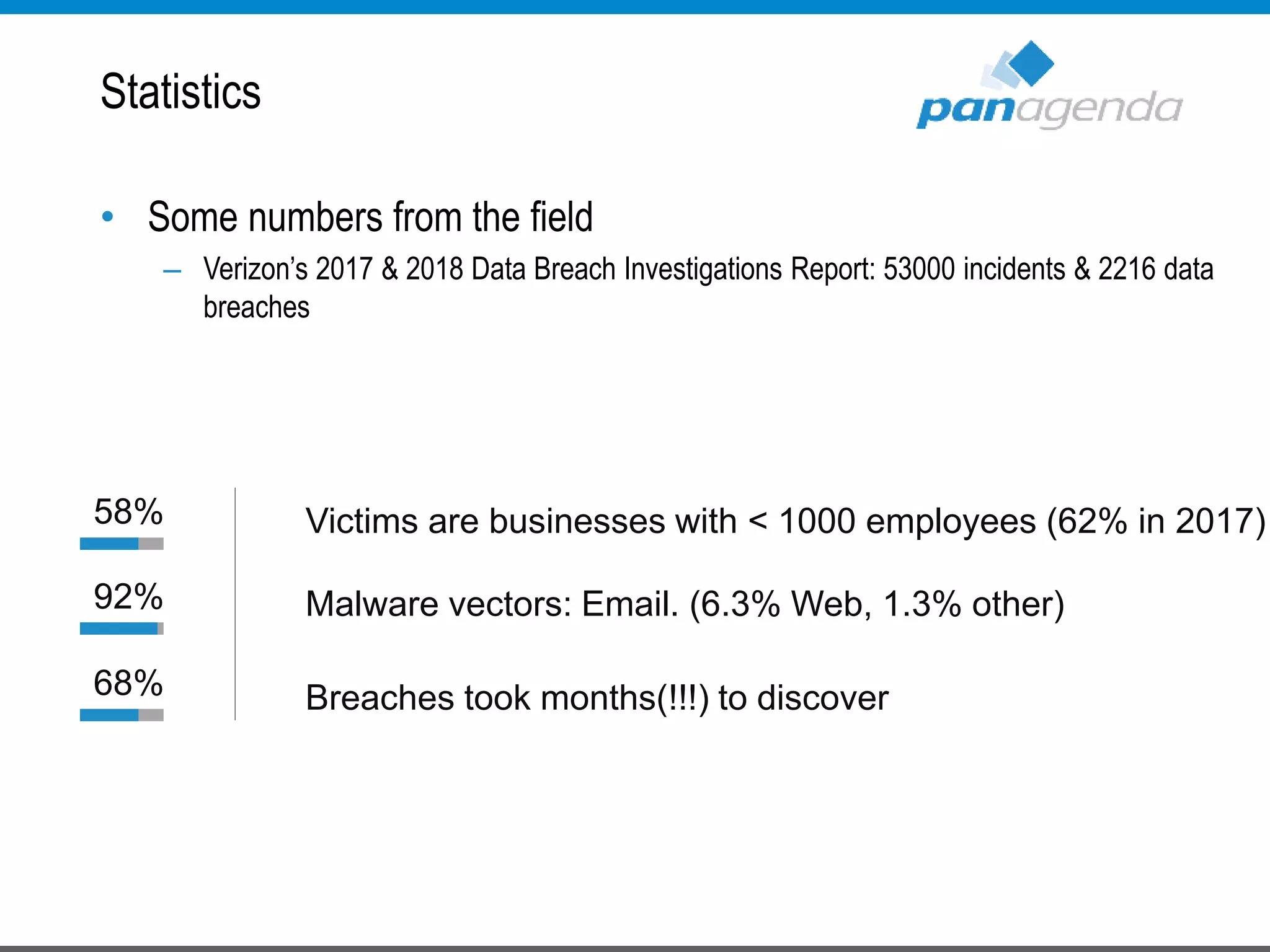
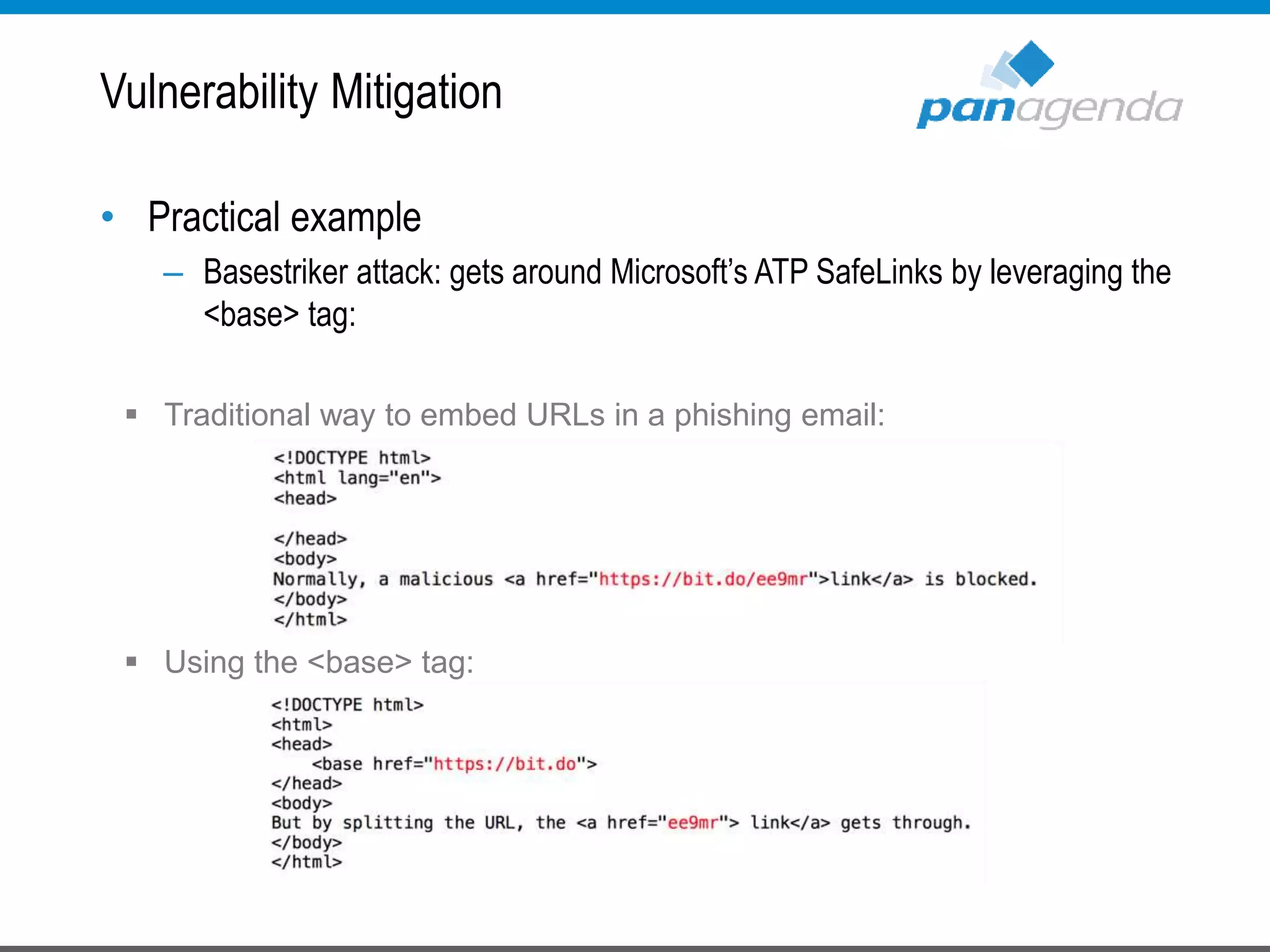
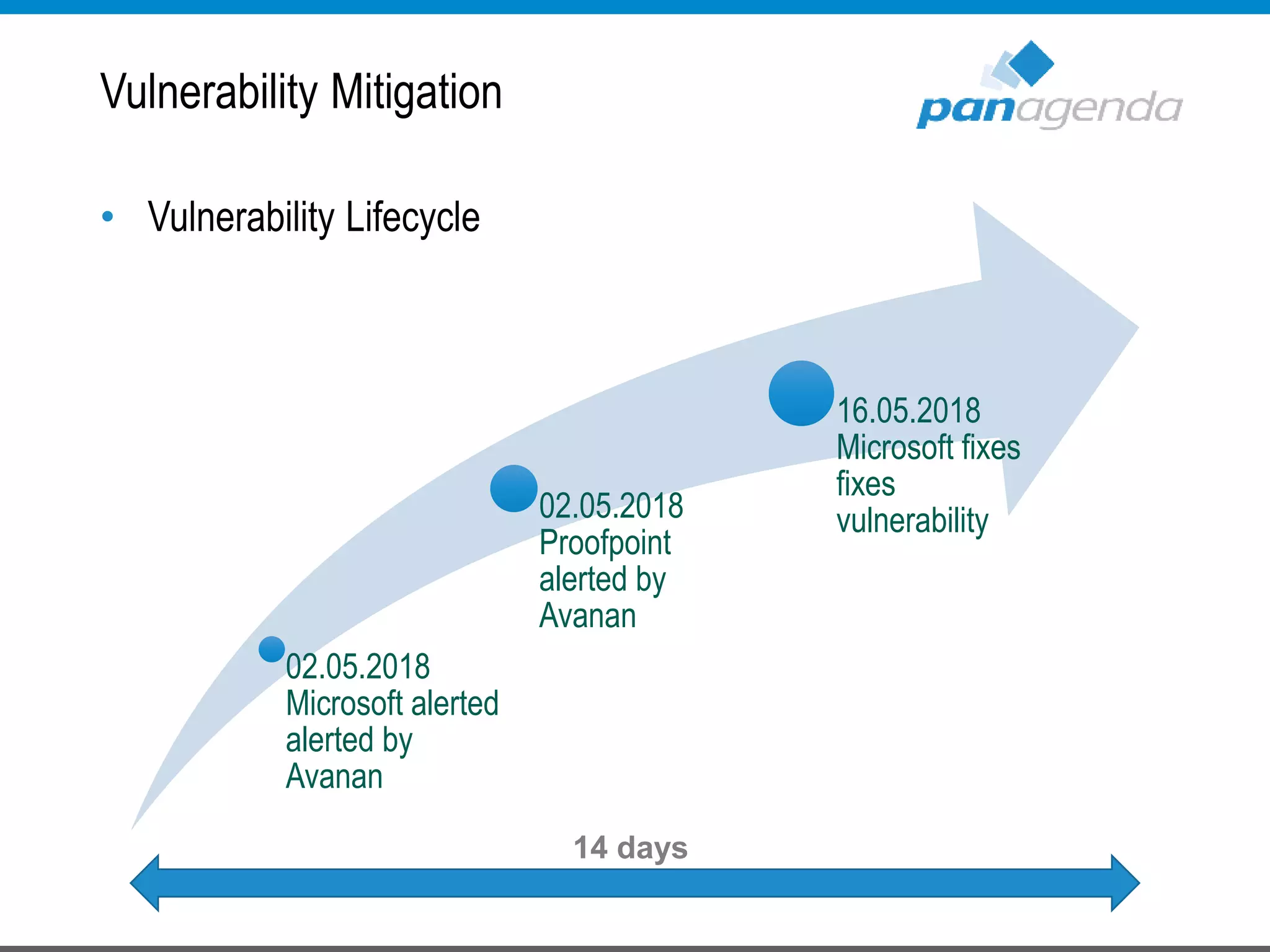
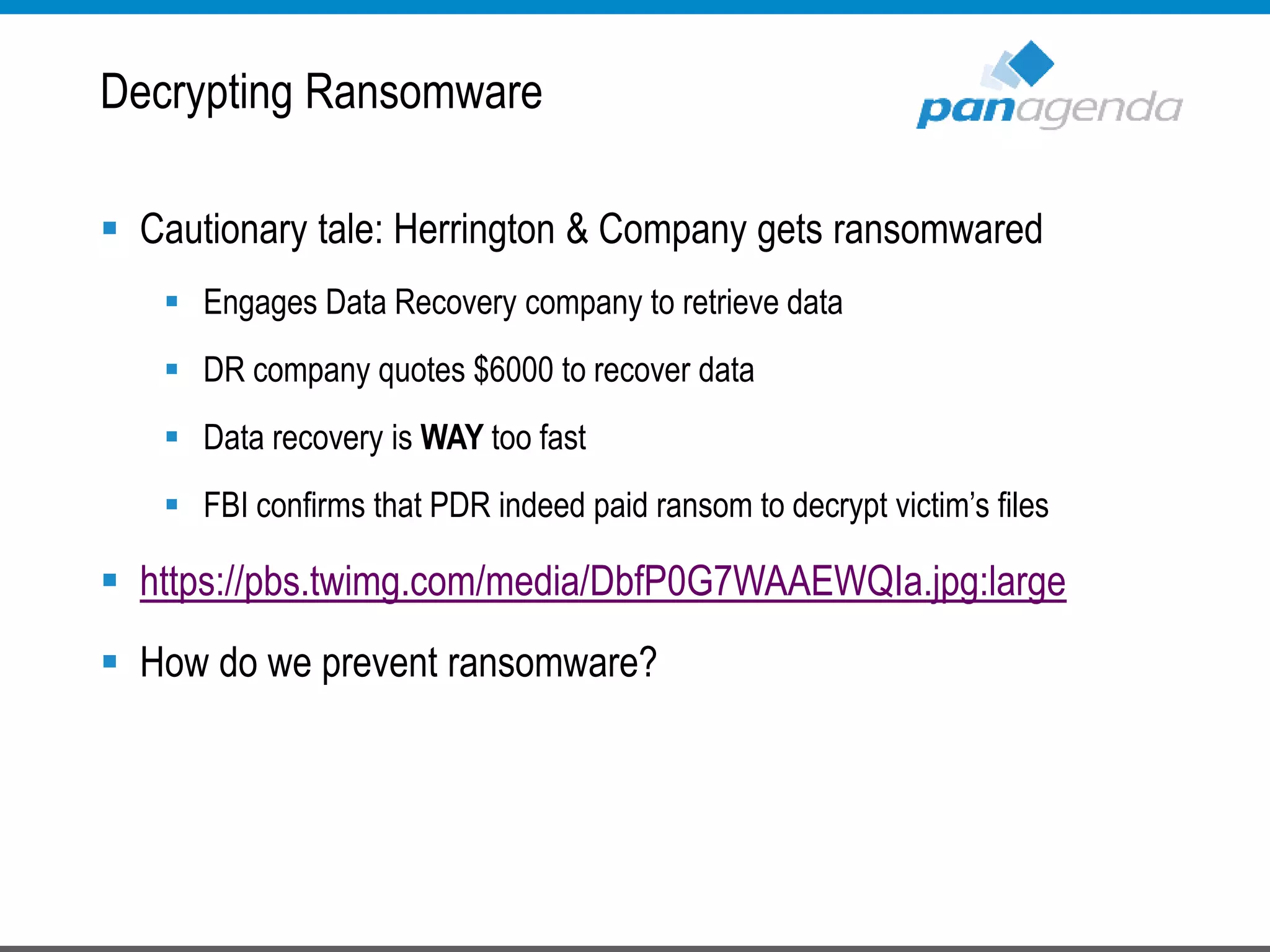
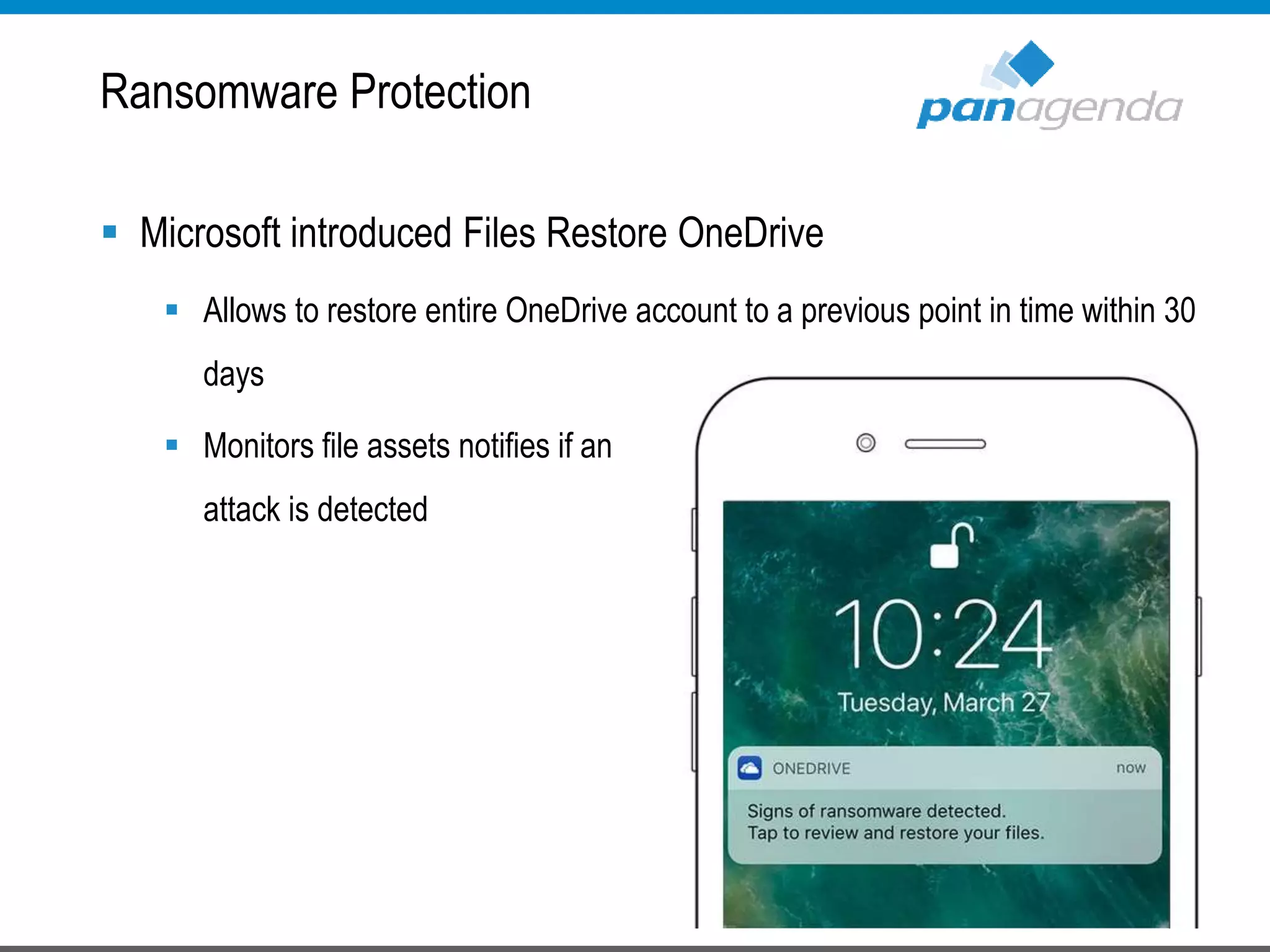
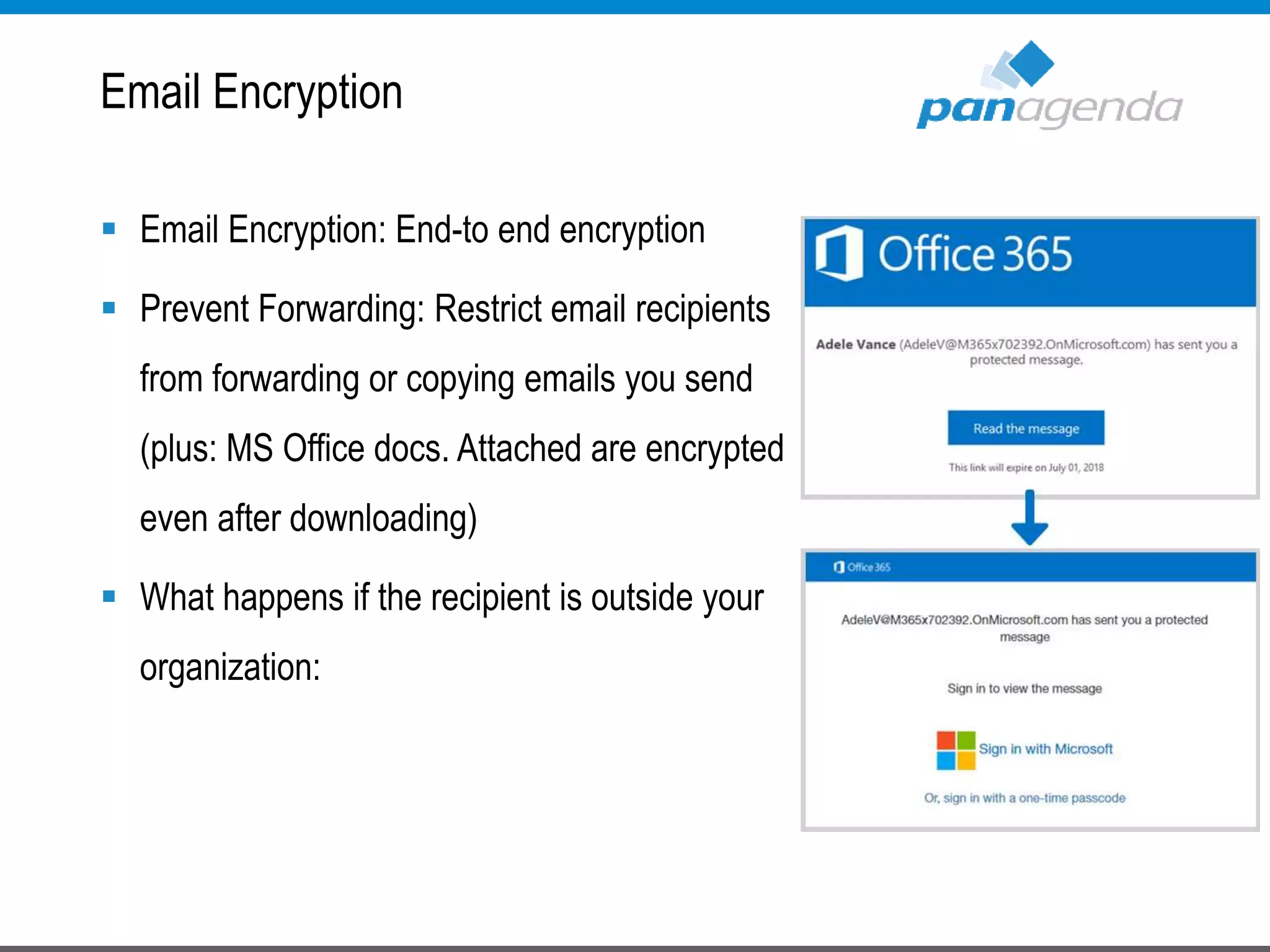
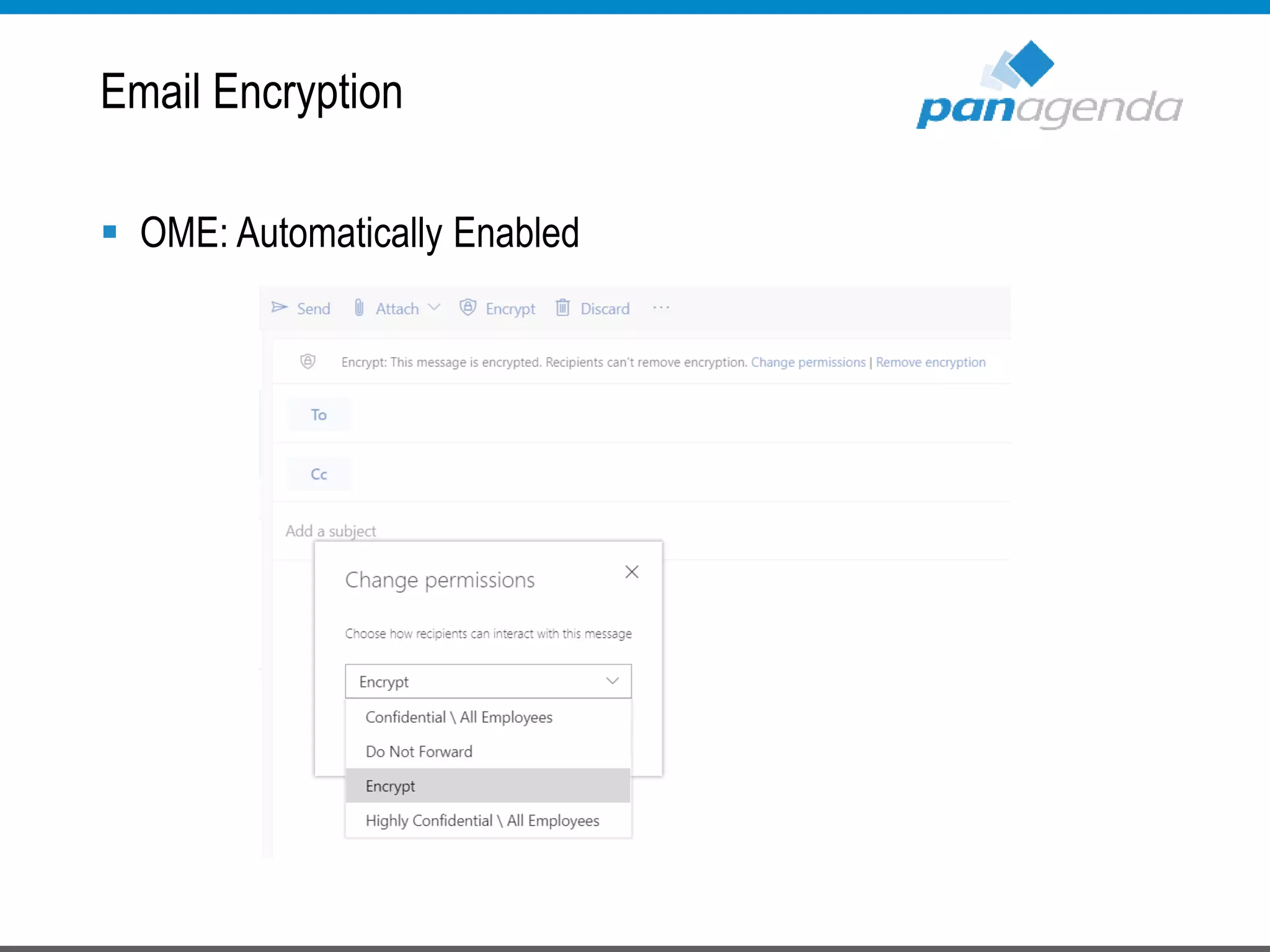
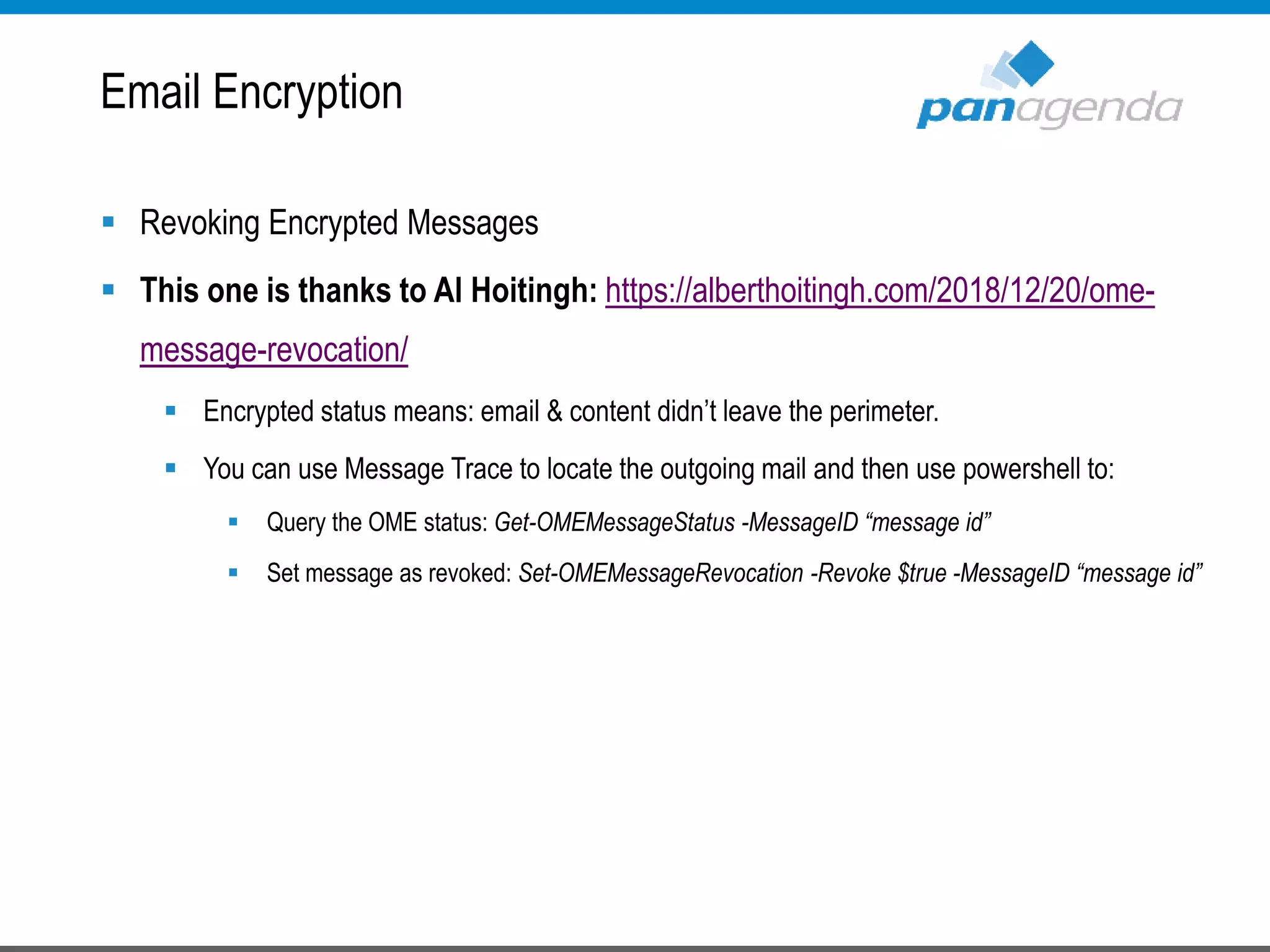
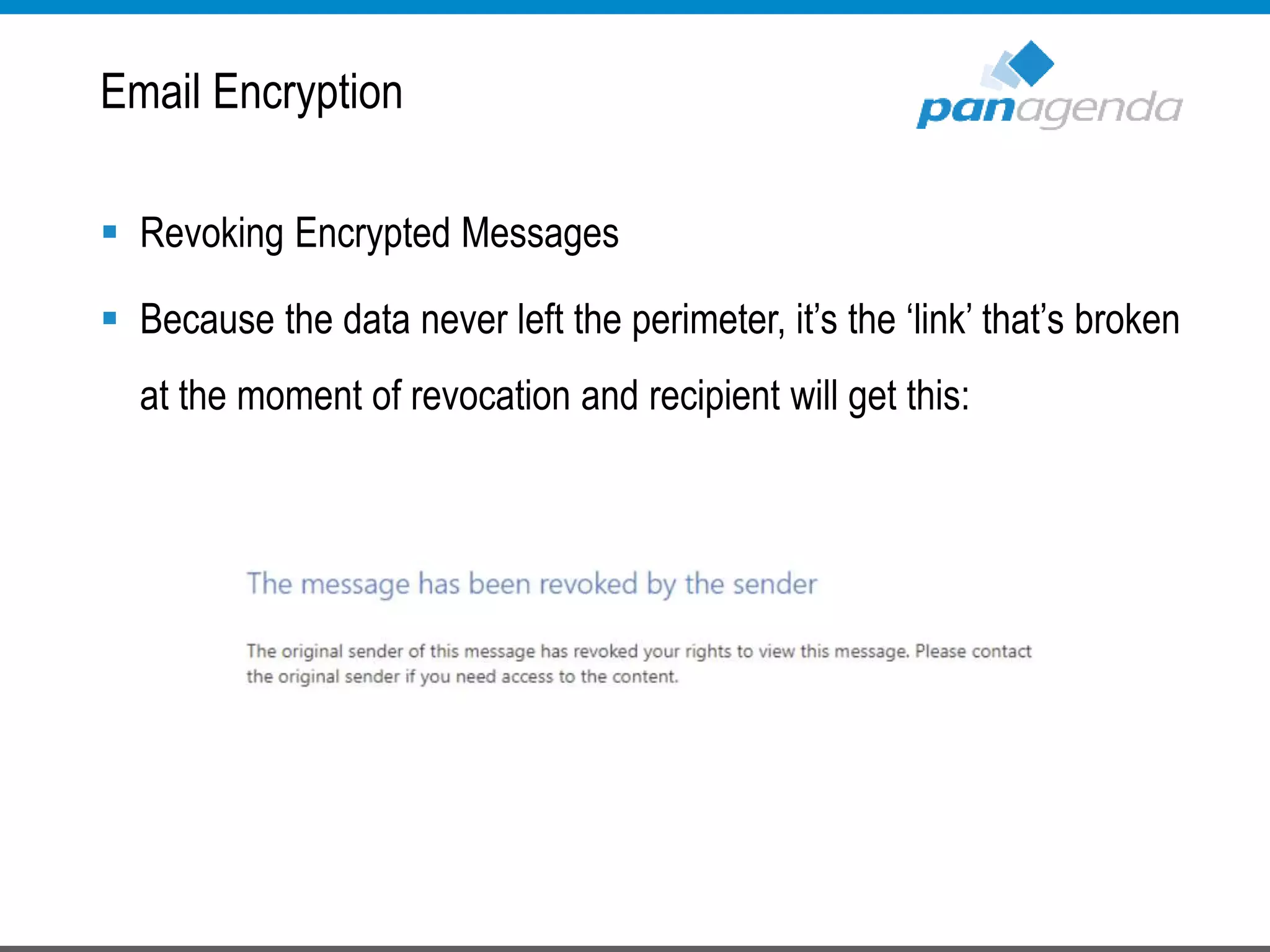
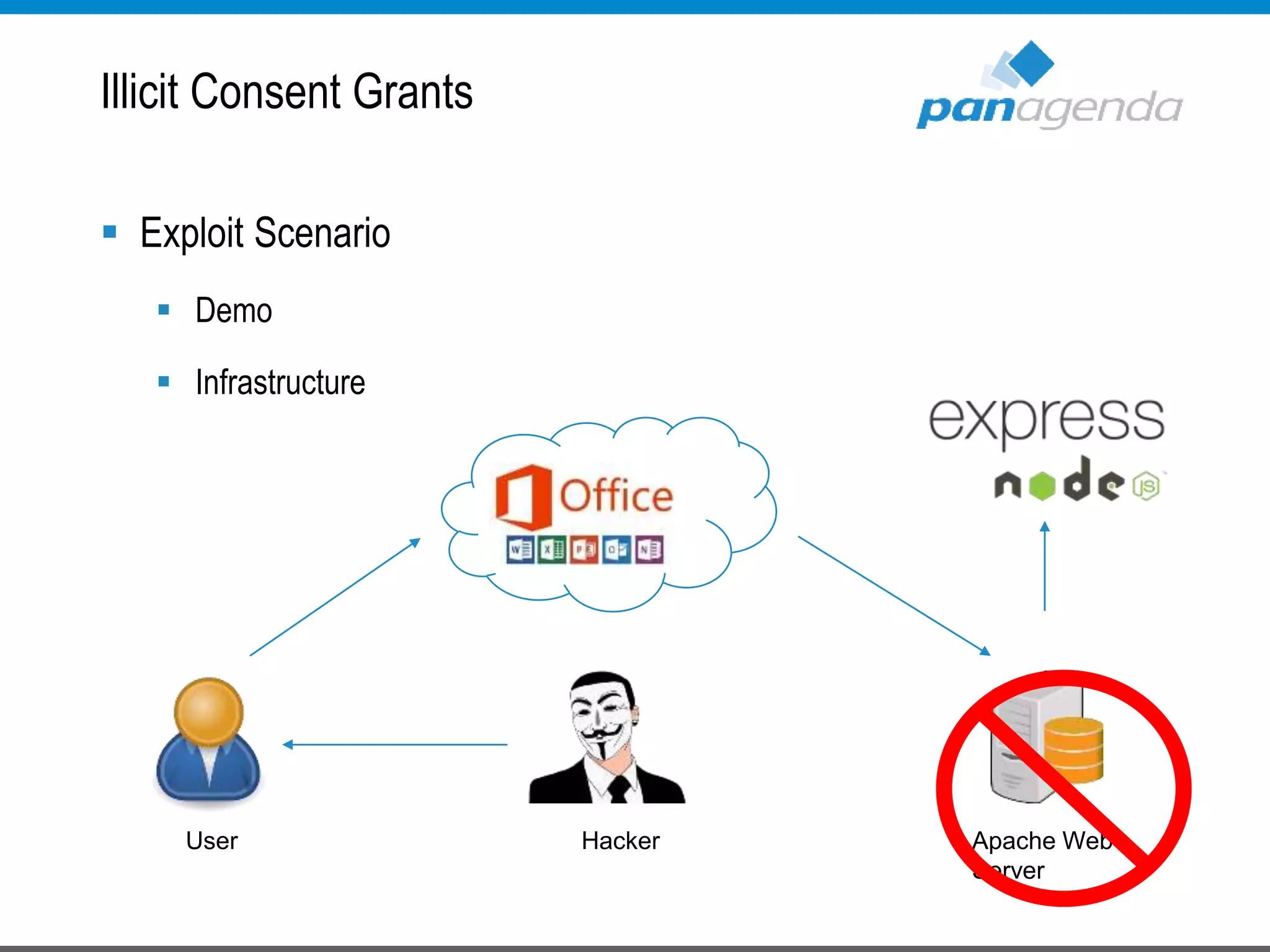
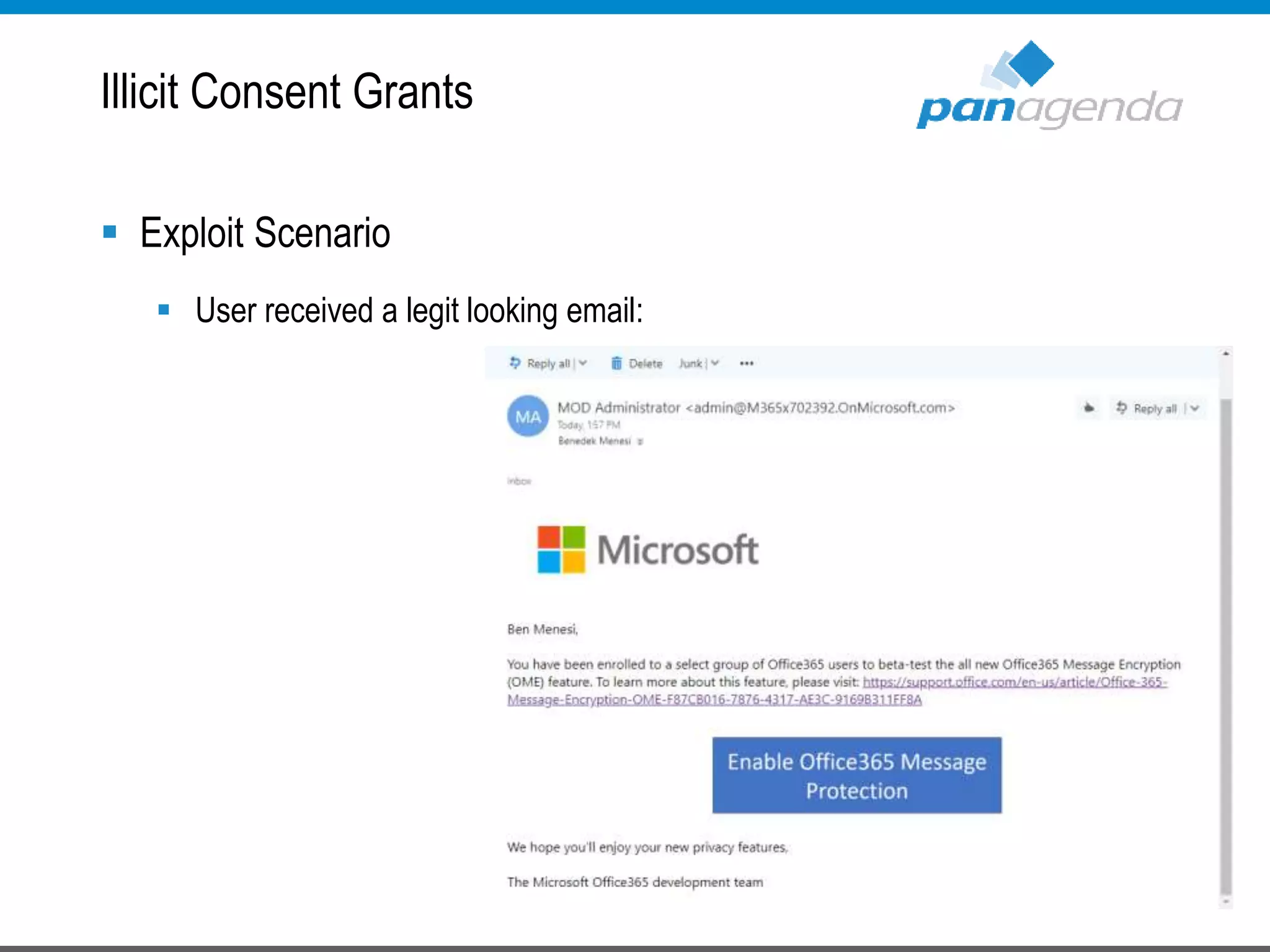
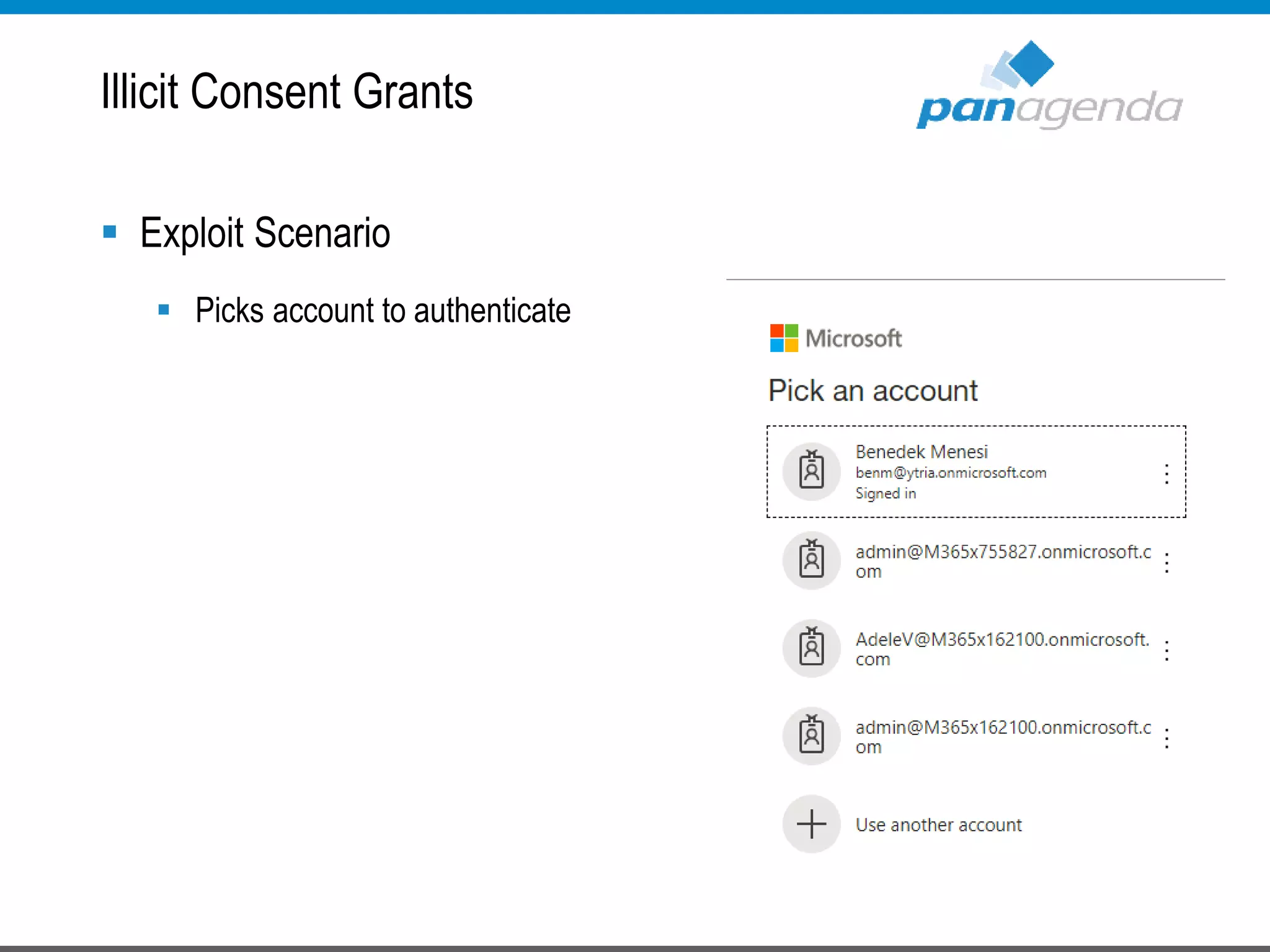
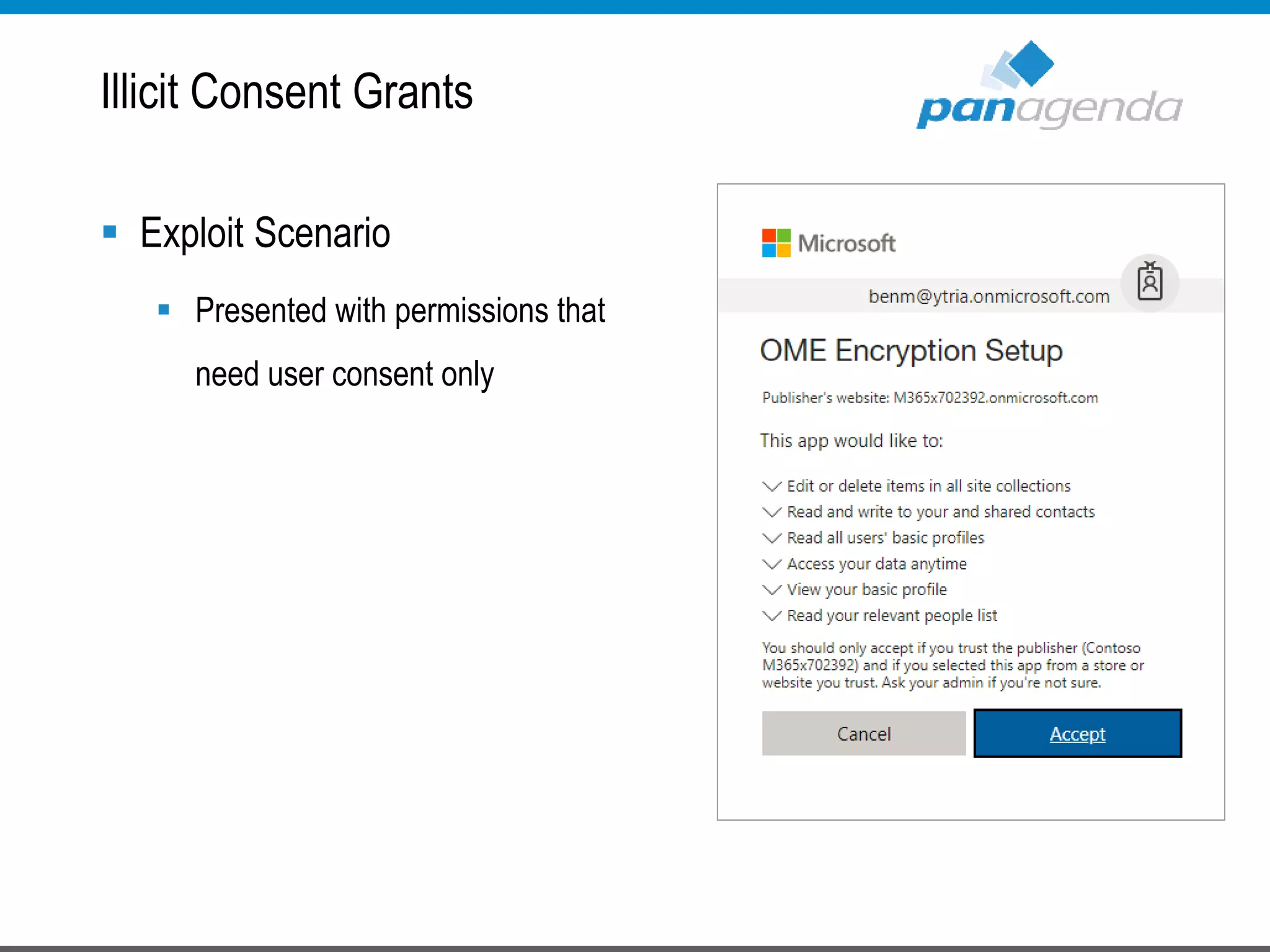
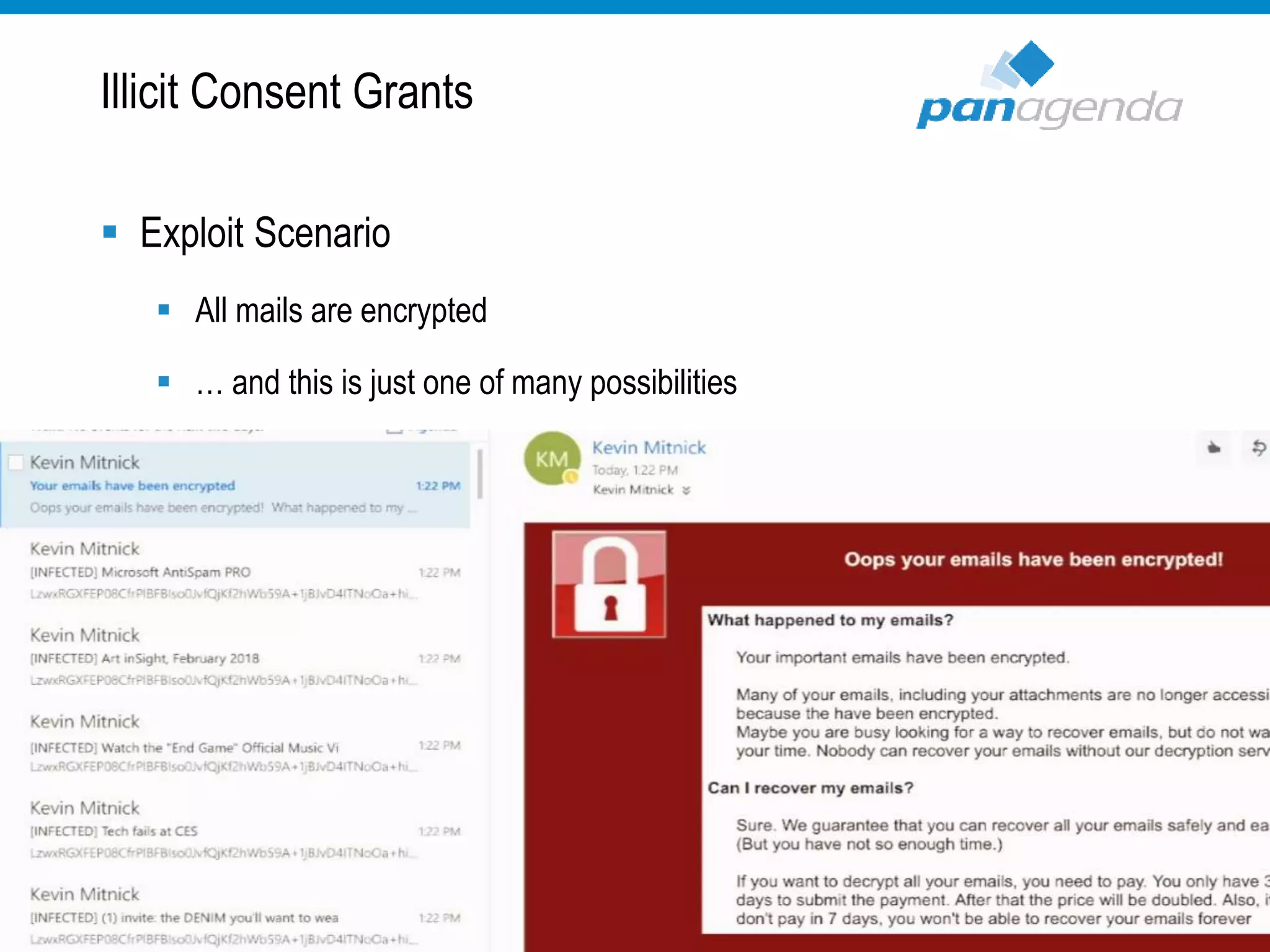
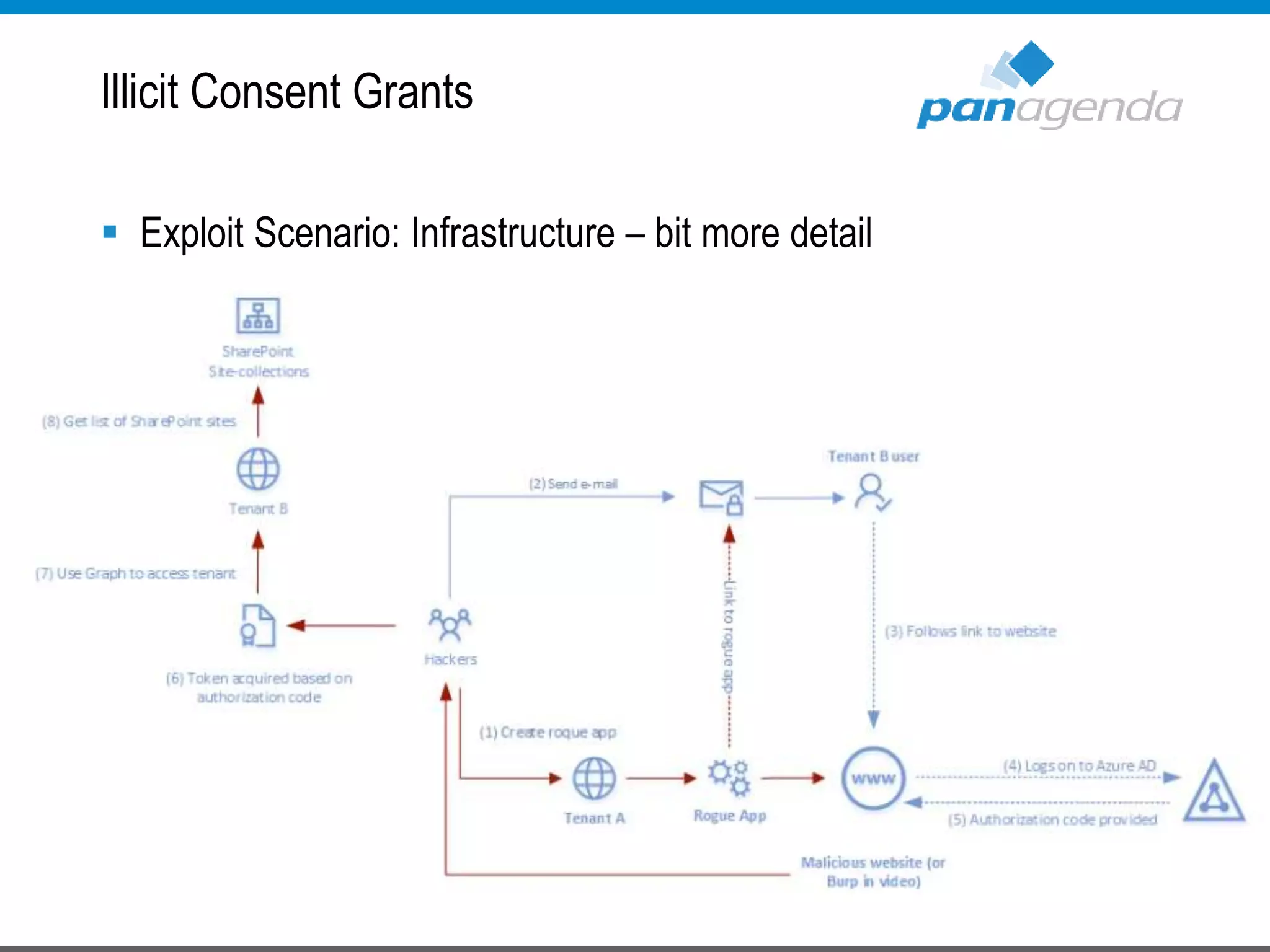
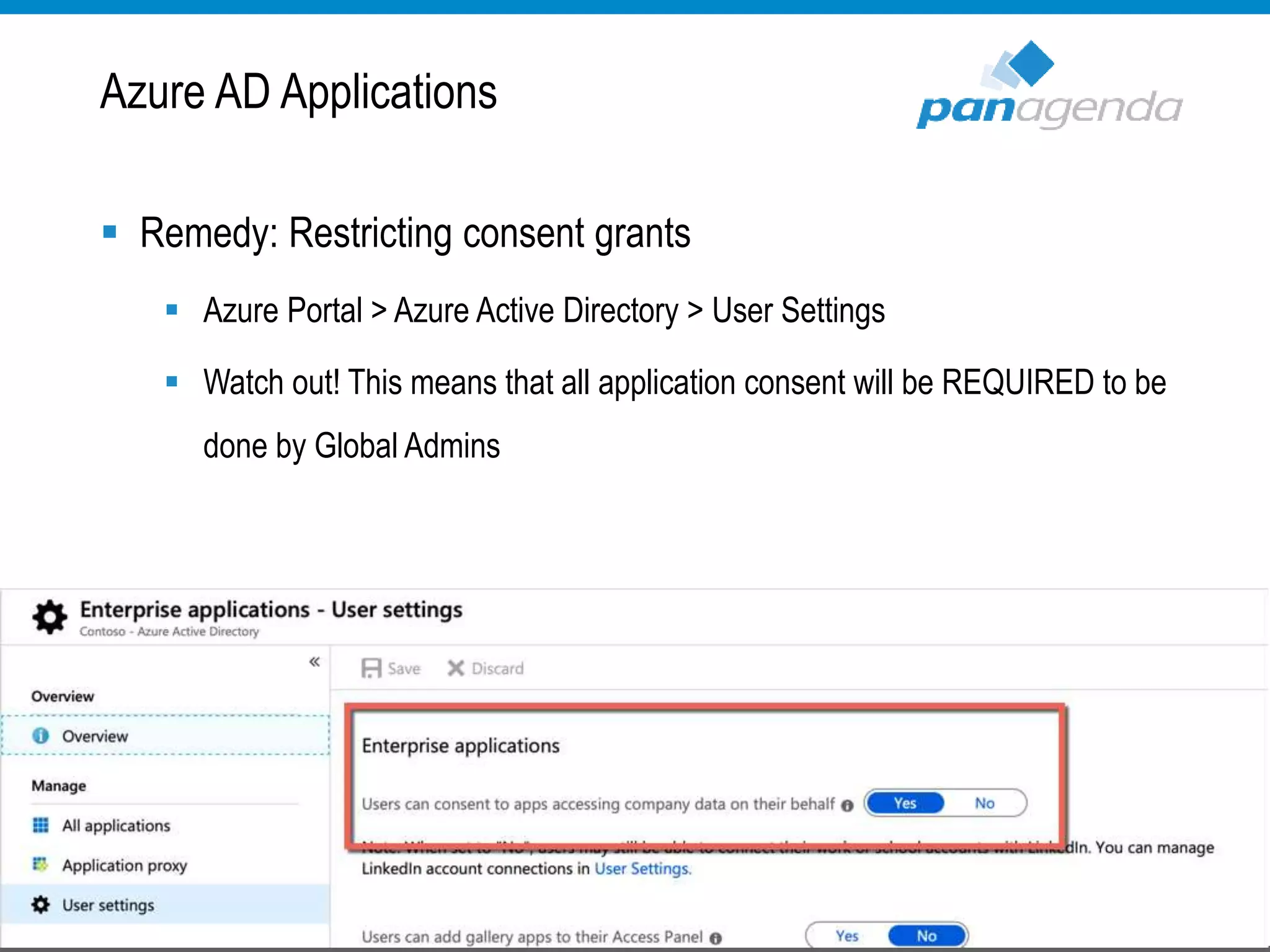
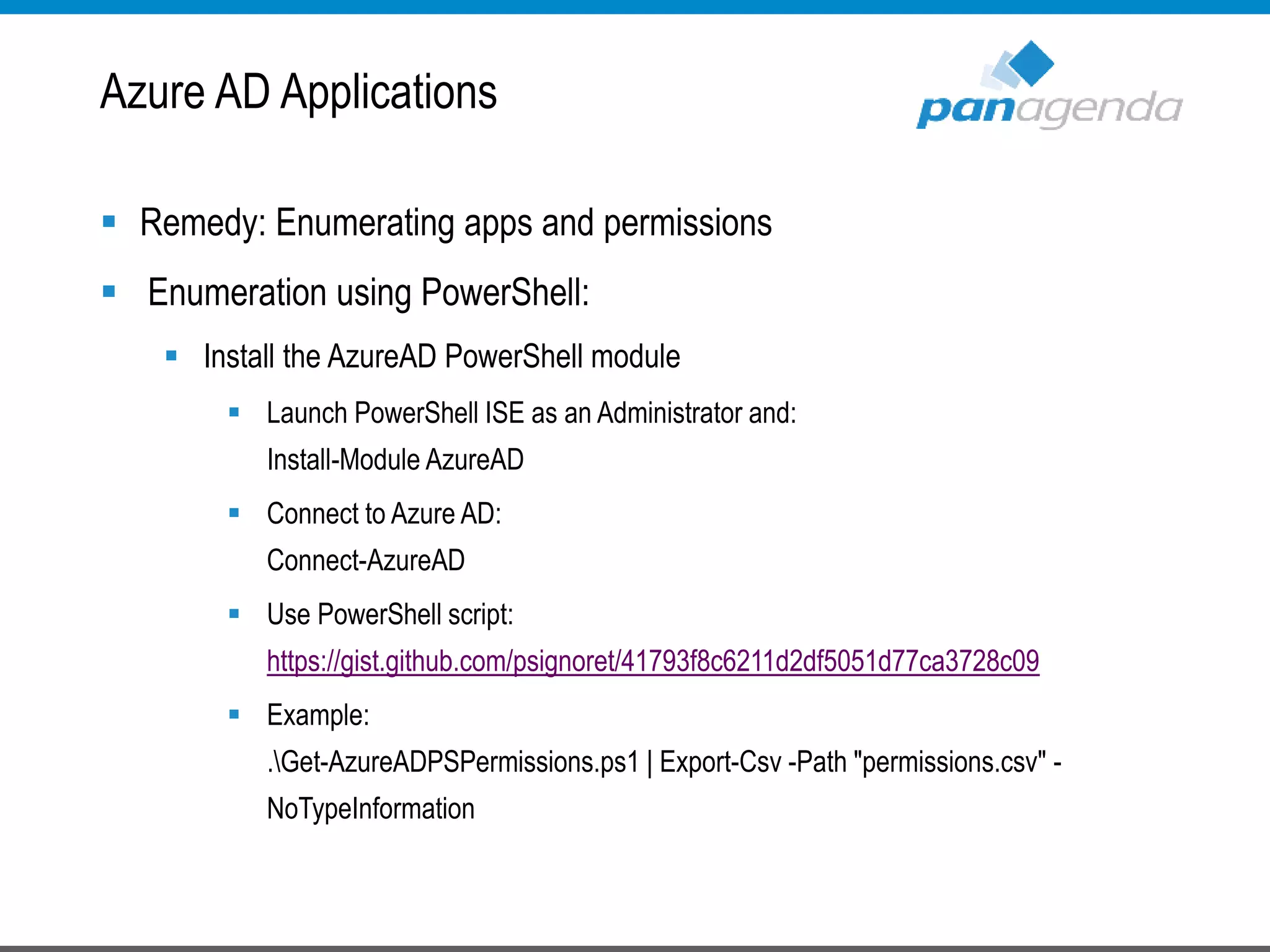
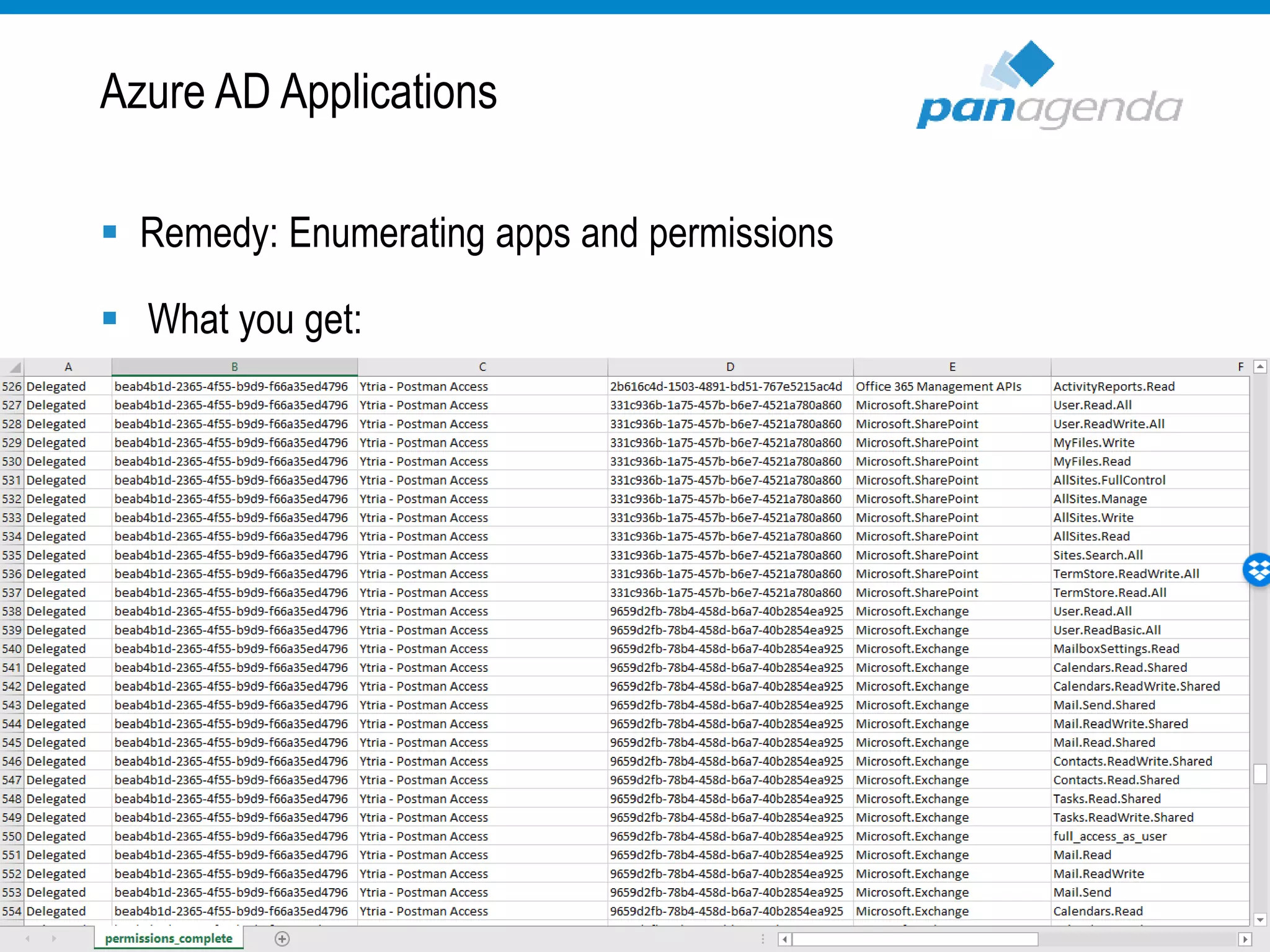
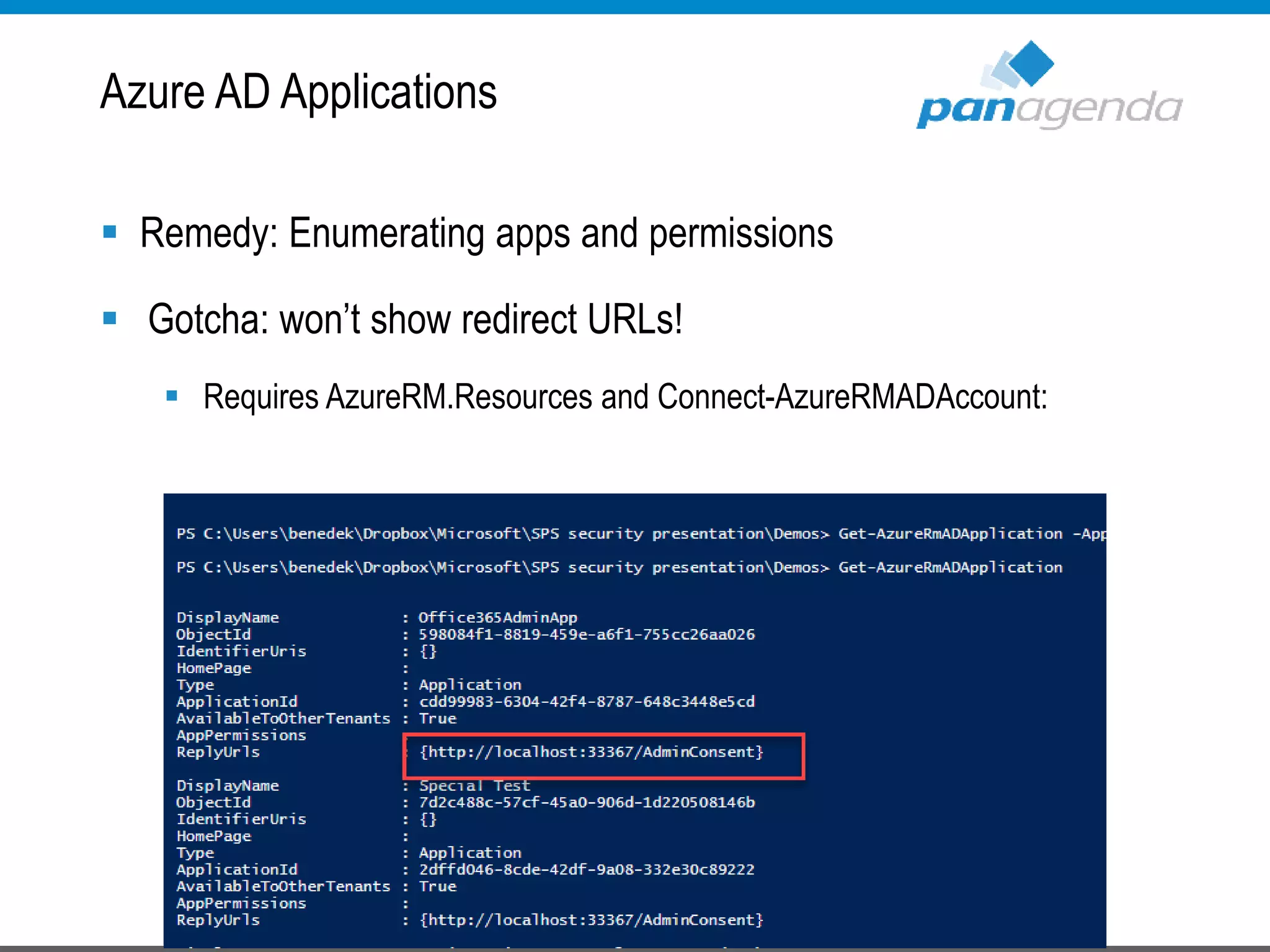
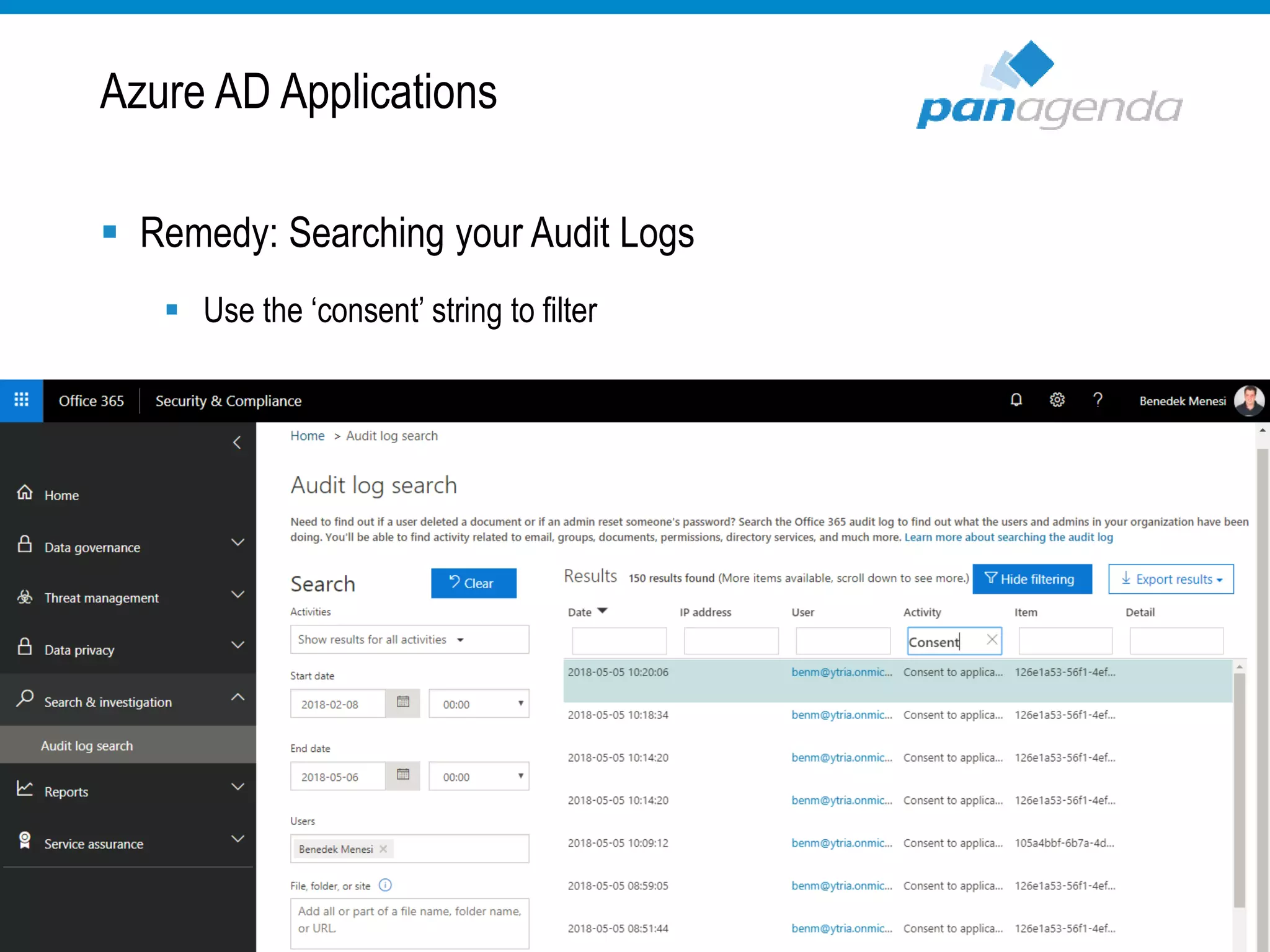
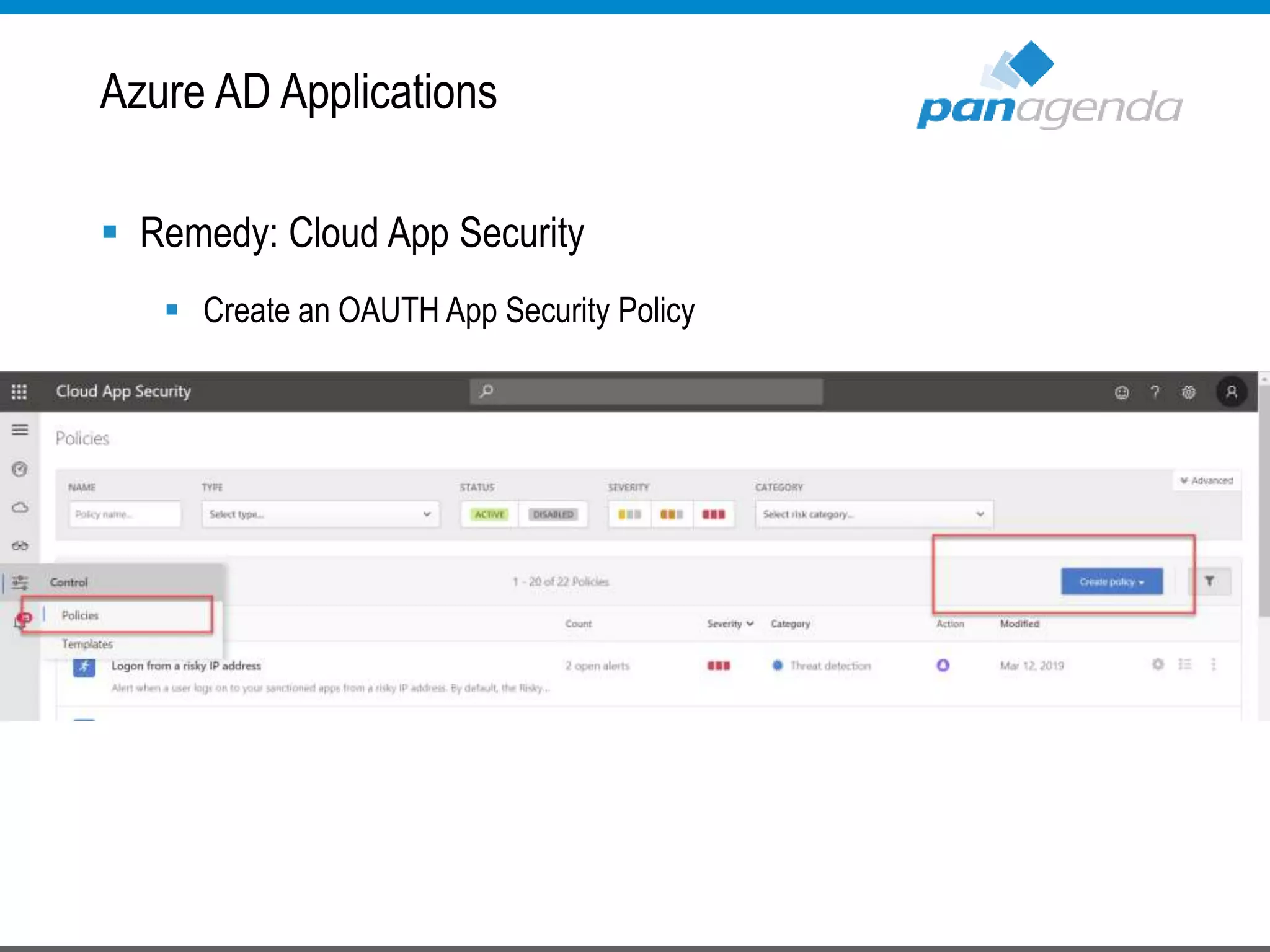
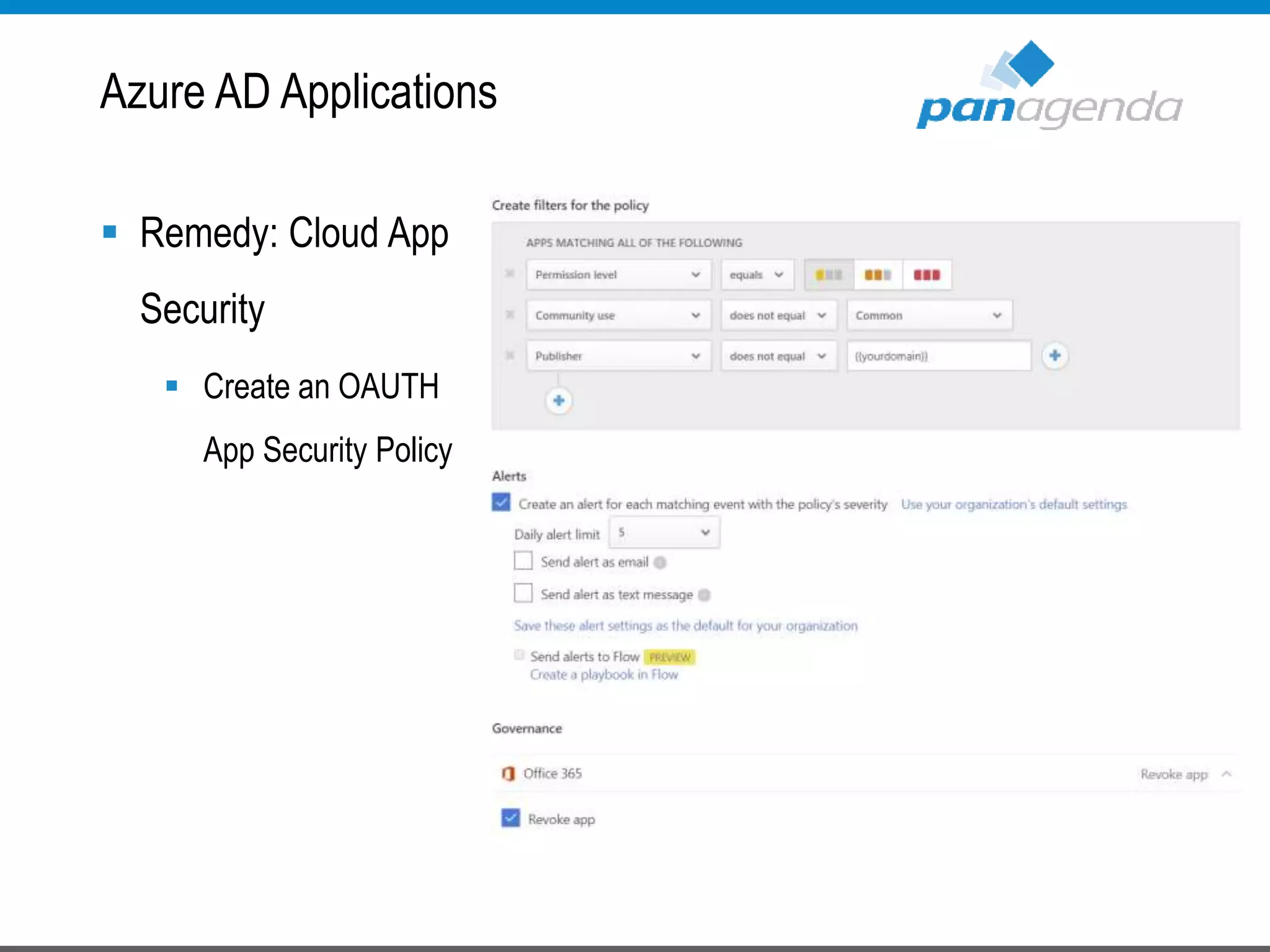
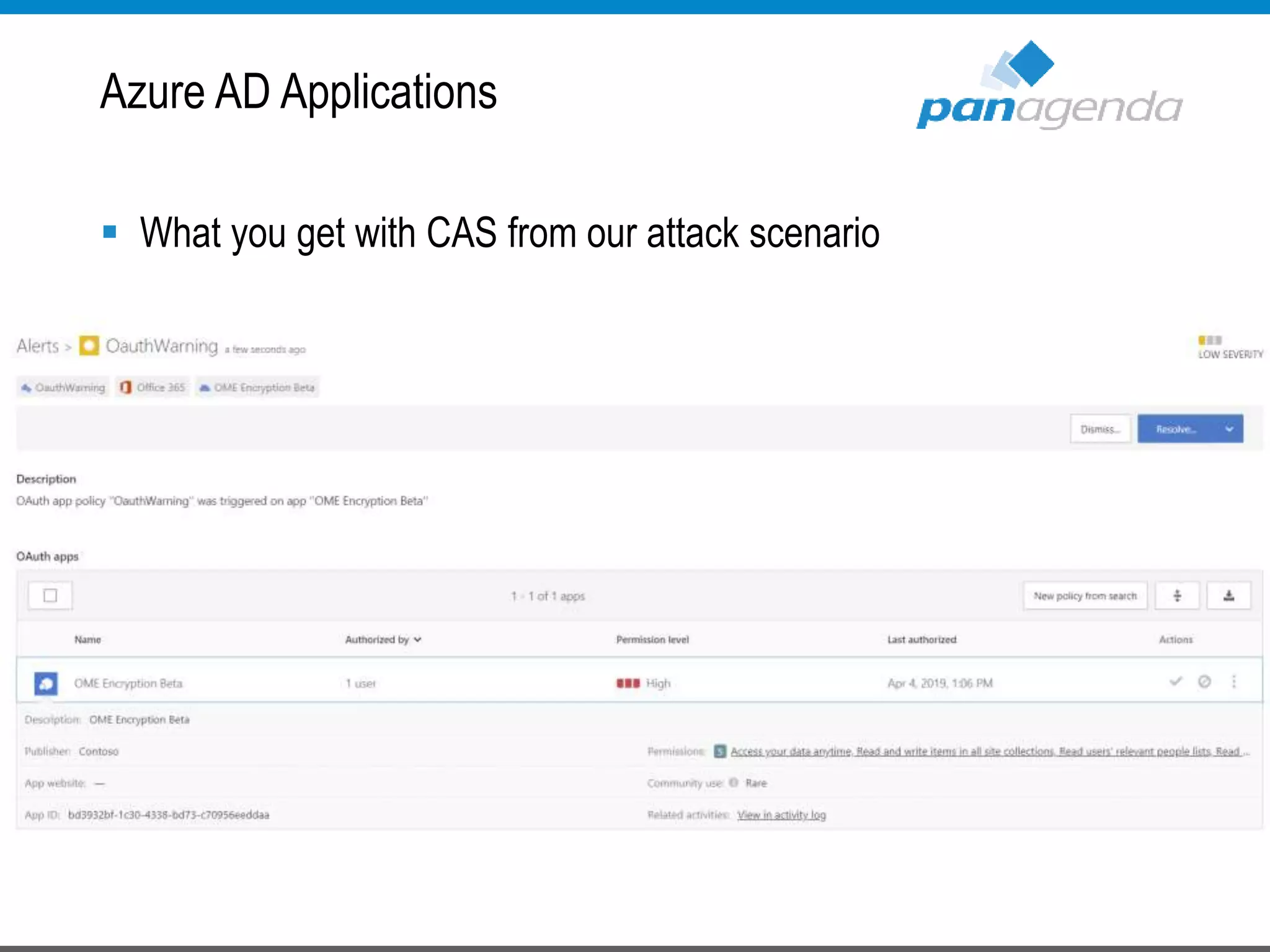
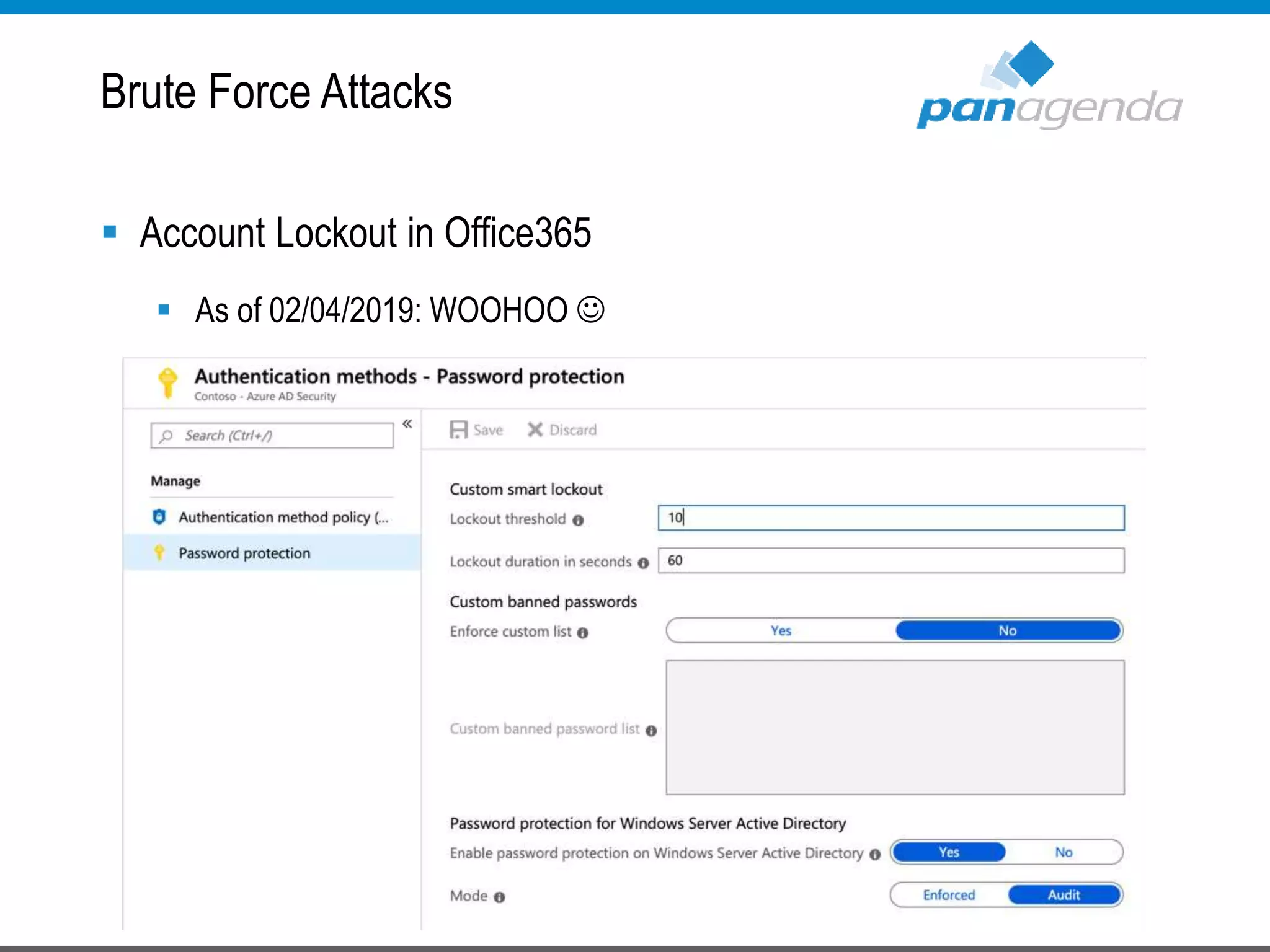
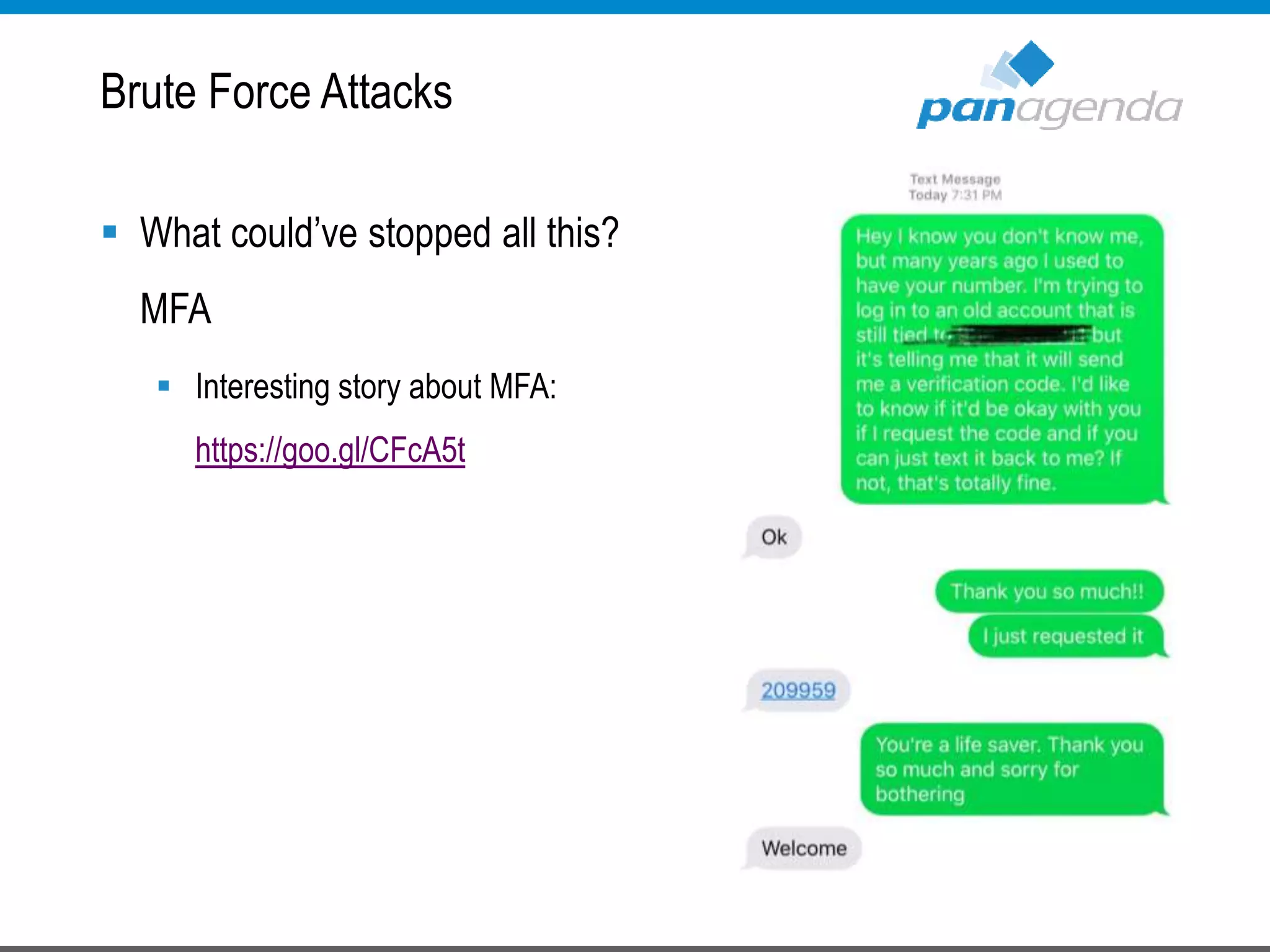
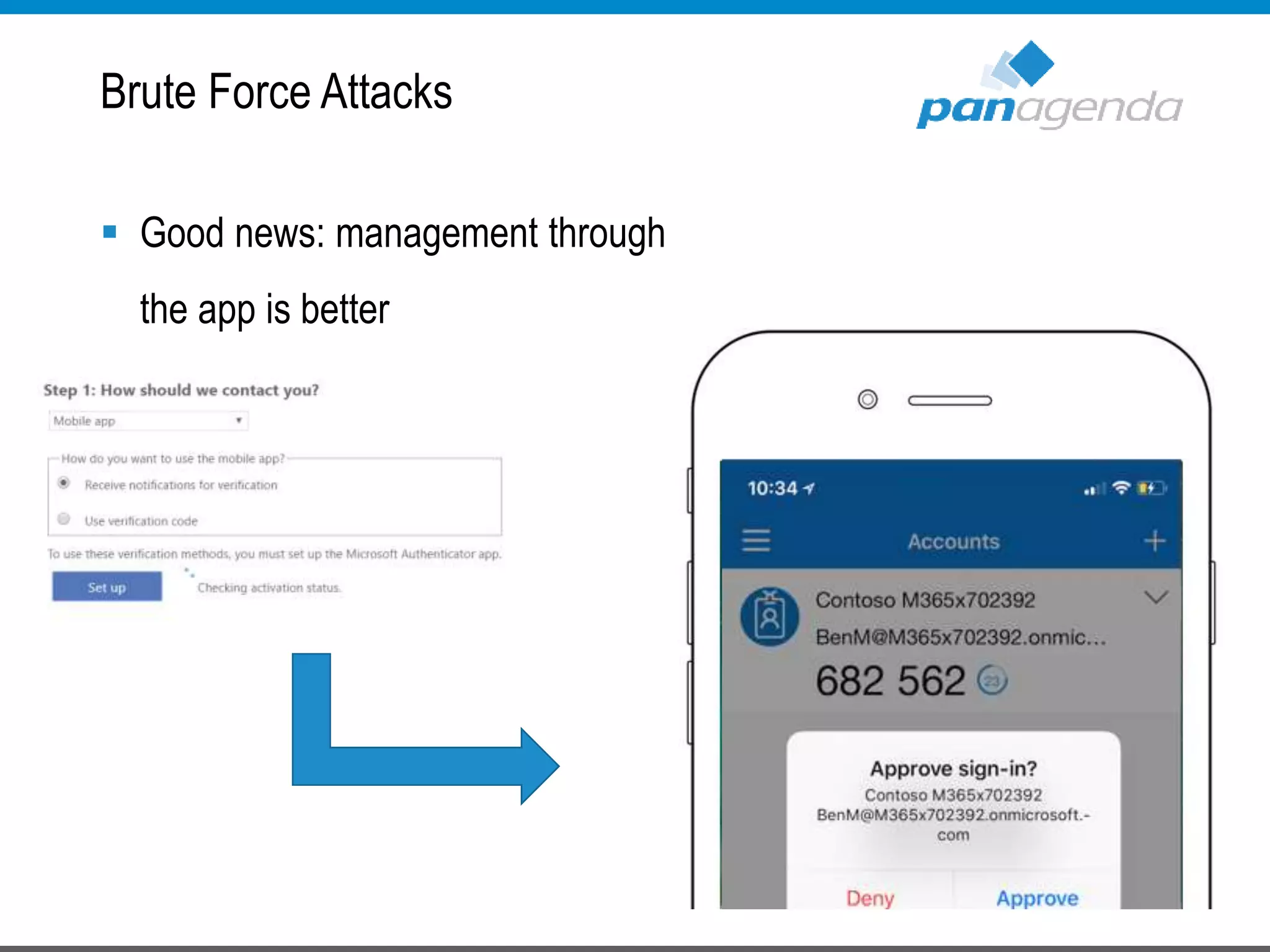
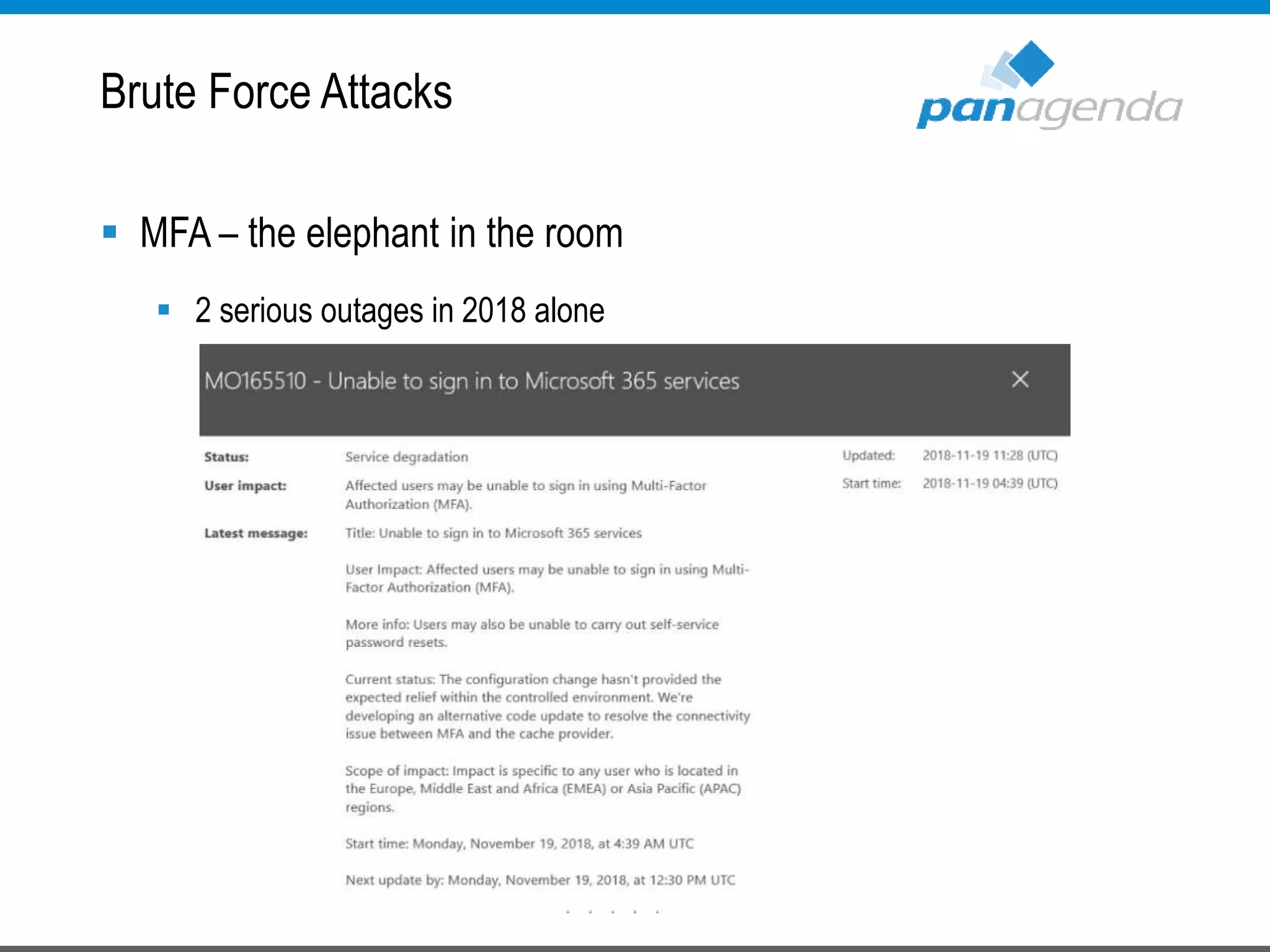
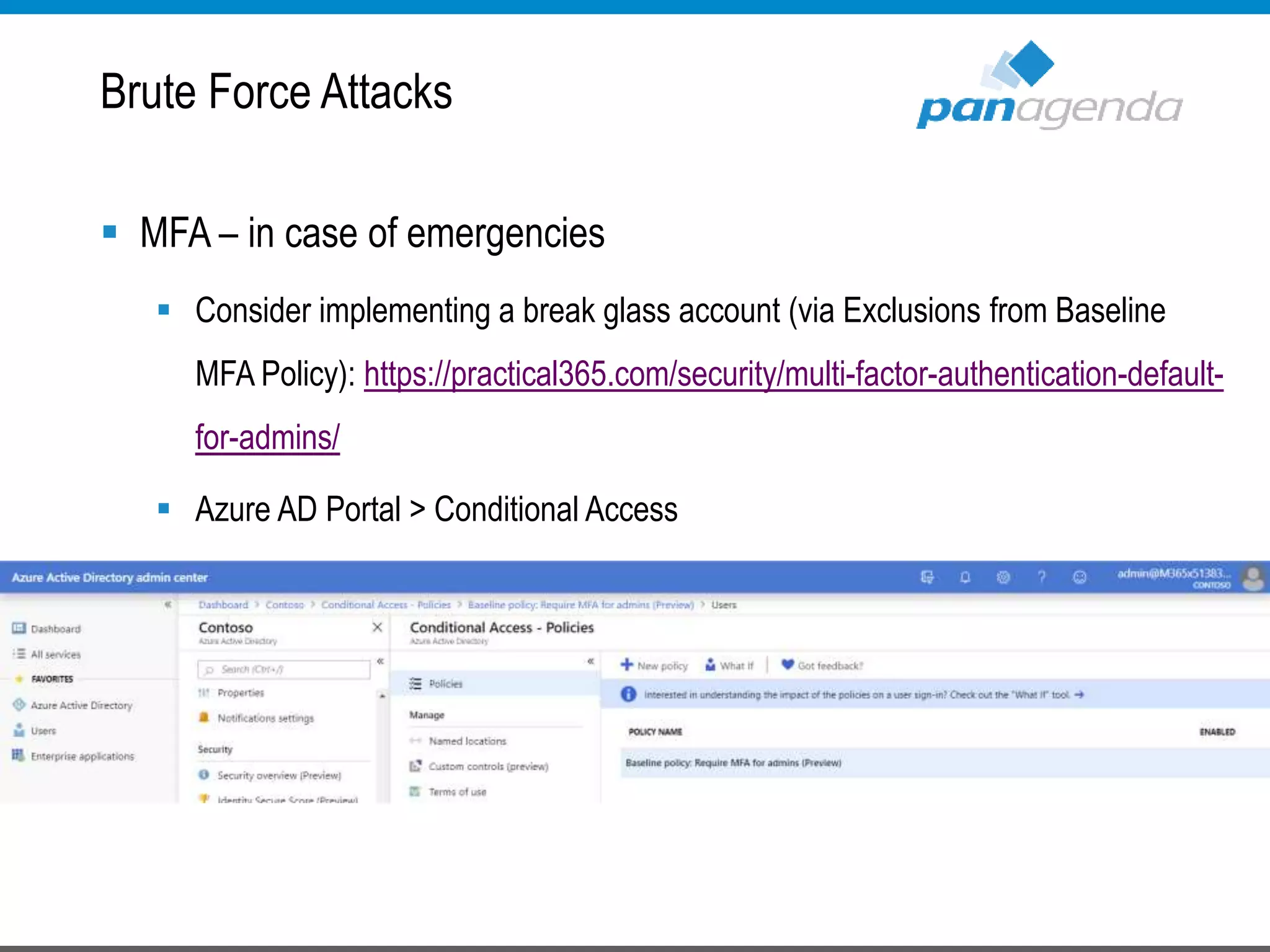
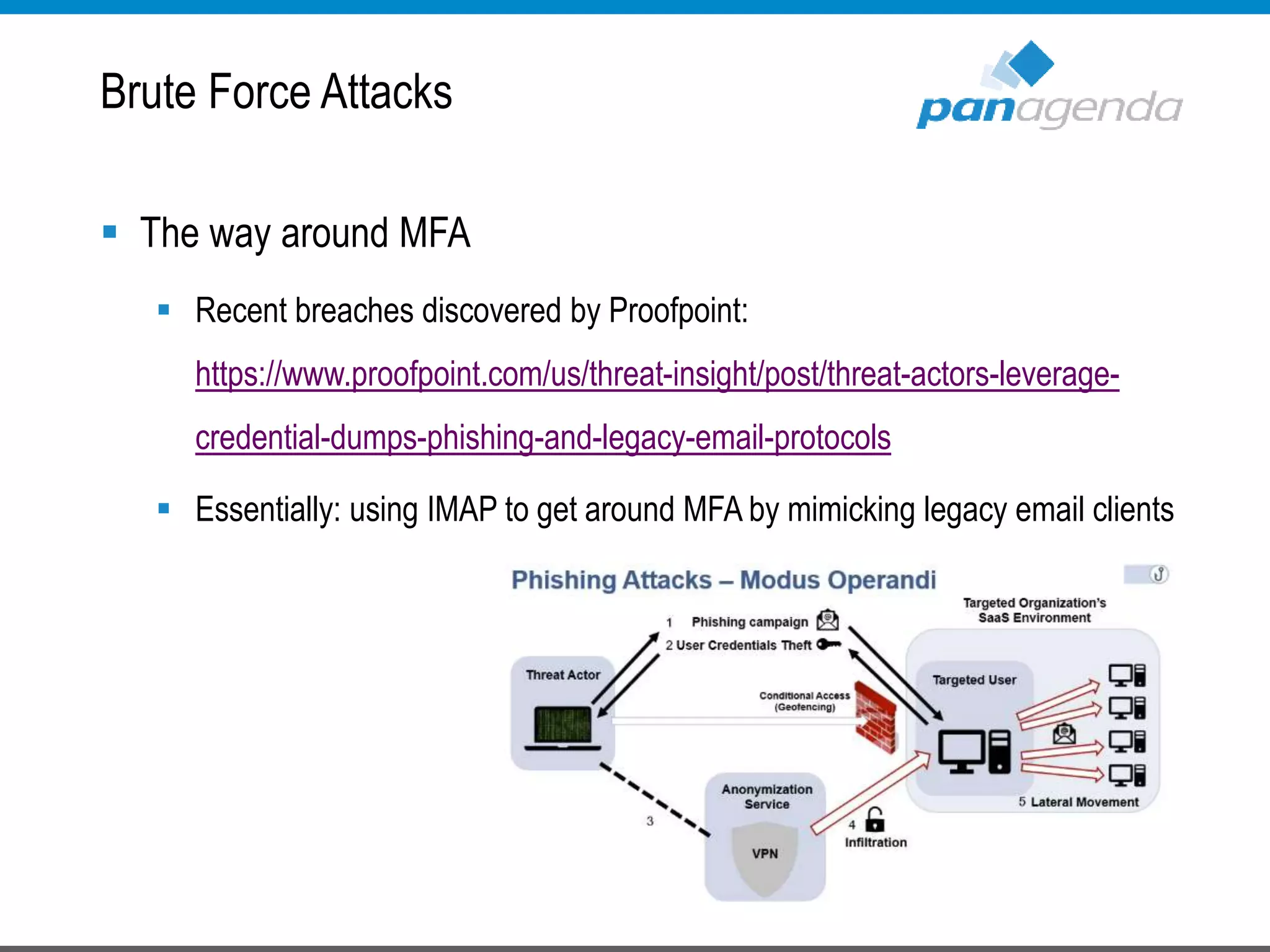
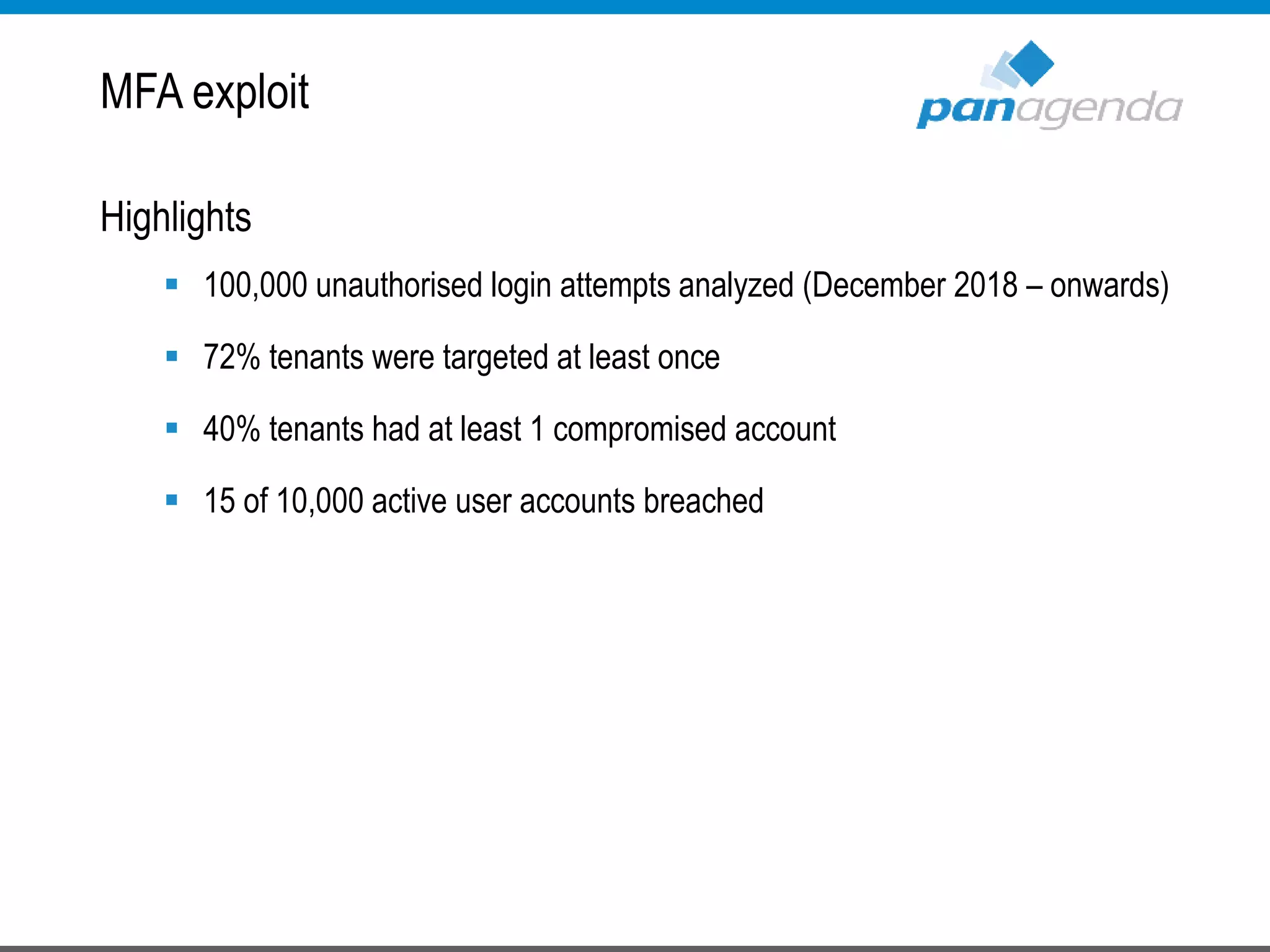
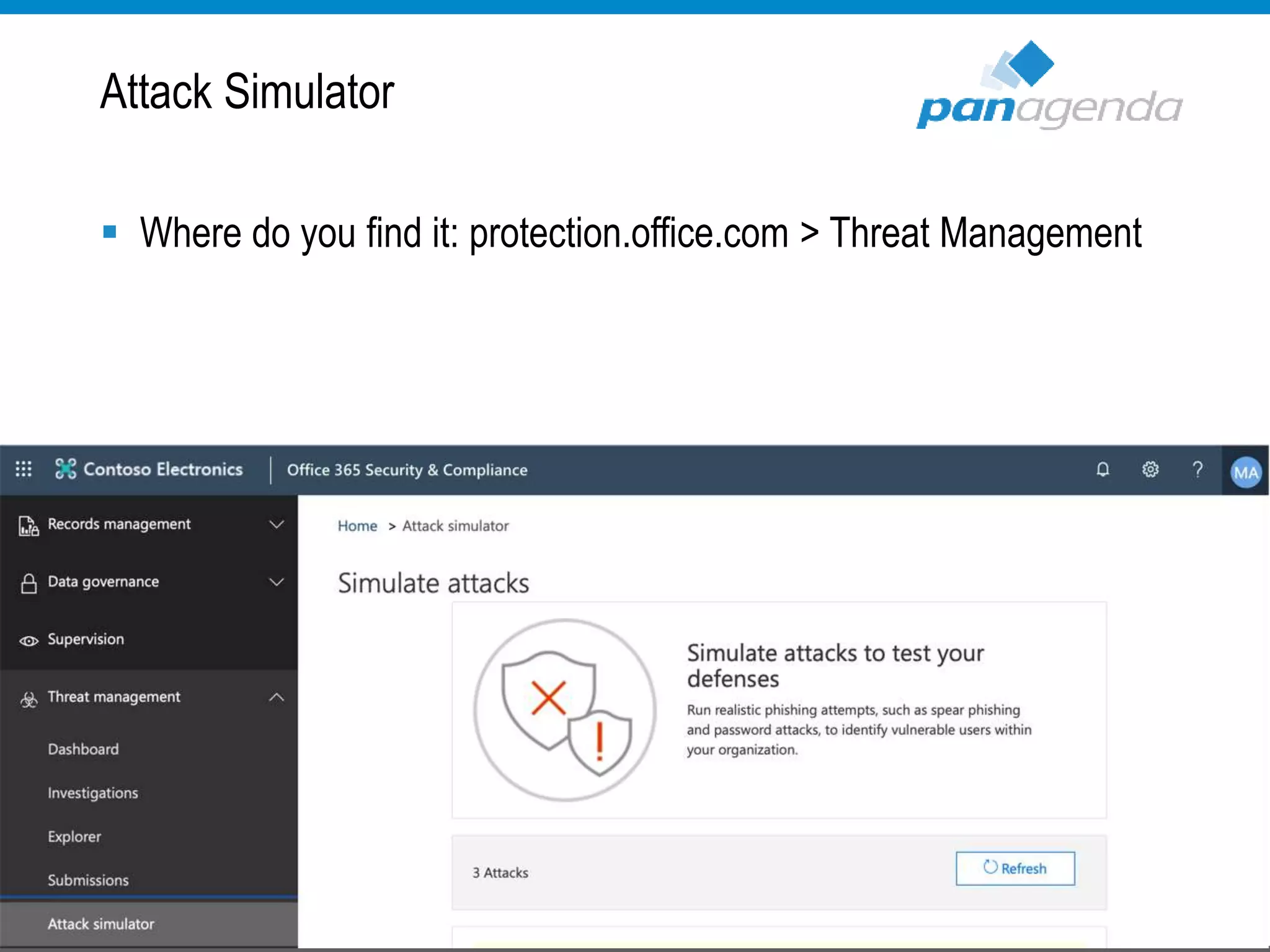
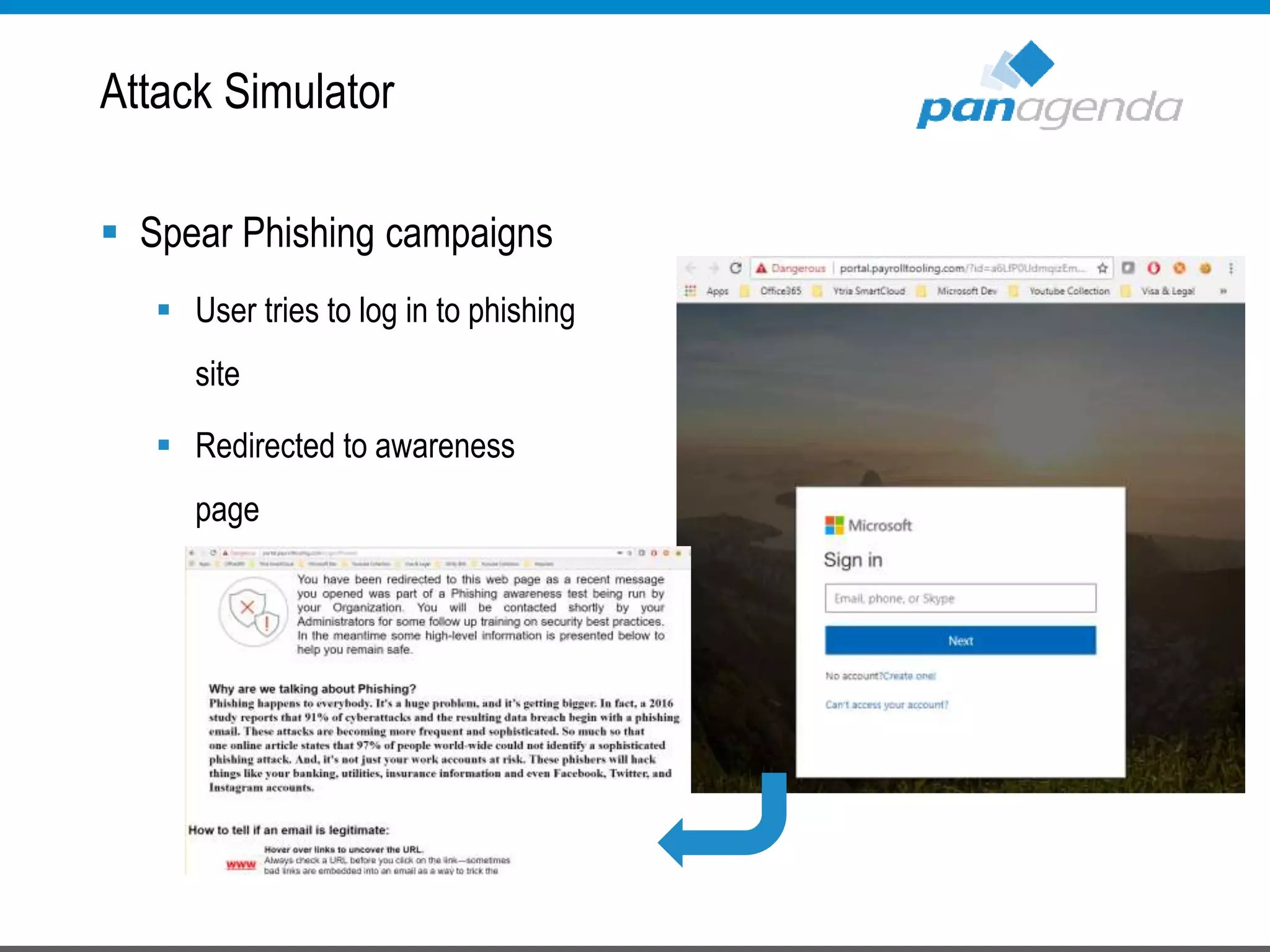
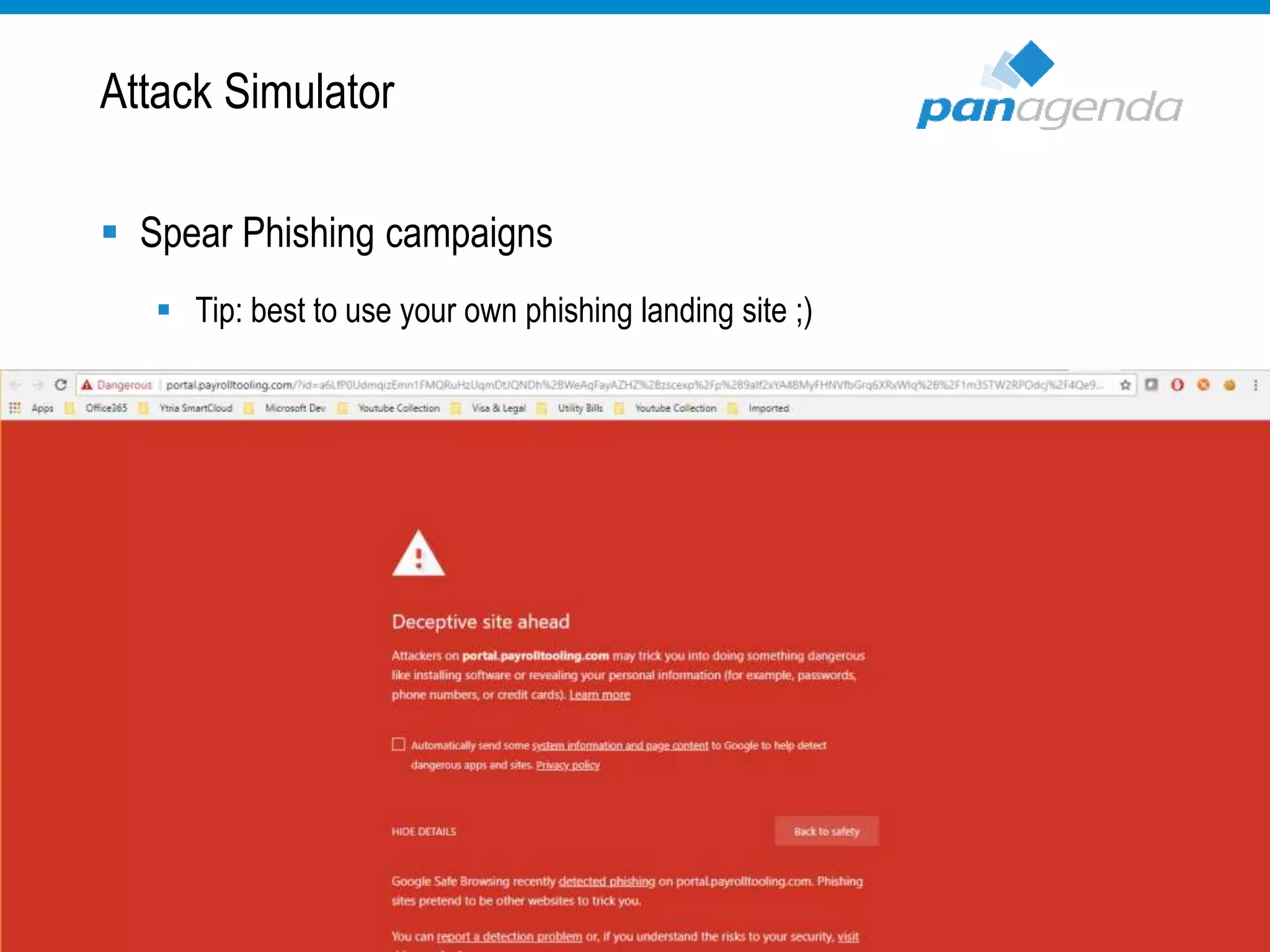
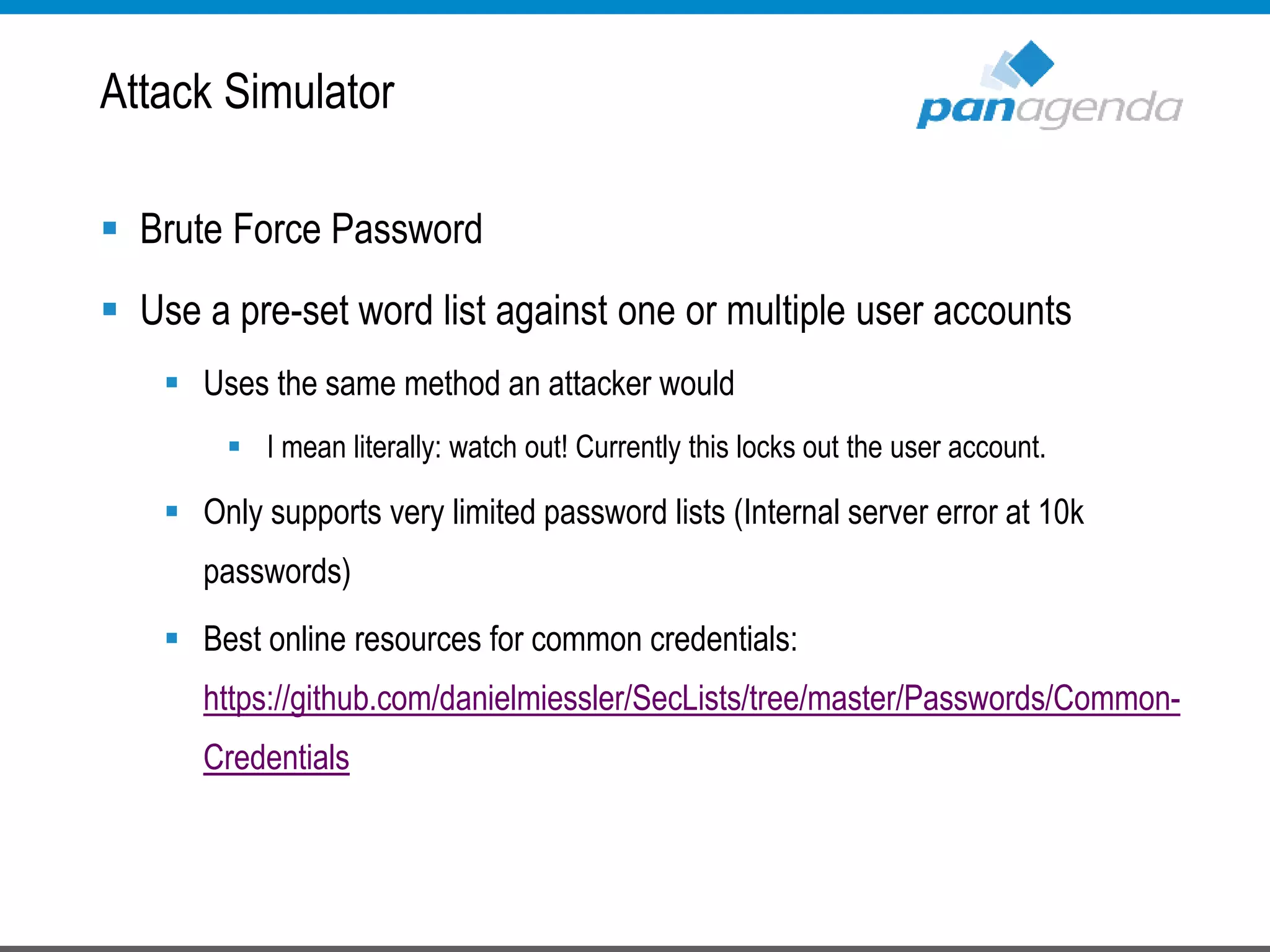
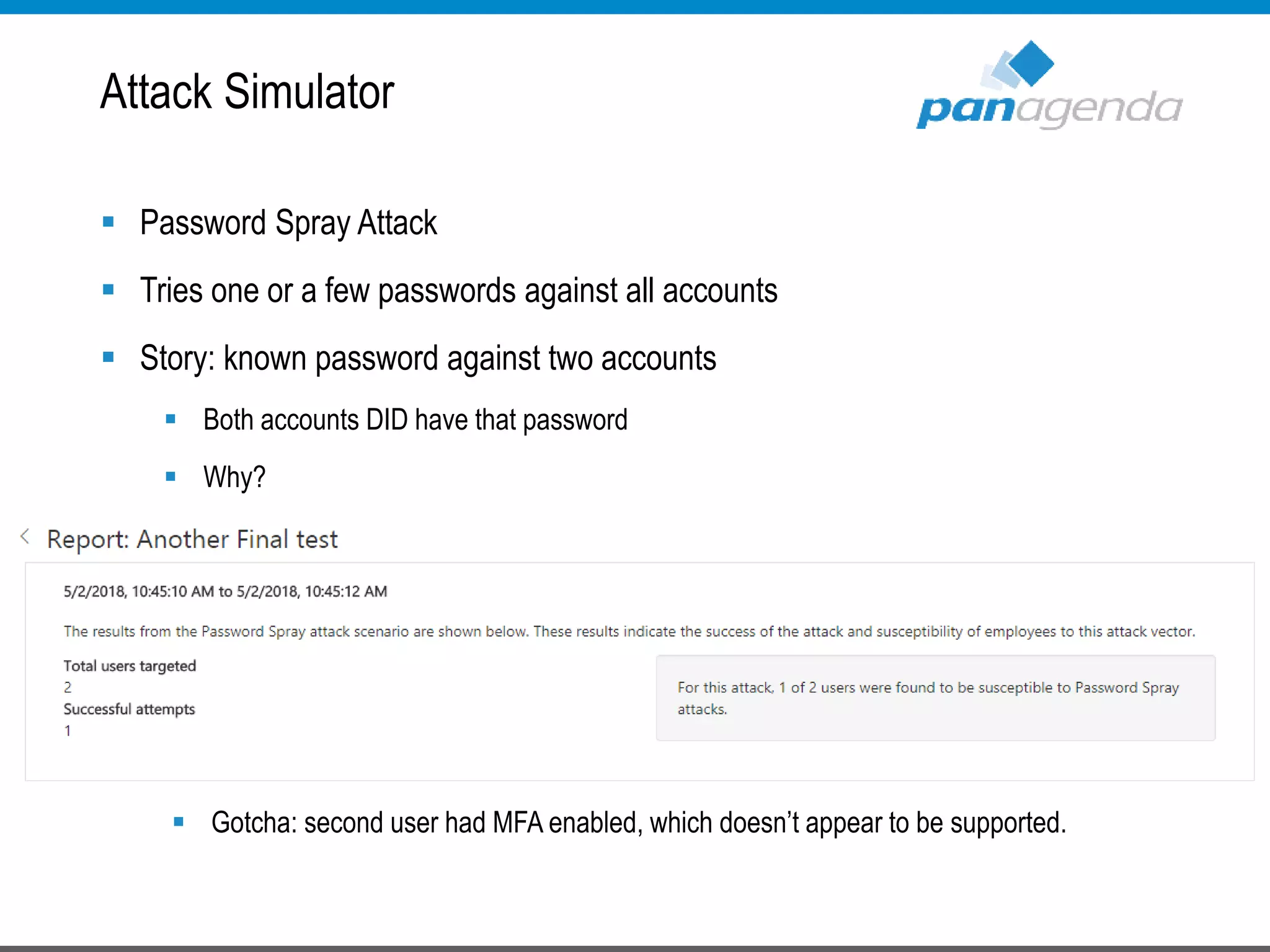
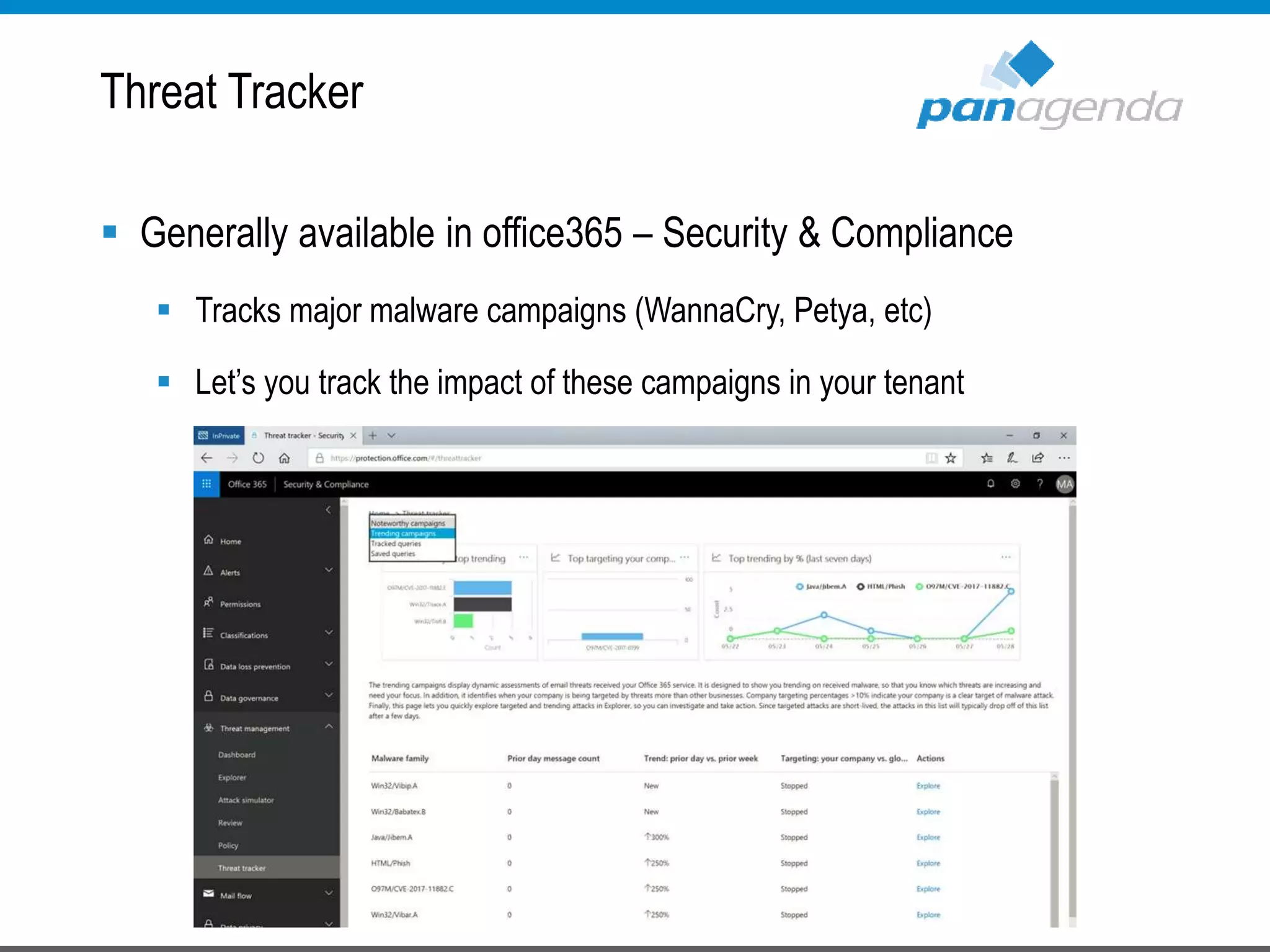
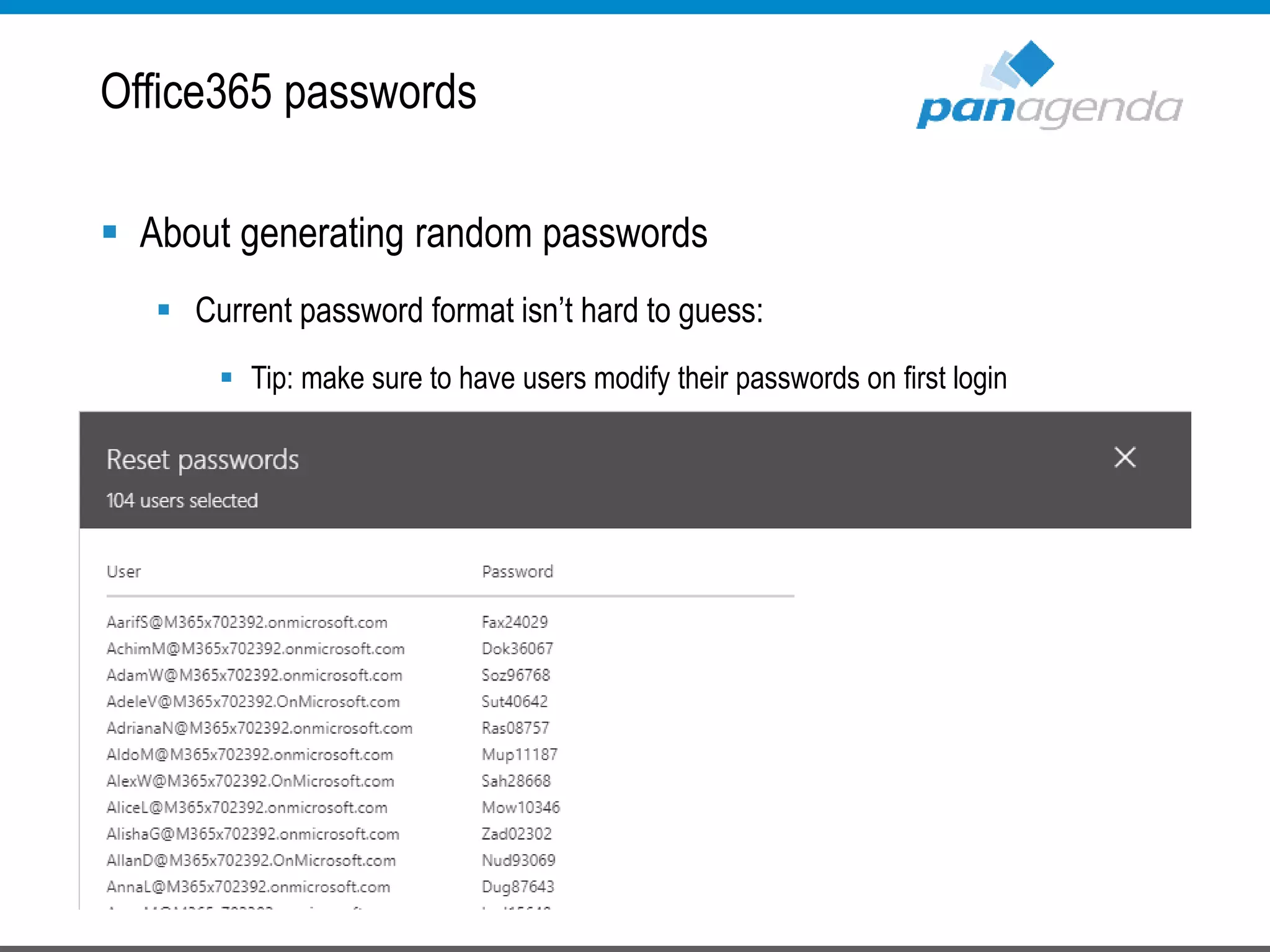
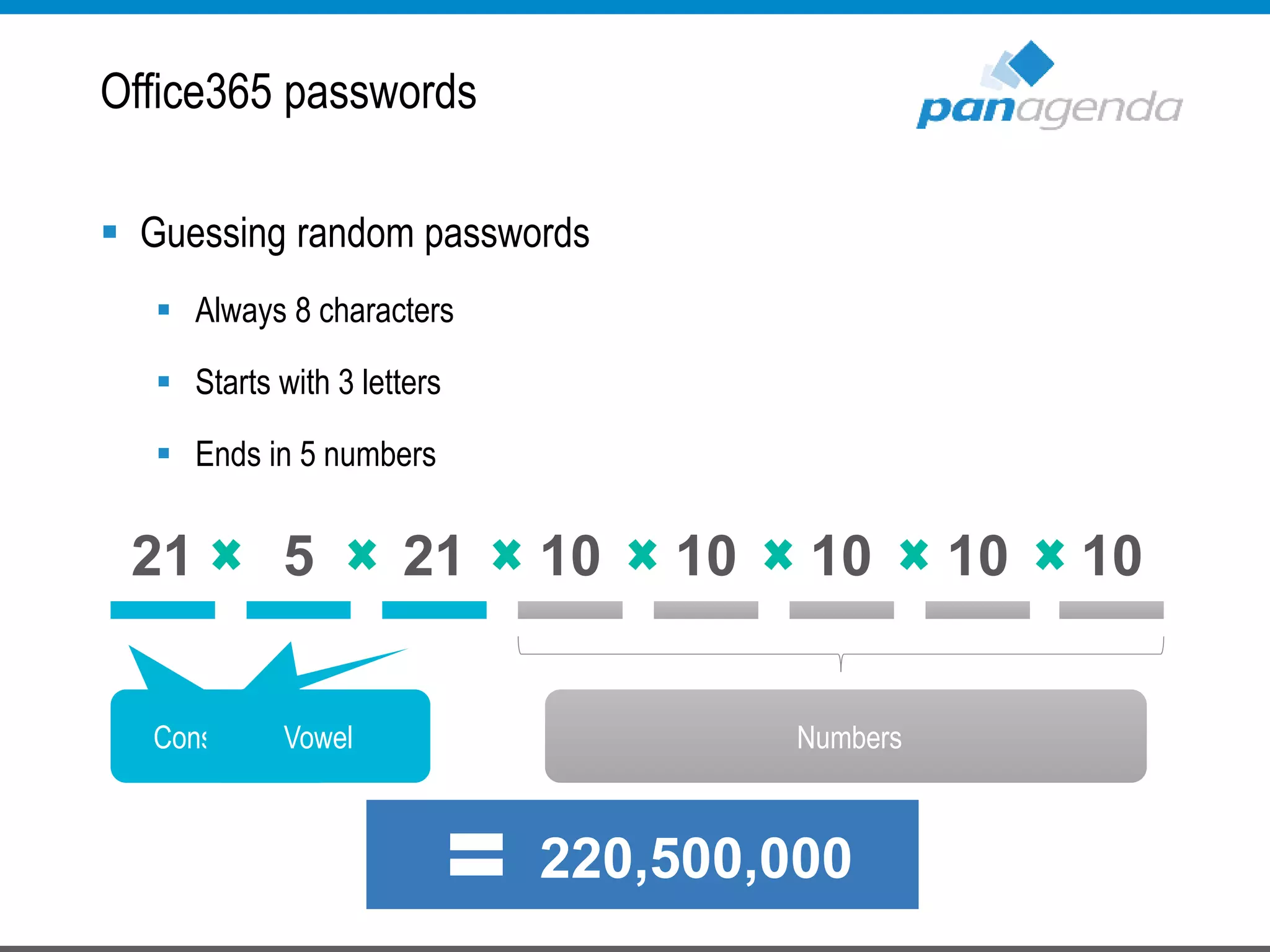
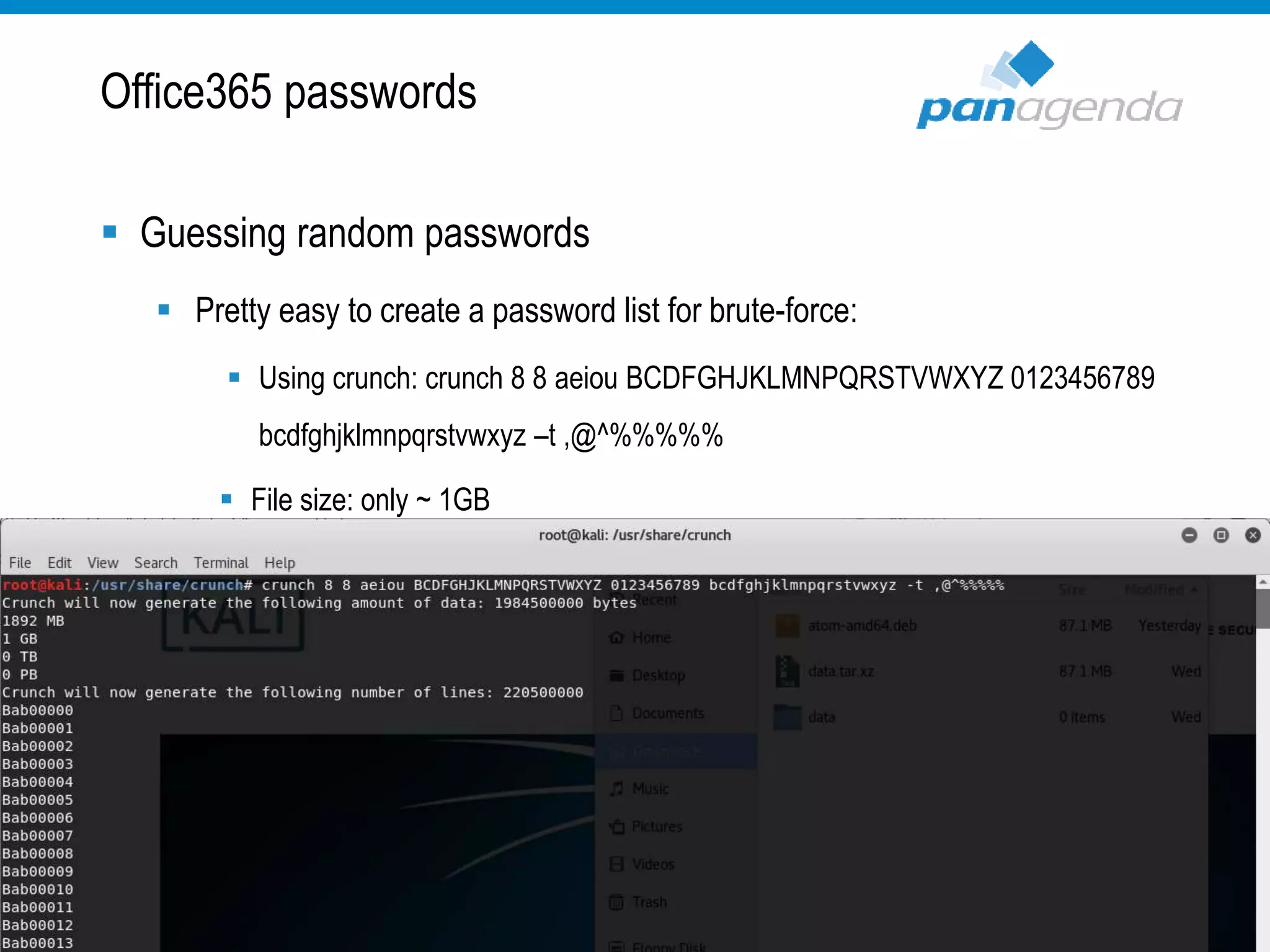
The document details a presentation by Ben Menesi on Office 365 security from a hacker's perspective, highlighting real-life threats such as ransomware, phishing, and brute force attacks. It discusses various tactics for protecting data, including multi-factor authentication, email encryption, and the importance of monitoring and controlling application permissions. Additionally, it emphasizes the need for effective security practices and user education to mitigate risks associated with cloud services and cyber threats.