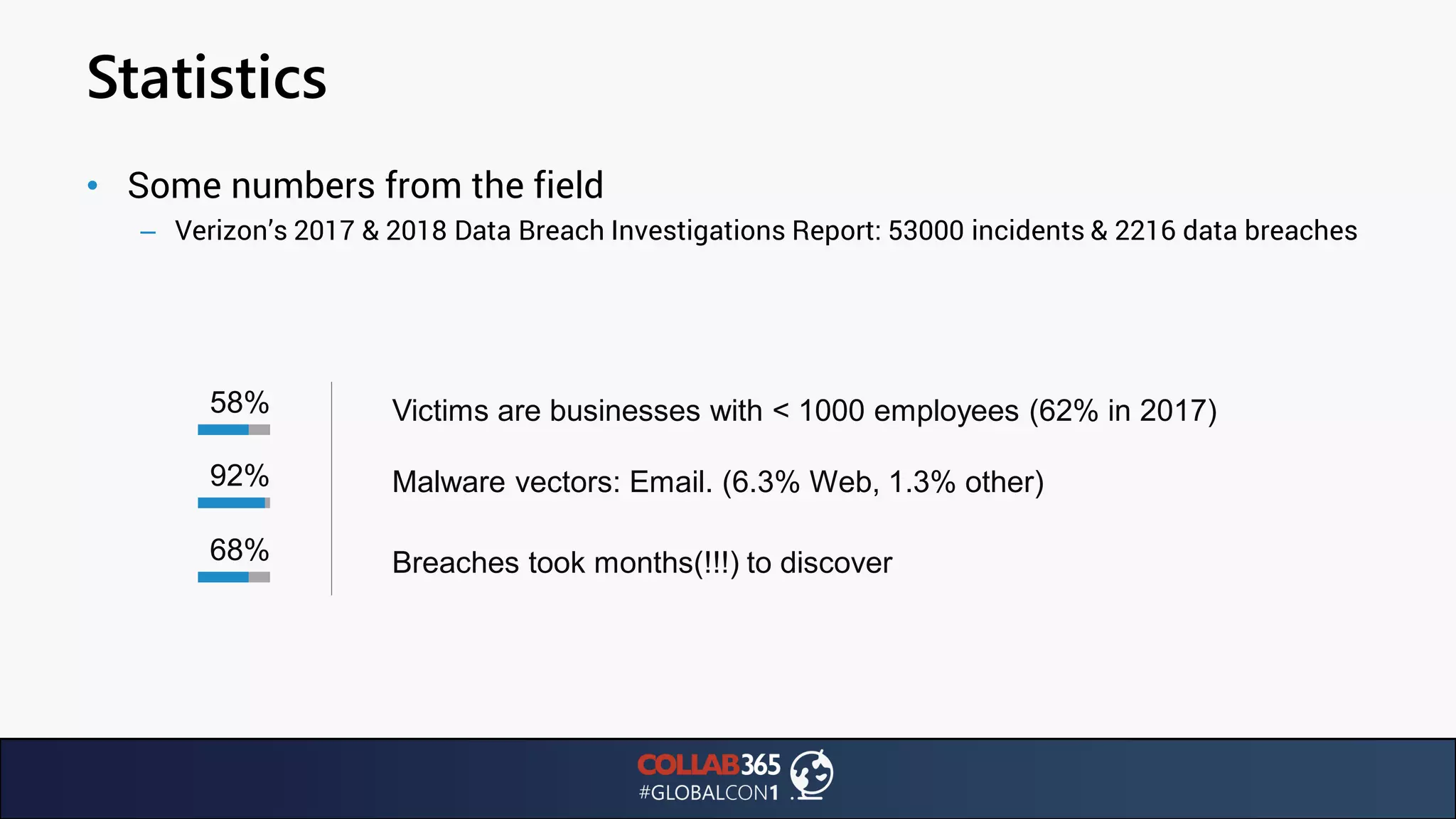
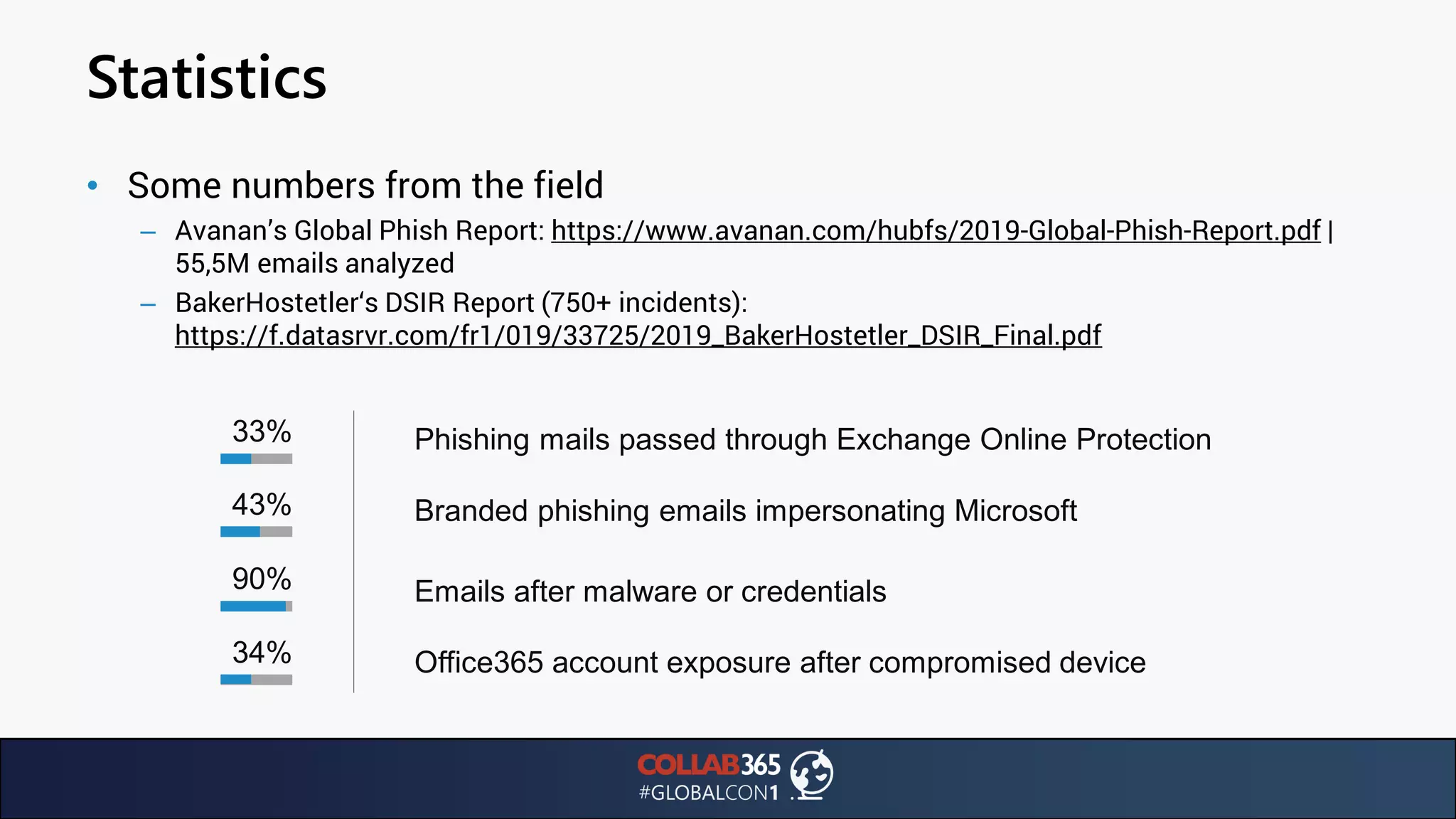
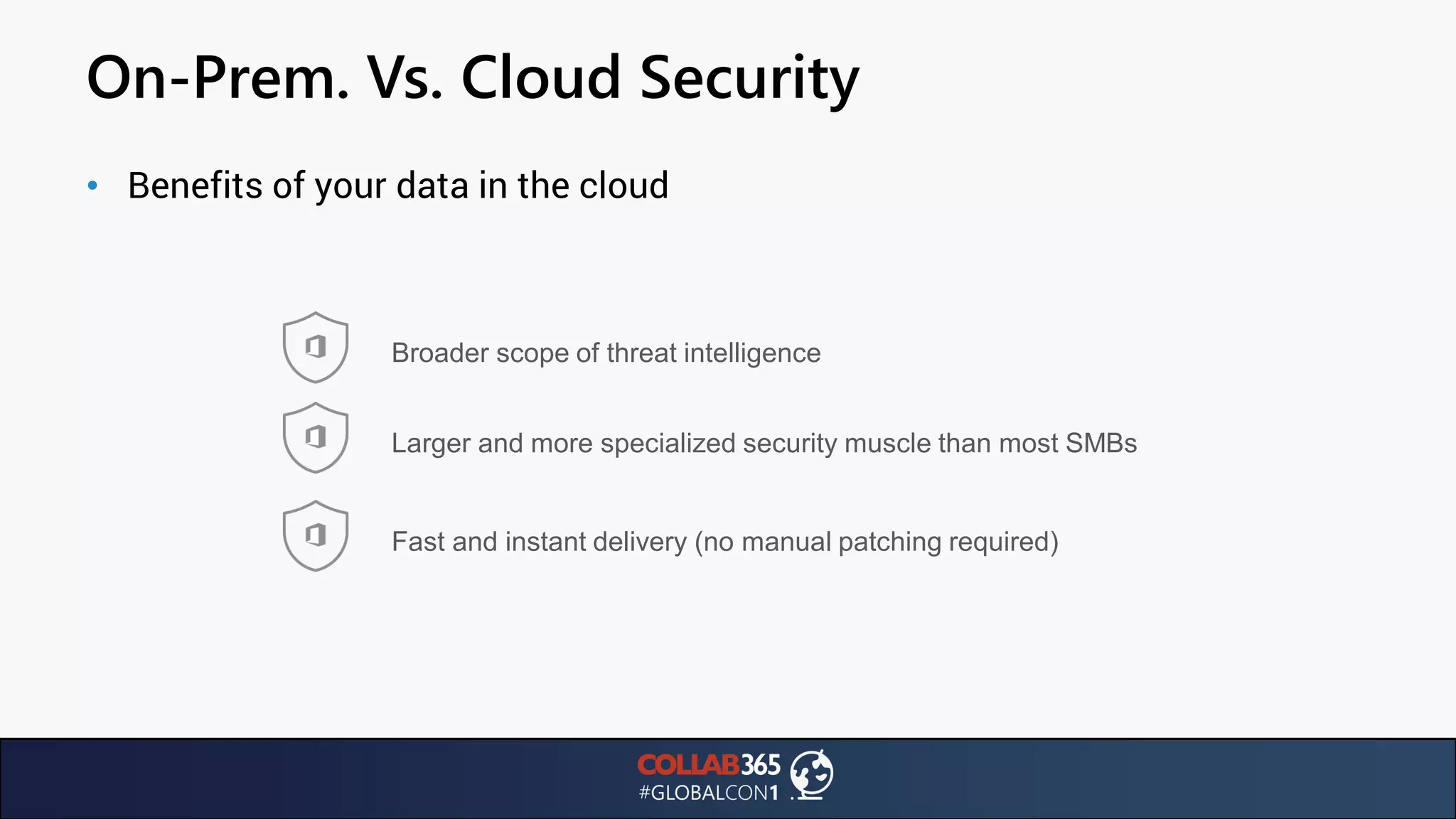
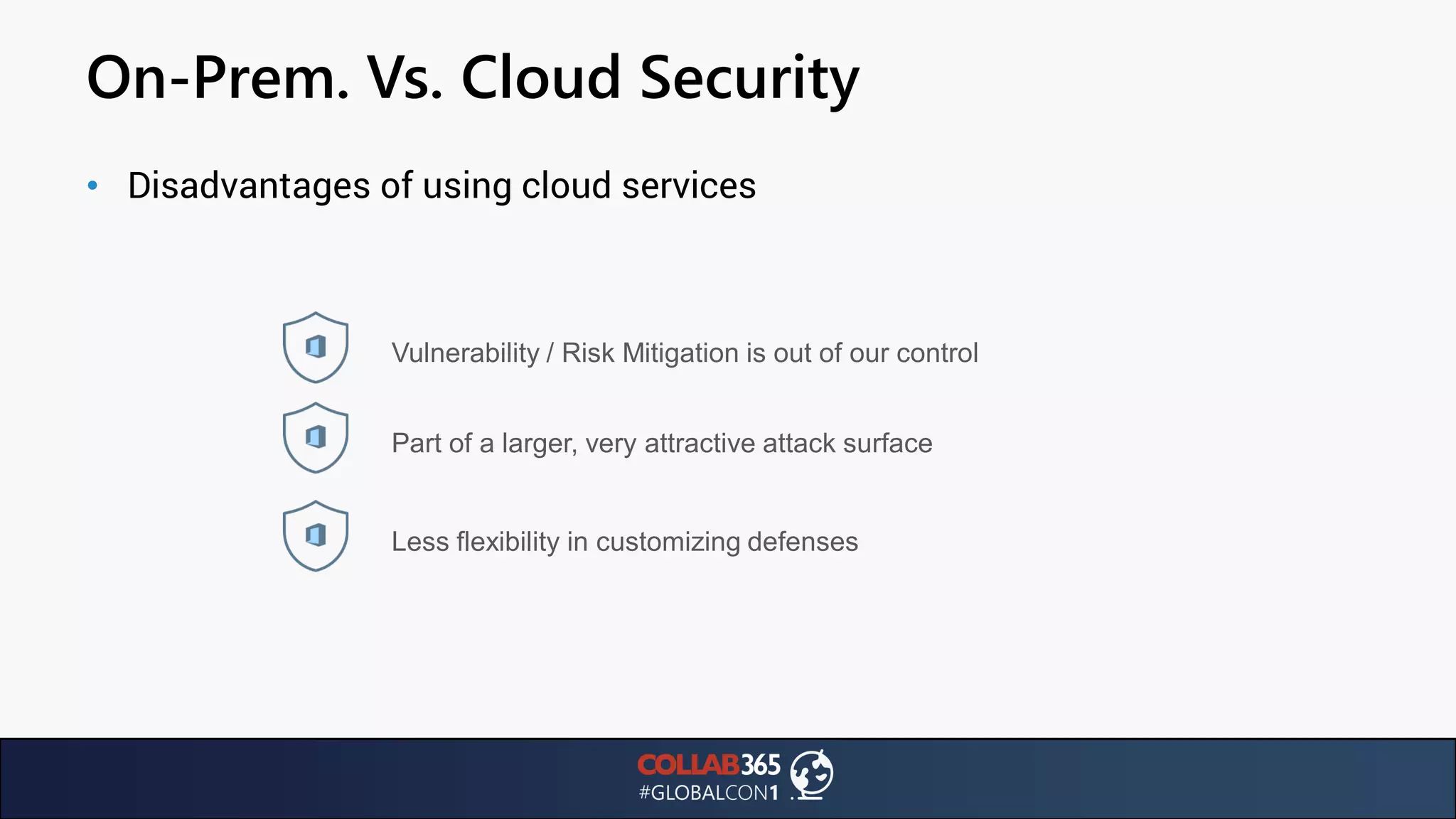
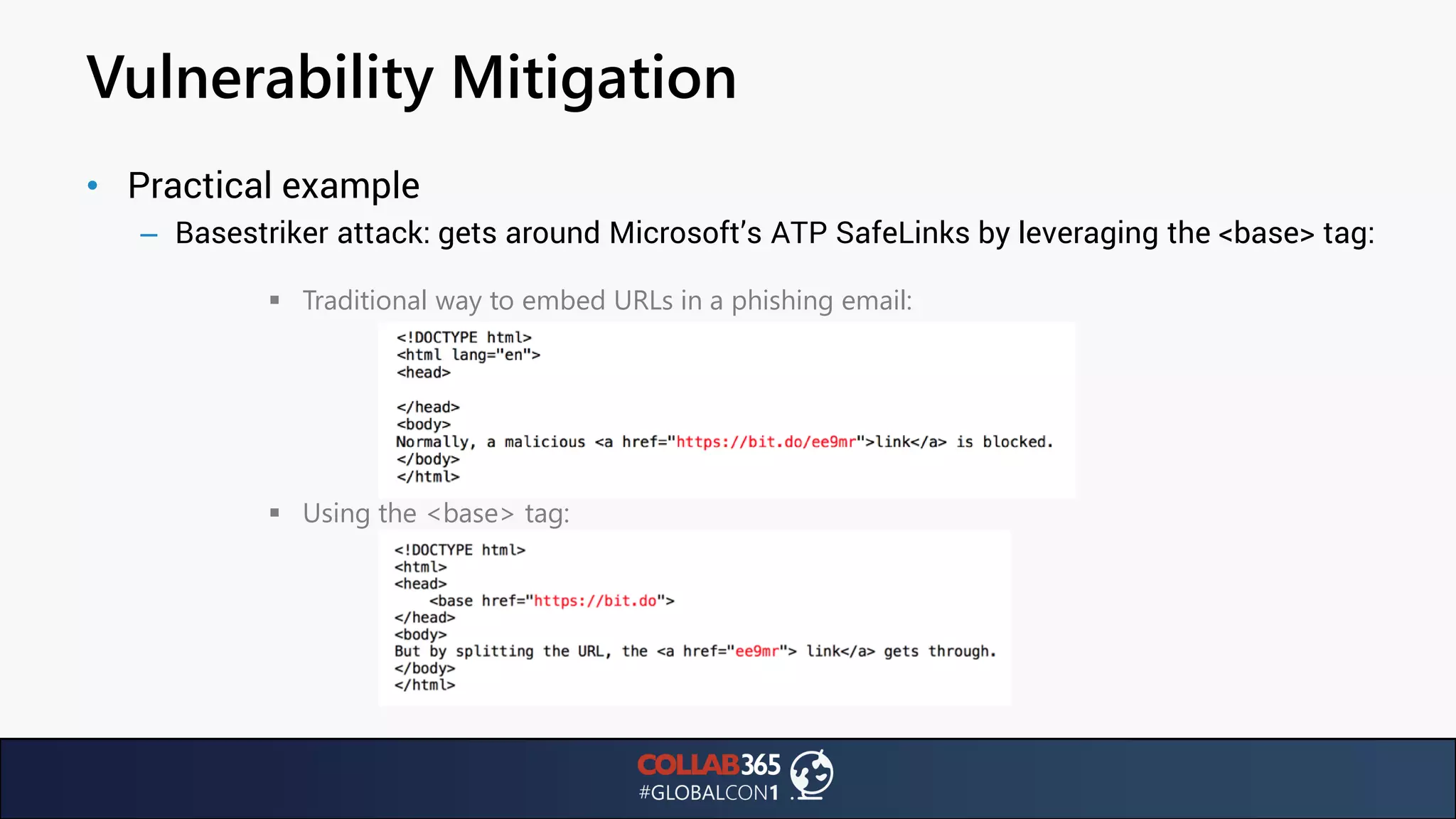
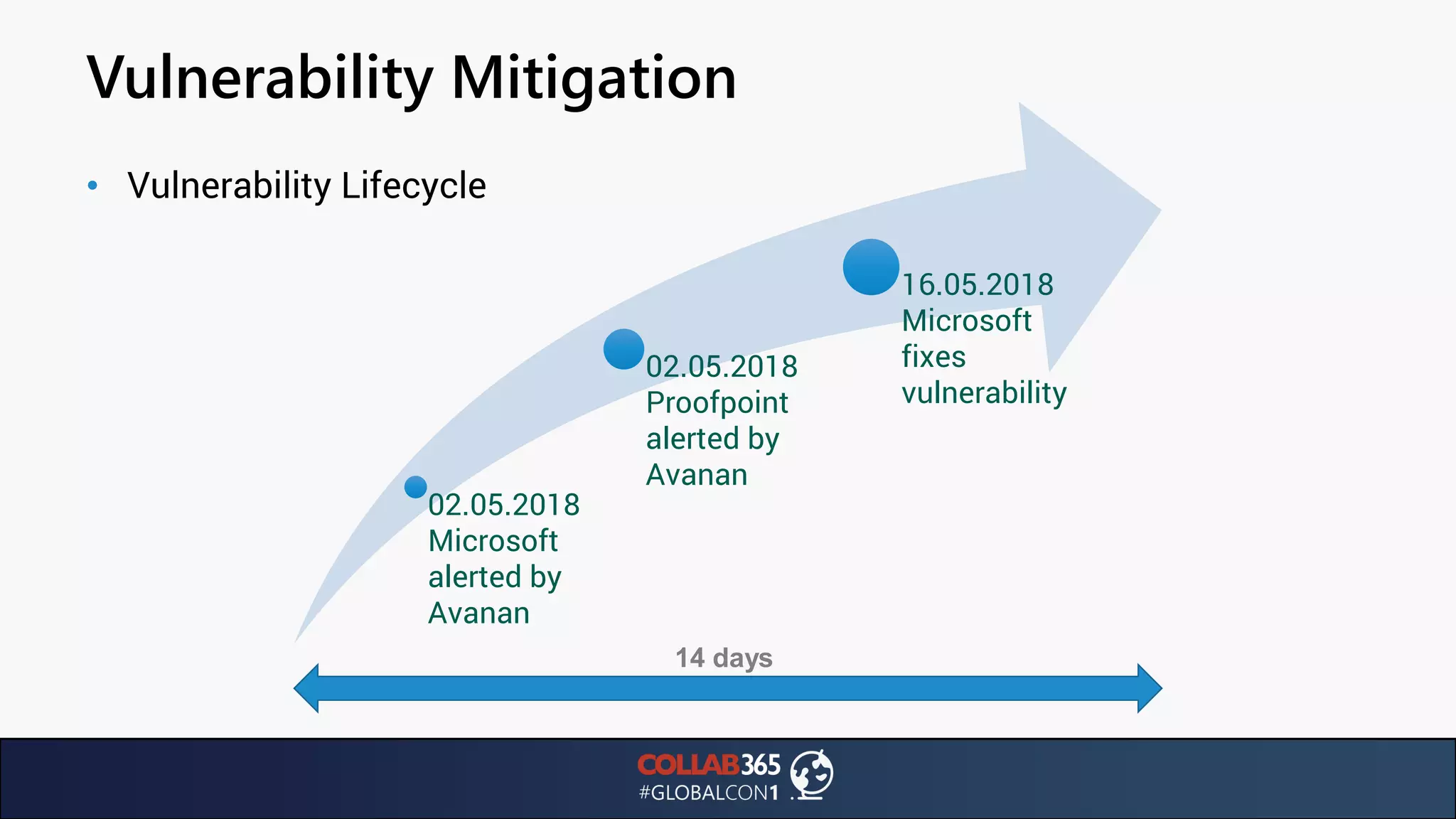
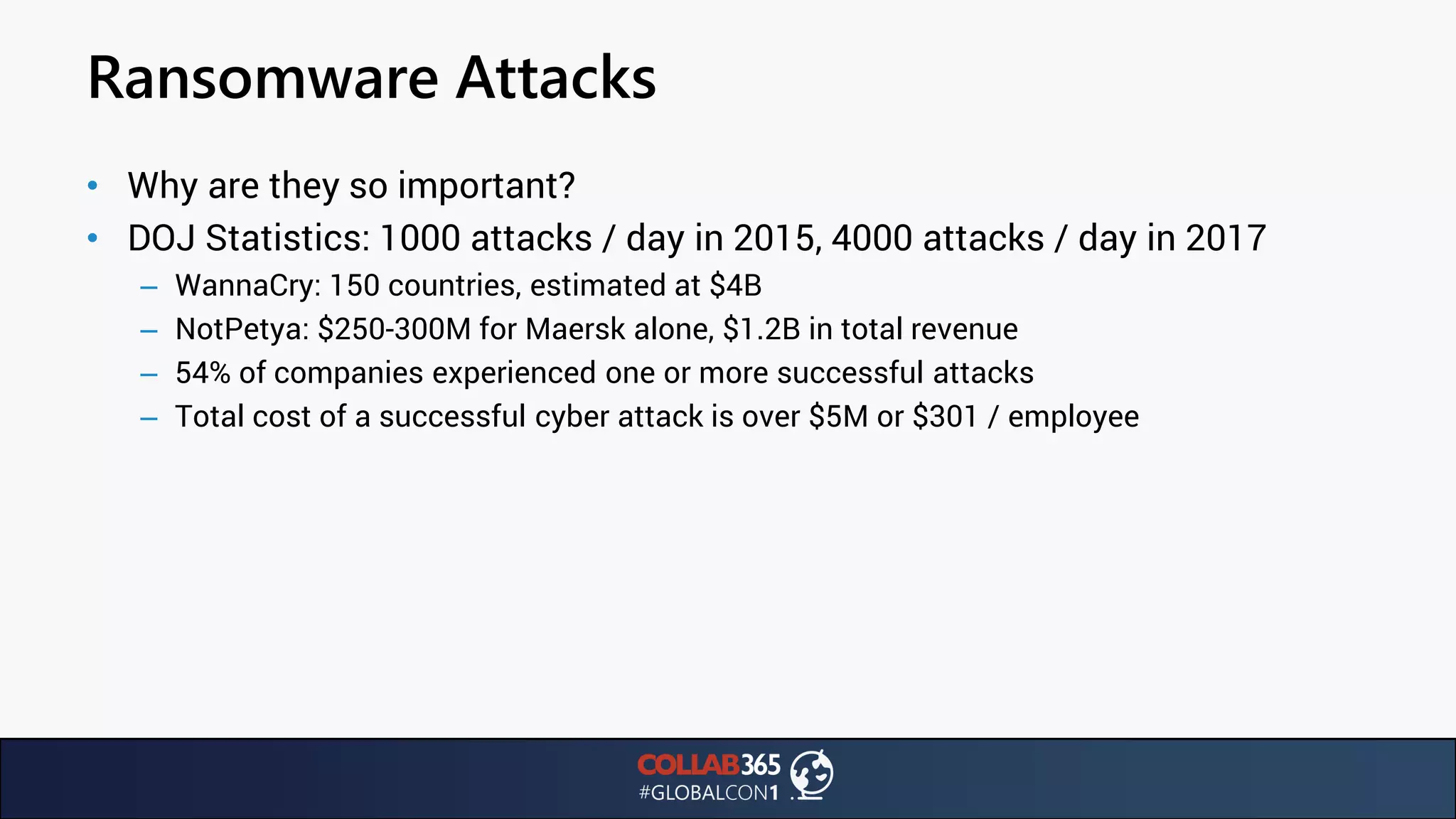
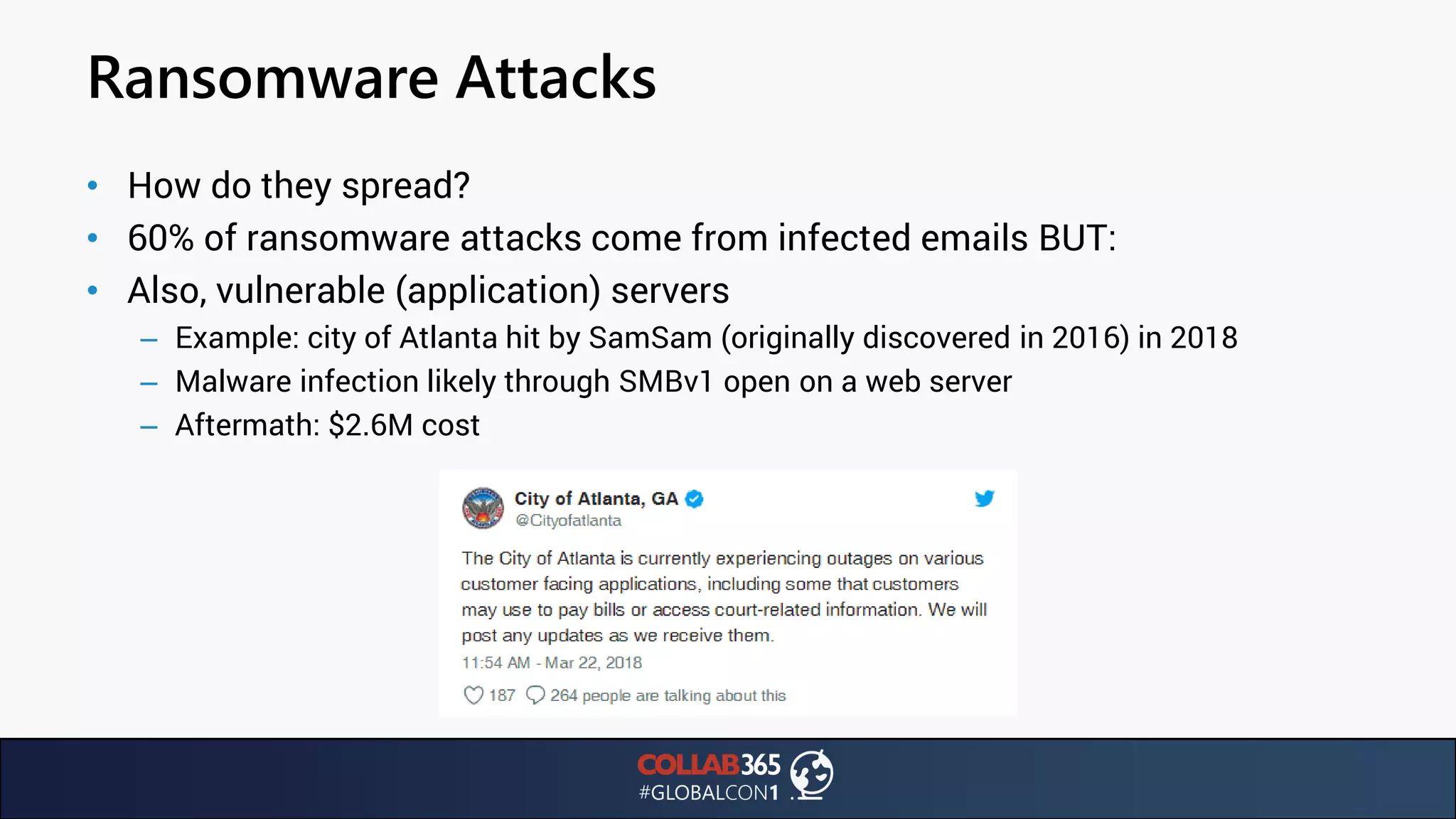
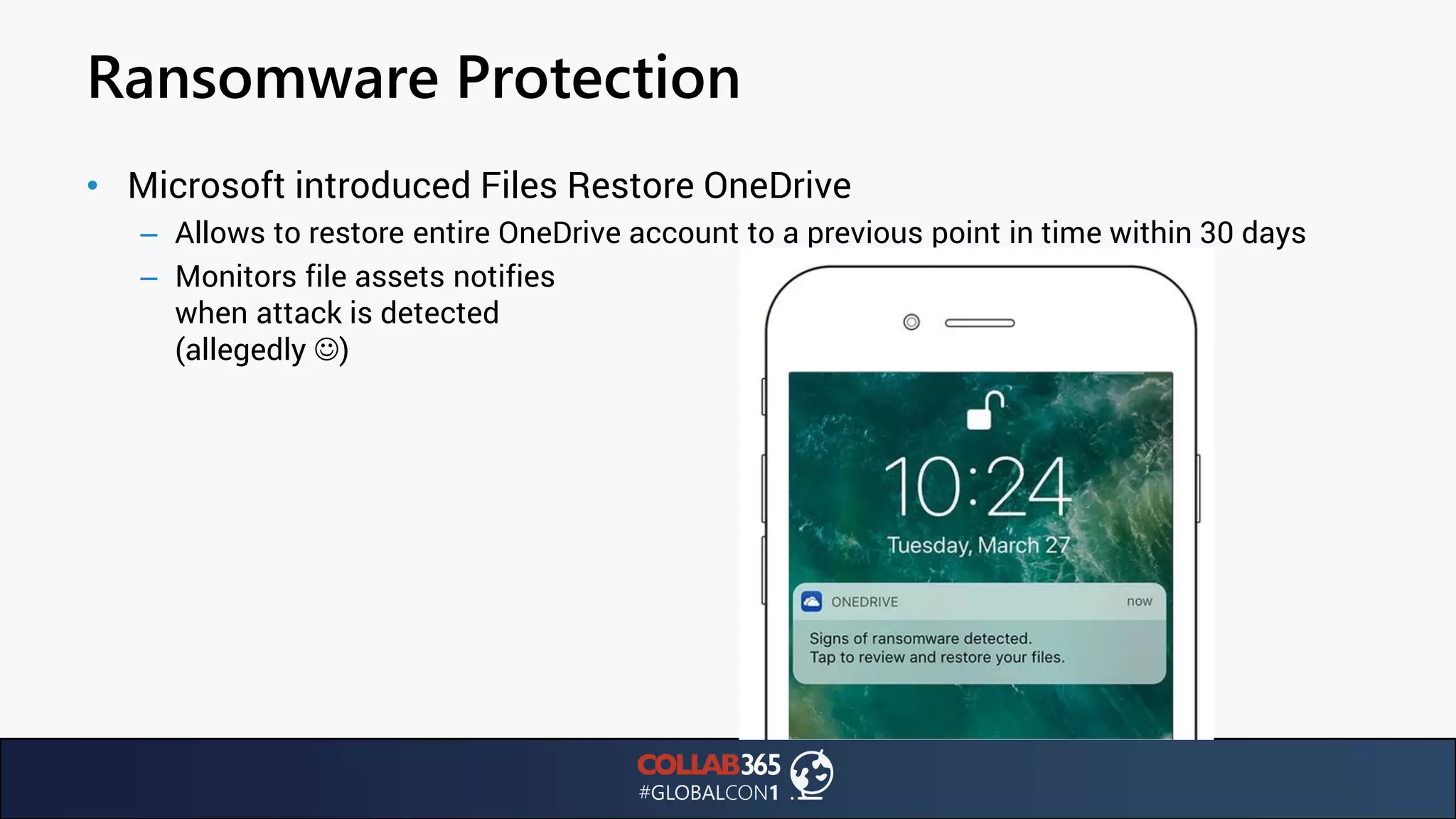
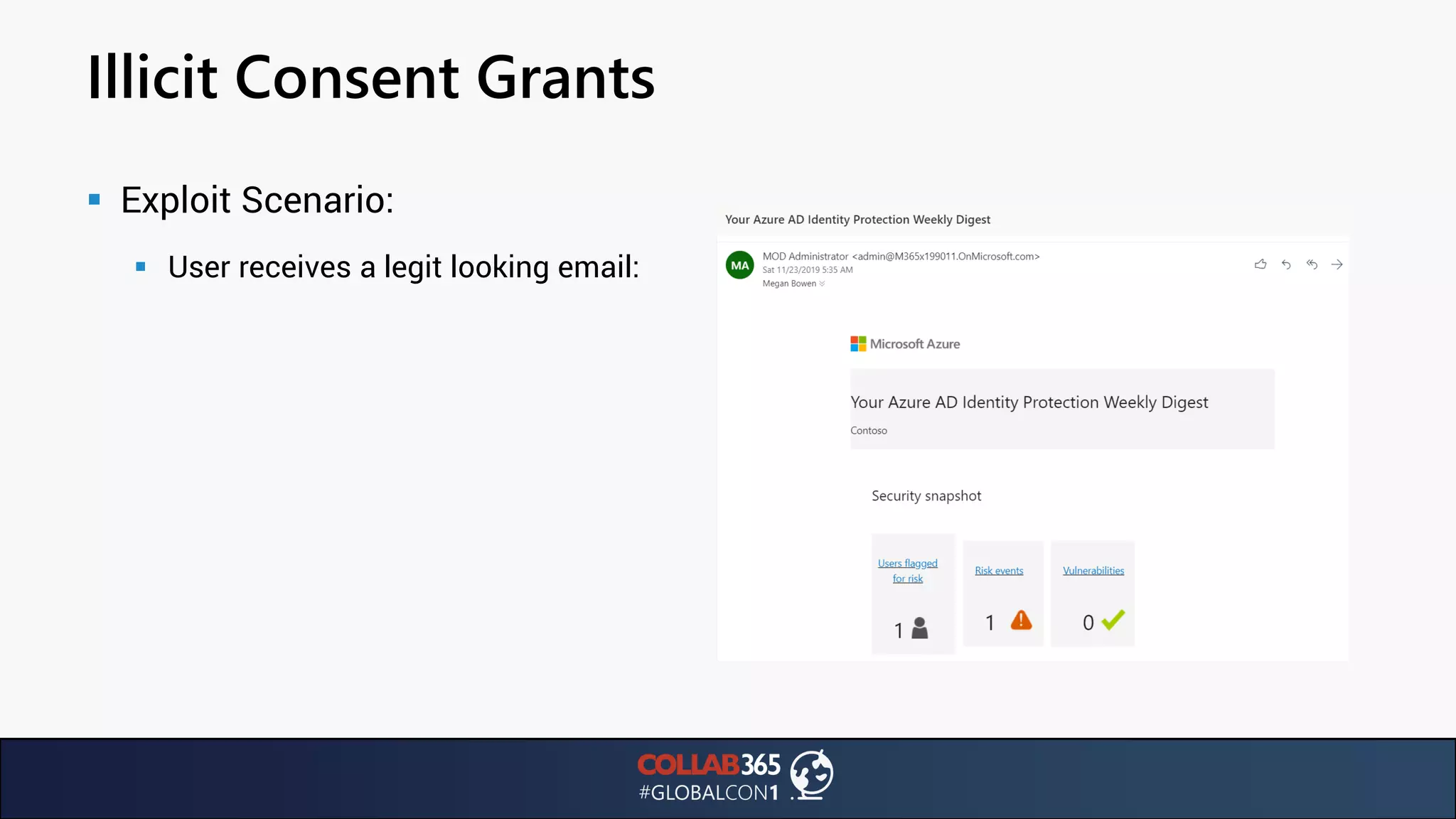
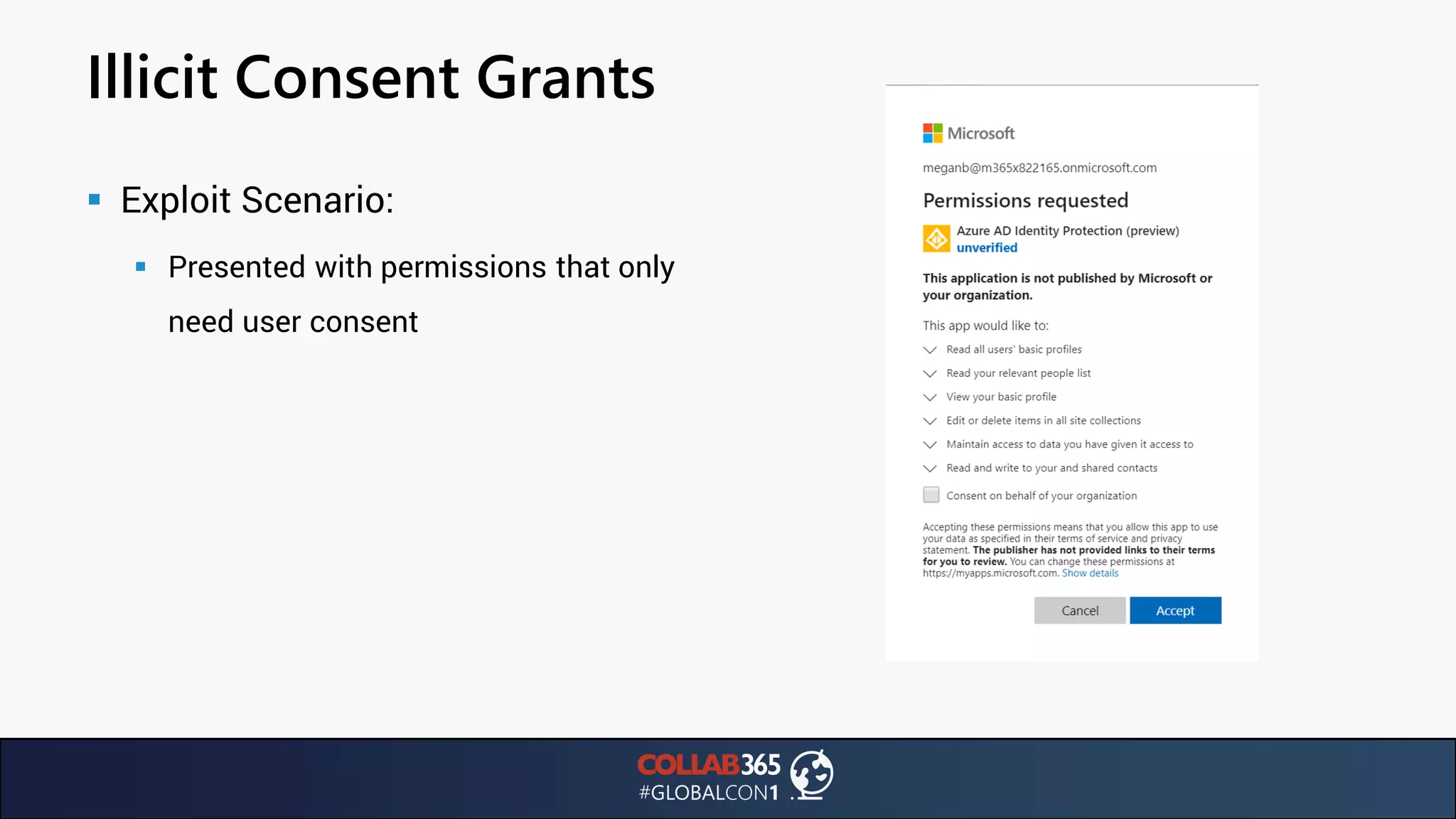
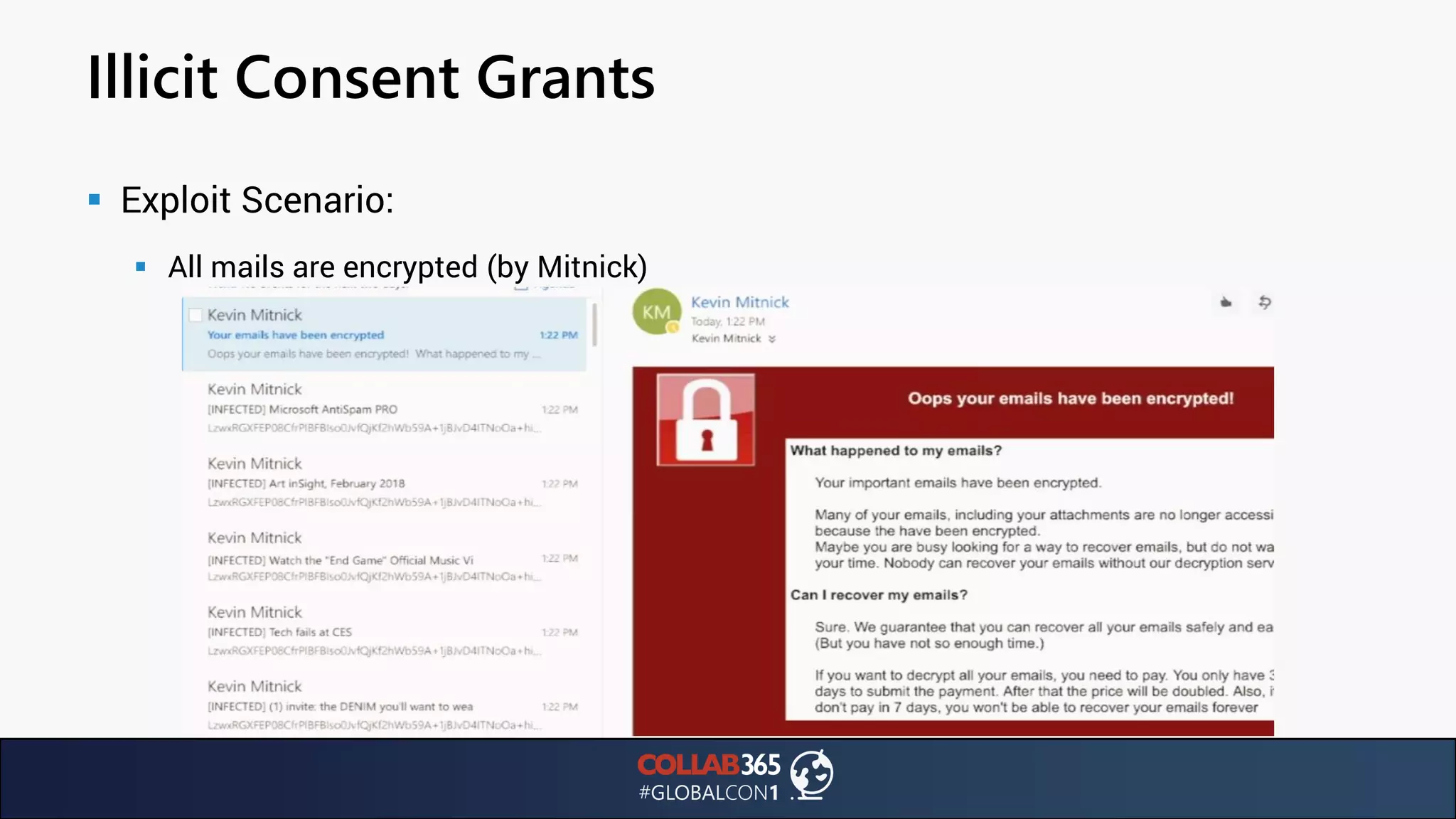
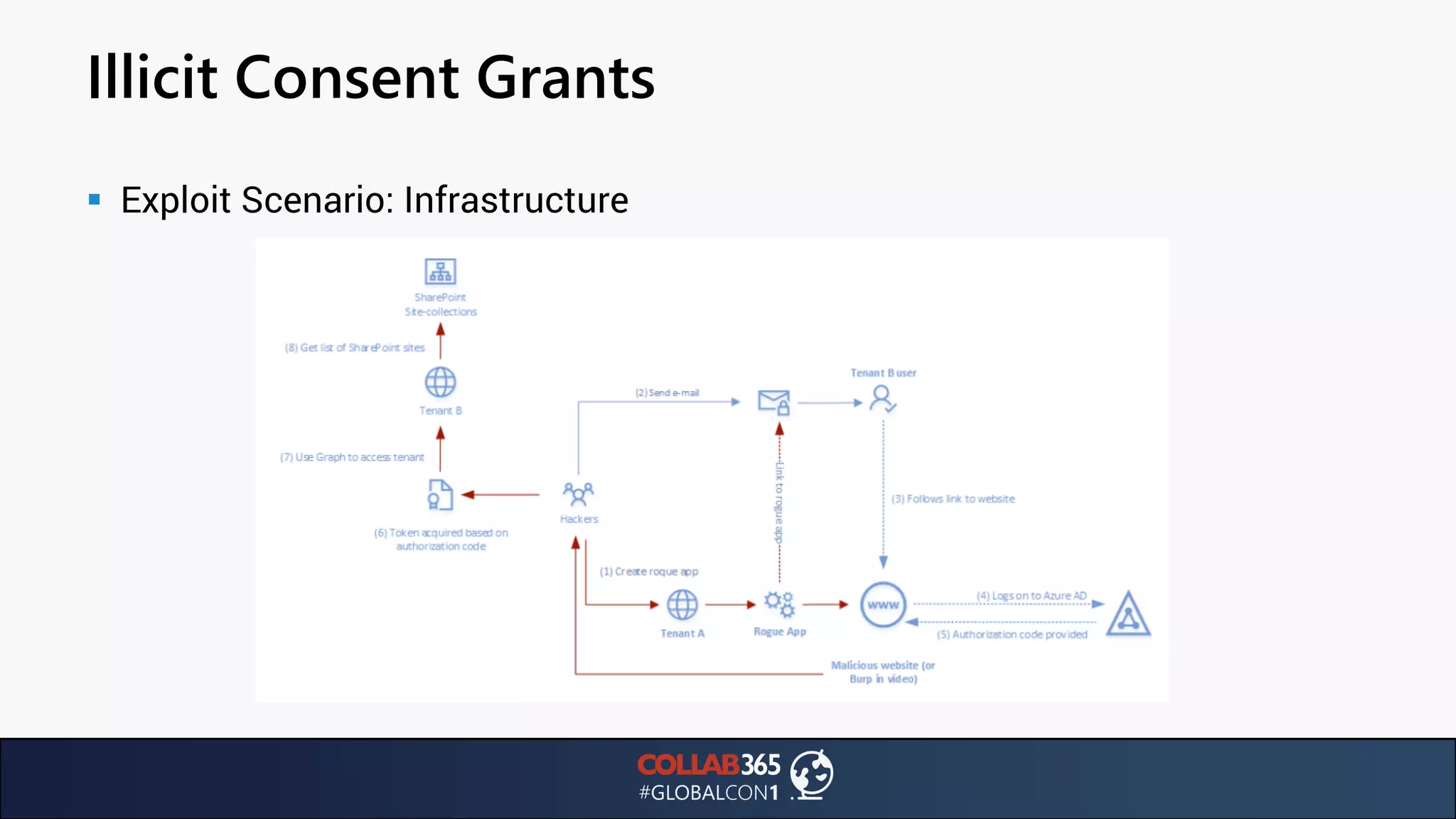
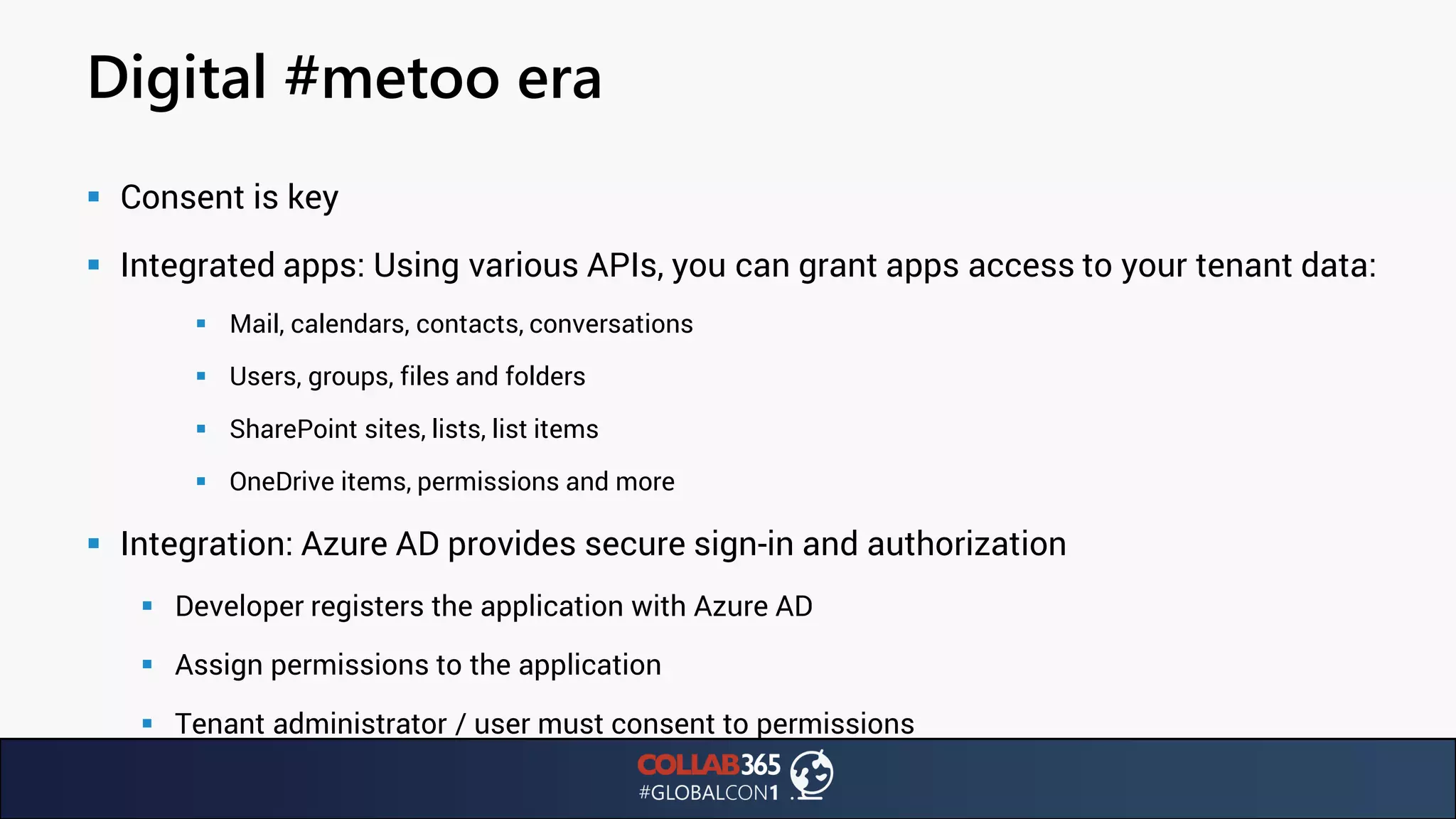
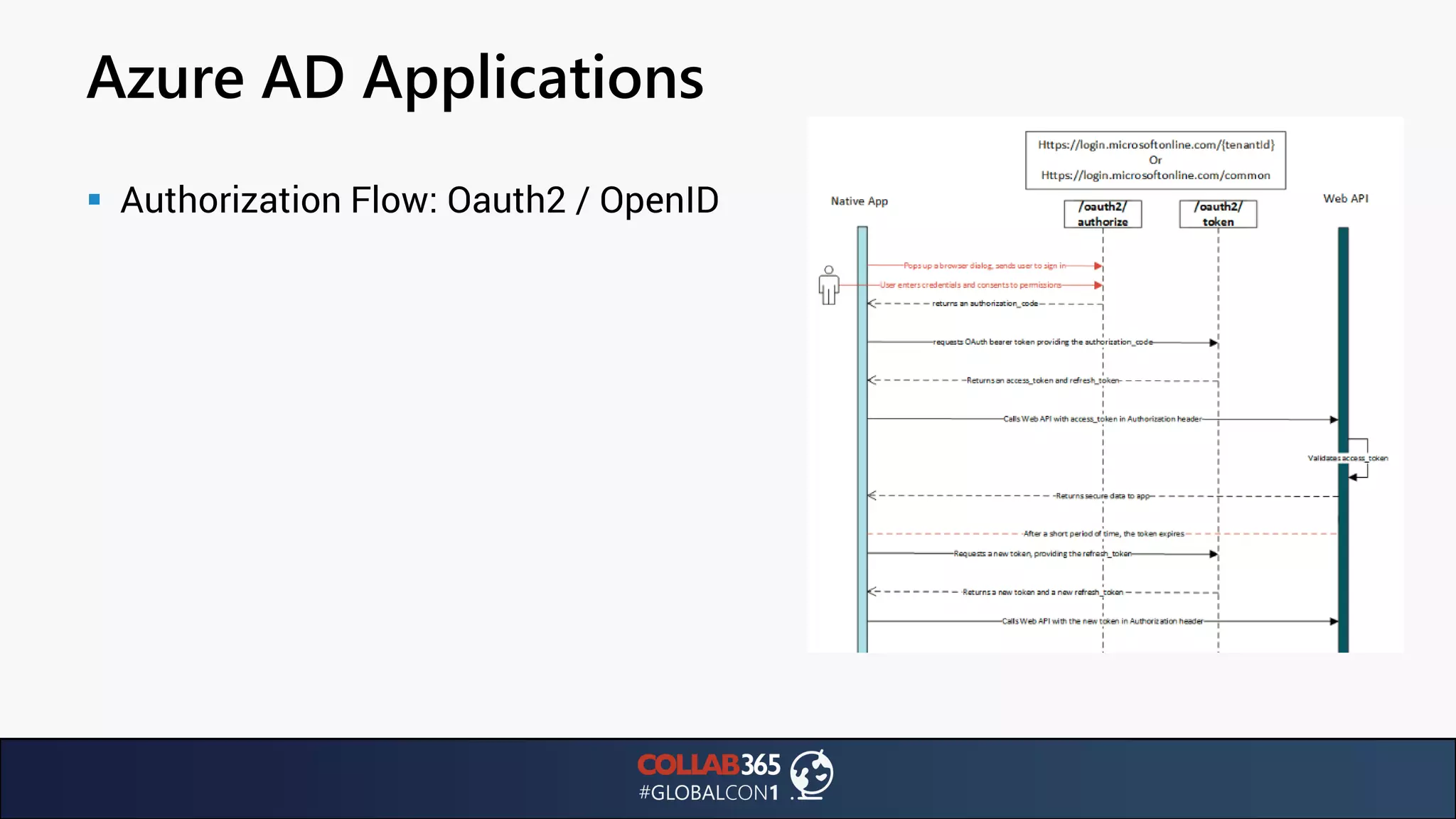
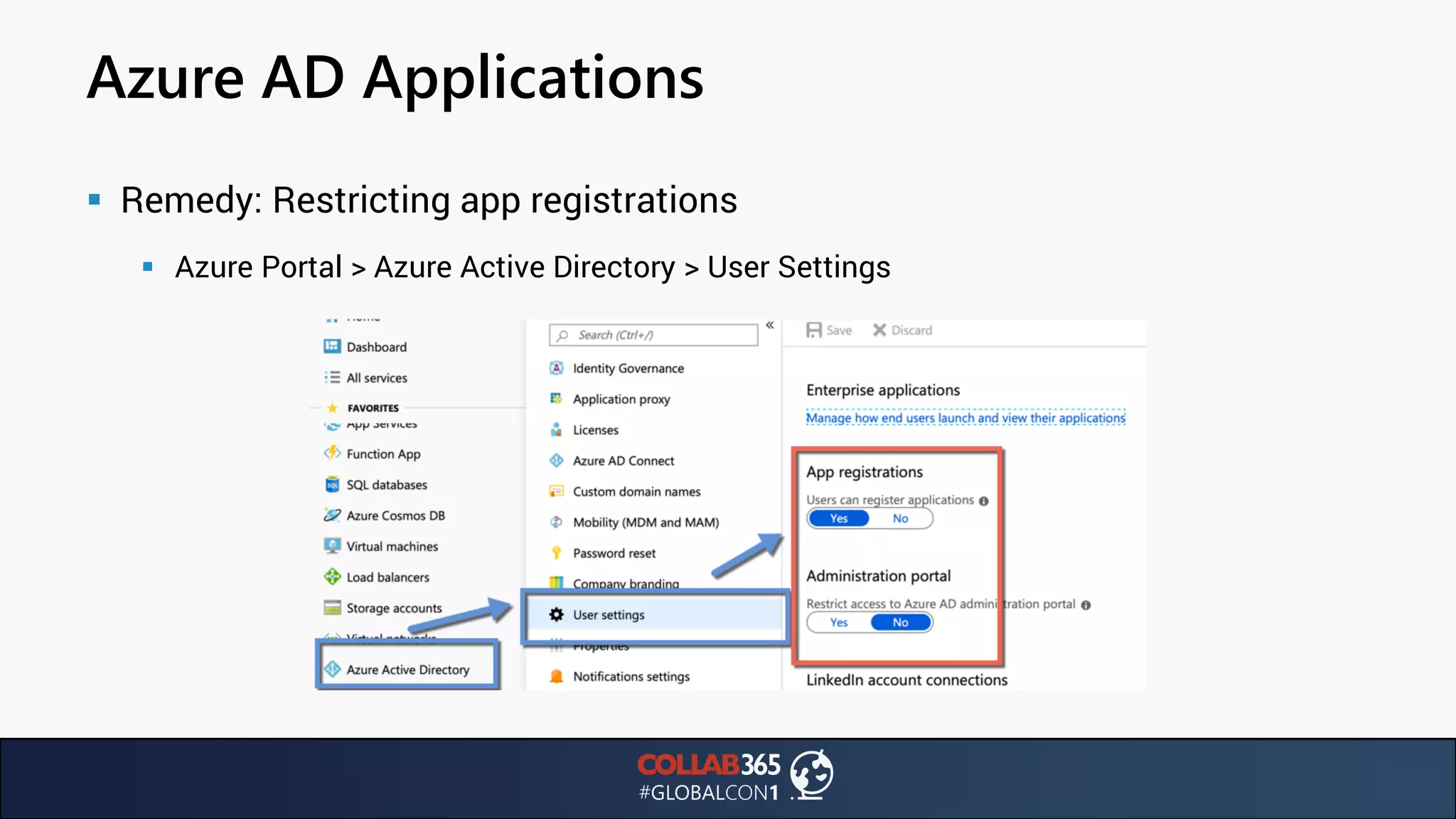
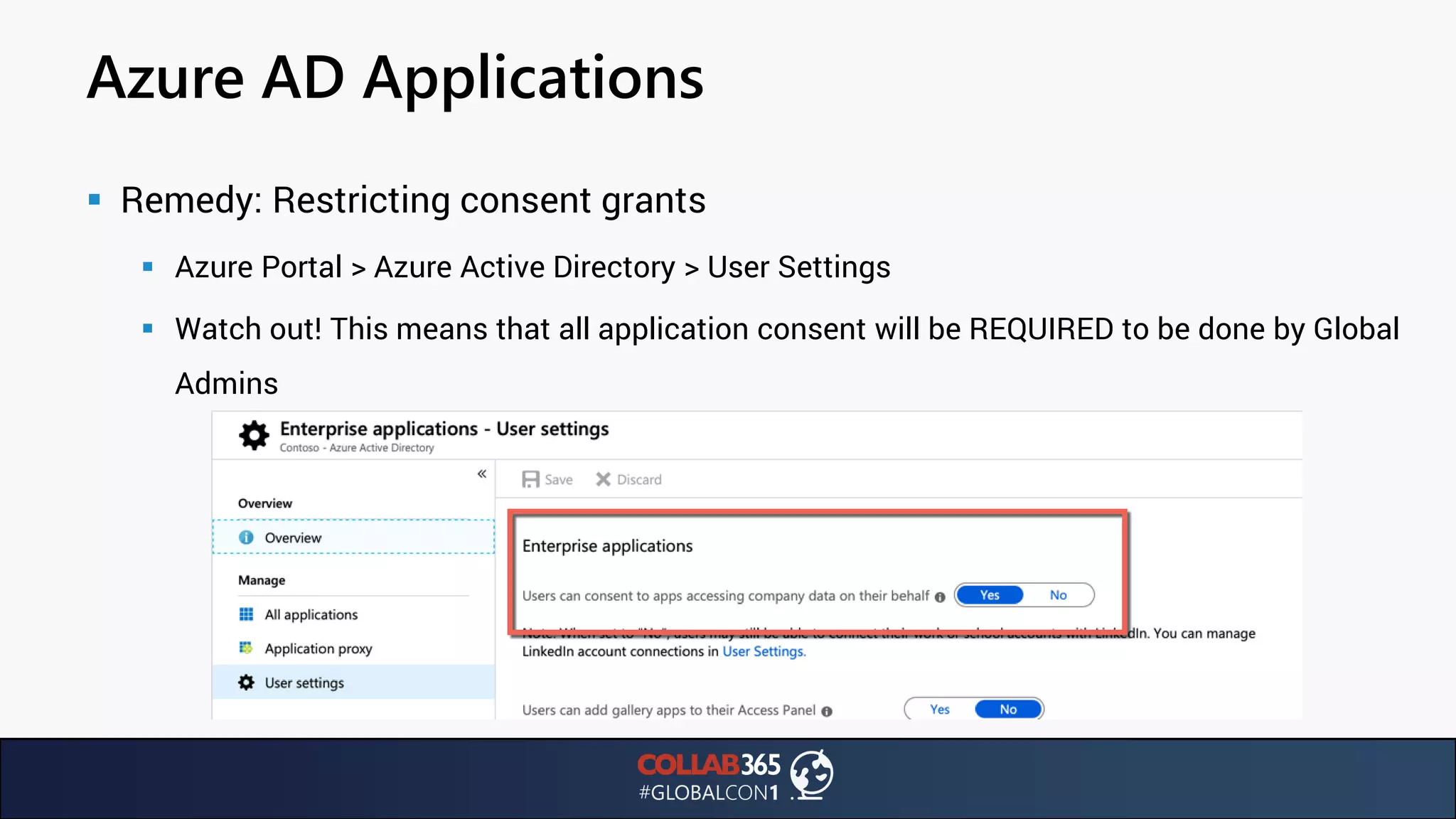
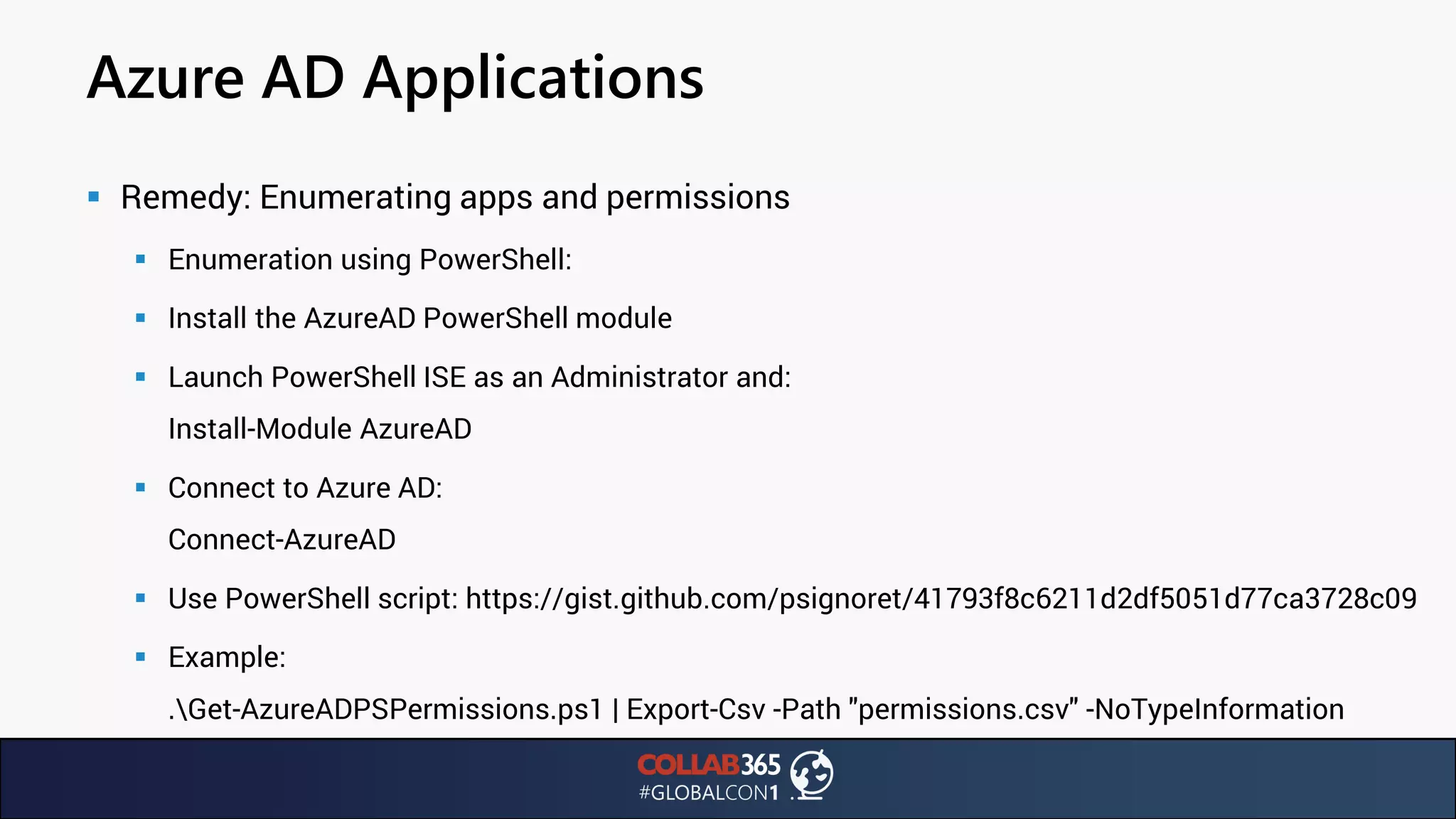
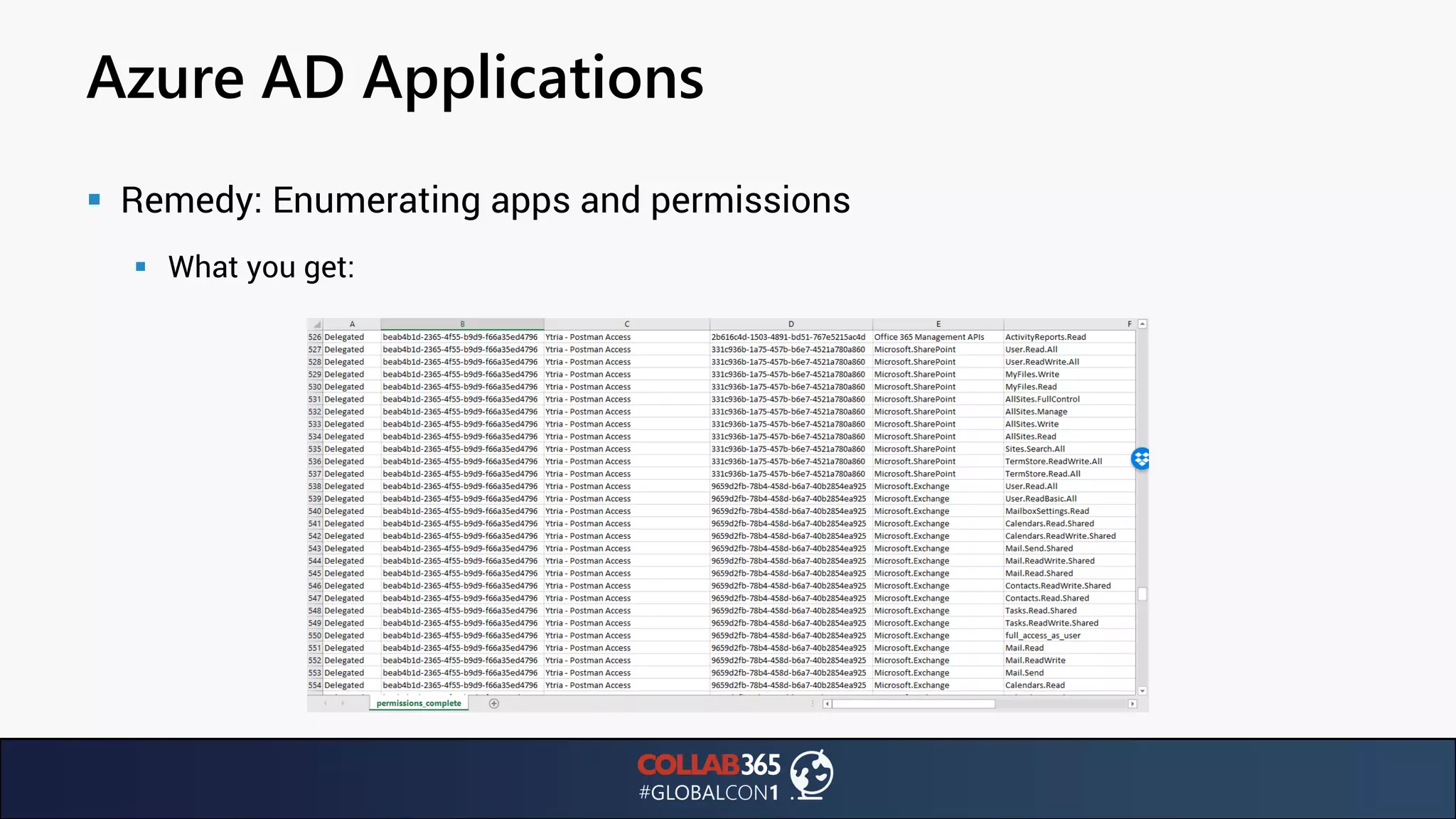
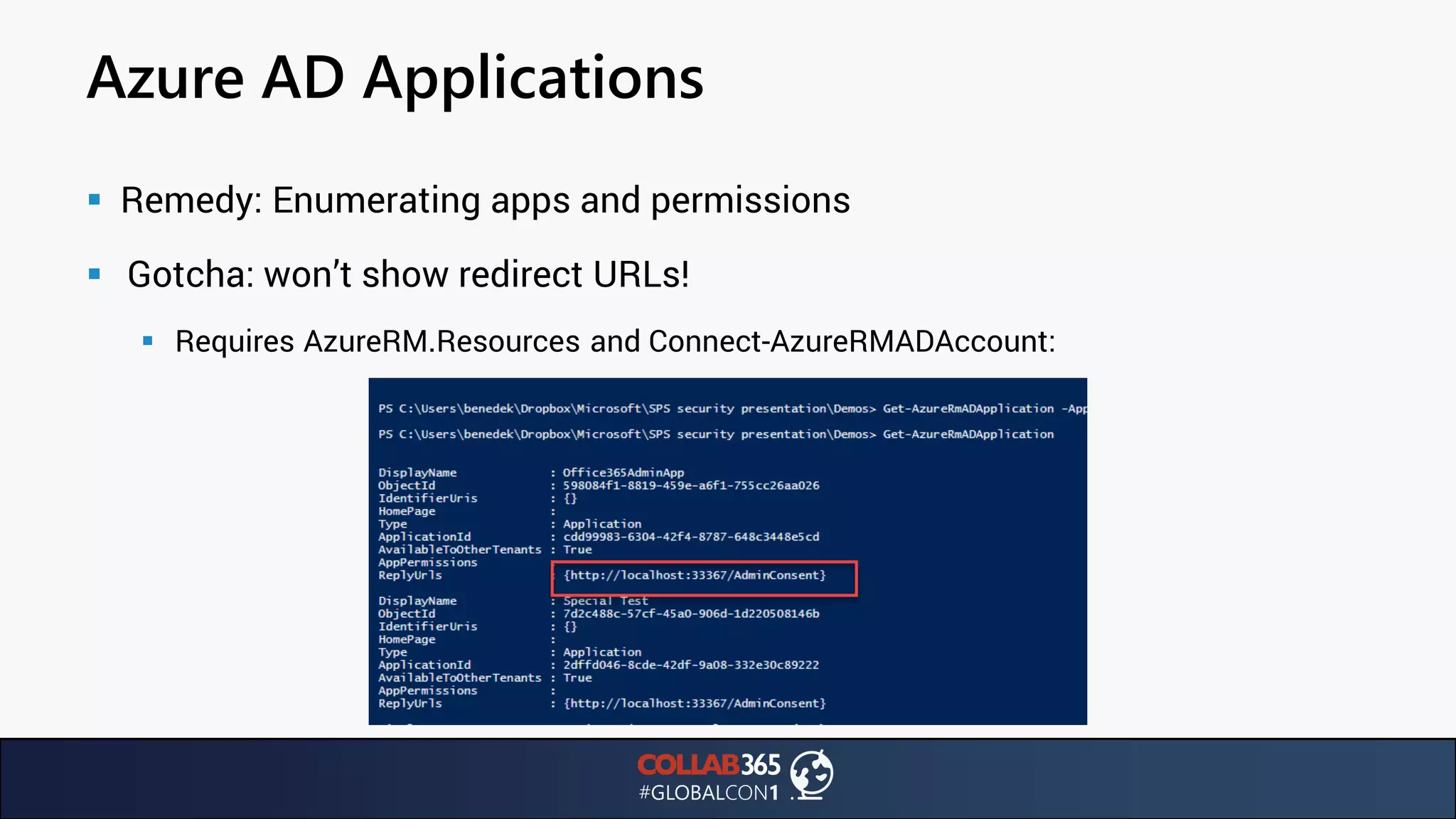
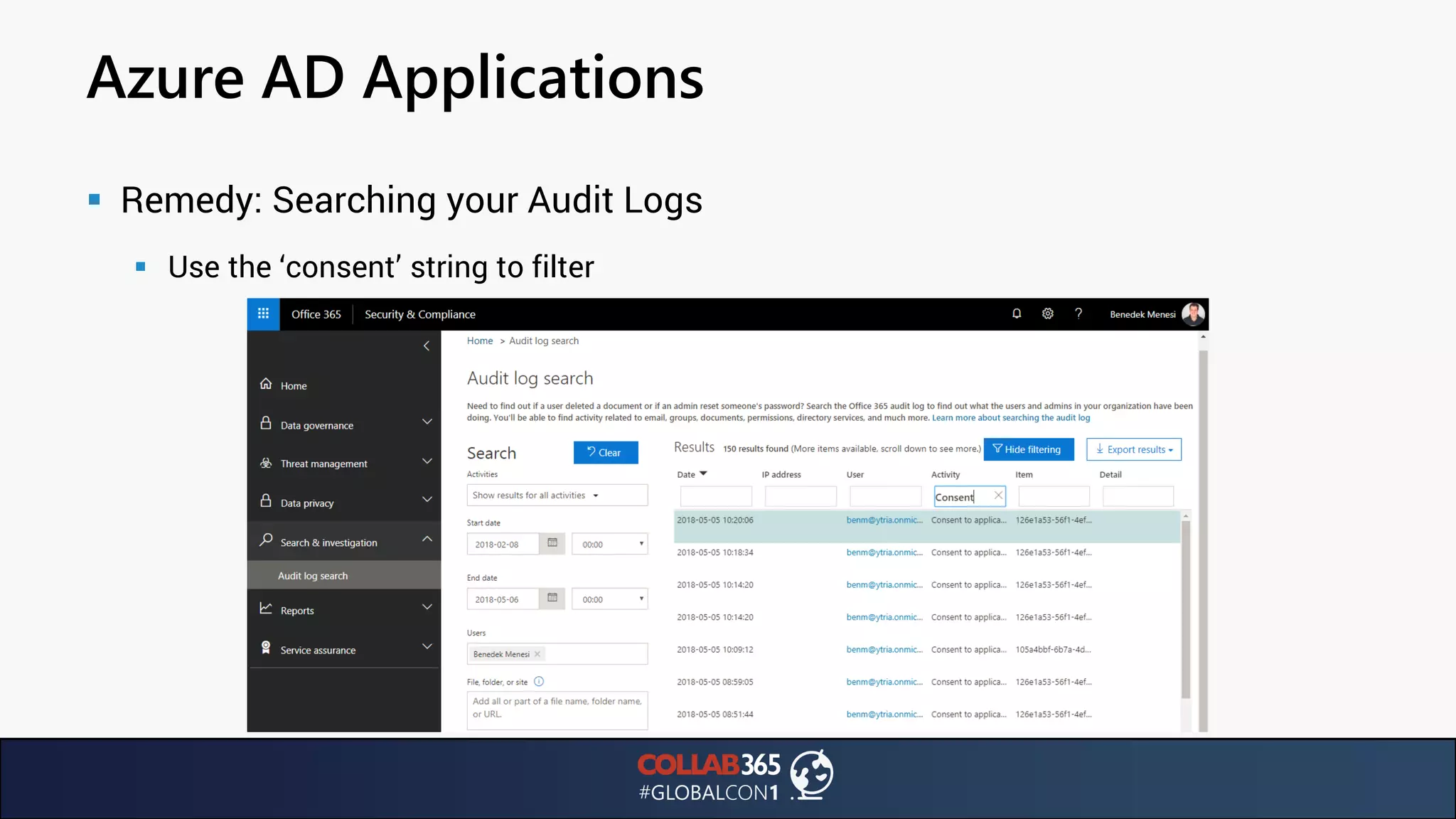
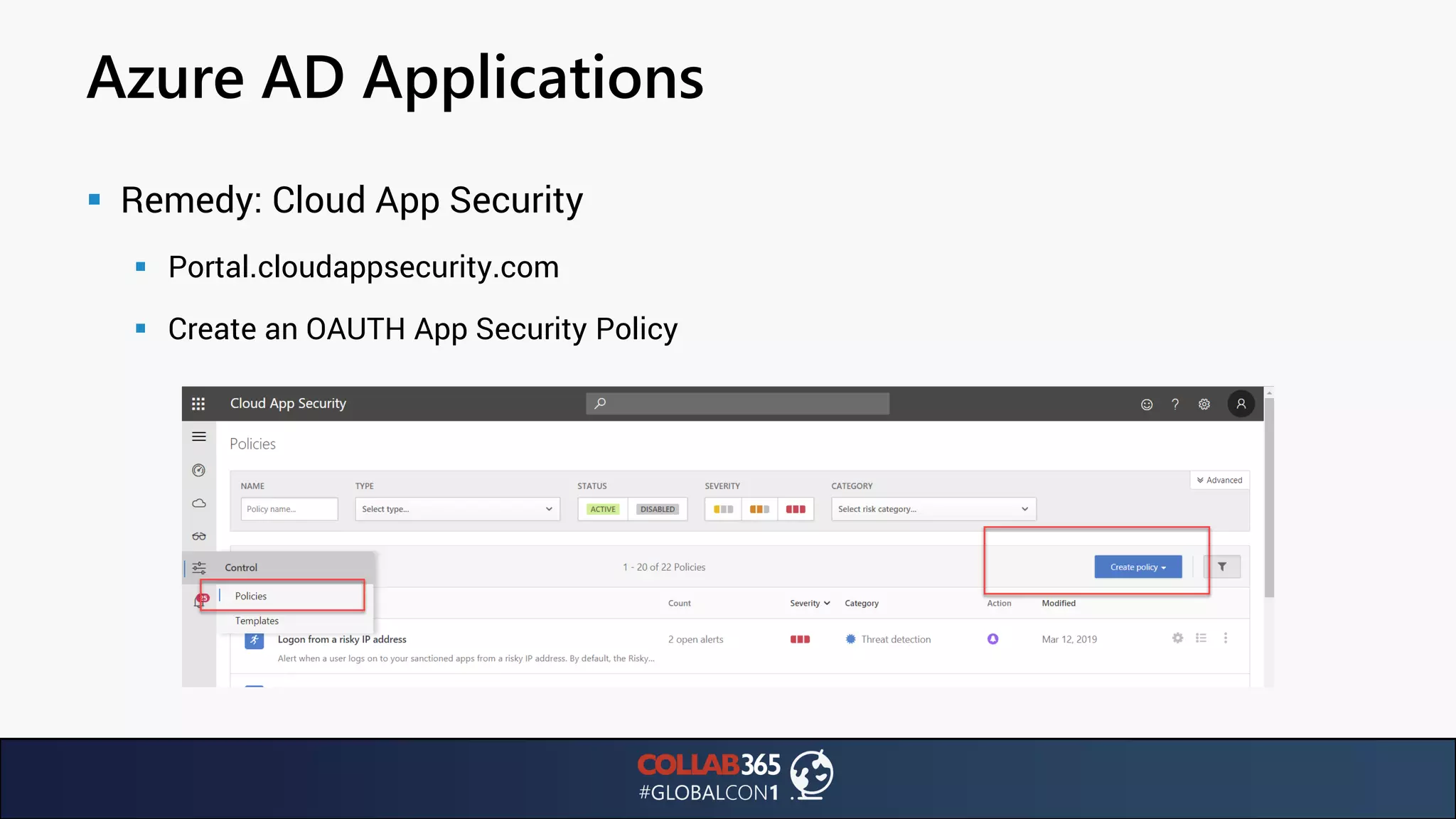
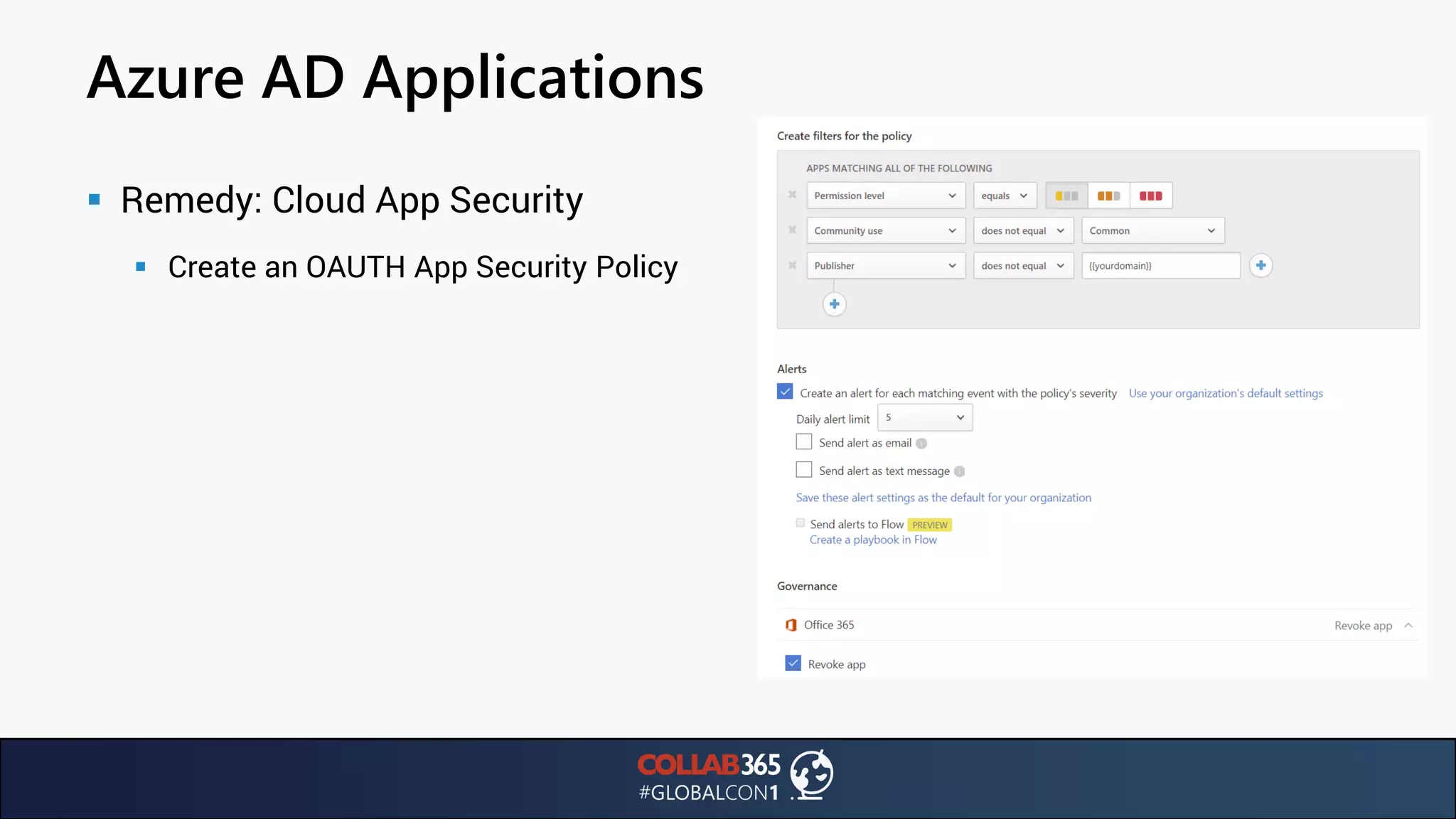
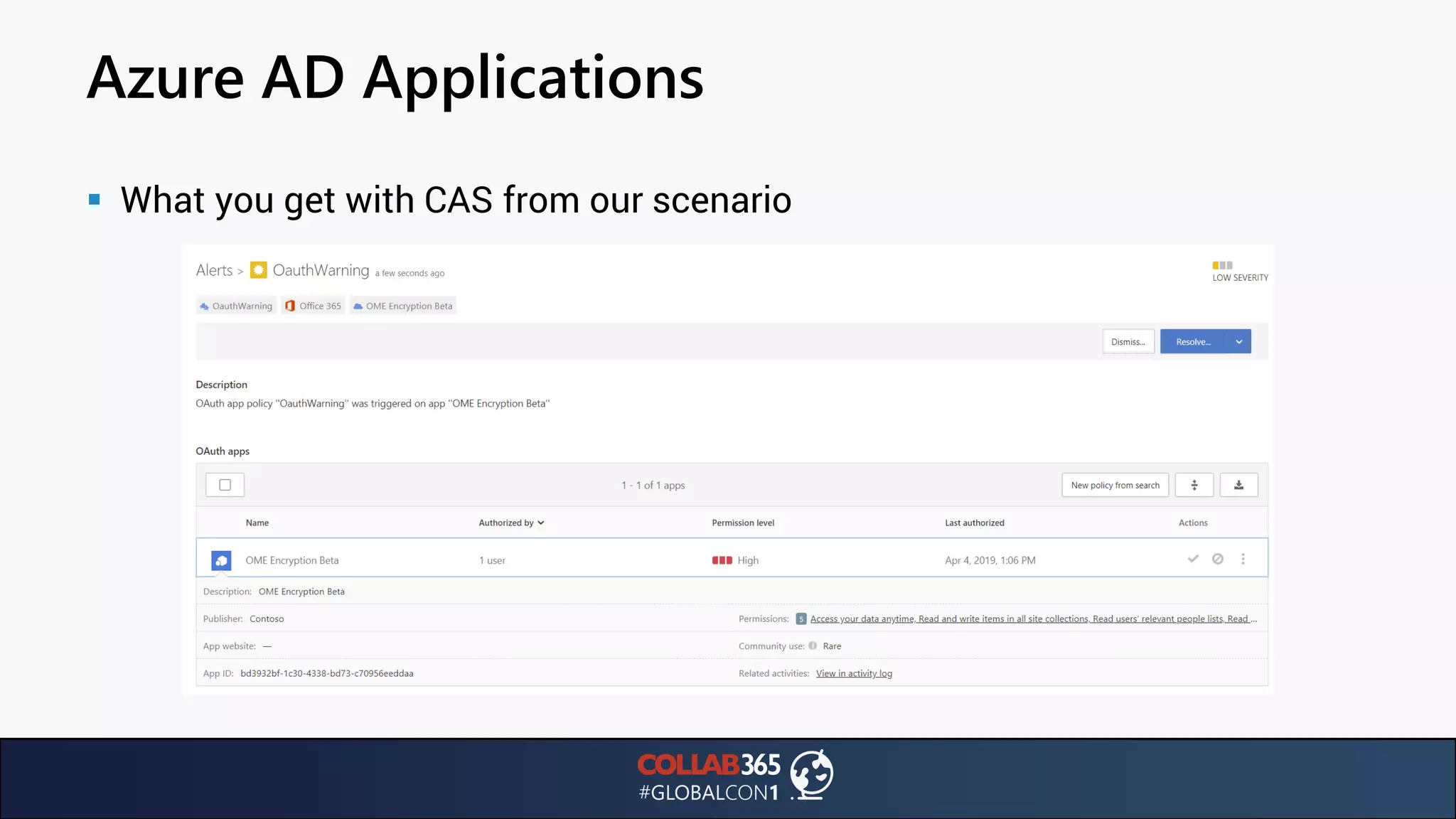
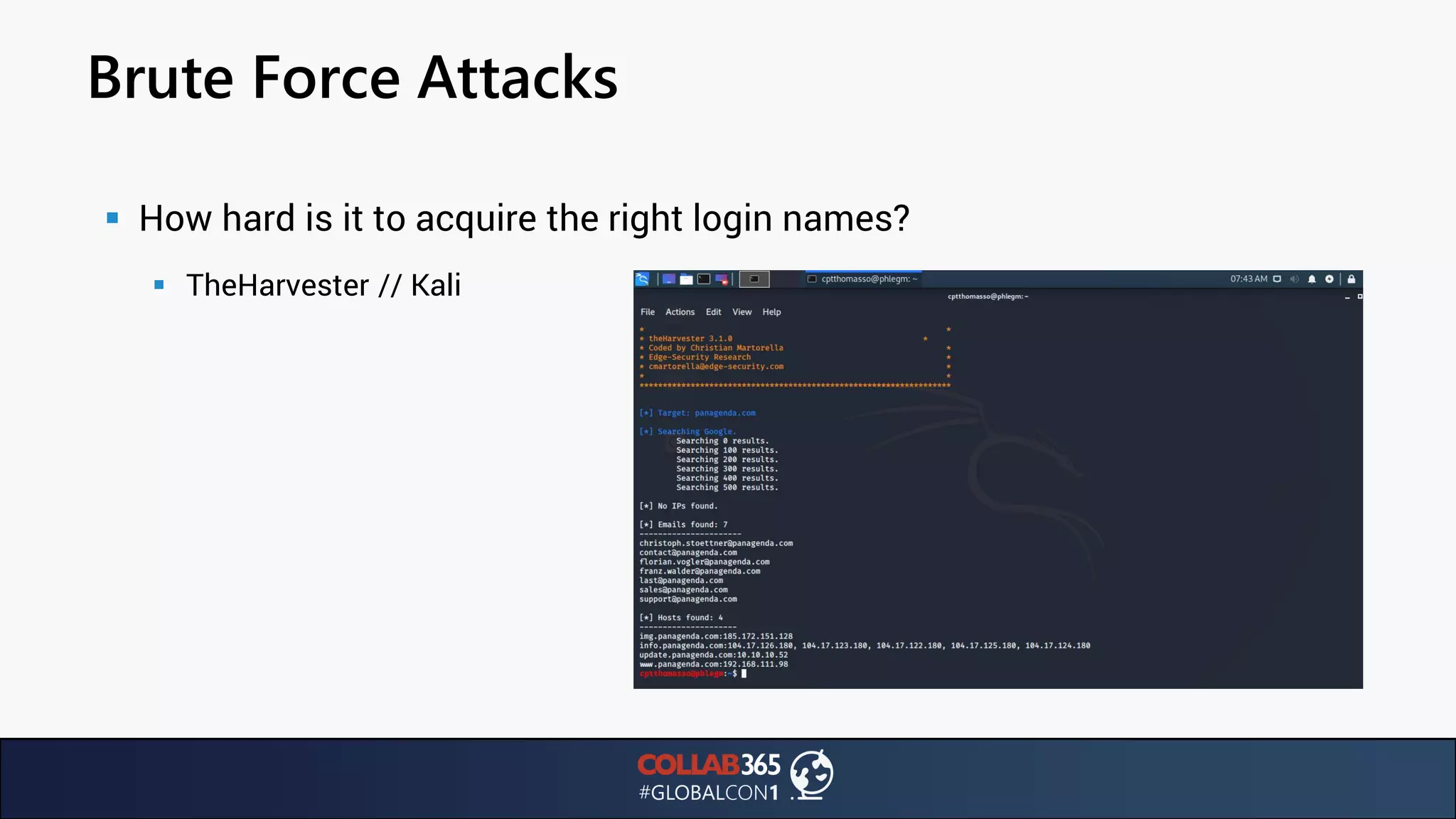
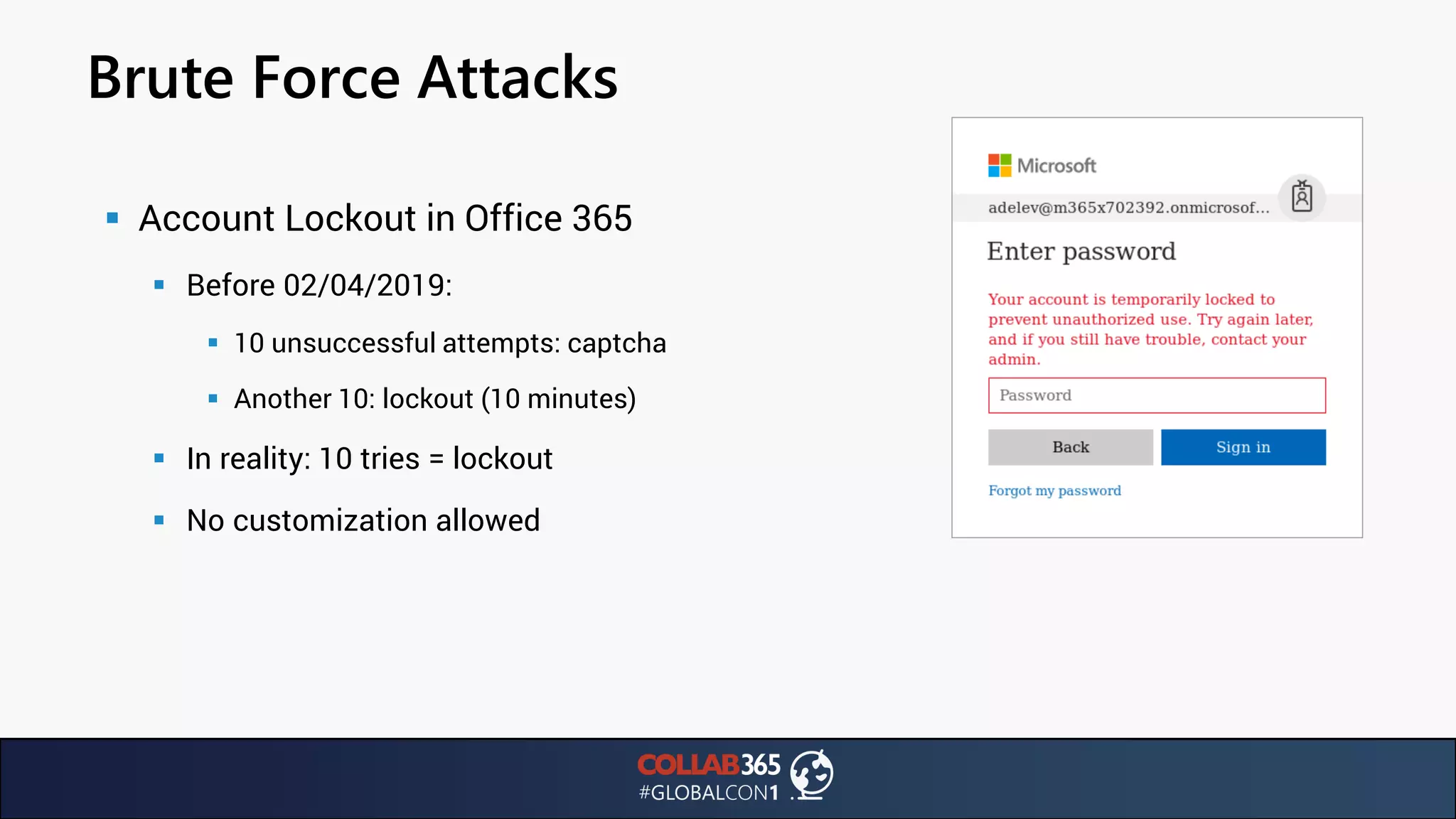
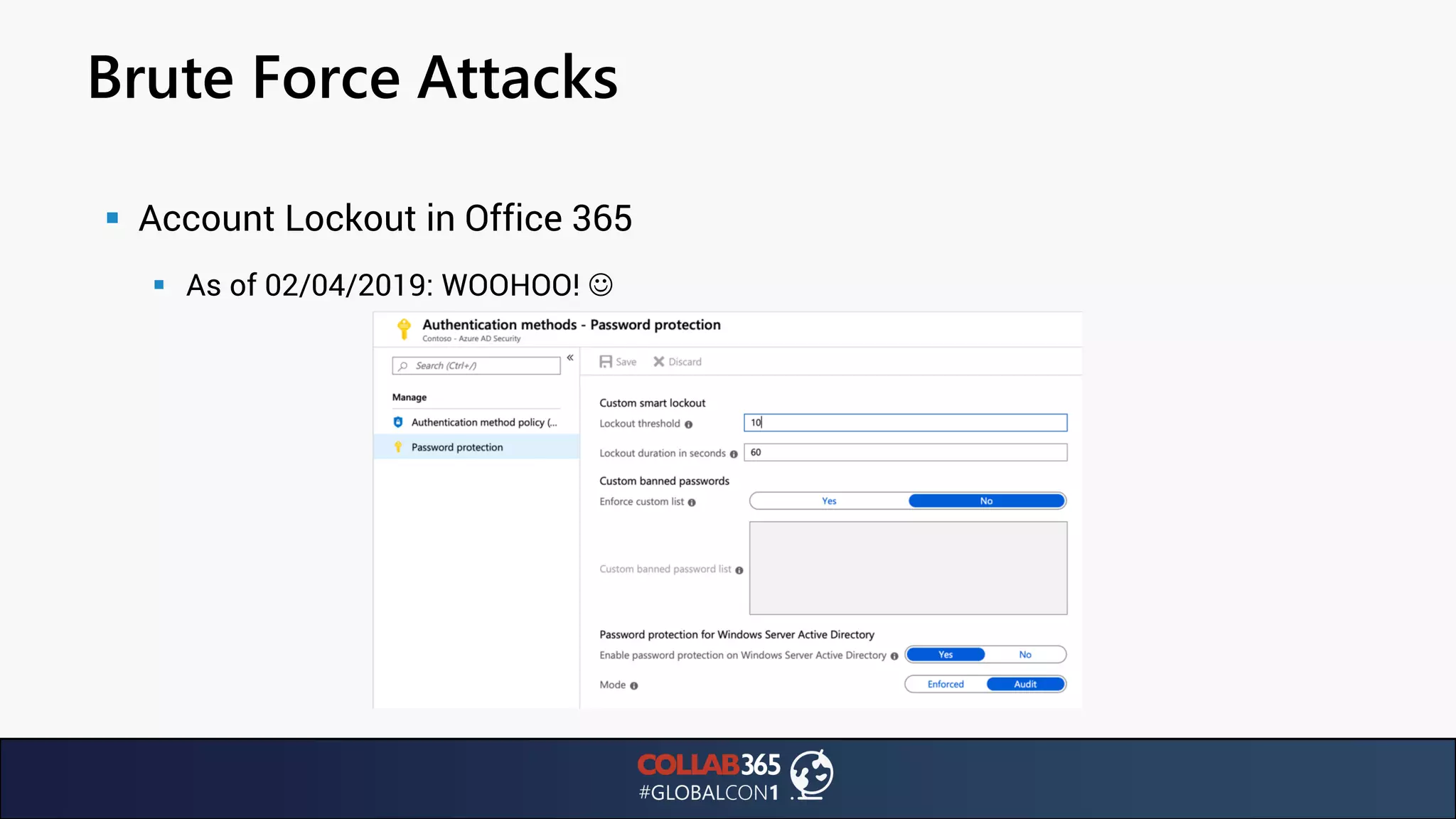
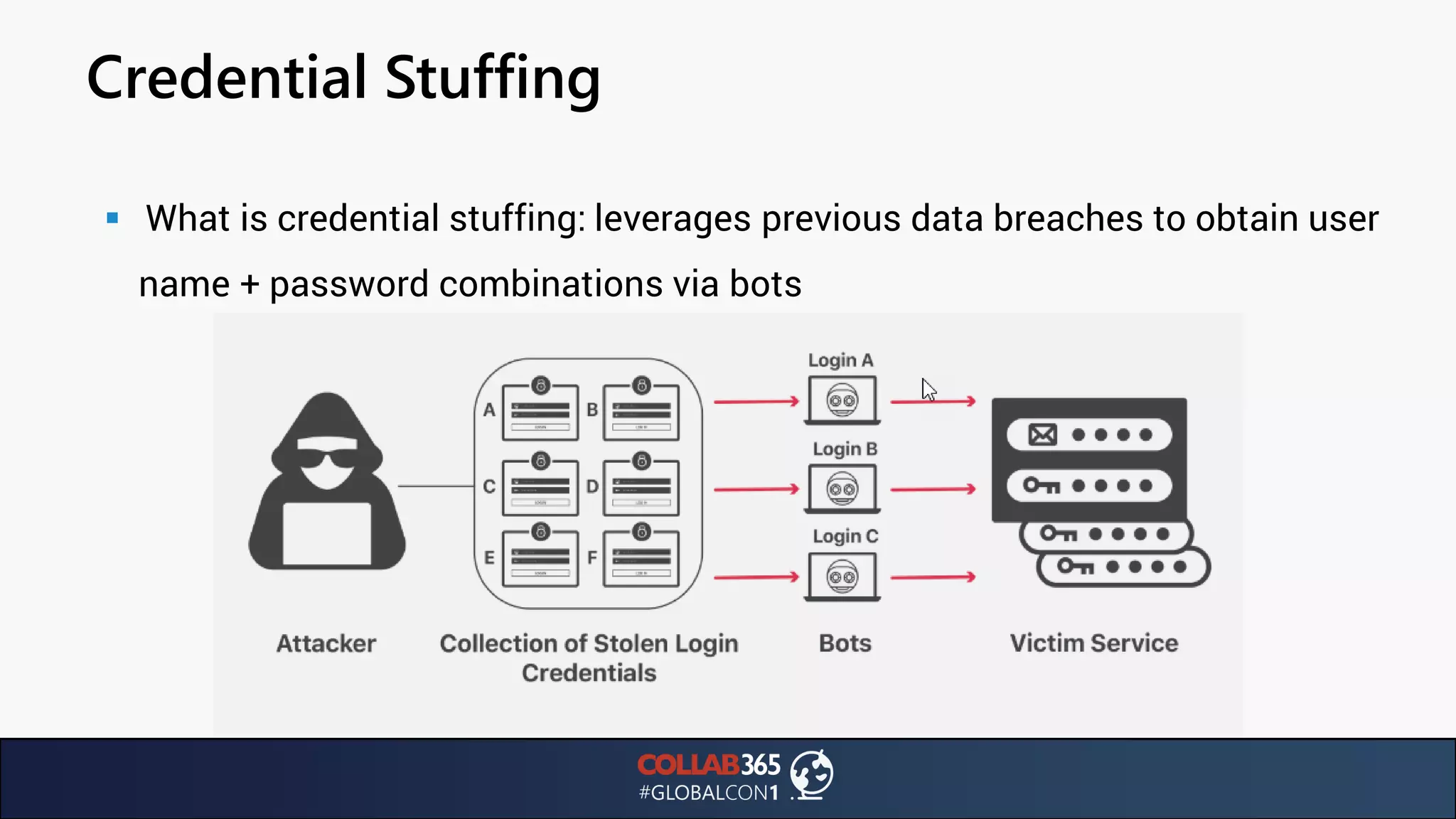
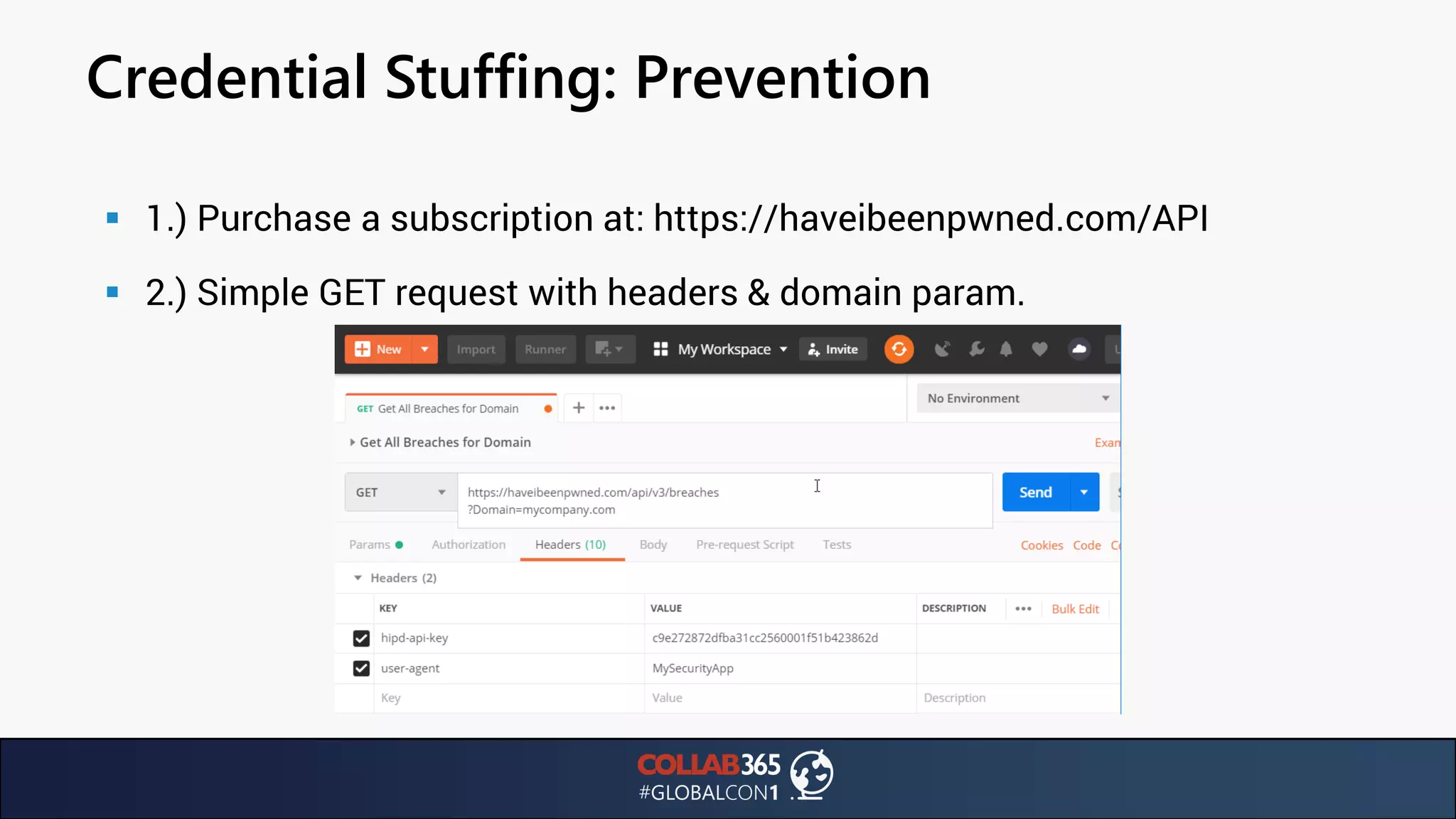
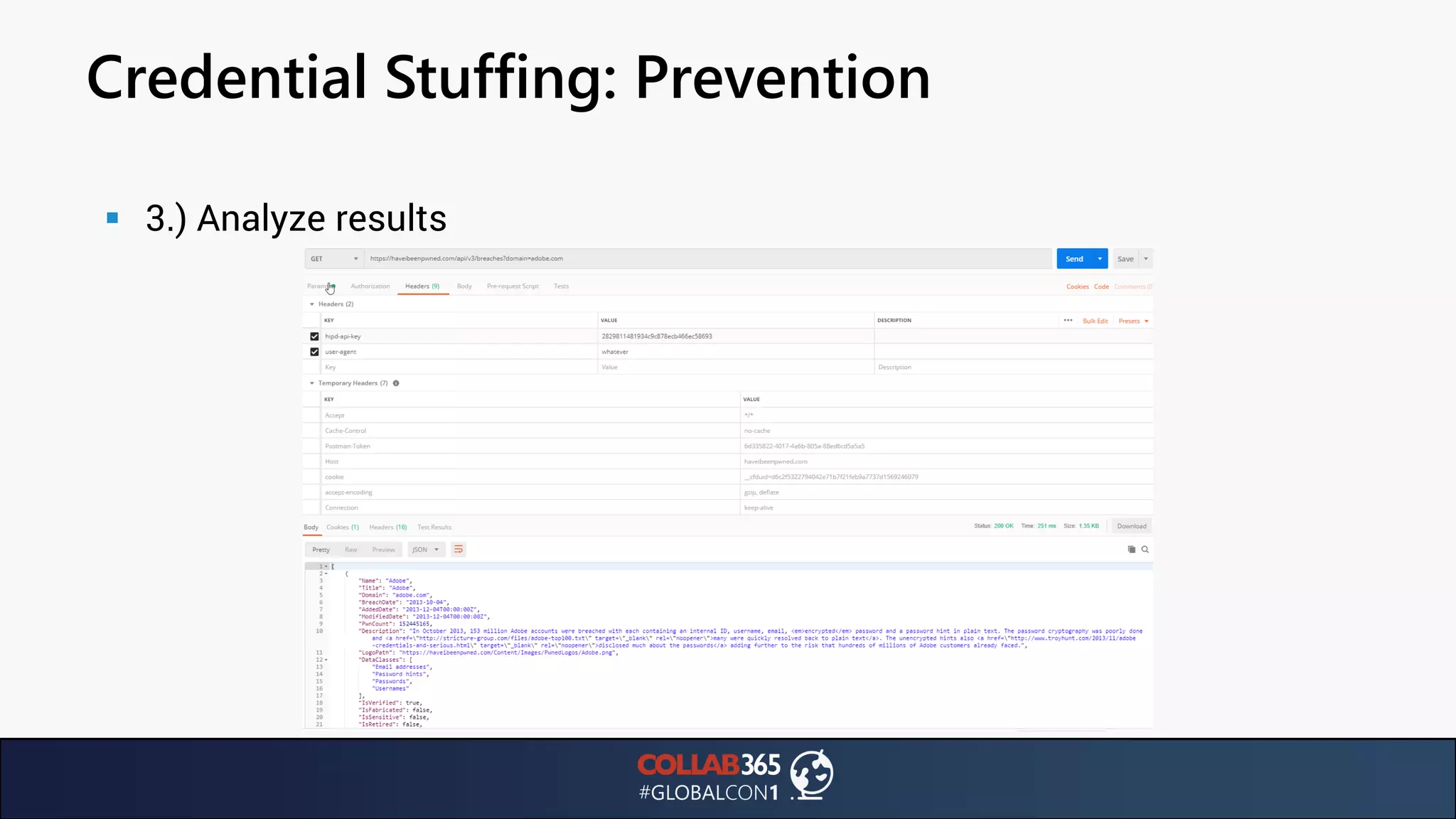
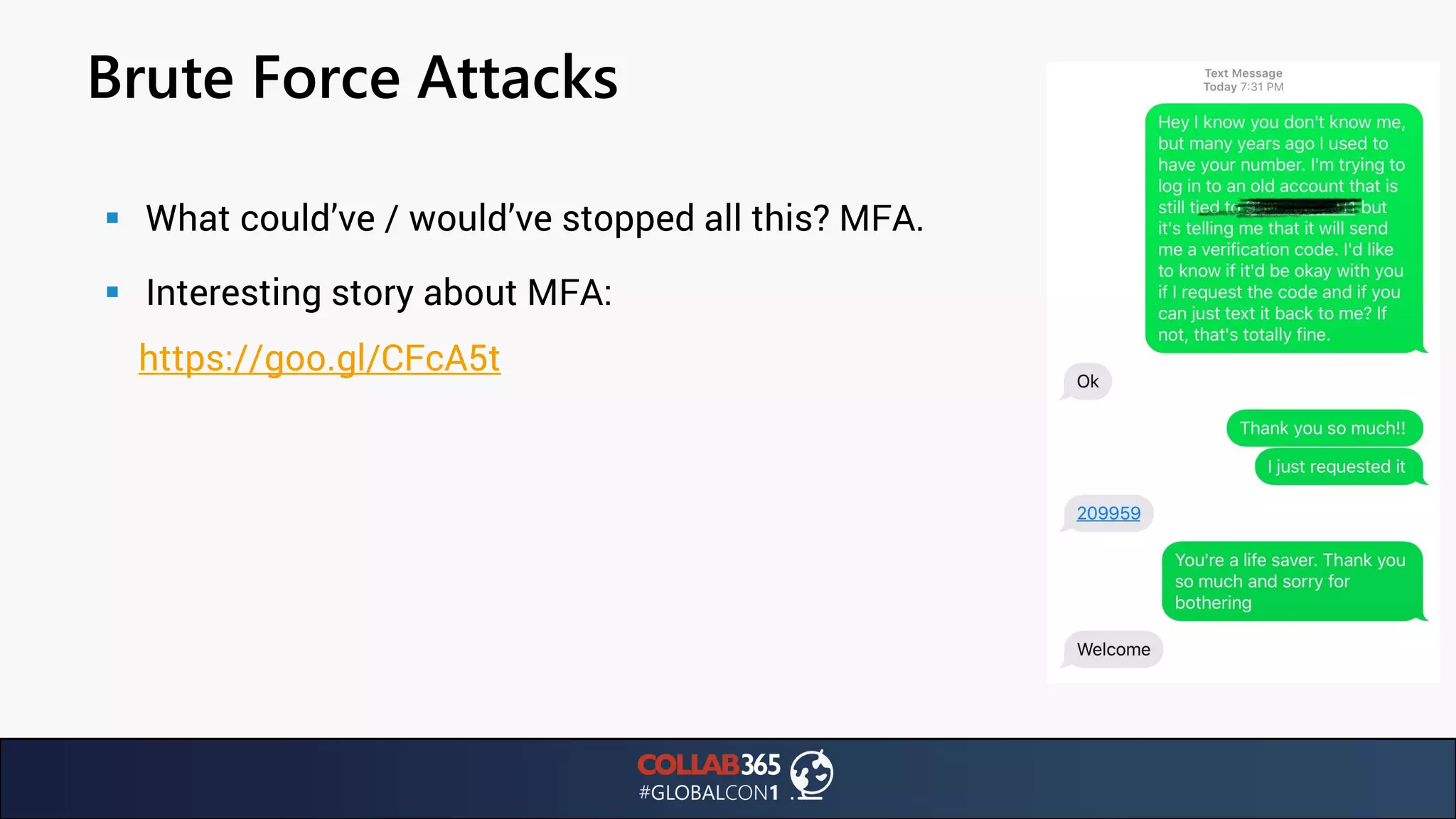
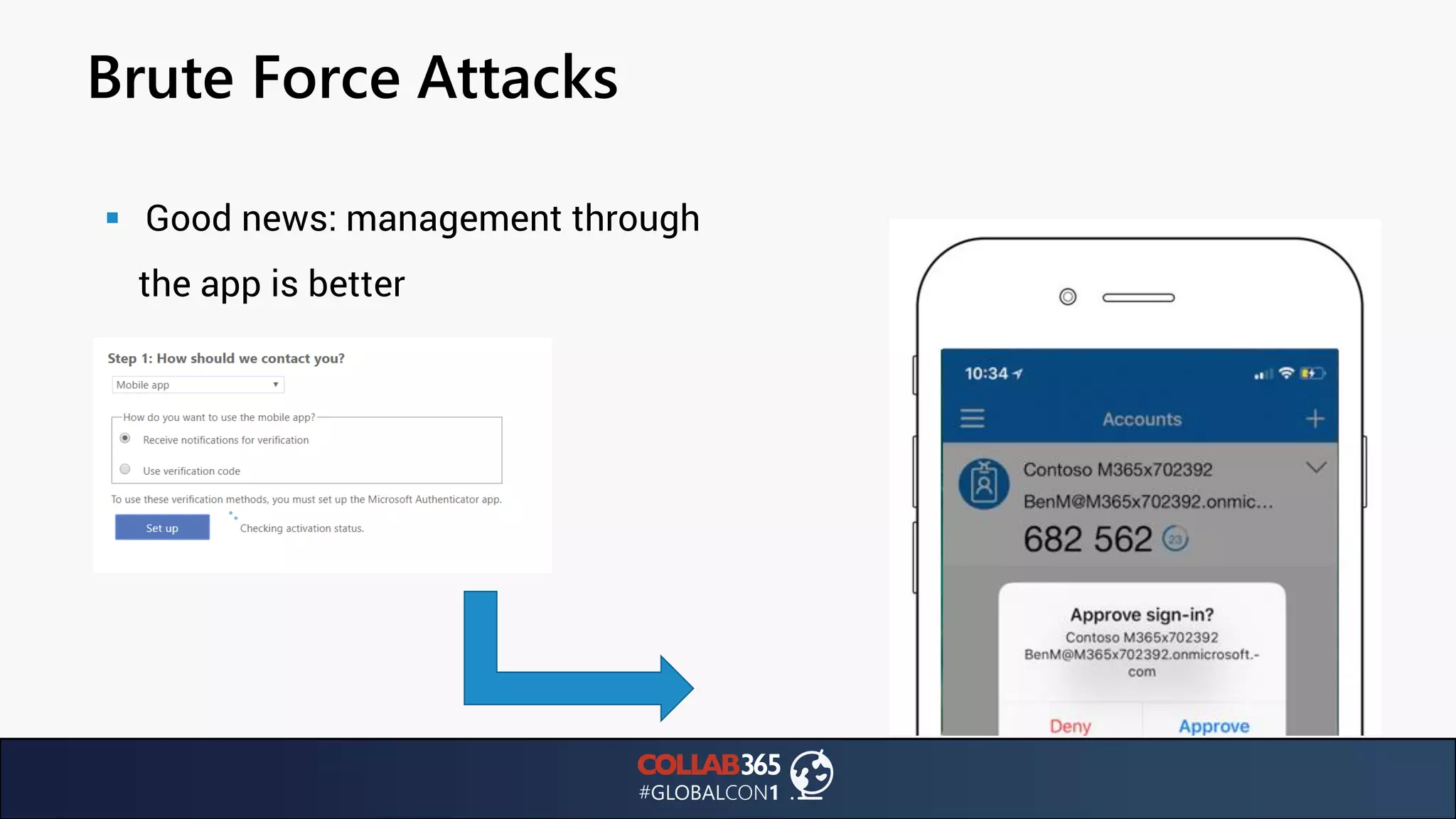
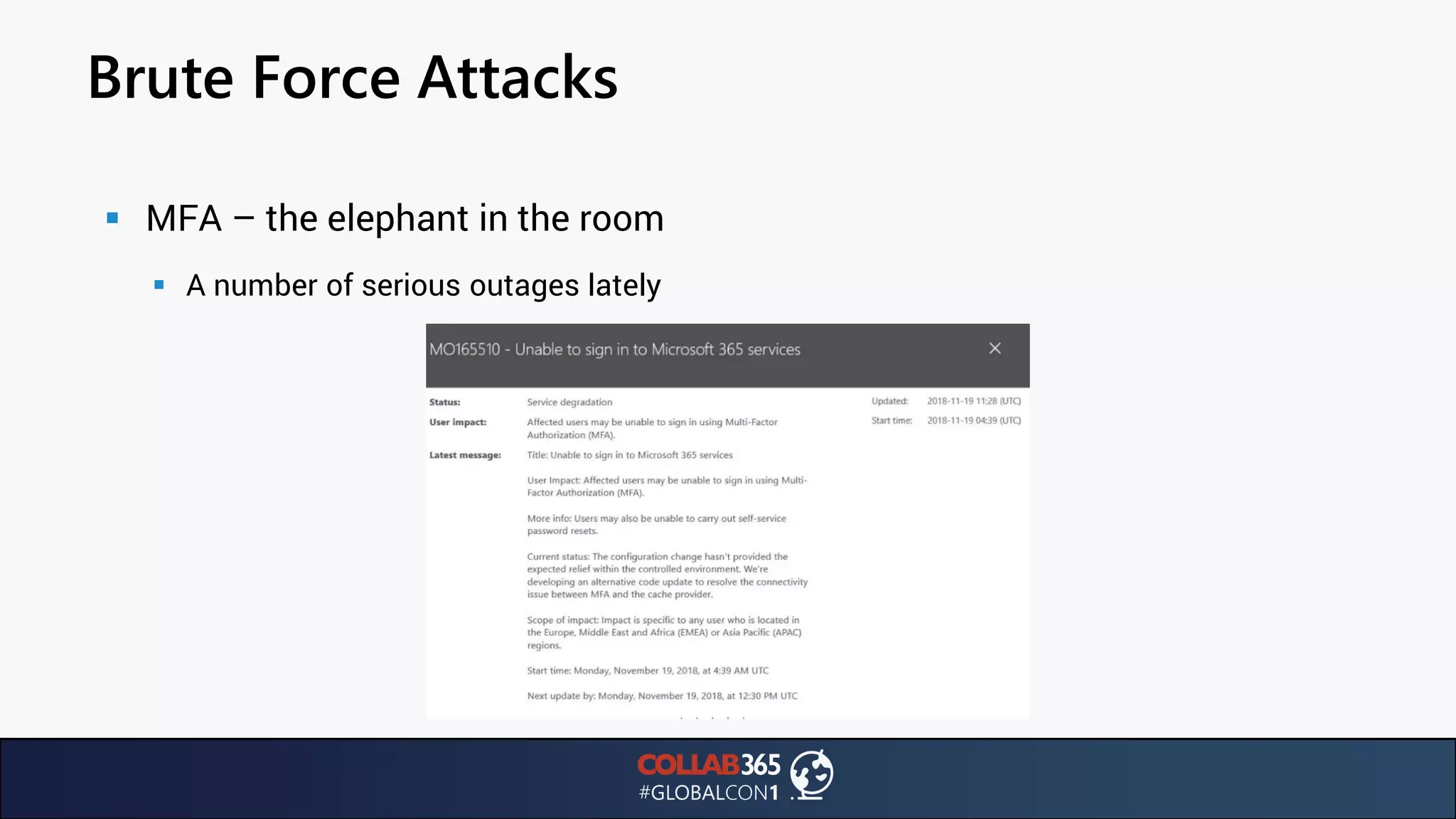
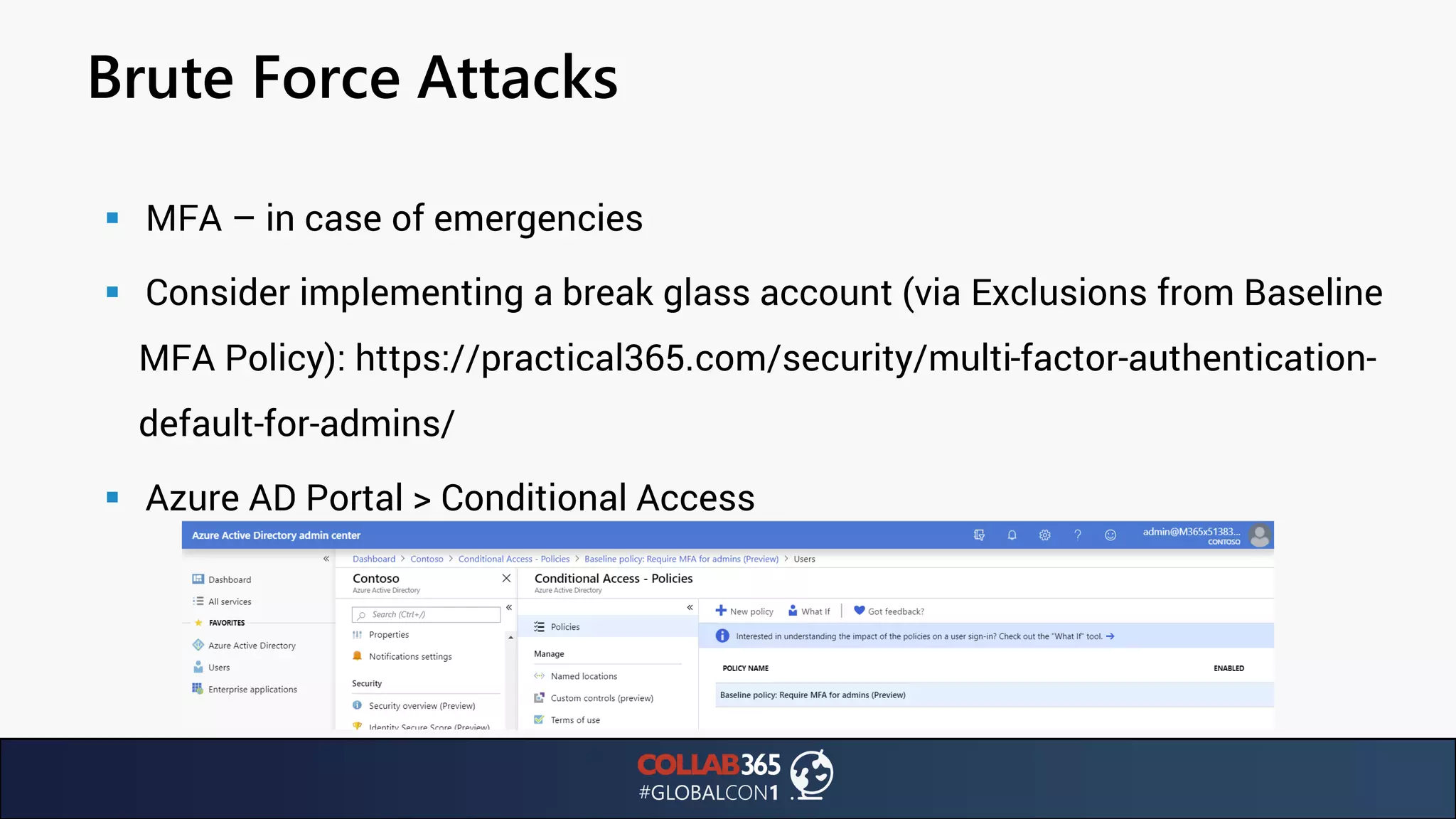
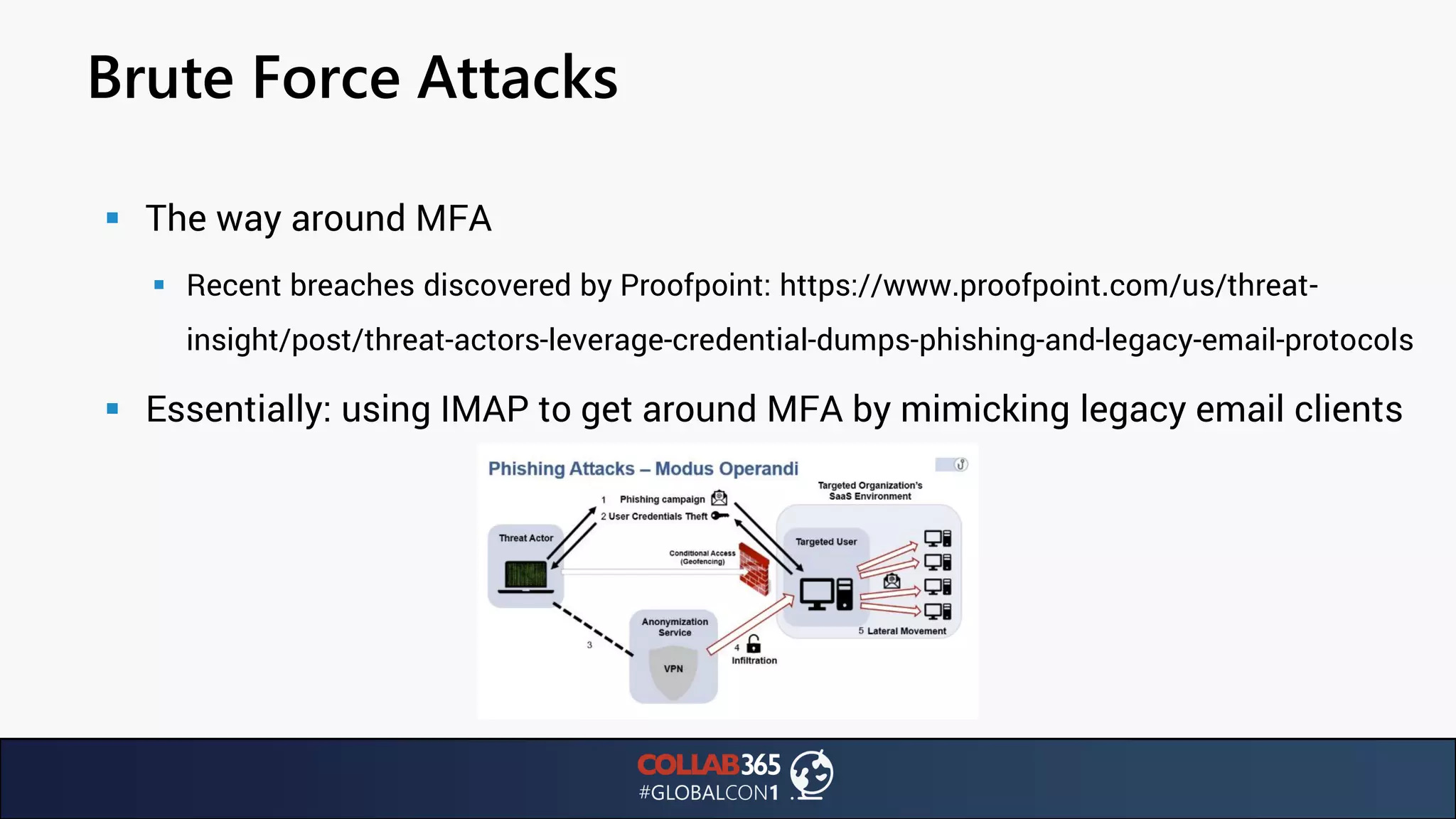
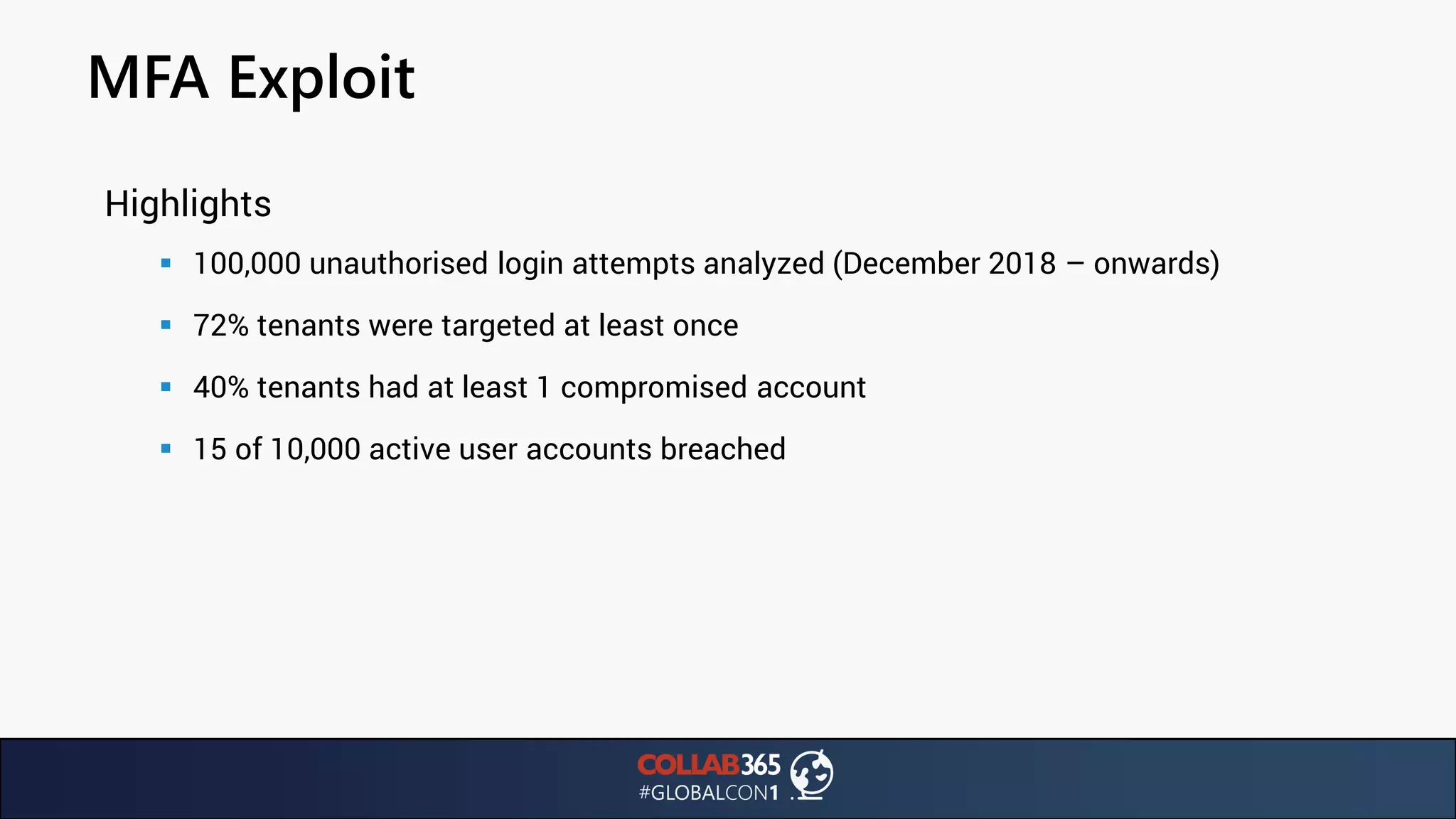
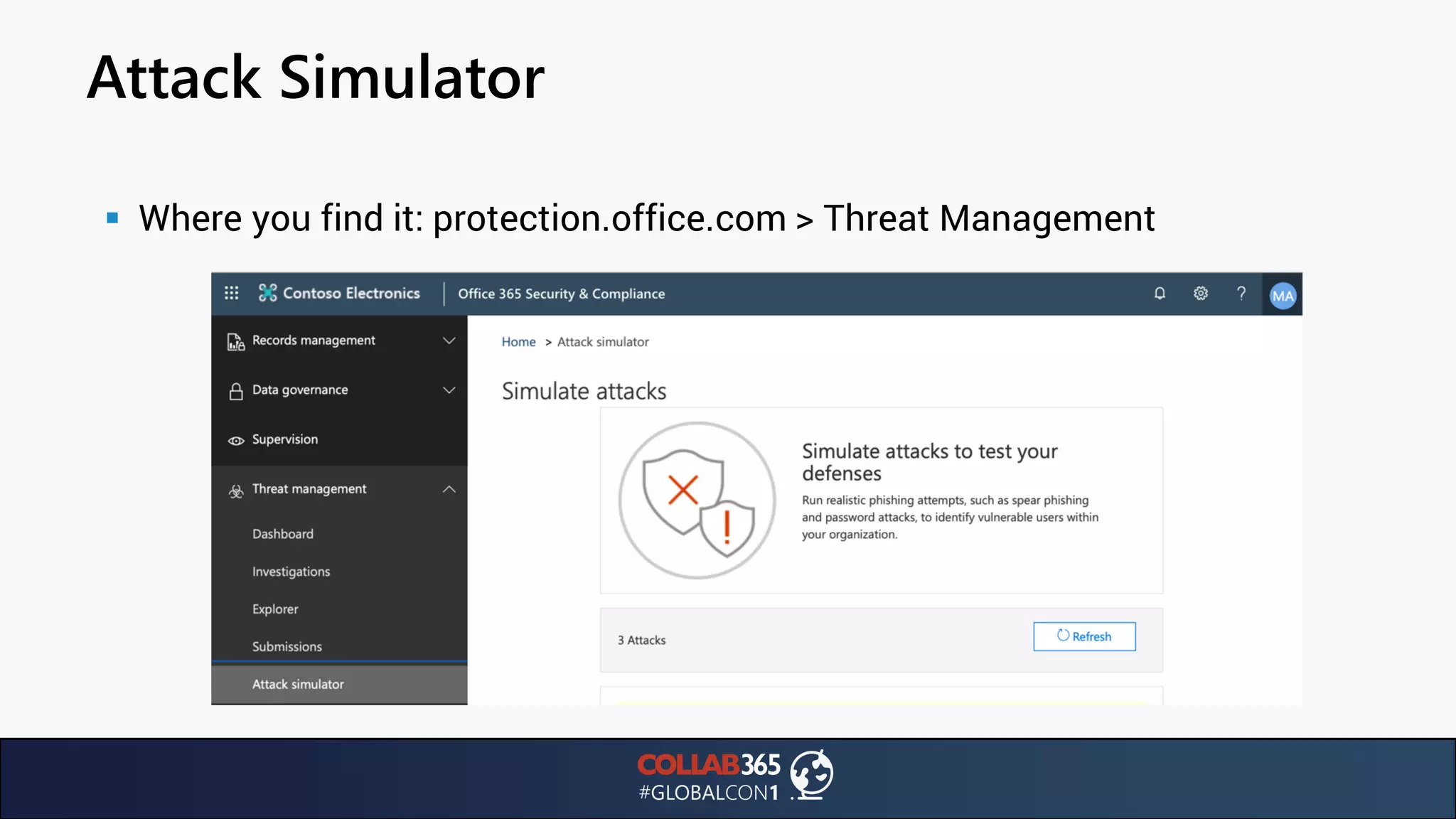
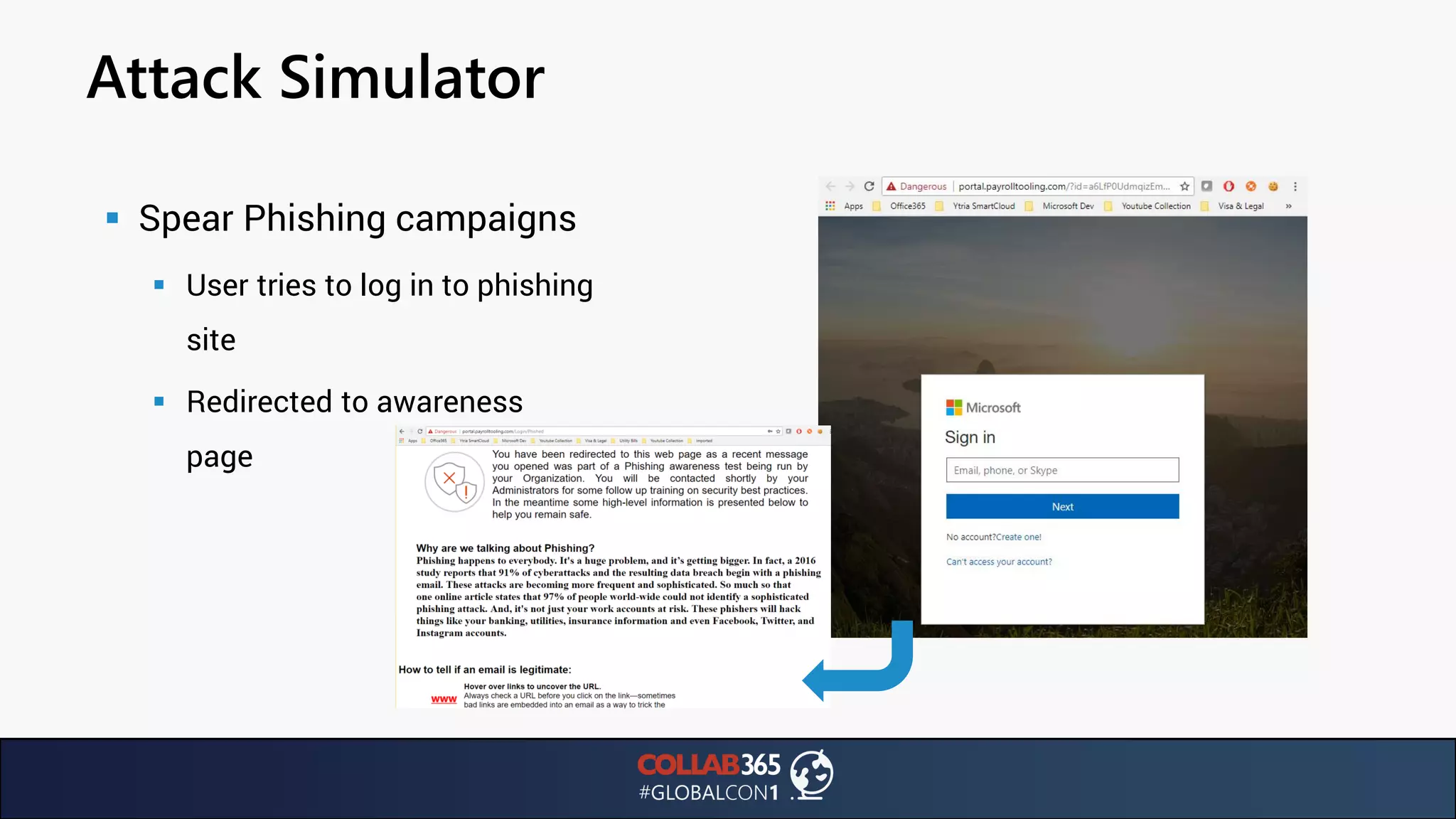
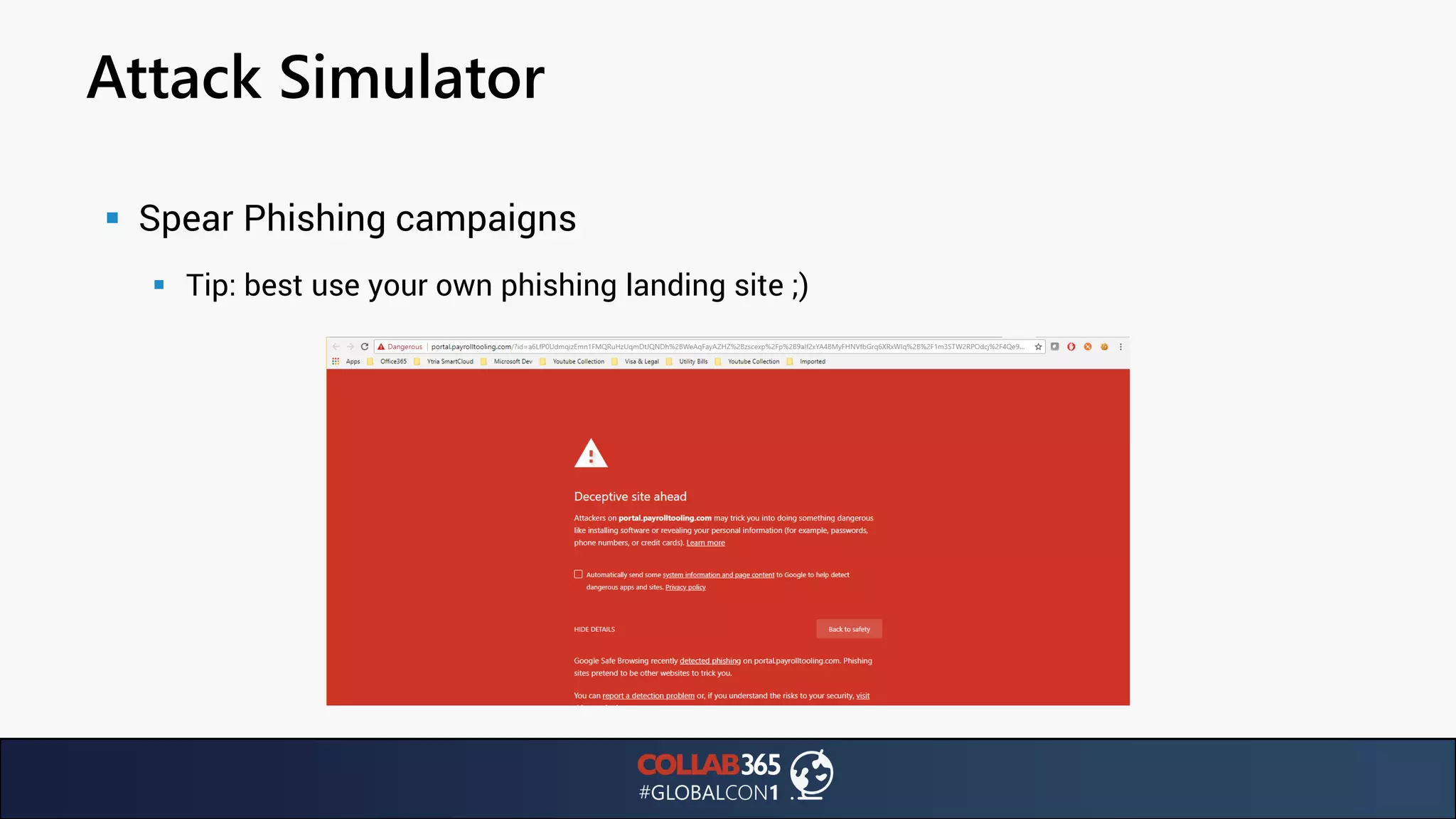
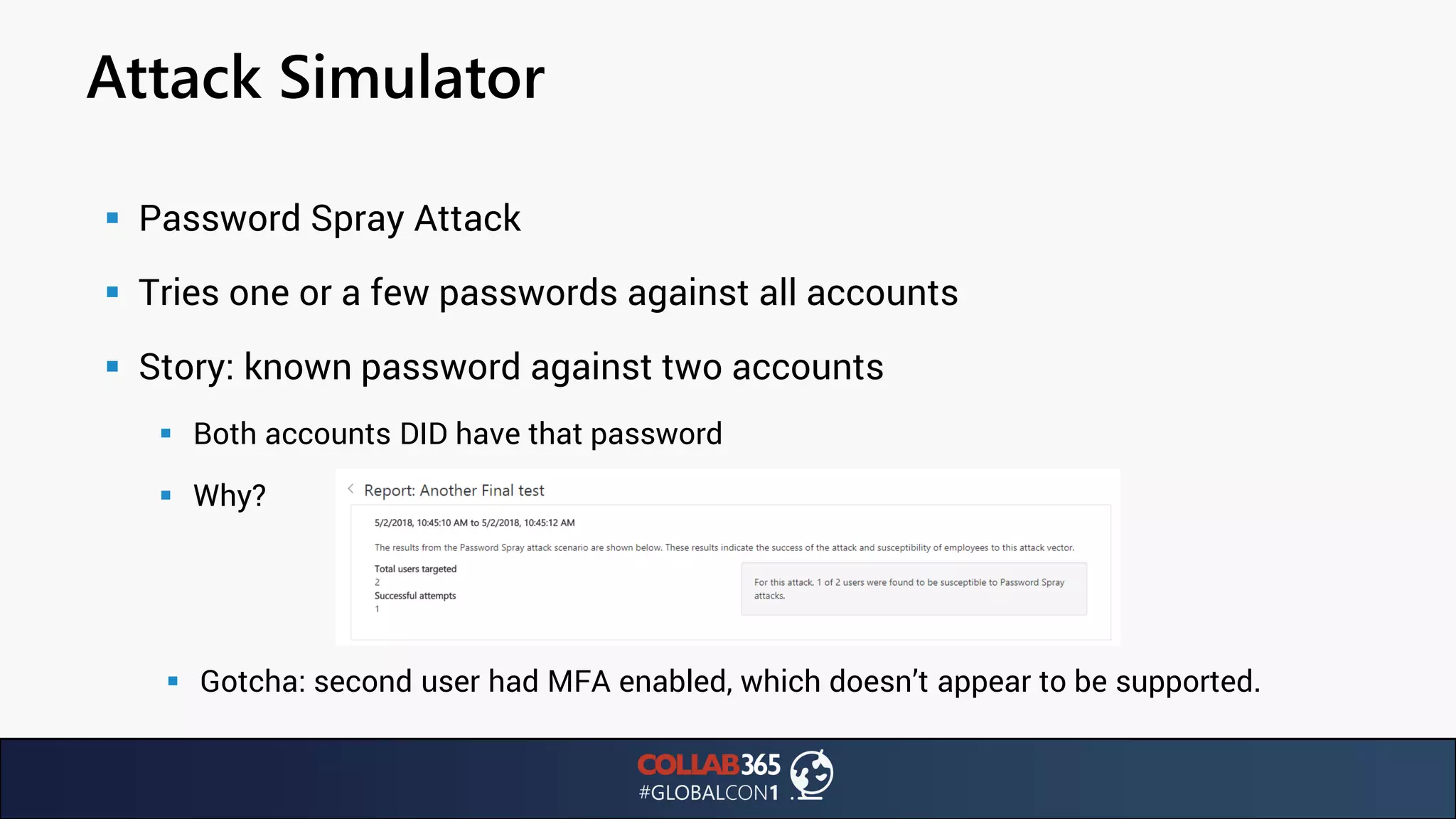
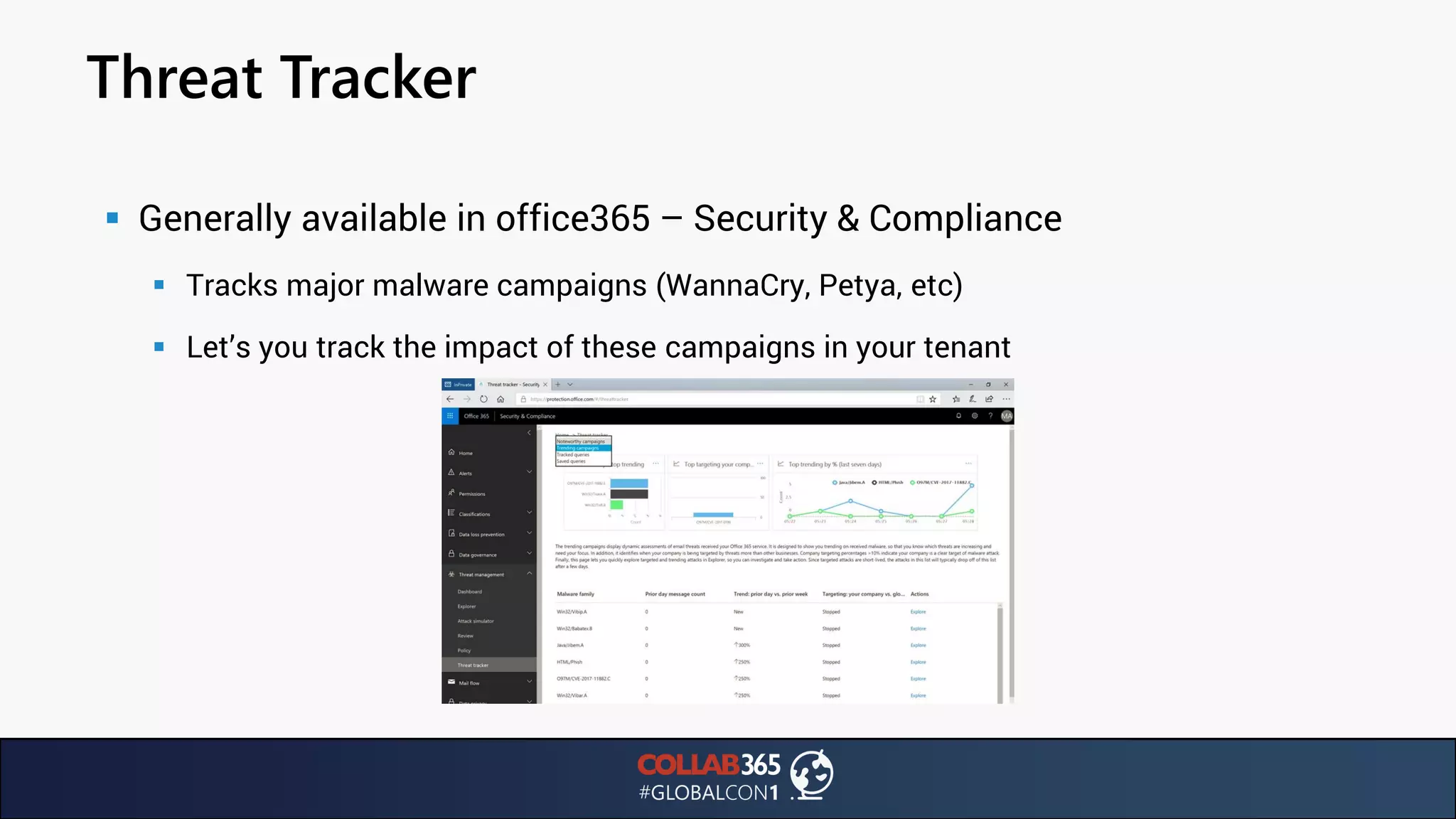
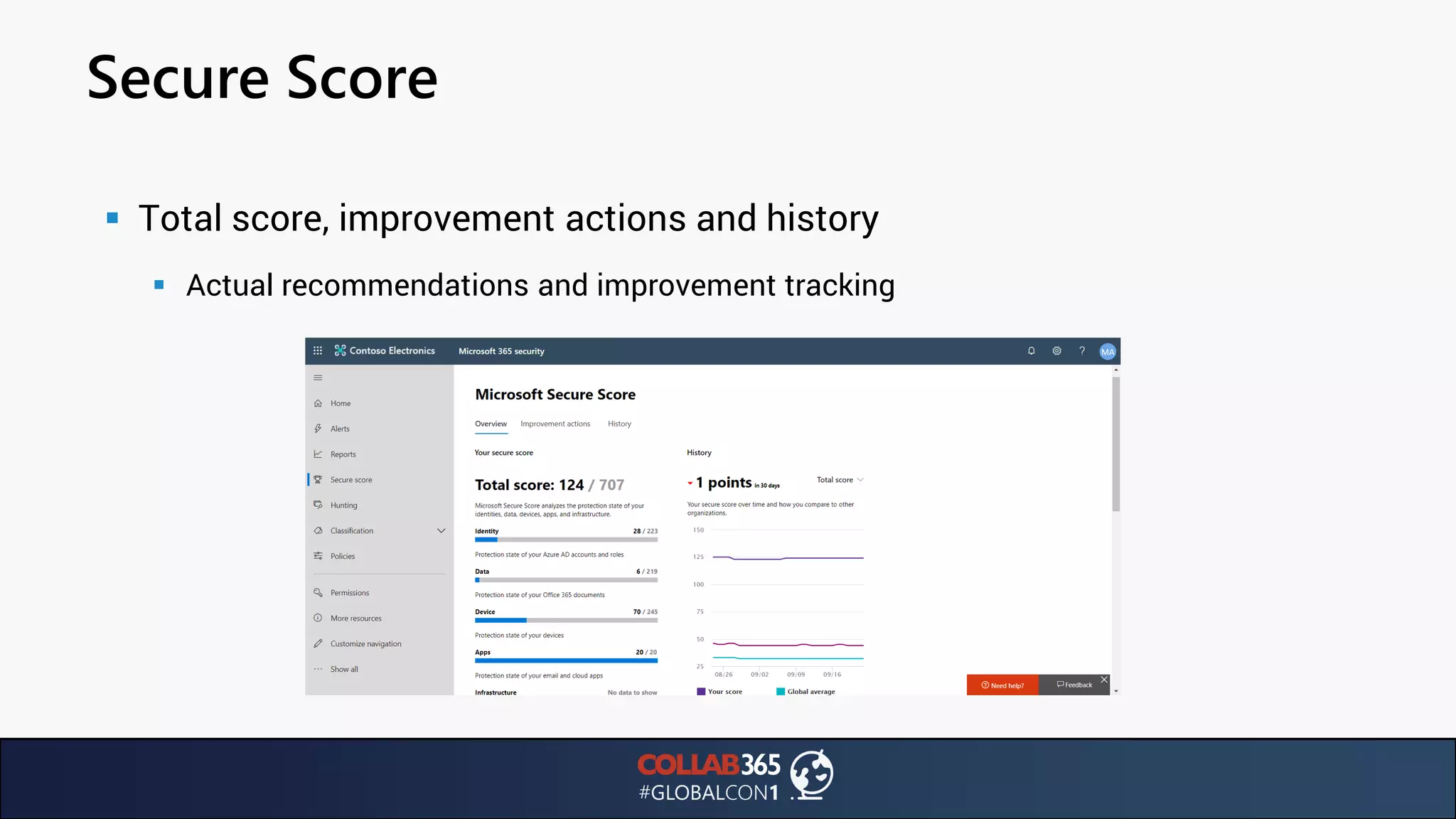
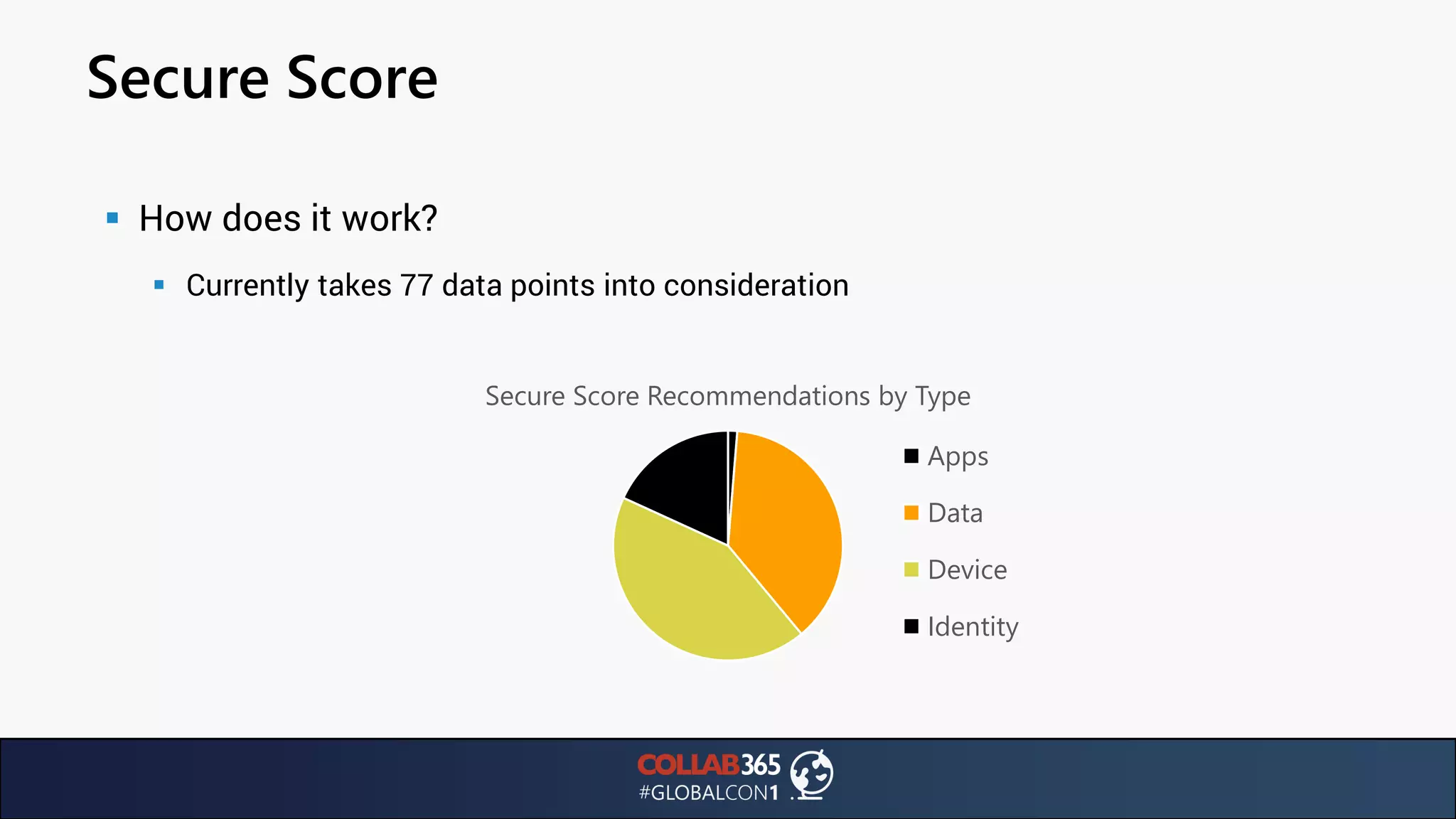
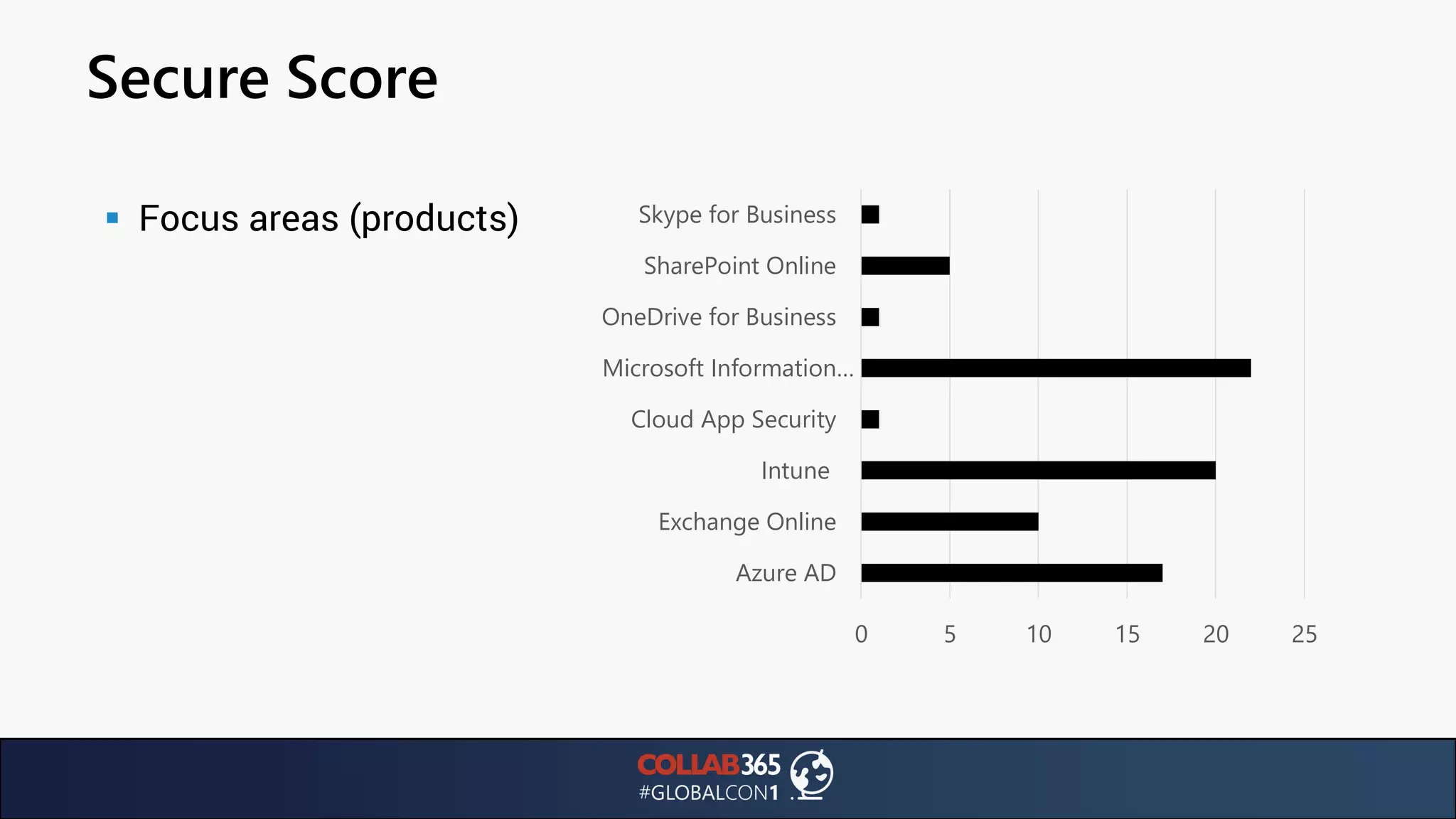
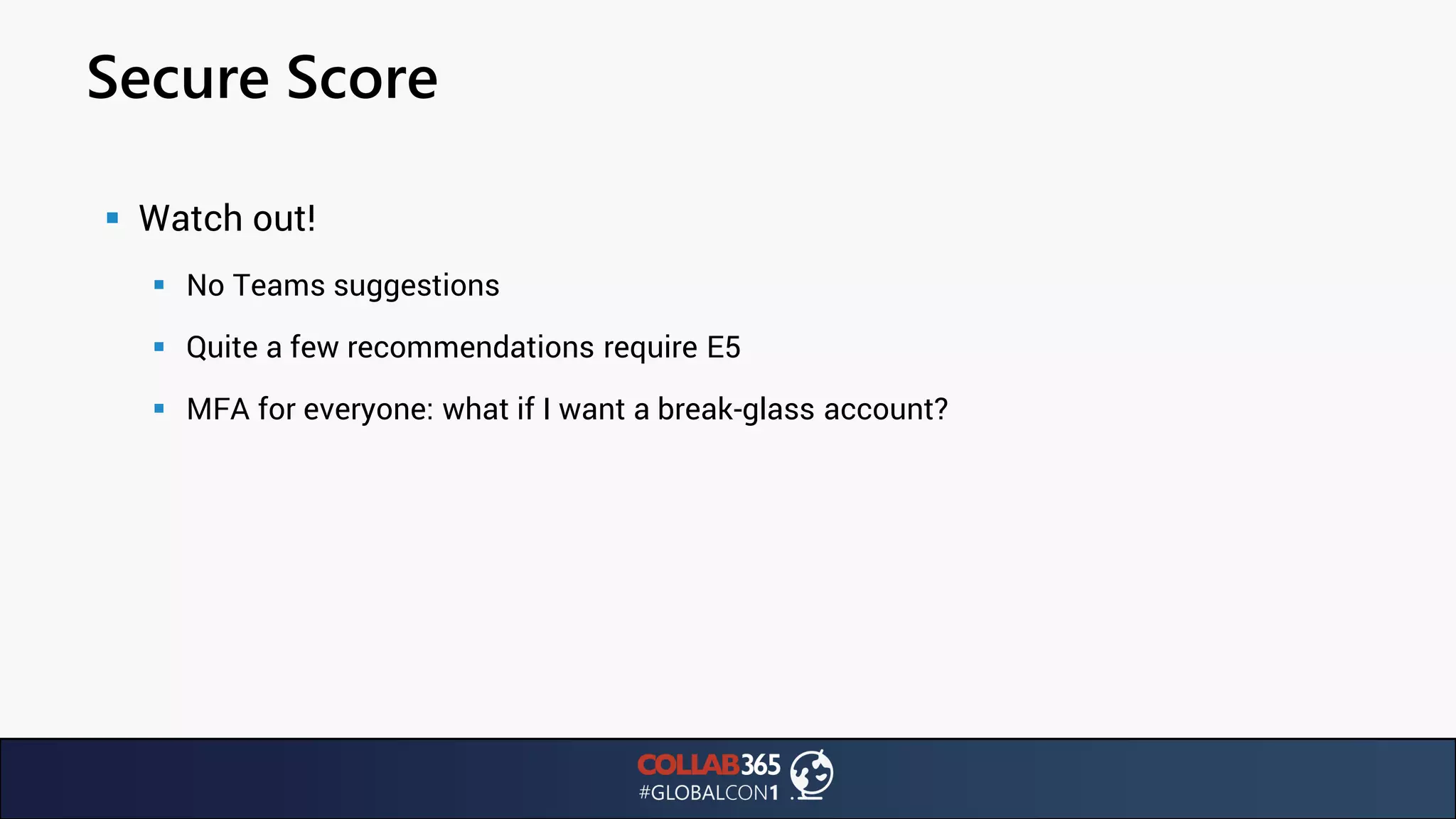
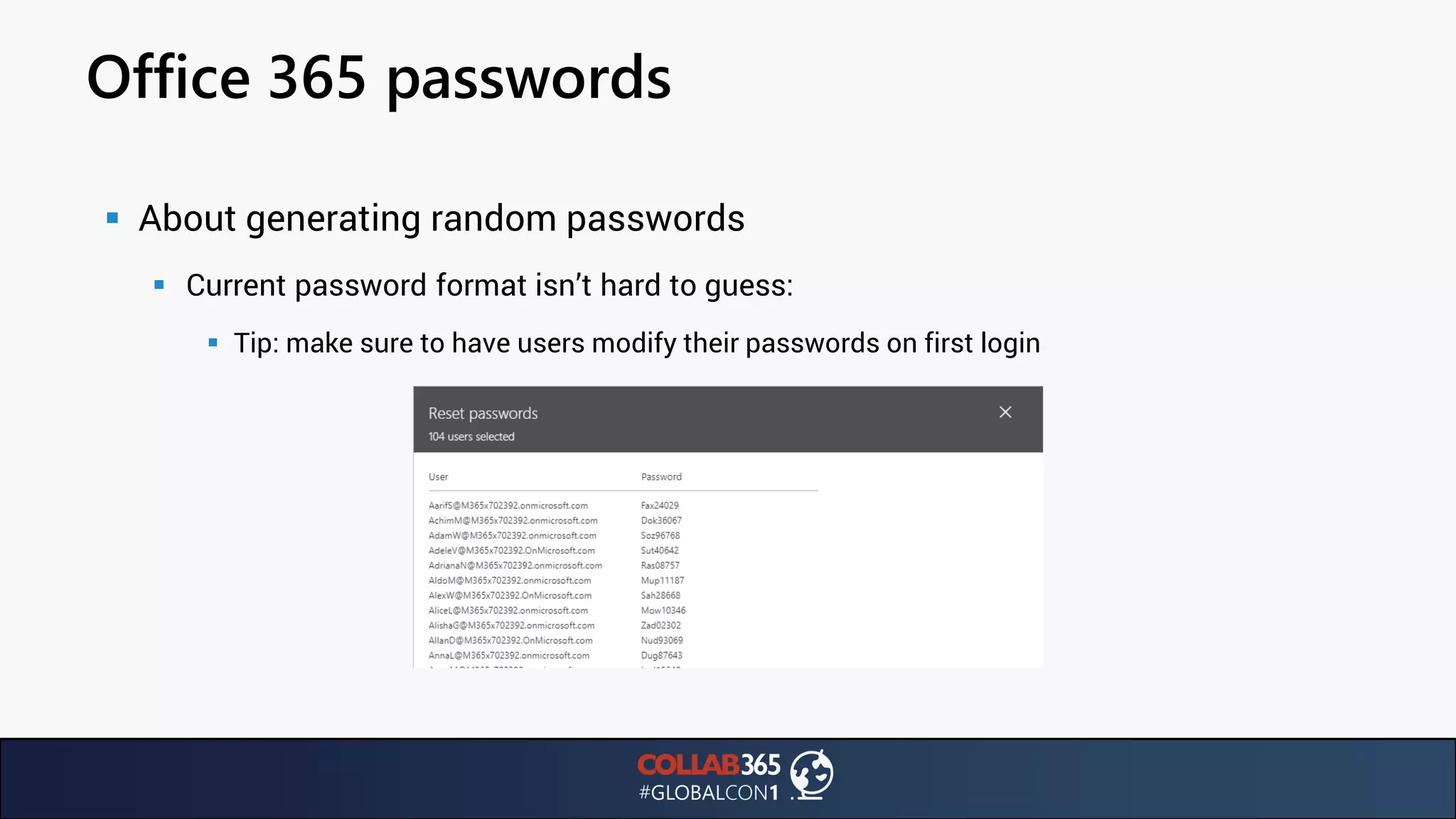
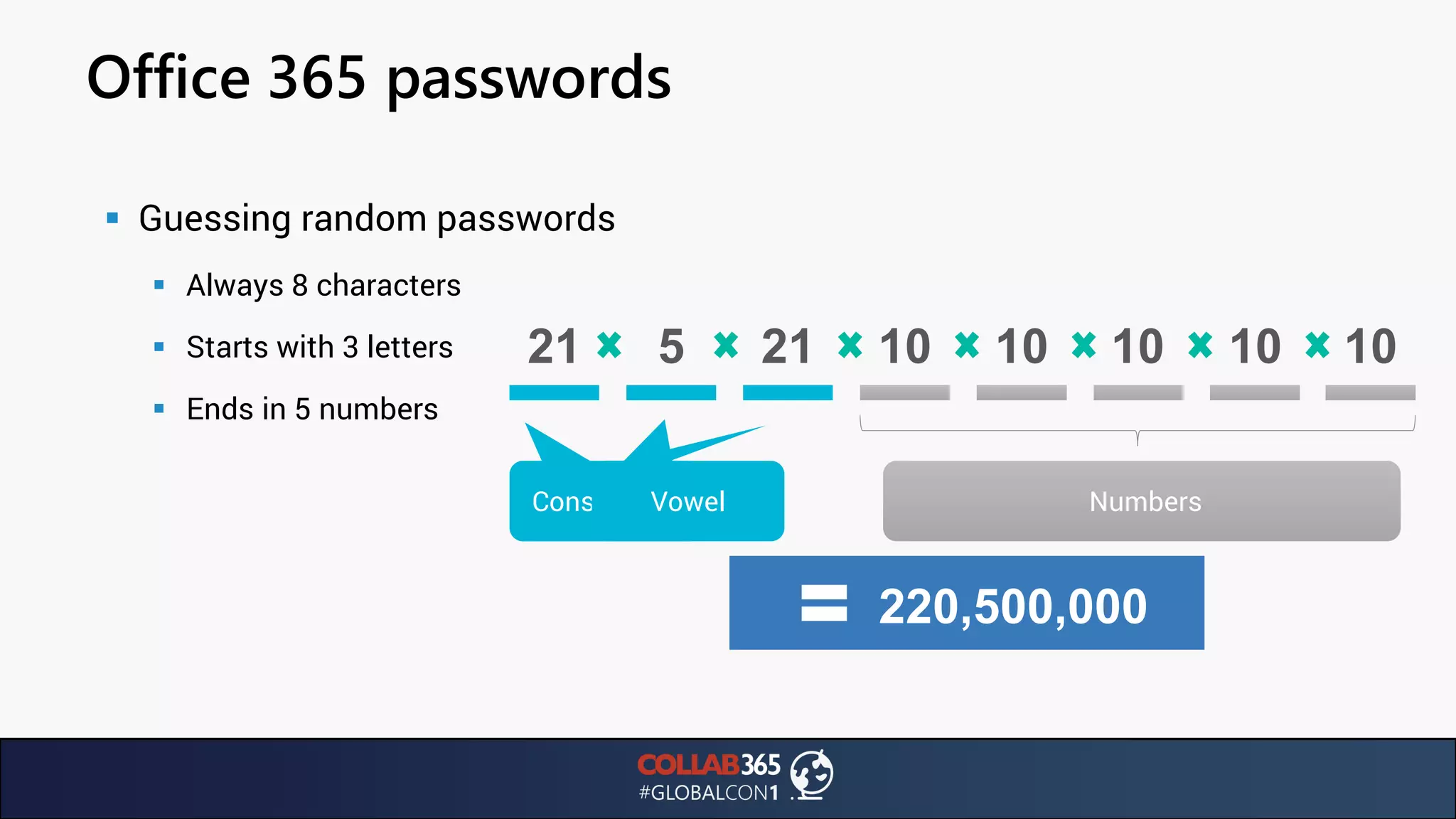
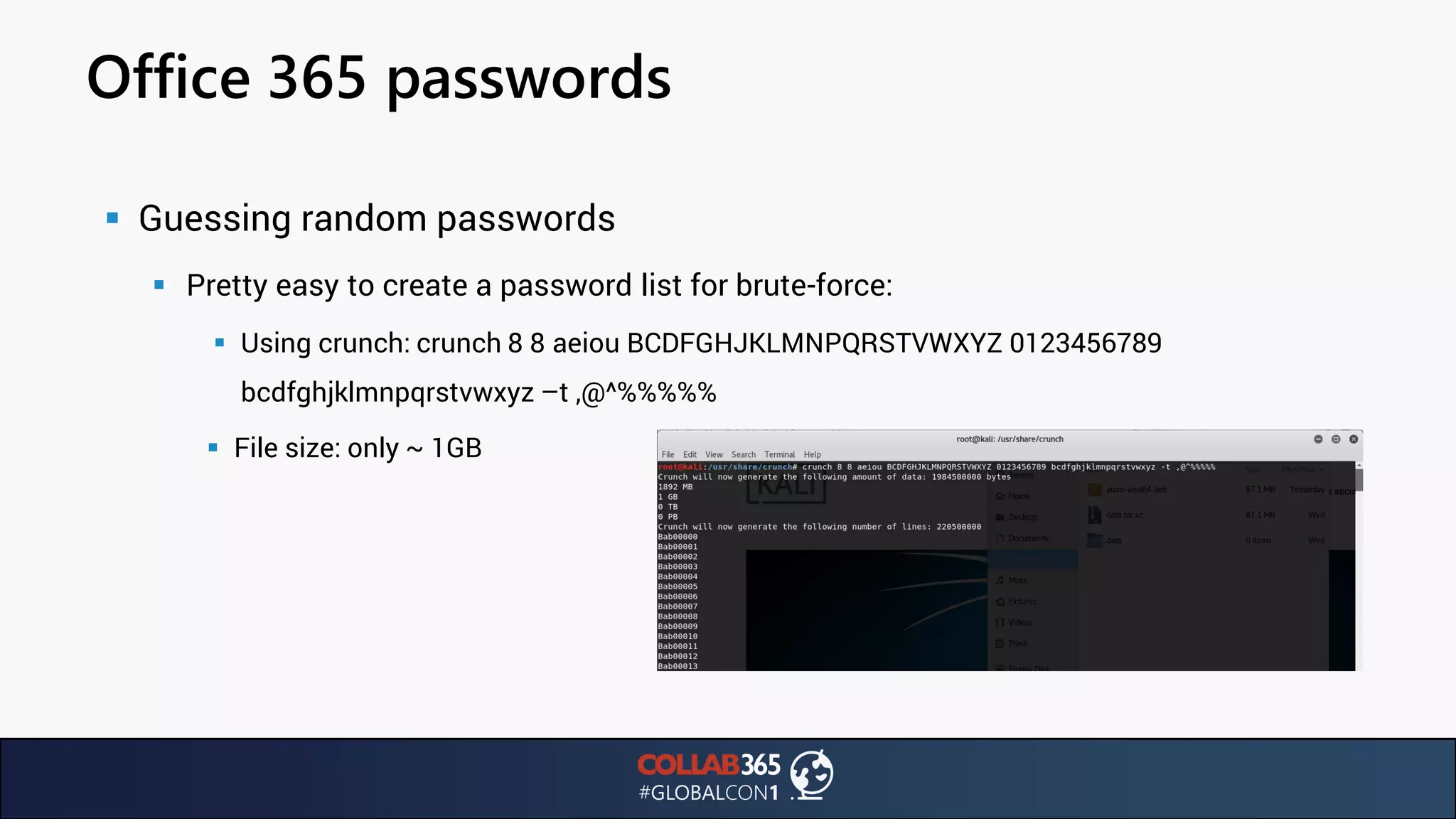
The document presents insights from a talk by Ben Menesi on threats faced by Office 365 from a hacker's perspective, focusing on issues like ransomware, email security, and multi-factor authentication. It discusses various statistics regarding cyber attacks, the effectiveness of cloud security compared to on-premises solutions, and specific vulnerabilities such as phishing and credential stuffing. The document also emphasizes the importance of educating users, employing multi-factor authentication, and monitoring applications to mitigate security risks.