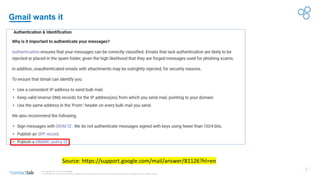
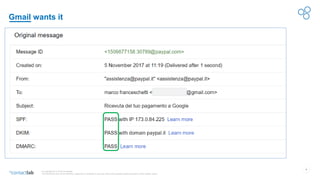
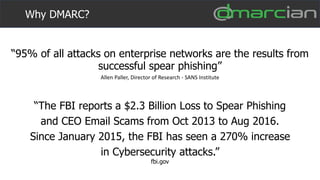
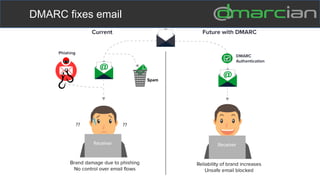
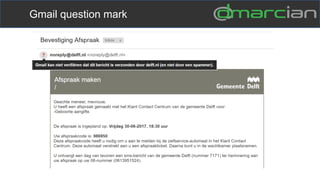
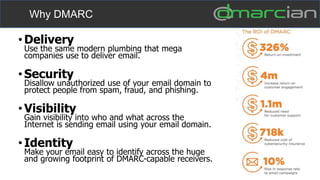
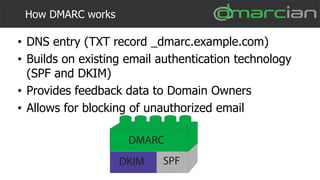
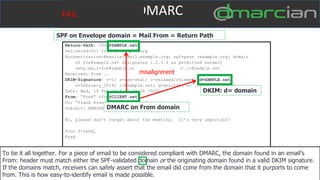
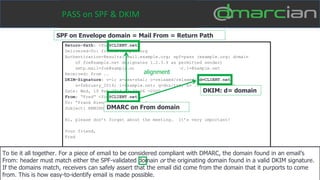
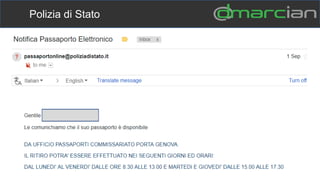
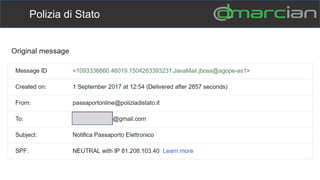
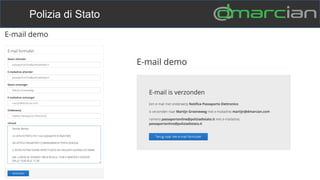
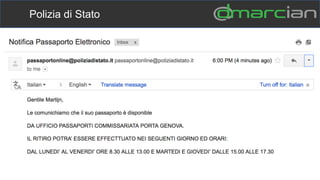
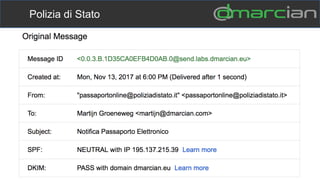
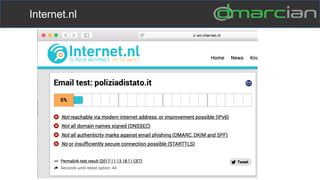
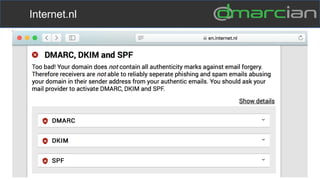
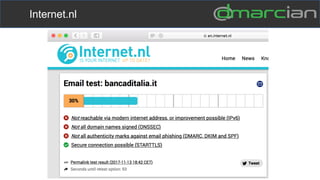
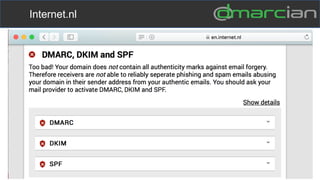
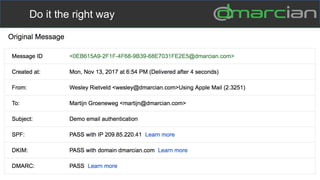
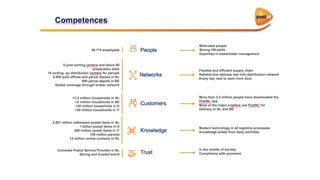
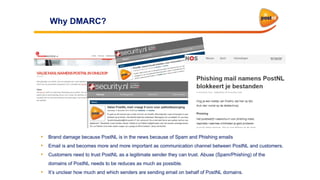
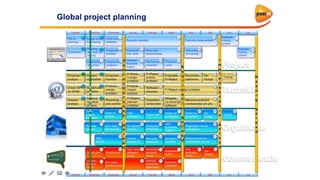
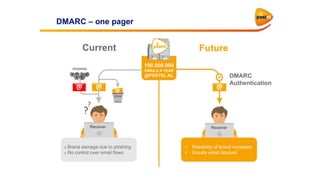
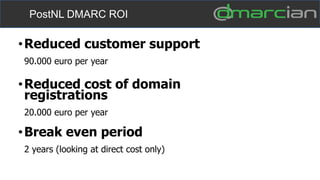
This document discusses the importance of DMARC (Domain-based Message Authentication, Reporting & Conformance) for email marketers, outlining how it enhances email security by preventing unauthorized use of domains and improving email deliverability. It highlights the role of authentication methods such as SPF and DKIM in securing emails, as well as the benefits of implementing DMARC policies. The document also emphasizes the financial and reputational risks associated with phishing attacks and provides insights into the workings and advantages of DMARC for organizations.