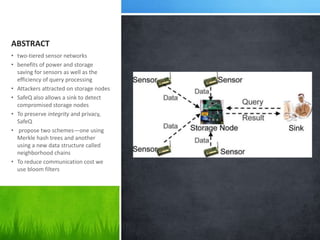
The document discusses a protocol called SafeQ for preserving privacy and integrity of range queries in two-tiered sensor networks, highlighting its benefits in power, storage efficiency, and query processing. It proposes two schemes using Merkle hash trees and neighborhood chains to ensure that storage nodes cannot obtain or manipulate sensitive data. Furthermore, SafeQ enables the sink to detect compromised storage nodes, thus enhancing overall security in hostile environments.