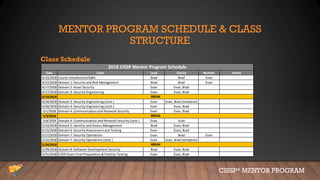
This document provides an overview of the CISSP Mentor Program session #1. It introduces Evan Francen and Brad Nigh, who lead the program. It discusses the severe talent shortage problem in cybersecurity, noting projections of millions of unfilled jobs by 2021 and factors contributing to this problem. It also outlines the agenda, schedule, and structure for the mentor program classes, which will cover CISSP domains and preparation for the exam.