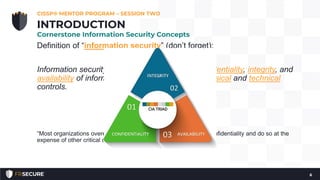
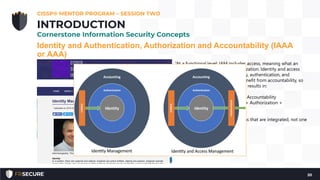
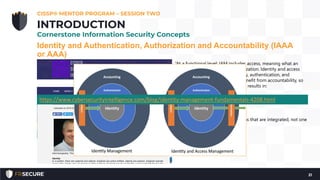
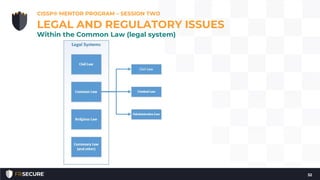
This document summarizes the second session of a CISSP mentor program held on April 10, 2019. The session covered several topics related to CISSP Domain 1 including security concepts like confidentiality, integrity, and availability. It defined key terms like risk, annualized loss expectancy, and return on investment. It also discussed identity and access management concepts such as identity, authentication, authorization, and accountability. The session aimed to help students understand and memorize these foundational information security principles.