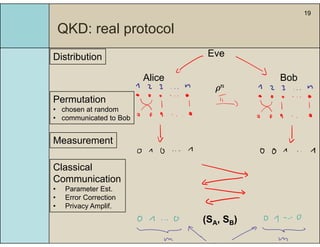
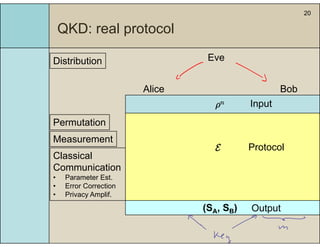
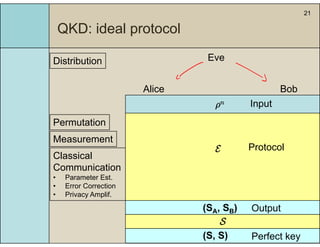
1) The document presents a technique for analyzing the security of real quantum key distribution (QKD) protocols by comparing them to an ideal protocol.
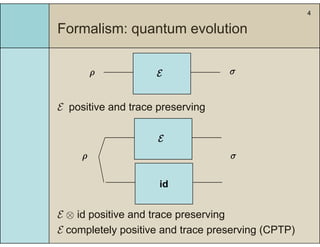
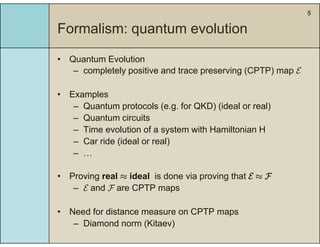
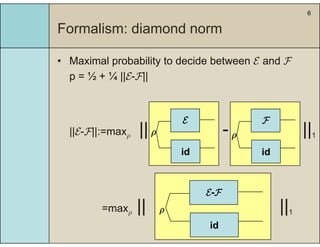
2) It introduces a formalism using completely positive and trace preserving maps and the diamond norm to measure the distance between real and ideal processes.
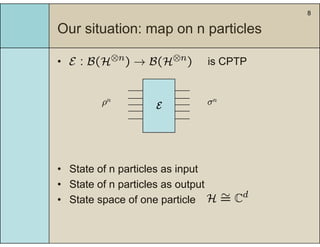
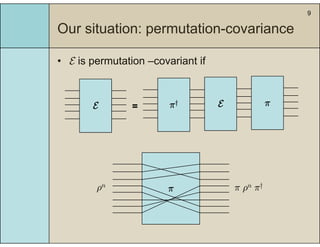
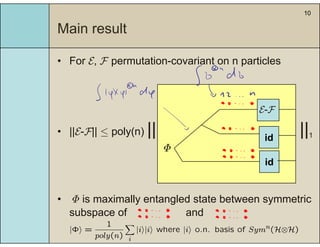
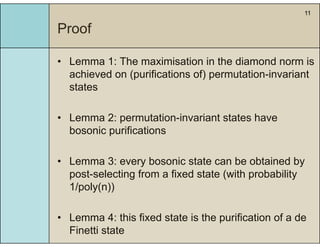
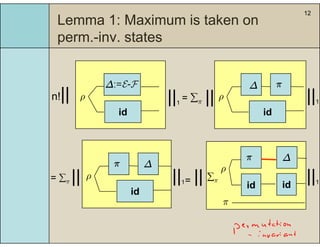
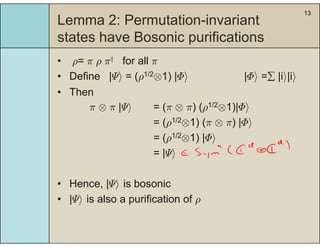
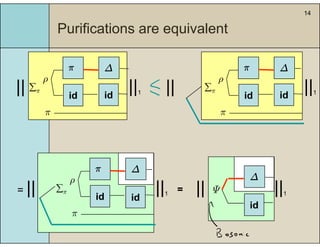
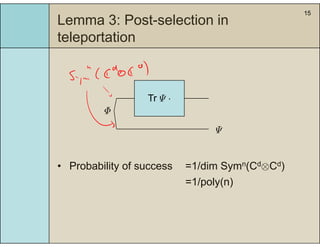
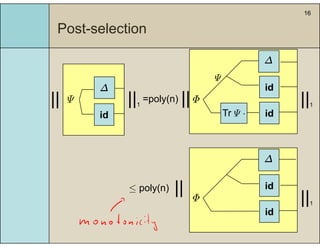
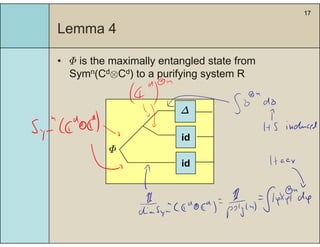
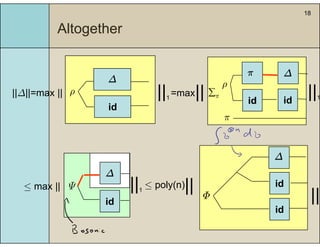
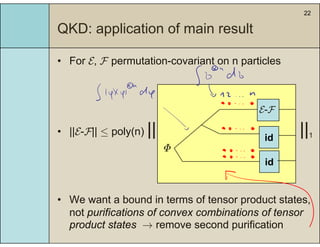
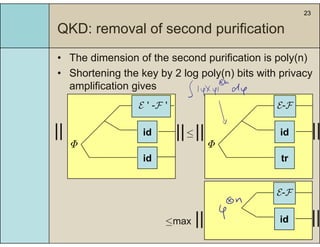
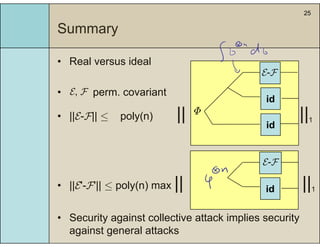
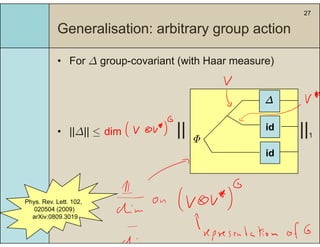
3) The main result is that for quantum evolutions that are permutation covariant, the diamond norm between them is bounded by a polynomial in the number of particles, when compared to evolutions corresponding to maximally entangled states.
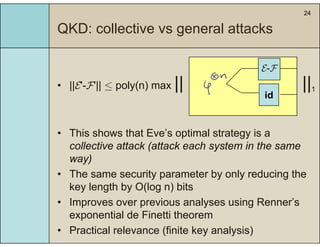
4) This bound allows proving the security of QKD protocols against general attacks by showing they are secure against collective attacks, improving on previous analyses that relied on an exponential de Finetti theorem.