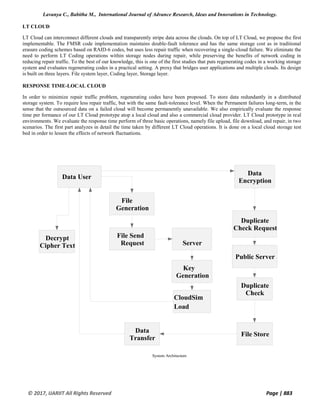
This document discusses an optimized report recovery system under LT-based cloud memory, focusing on improving document recovery delay in distributed storage. It emphasizes the use of fountain codes, Luby transformation (LT) codes, and presents a novel approach for multi-cloud storage that balances recovery time and successful decoding. The proposed system, LT Cloud, aims to enhance data repair efficiency while providing fault tolerance and minimizing bandwidth during recovery processes.