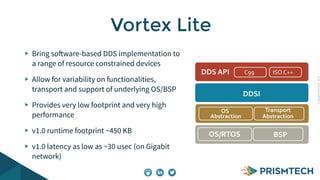
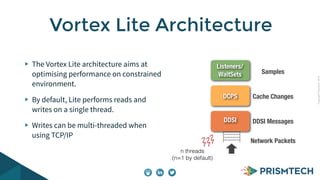
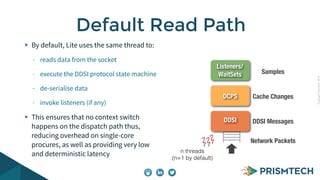
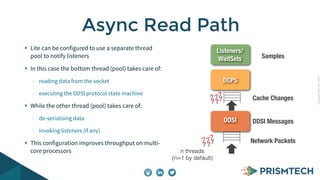
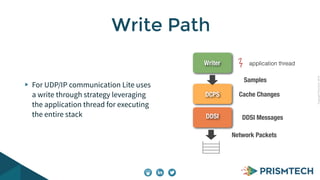
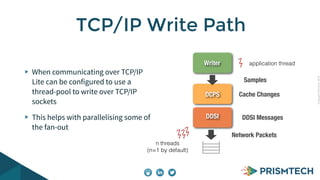
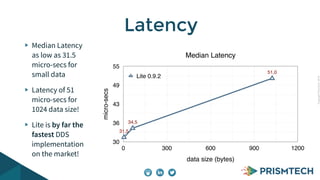
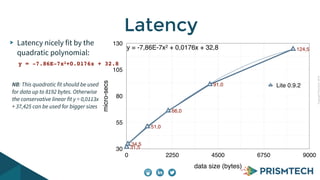
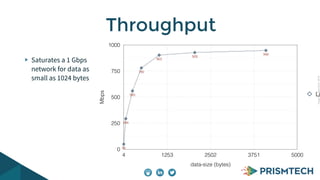
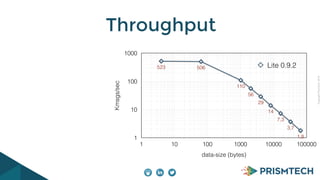
Vortex Lite is a lightweight implementation of the DDS standard that is optimized for resource-constrained devices. It has a small runtime footprint of around 450KB and provides low latency of 30 microseconds and high throughput by utilizing efficient single-threaded and multi-threaded designs. Vortex Lite can also connect to cloud services by enabling TCP/IP and configuring peers to Vortex Cloud addresses.












![CopyrightPrismTech,2014
Reading Data
#include "generated/Test.h"
int main (int argc, char ** argv) {
dds_entity_t ppant;
dds_entity_t topic;
dds_entity_t reader;
dds_sample_info_t info;
void * samples[1];
/* Initialize DDS */
dds_init (argc, argv);
/* Create participant */
dds_participant_create (&ppant,
DDS_DOMAIN_DEFAULT,
NULL, NULL);
/* Create topic */
dds_topic_create (ppant, &topic,
&Test_Topic_desc,
"TestTopic",
NULL, NULL, 0);
/* Create writer with QoS */
dds_reader_create (ppant, &reader,
topic, NULL, NULL, 0);
while (true) {
/* Wait for valid sample then print and exit */
ret = dds_read (reader, samples, 1, &info, 0);
if (ret > 0 && info.valid_data)
{
printf ("Test Sample (%d, %d)n",
sample.d1, sample.d2);
break;
}
dds_sleepfor (DDS_SECS (1));
}
/* Clean up */
dds_entity_delete (ppant);
dds_fini ();
}](https://image.slidesharecdn.com/2015-150128022014-conversion-gate02/85/Introducing-Vortex-Lite-38-320.jpg)
![CopyrightPrismTech,2014
Listener Declaration
static void data_available_handler (dds_entity_t reader) {
int ret;
const uint32_t max = 1;
dds_sample_info_t info[max];
void * samples[max];
Test_Topic sample;
uint32_t mask = 0;
samples[0] = &sample;
/* Set type of samples required. */
mask = DDS_ALIVE_INSTANCE_STATE;
/* Read samples. */
dds_read (reader, samples, max, info, mask);
printf ("Data Received ...n");
printf ("Sample (%d, %d)n", sample.d1, sample.d2);
}](https://image.slidesharecdn.com/2015-150128022014-conversion-gate02/85/Introducing-Vortex-Lite-39-320.jpg)