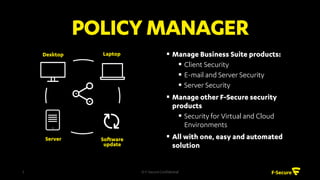
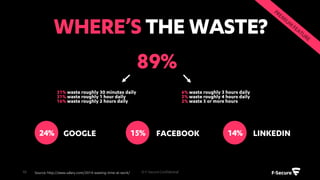
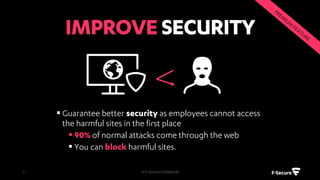
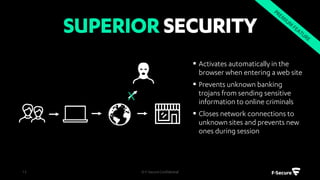
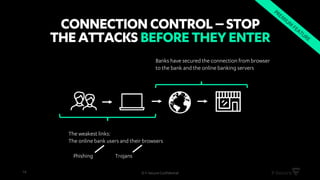
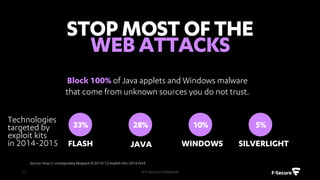
The document outlines the features and benefits of F-Secure's centralized policy management solution for IT security, which offers comprehensive management of various security applications and policies. Key functionalities include automated patch management, USB device control, web content filtering, and advanced protection against malware and botnets. Additionally, it emphasizes scalability, ease of use, and the ability to enhance overall business productivity through proactive security measures.