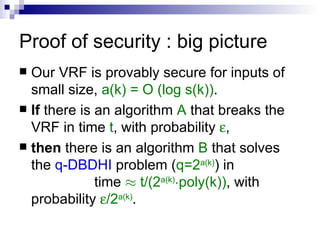
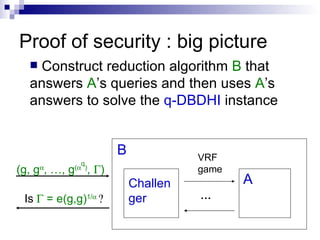
The document describes a construction of a verifiable random function (VRF) that improves upon previous work. It directly constructs a VRF without using Goldreich-Levin hardcore bits, allows inputs of arbitrary size without encoding, and has proofs and keys consisting of a constant number of group elements. The security of the VRF relies on complexity assumptions in bilinear groups and it finds applications like non-interactive lotteries and compact e-cash schemes.

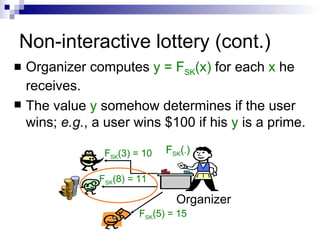
![Non-interactive lottery [MR02] Lottery organizer has a secret function F SK ( . ) Each participant chooses a lottery ticket x and sends it to the organizer Organizer F SK ( . ) x 1 = 3 x 2 = 8 x 3 = 5](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-3-320.jpg)

![Verifiable Random Function What we need is a verifiable random function (VRF) [MRV99] On input x , owner of secret key SK can compute y = F SK (x) together with proof SK (x). The output y looks random. Yet the proof SK (x) convinces every verifier that y is correct with respect to public key.](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-6-320.jpg)
![Previous work VRFs have many useful applications (non-interactive lottery, rZK, e-cash, verifiable transaction escrow). However, they are not very well studied [MRV99, Lys02, Dod03] Prior constructions are not very efficient. ](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-7-320.jpg)
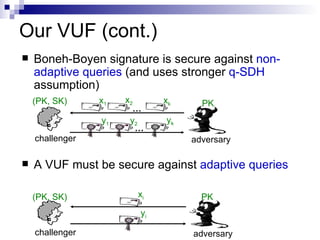
![Previous work (cont.) Use an inefficient Goldreich-Levin hardcore bit [MRV99, Lys02] Construct a verifiable unpredictable function (VUF) , whose output is hard to guess but not necessarily random. Use Goldreich-Levin bit to convert a VUF into a VRF.](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-8-320.jpg)
![Previous work (cont.) Use an inefficient Goldreich-Levin hardcore bit [MRV99, Lys02] Inputs need to be encoded in a special way [MRV99, Lys02, Dod03] [MRV99]: inputs are first mapped into primes [Lys02, Dod03]: inputs are mapped to codewords of an error-correcting code](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-9-320.jpg)
![Previous work (cont.) Use an inefficient Goldreich-Levin hardcore bit [MRV99, Lys02] Inputs need to be encoded in a special way [MRV99, Lys02, Dod03] Proofs and keys are long [Lys02, Dod03] [Lys02, Dod03]: keys (PK, SK) and proofs SK (x) consist of O(|x|) group elements.](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-10-320.jpg)

![Bilinear groups G, G 1 : cyclic groups of prime order p An admissible bilinear map e: G £ G G 1 bilinear: 8 u,v 2 G and 8 x,y 2 Z e(u x , v y ) = e(u, v) xy non-degenerate: e(g, g) ≠ 1 efficiently computable Can construct such maps from Weil pairing on elliptic curves [JN01]](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-12-320.jpg)
![Compexity assumptions We make two assumptions: q-DHI assumption : given (g, g x , …, g (x q ) ), it is hard to compute g 1/x [MSK02] q-DBDHI assumption : given (g, g x , …, g (x q ) ), it is hard to distinguish e(g,g) 1/x from random [BB04] Hard = adversary running for s(k) steps is unlikely to succeed. Here, s(k)= (poly(k)) and s(k)=o(2 k ) .](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-13-320.jpg)
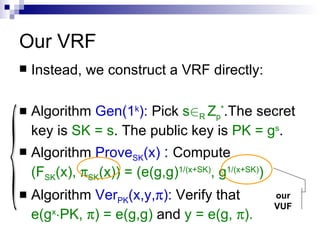
![Our VUF Starting point: Boneh-Boyen signature [BB04] Algorithm Gen(1 k ): Pick s 2 R Z p * .The secret key is SK = s . The public key is PK = g s . Algorithm Sign SK (x): To sign x , compute y = g 1/(x+SK) . Algorithm Ver PK (x, y): Check that e(y, g x ¢ PK) = e(g, g). {](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-14-320.jpg)




![Extending the input size (cont.) Alternatively, we can truncate basic VRF’s output to a(k)-1 bits and use [MRV99] tree construction: 0 a-1 y=F(0 a ) z=F(0 a-1 1) F(z0) F(z1) F(y0) F(y1) F(F(y1)1) F(F(y1)0) 0 1 0 1 0 1 0 1 VRF value for x = 011](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-24-320.jpg)
![Efficiency Suppose a(k) = 160 bits, the length of SHA-1 digests. We then have: Group size Length of proofs and keys 160 bits, elliptic group >3,200 bytes [Dod03], [Lys02] 14,383 bits, Z n * 280,000 bytes [MRV99] 1,000 bits, elliptic group 125 bytes Our VRF](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-25-320.jpg)
![Compact e-cash [CHL05] Offline anonymous e-cash scheme. A user can withdraw a wallet of 2 l coins from the bank and later spend them. In best known schemes, withdraw and spend operations take O(2 l ¢ k) time ( k is the security parameter). In EuroCrypt ’05, [CHL05] used our VRF to construct a scheme whose withdraw/spend operations take O(l+k) time.](https://image.slidesharecdn.com/pkc-100909225203-phpapp02/85/A-verifiable-random-function-with-short-proofs-and-keys-26-320.jpg)

