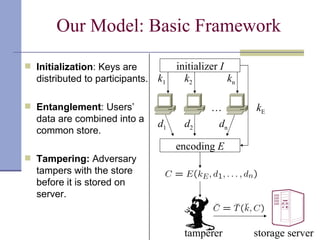
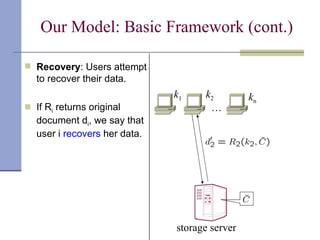
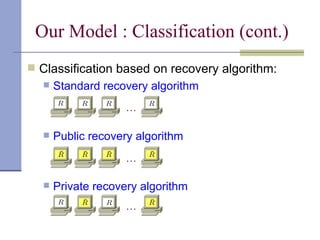
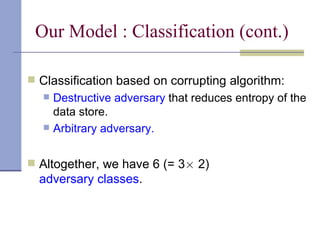
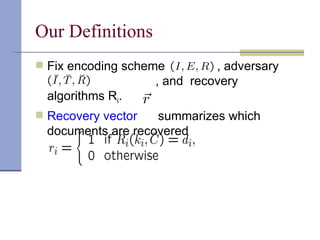
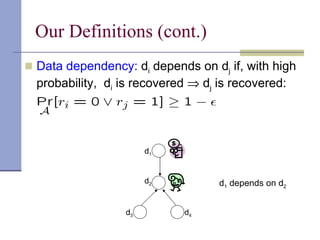
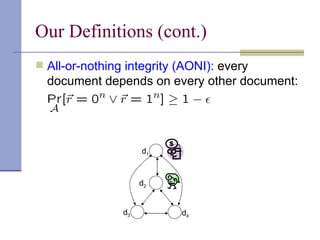
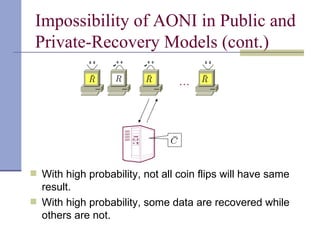
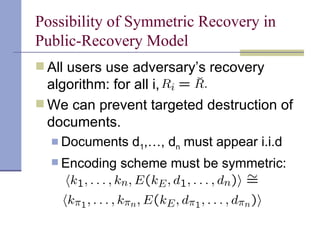
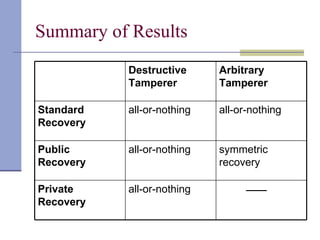
The document proposes a model for entangling users' data to protect remotely stored data from server corruption. It defines six adversary classes based on the recovery algorithm (standard, public, private) and corruption method (destructive, arbitrary). It shows all-or-nothing integrity is possible in the standard-recovery model by using message authentication codes, but not in public/private models as adversaries can modify the recovery algorithm. Symmetric recovery is possible in the public model if encoding is symmetric. All-or-nothing integrity is achievable against destructive adversaries by interpolating a polynomial of the data.

![Previous Work: Dagster [SW01] New Document Encrypt c randomly chosen blocks Pool of blocks Analysis: Deleting a typical document loss of O( c ) documents](https://image.slidesharecdn.com/esorics-100909225158-phpapp02/85/Towards-a-theory-of-data-entangelement-4-320.jpg)
![Previous Work: Tangler [WM01] (0, New Document) 2 randomly chosen blocks Pool of n blocks Analysis: Deleting a typical document loss of O ( (log n ) / n ) documents Interpolate degree-2 poly F() (x 1 ,F(x 1 )) (x 2 ,F(x 2 ))](https://image.slidesharecdn.com/esorics-100909225158-phpapp02/85/Towards-a-theory-of-data-entangelement-5-320.jpg)