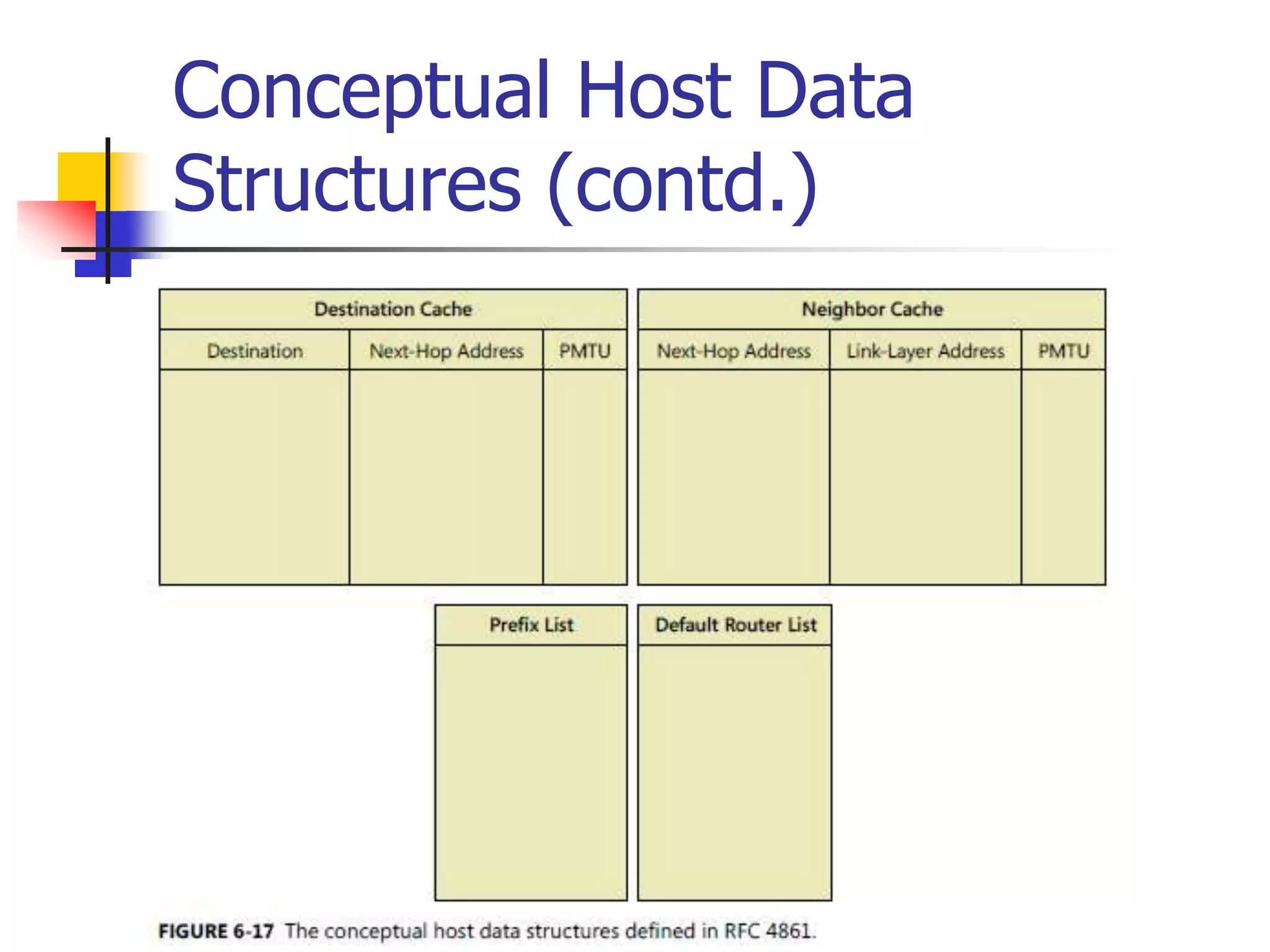
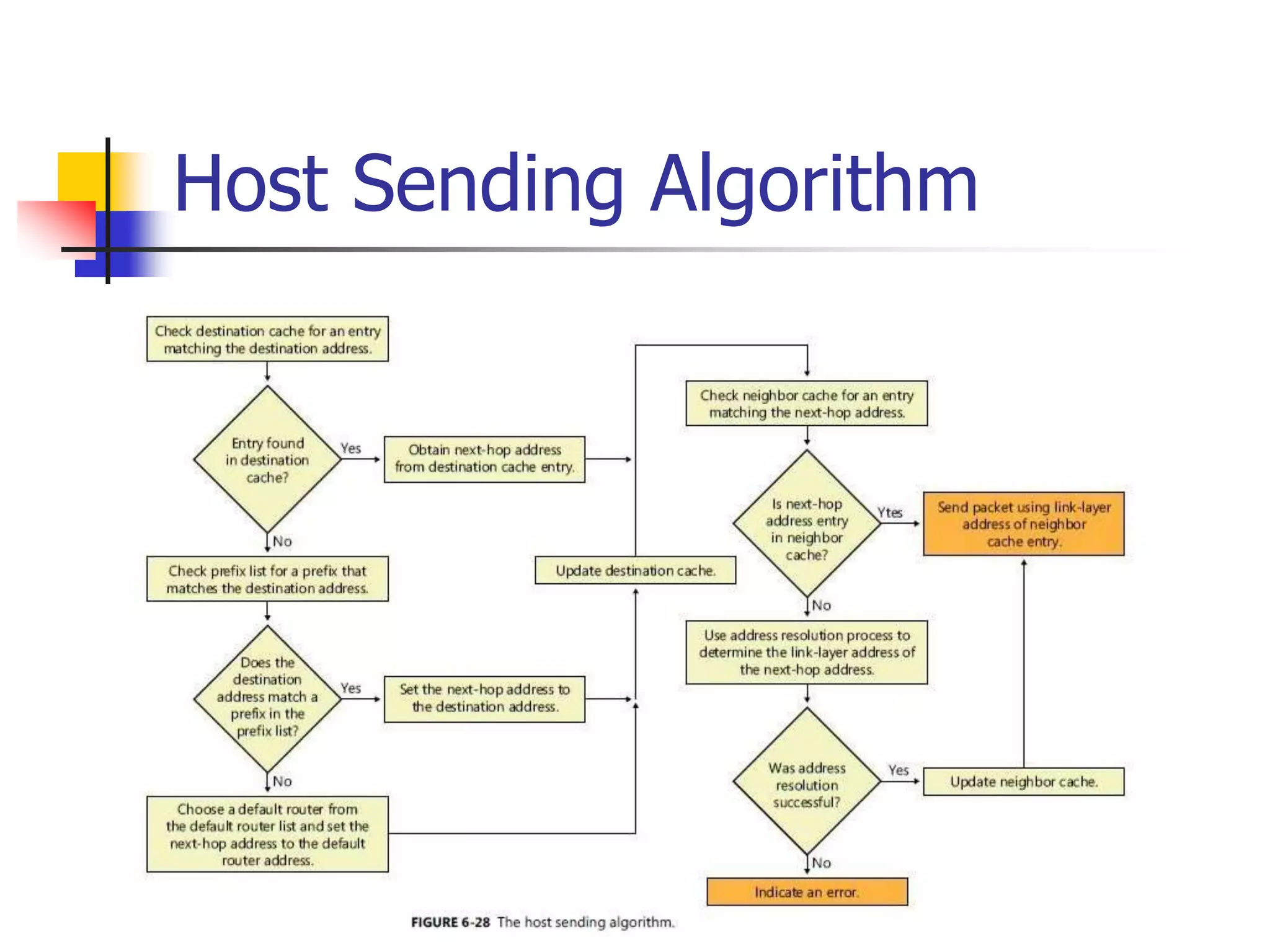
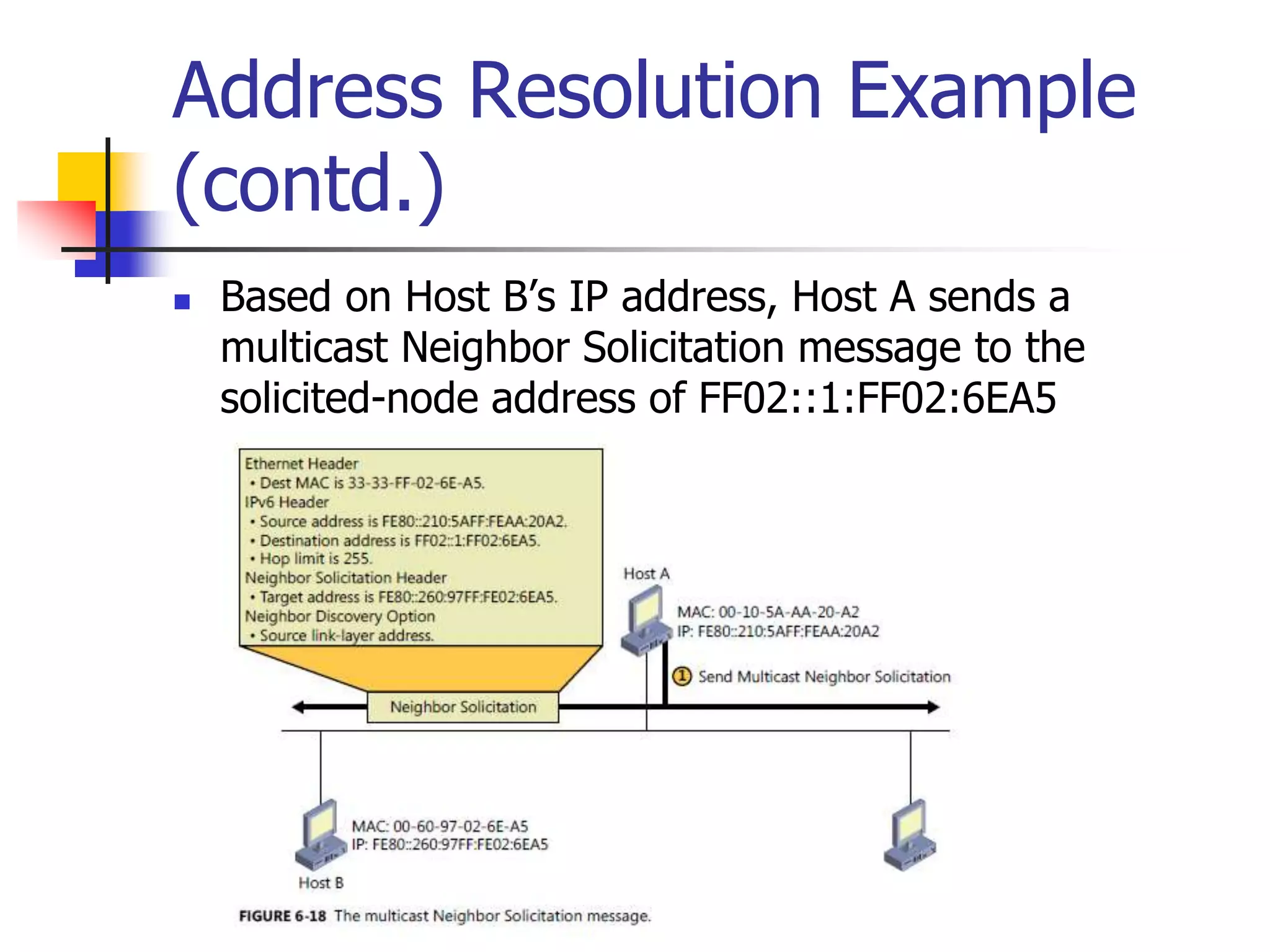
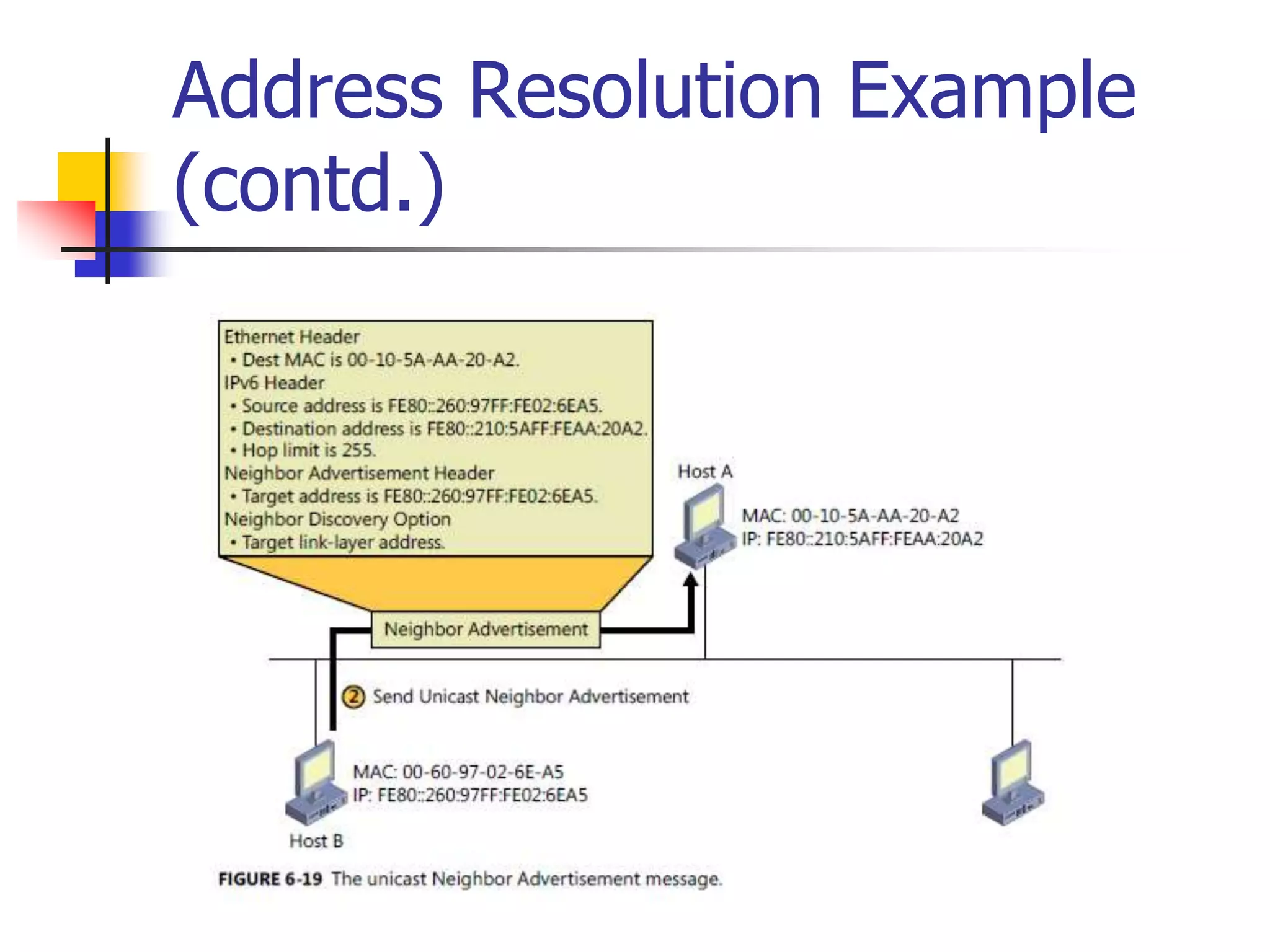
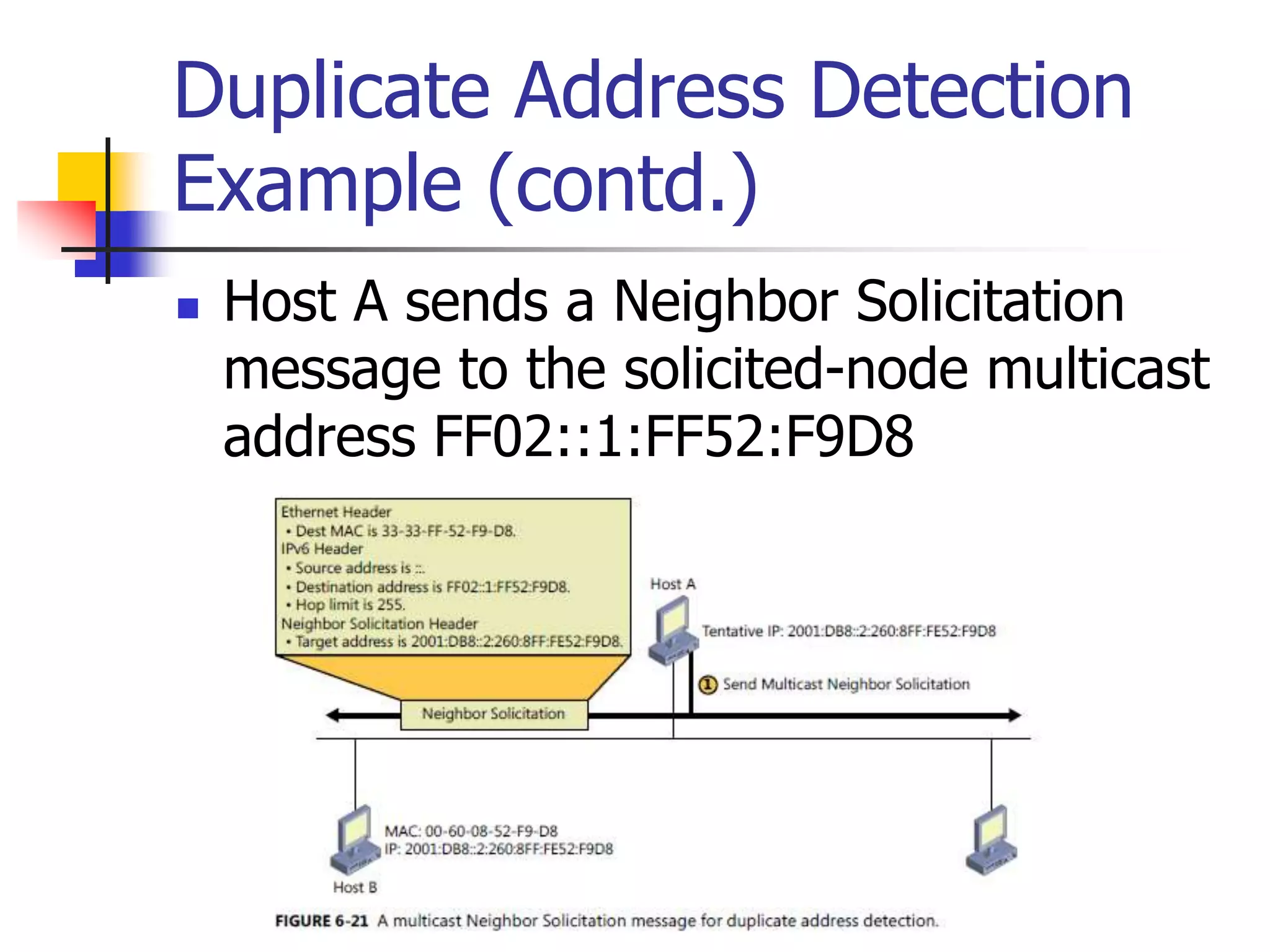
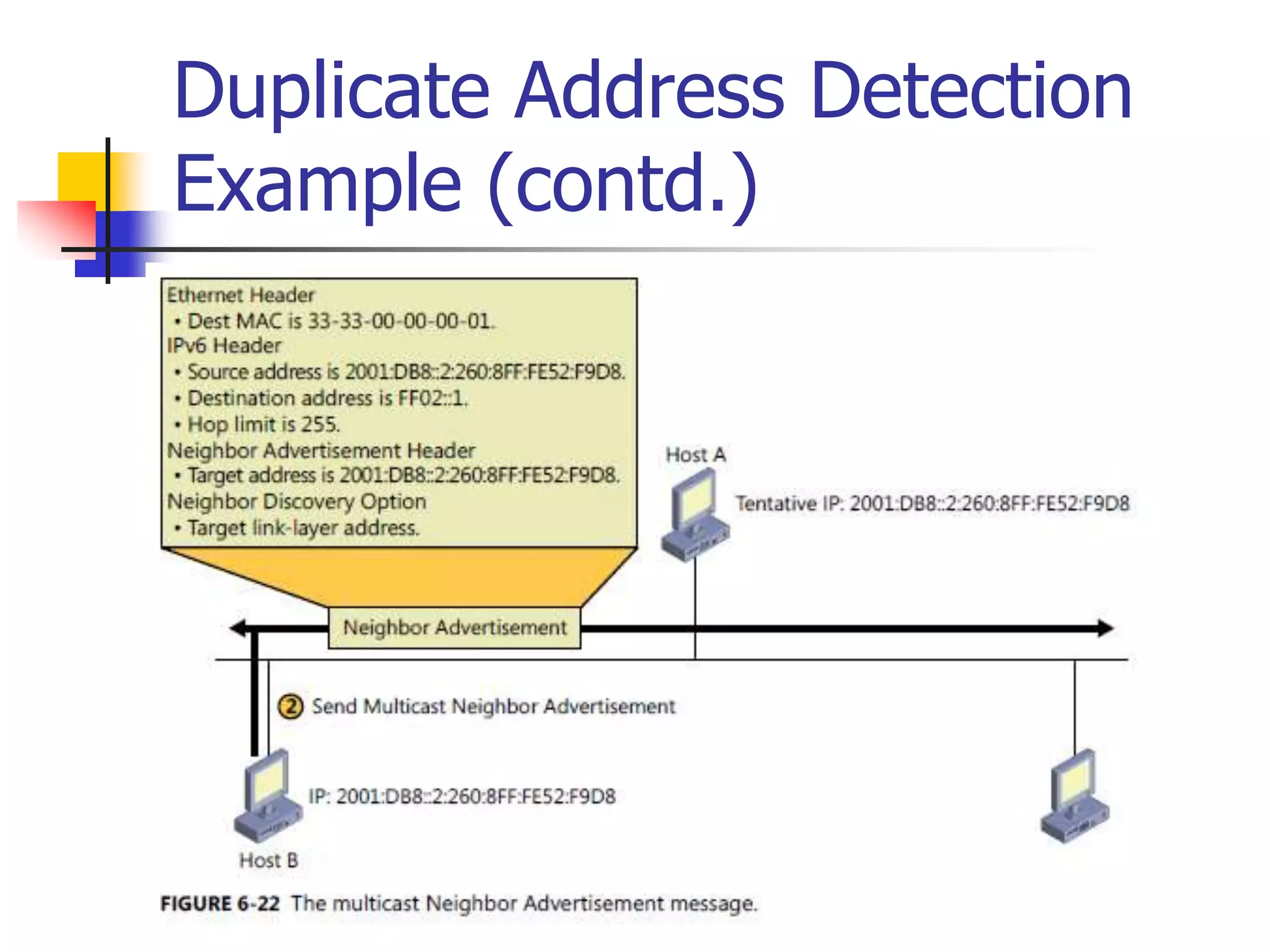
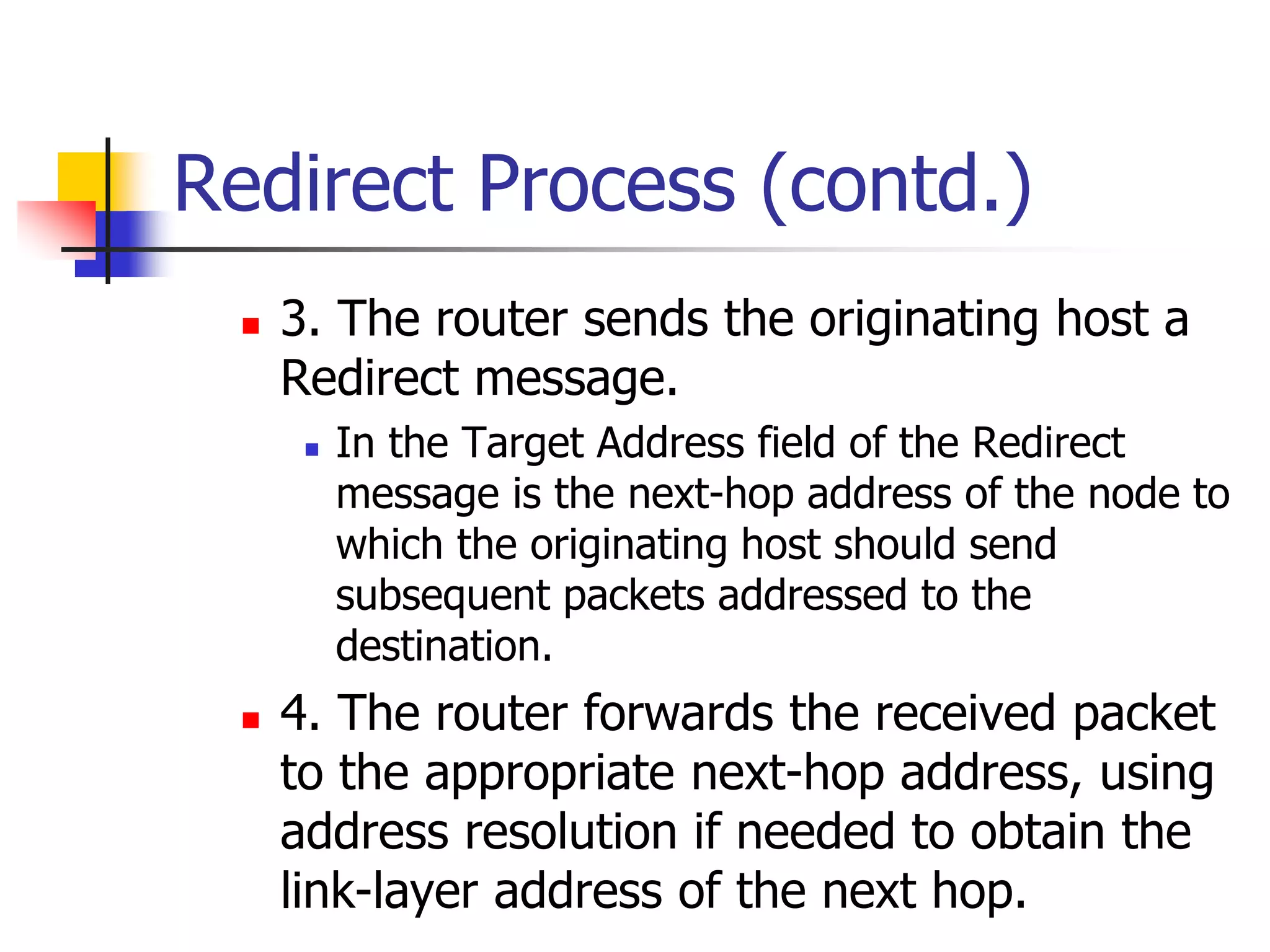
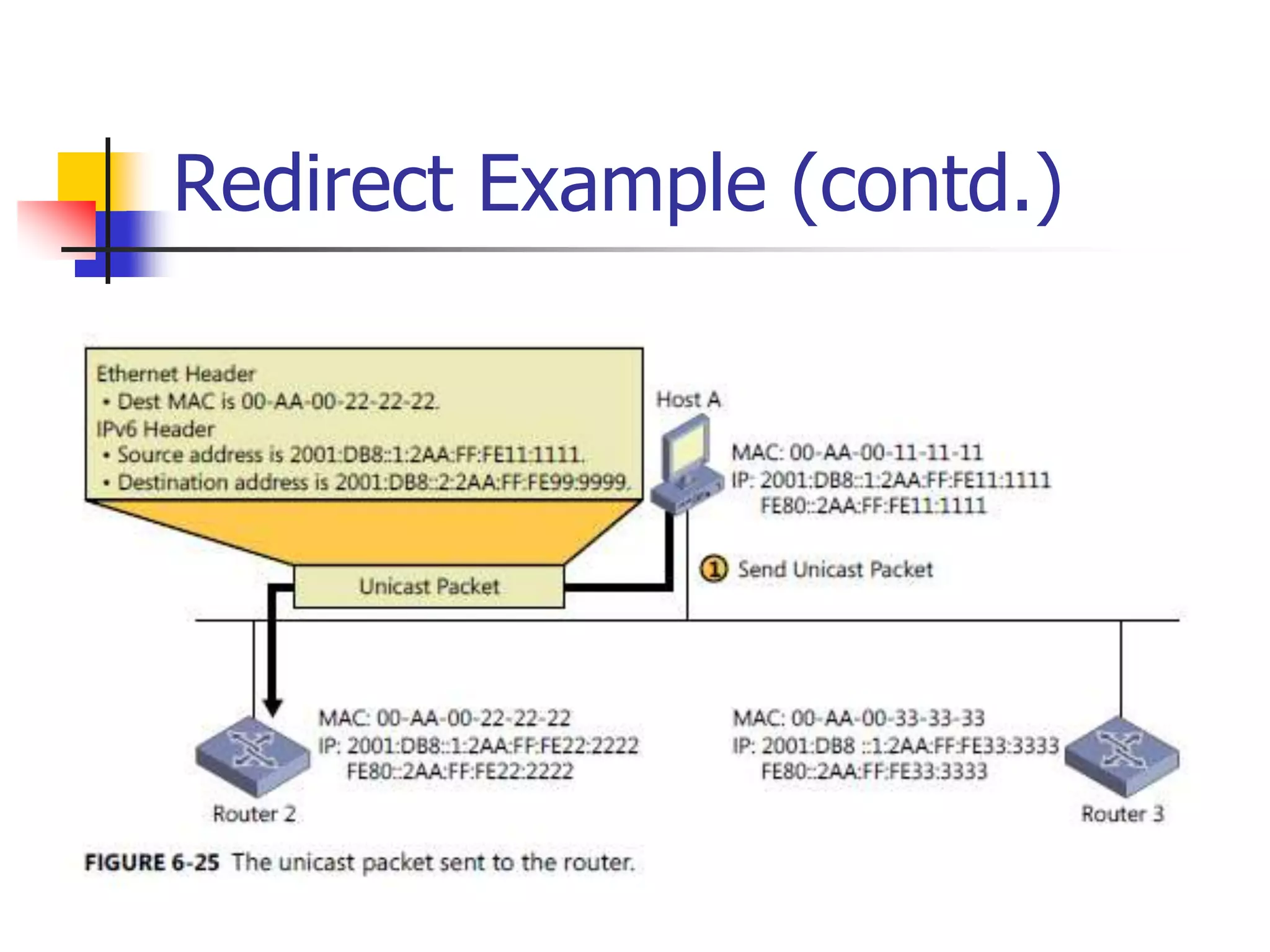
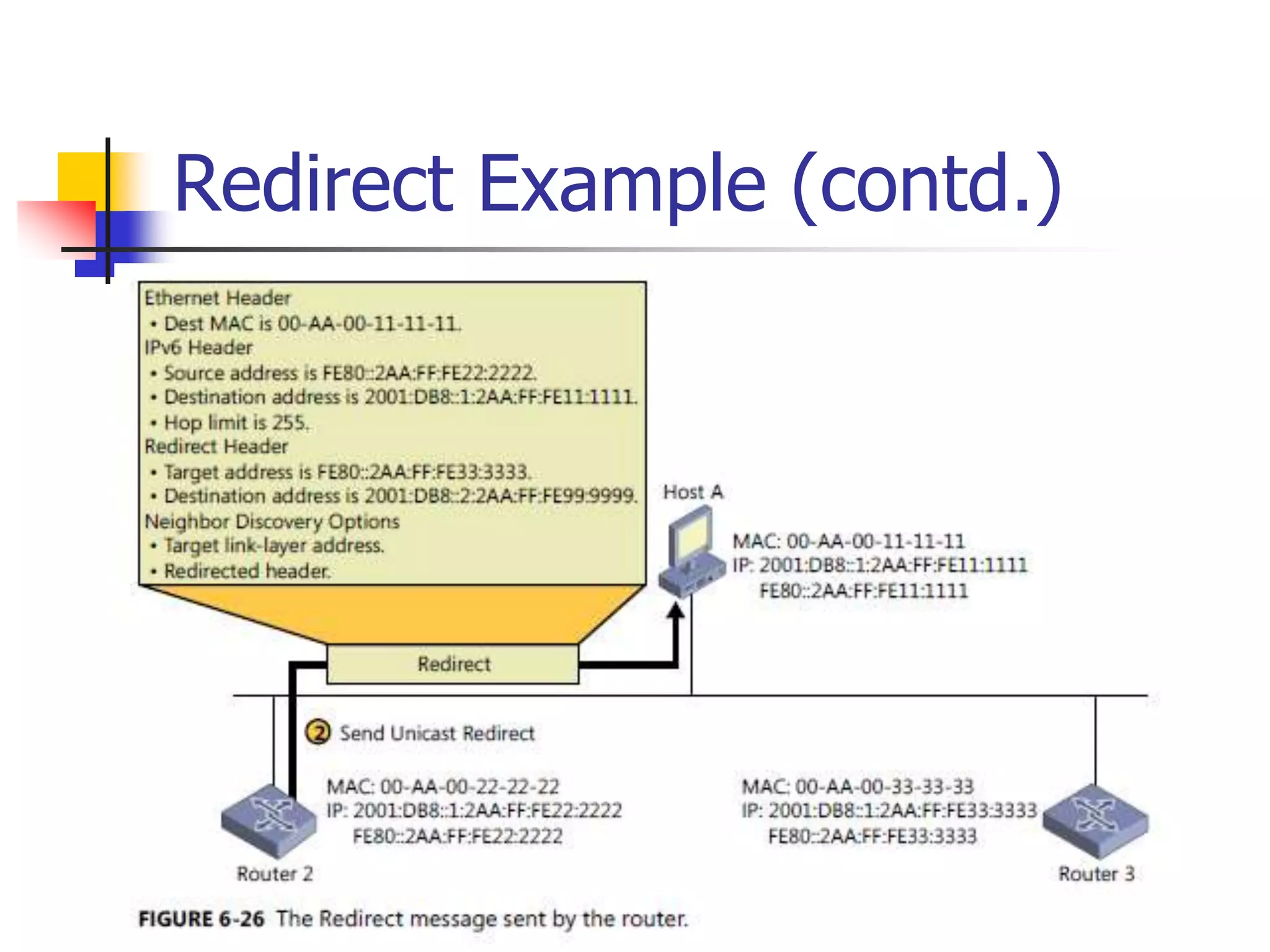
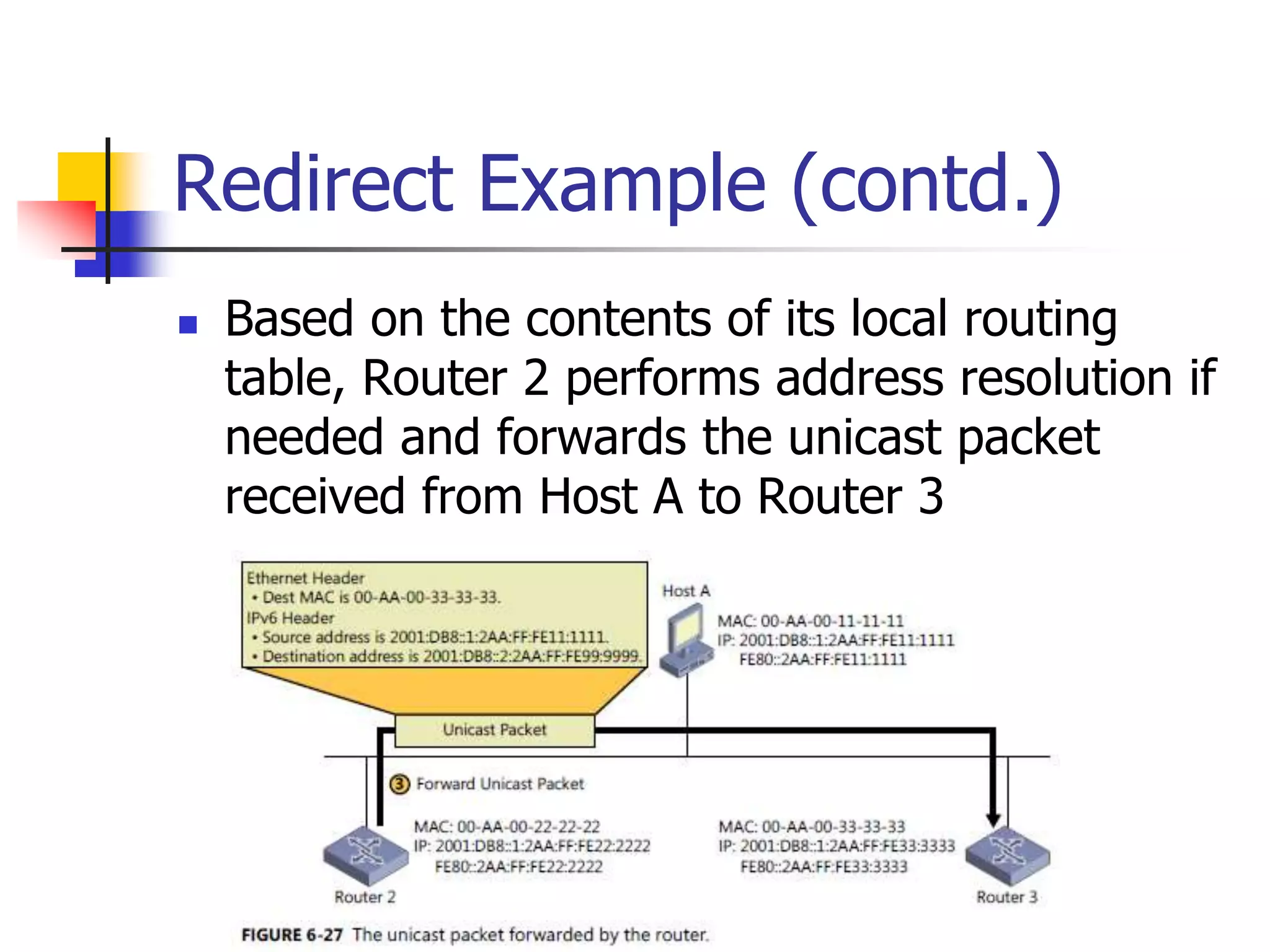
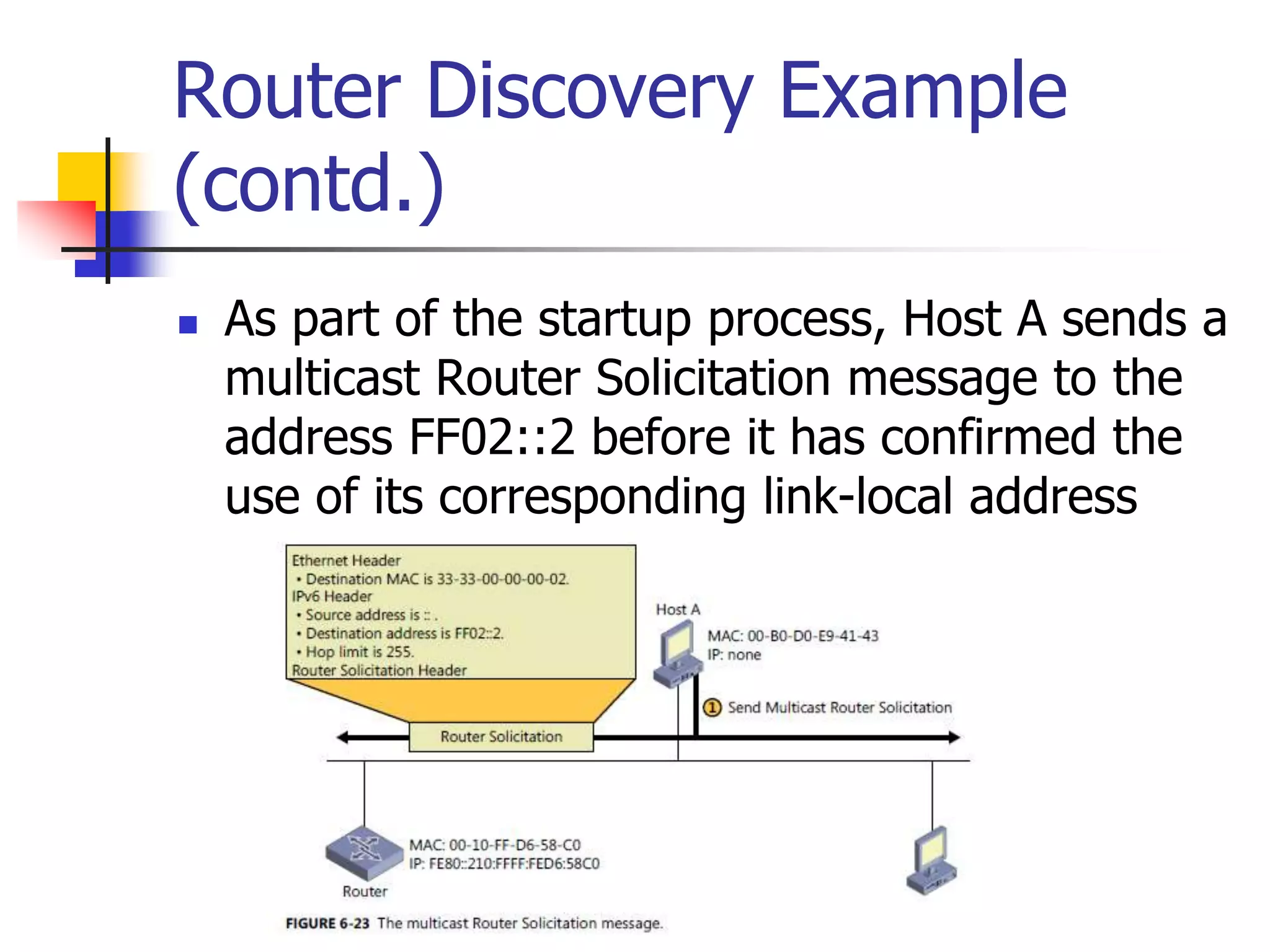
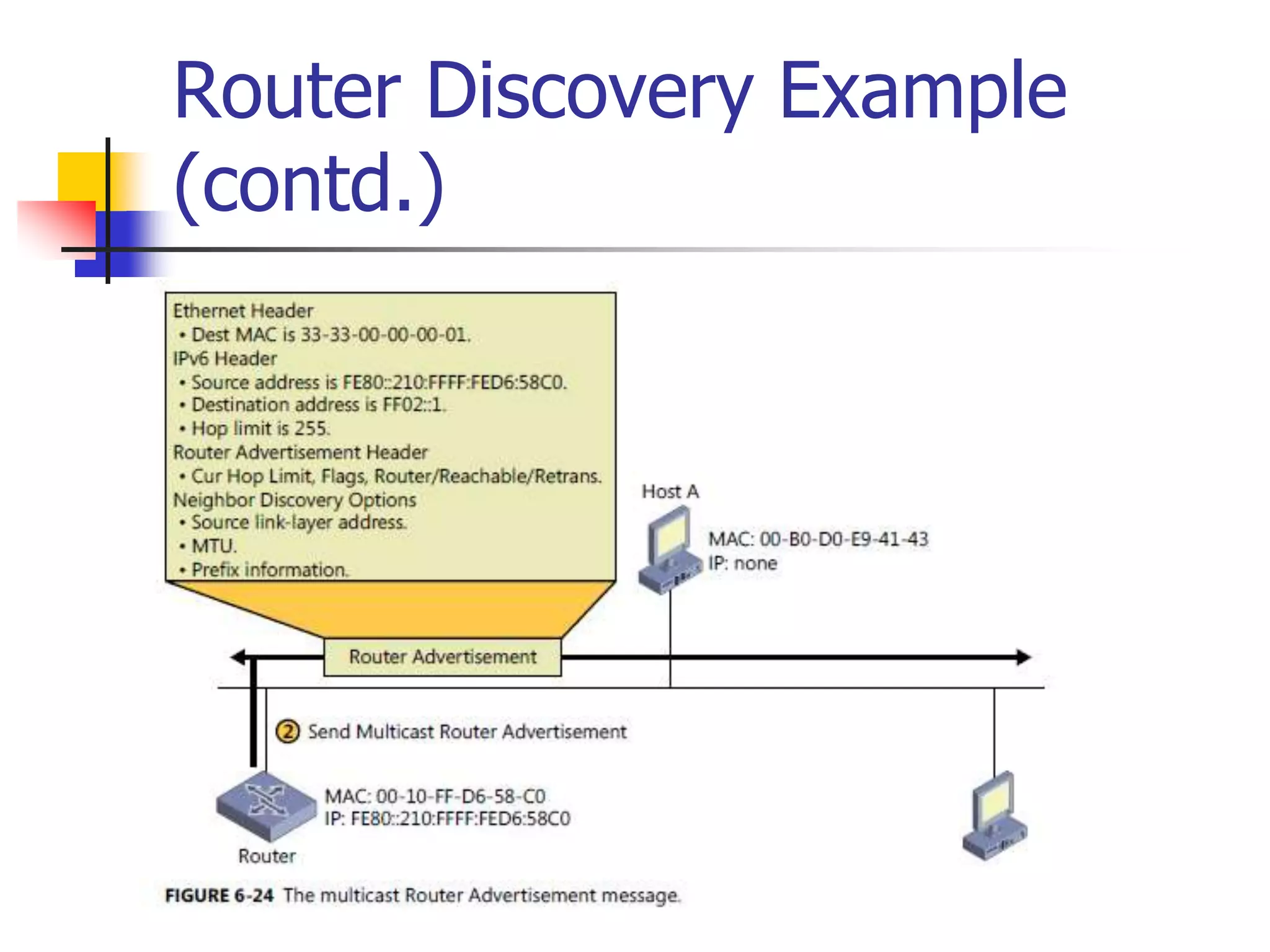
The document discusses IPv6 Neighbor Discovery. It explains that Neighbor Discovery allows nodes on the same link to discover each other, determine link-layer addresses, find routers, and maintain reachability information for active neighbors. It describes the various Neighbor Discovery message types and processes, including address resolution, duplicate address detection, and redirect function. Conceptual data structures for neighbor caches, destination caches, prefix lists, and default router lists are also outlined.