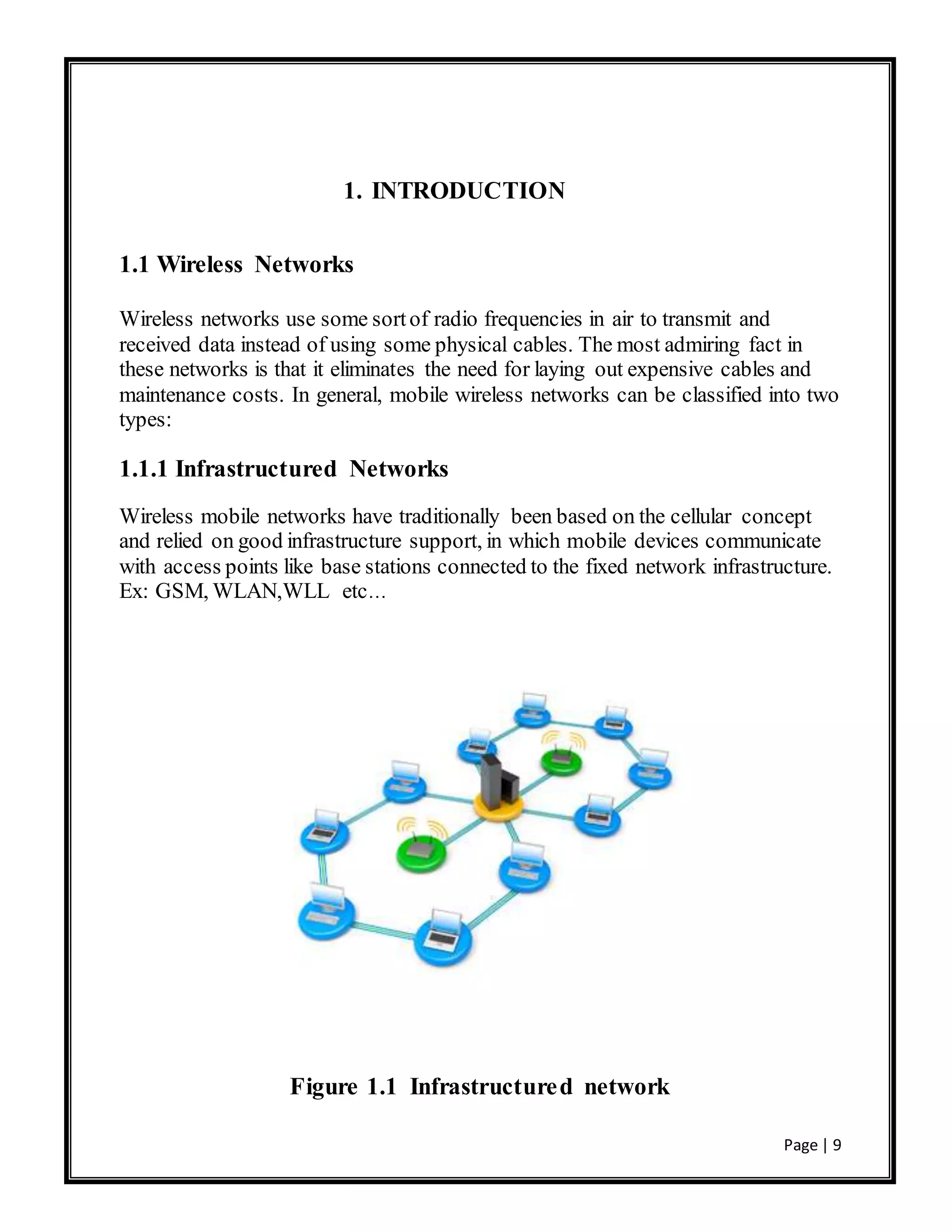
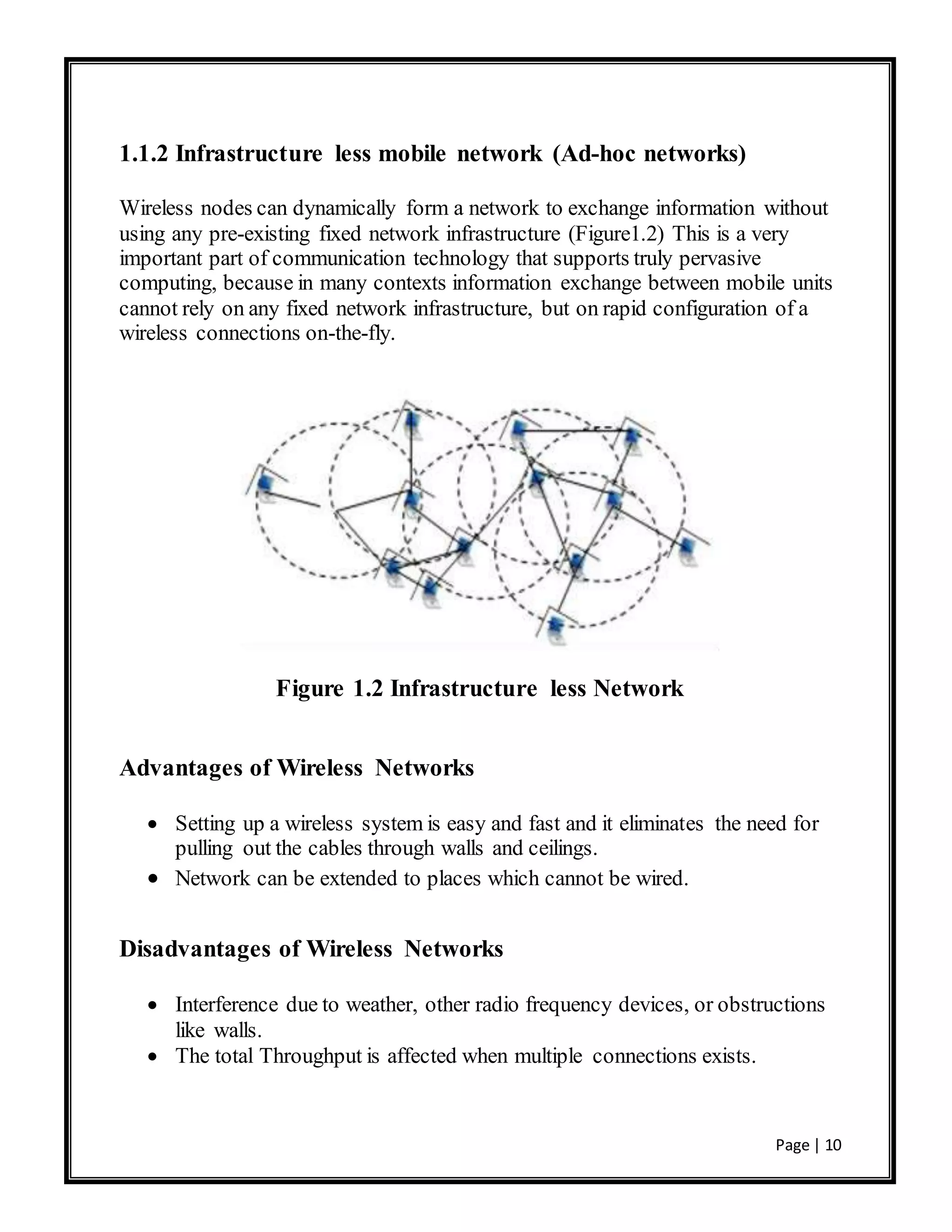
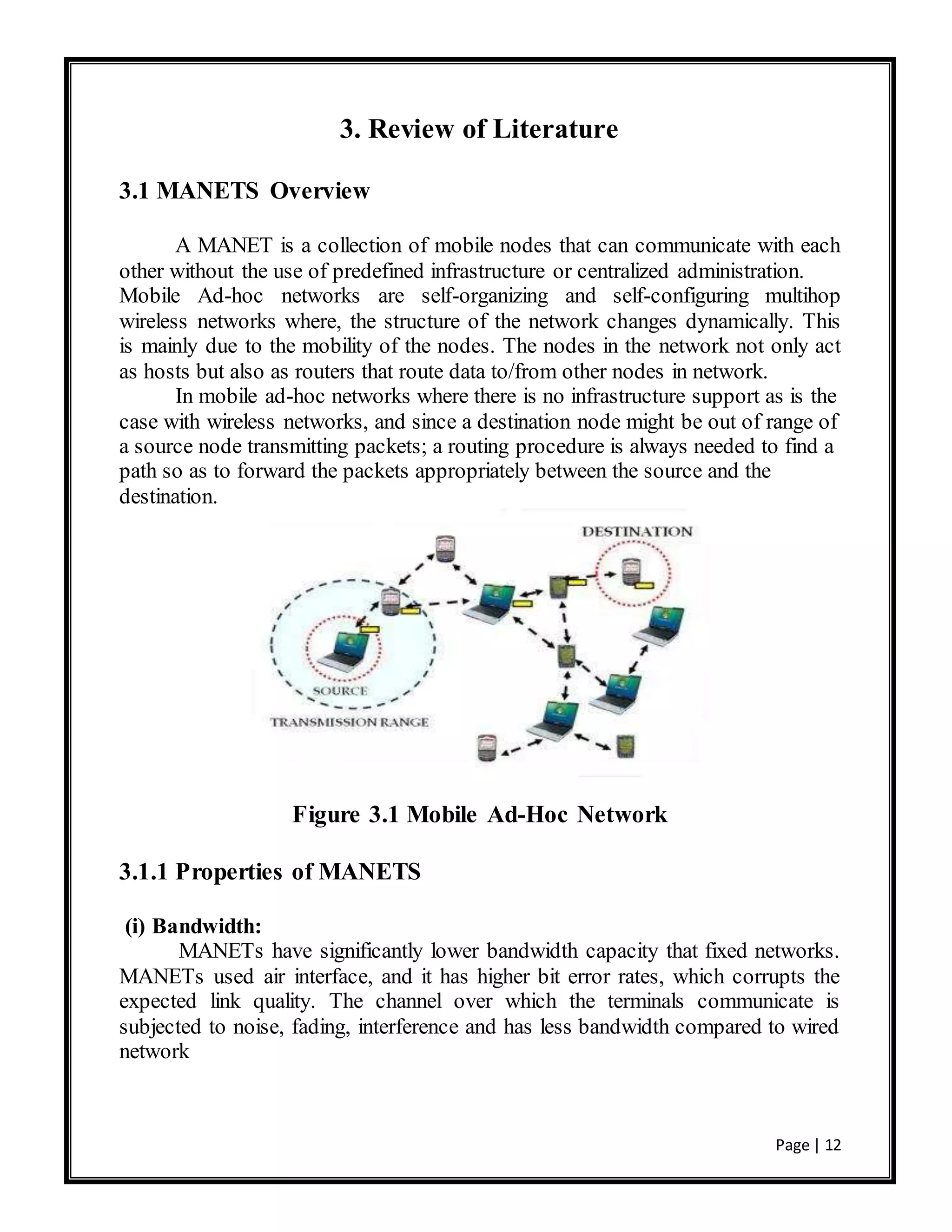
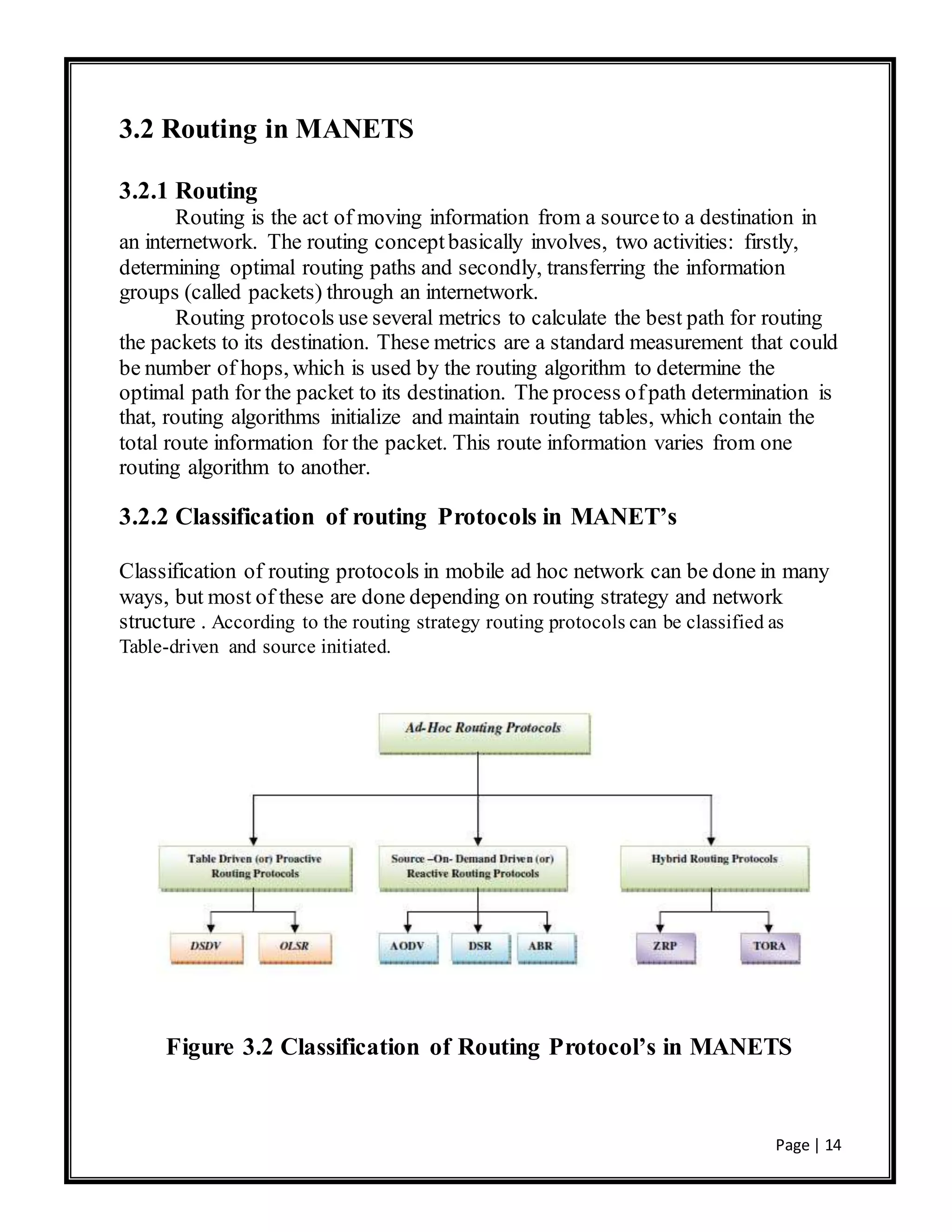
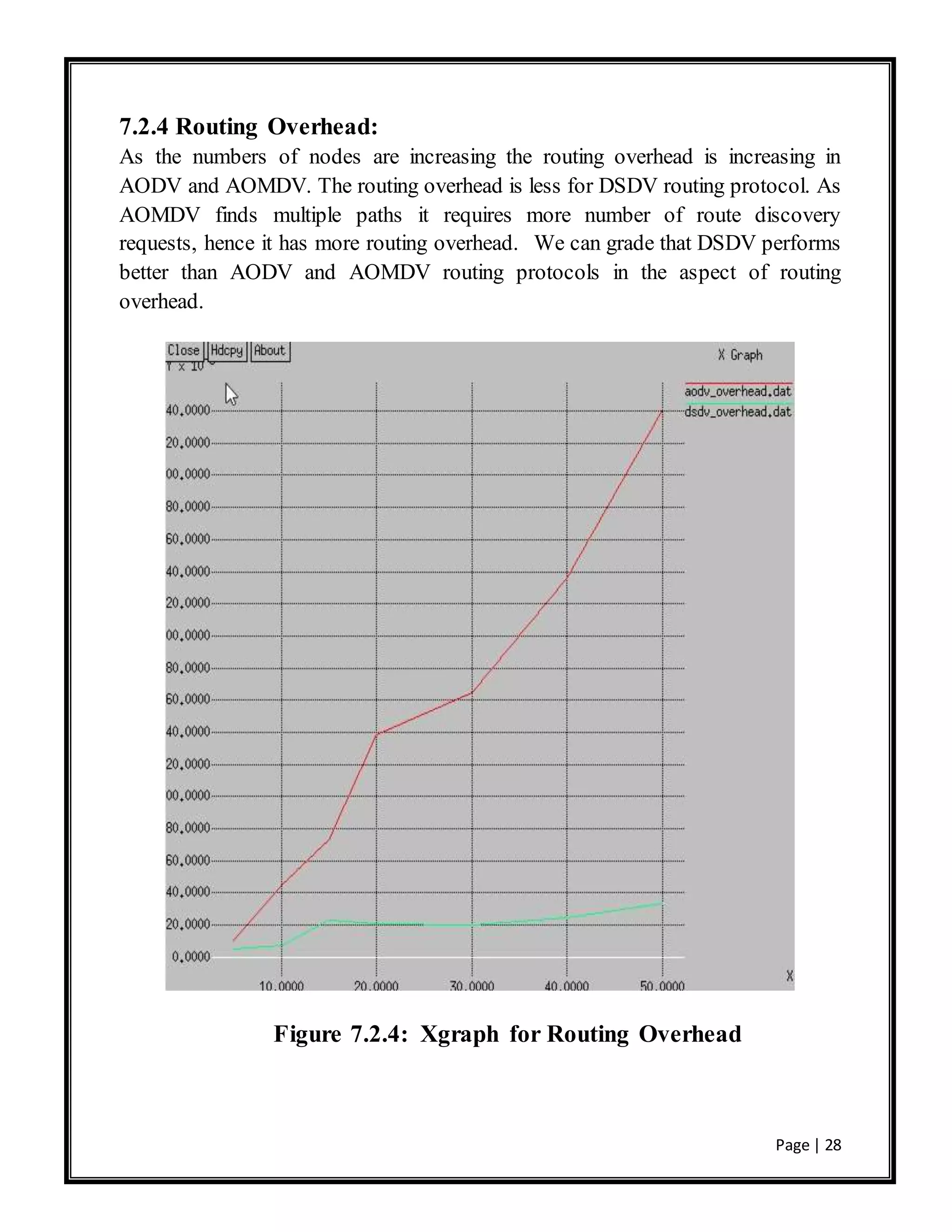
This document is a project report submitted by three students for their Bachelor of Technology degree. It analyzes the performance of the AODV and DSDV routing protocols for mobile ad hoc networks (MANETs) using the NS-2 network simulator. The report includes an introduction to MANETs, a literature review of routing protocols for MANETs including AODV and DSDV, a description of the simulation setup and design using NS-2, results of the simulations comparing the performance of AODV and DSDV under different metrics, and conclusions.












![Page | 20
5.2 Defining Global Variables:
set ns_ [new Simulator] #creates a new simulator instance
set topo [new Topography] #creates a new topology
$topo load_flatgrid 670 670 #defines it in 670X670 area
Here set command is used to create a global variable. The first argument is the
variable name (ns_, topo, etc.). the second argument is used to get the value of the
variable.
5.3 Defining Standard NS/NAM Trace:
To run the output of the program in an animator we need a nam file, and to
analyze the output we need trace file. So the program must output certain files
called nam file and trace file. We can do so by the following commands:
Set tracefd [open demo.tr w]
$ns_ trace-all $tracefd
Set namtrace [open demo.nam w]
$ns_ namtrace-all-wireless $namtrace 670 670
5.4 Mobile Node Configuration:
We can configure a mobile node by following codes.
$ns_node-config -adhocRouting DSDV
-llType LL
-macType Mac/802_11
-ifqLen 50
-ifqType Queue/DropTail/PriQueue
-antType Antenna/OmniAntenna
-propType Propagation/TwoRayGround
-phyType Phy/WirelessPhy 20](https://image.slidesharecdn.com/85578728-62b1-40ca-8a62-e63455cc2e56-150625091632-lva1-app6891/75/Performance-Analysis-of-AODV-and-DSDV-FINAL-YEAR-PROJECT-20-2048.jpg)


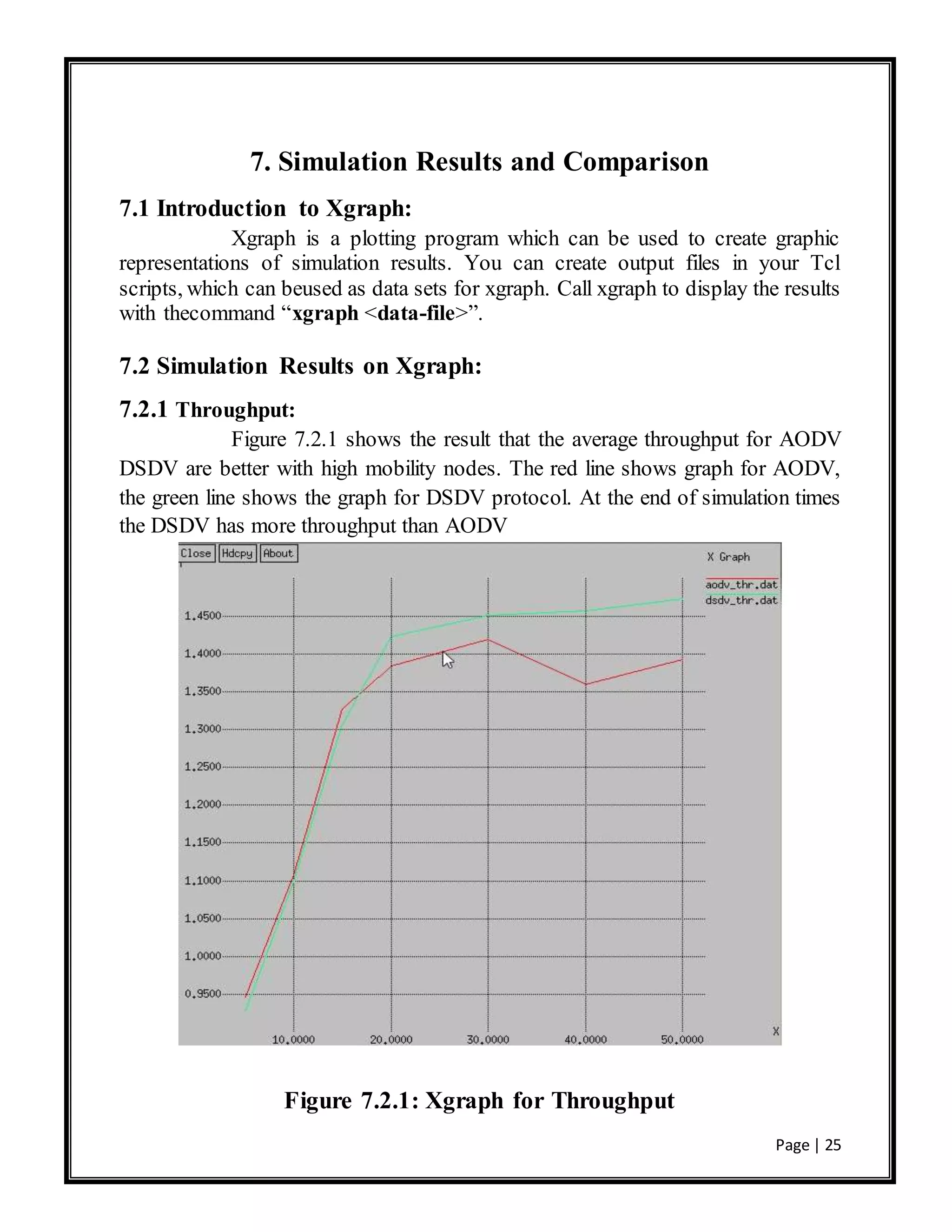
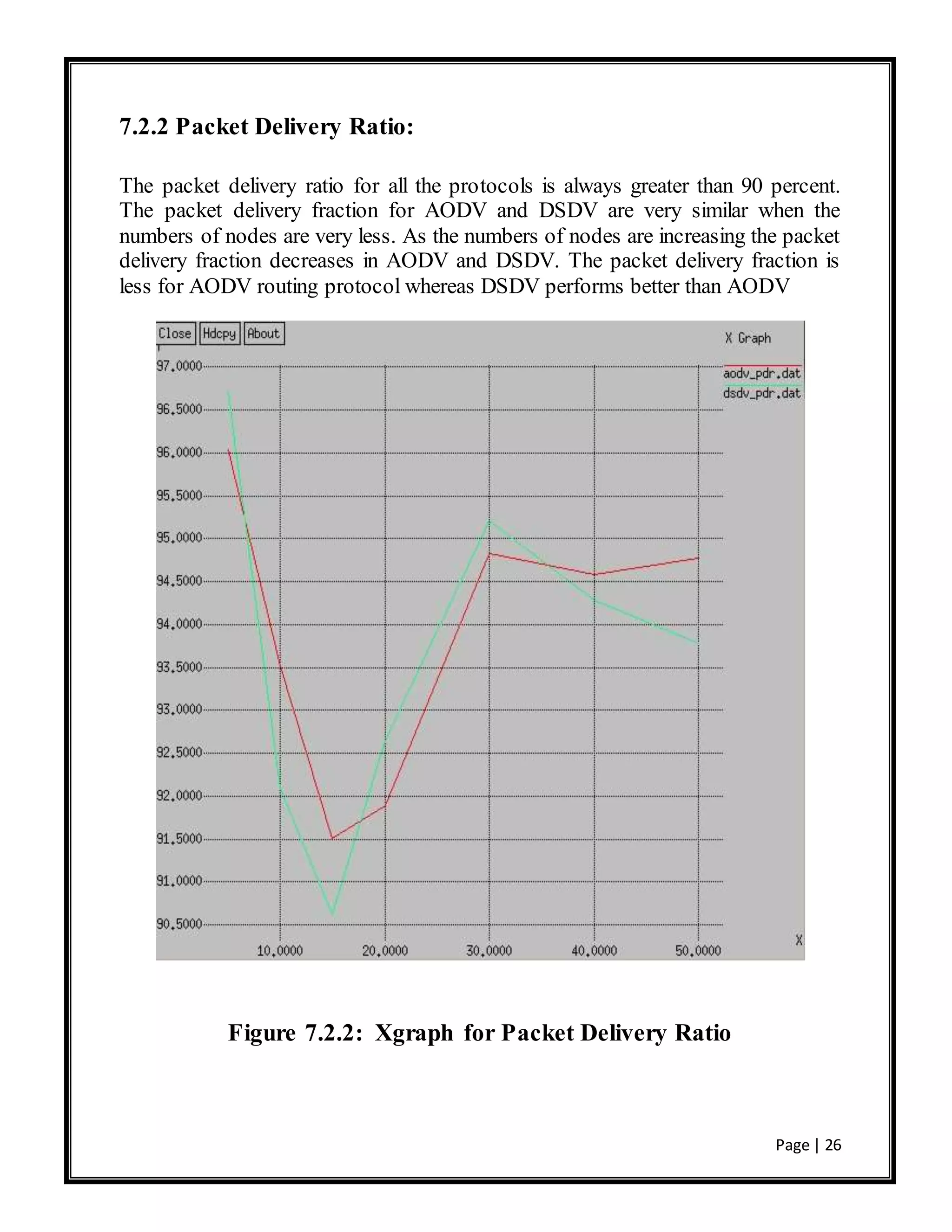
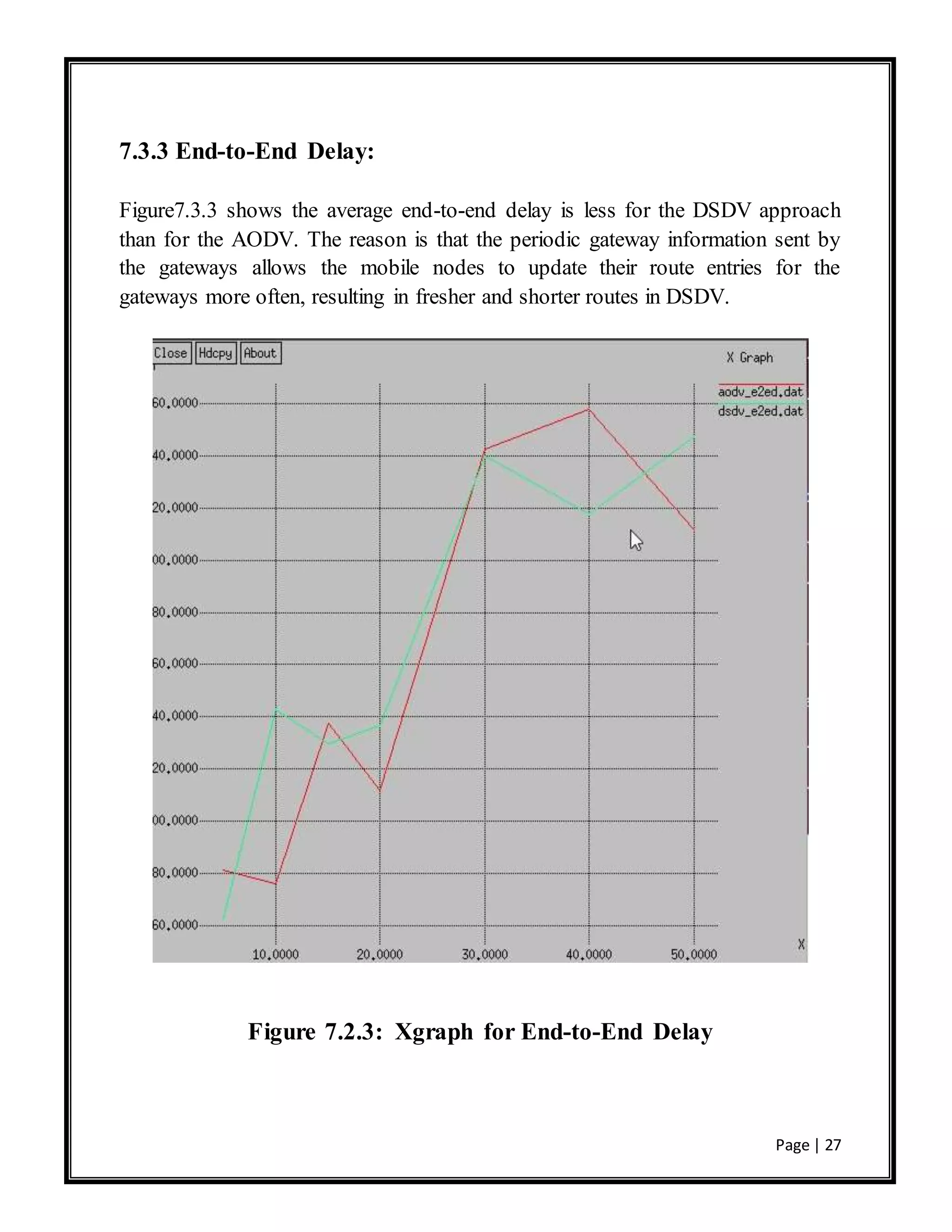

![Page | 30
9. References
1. Mina Vajed Khiavi, Shahram Jamali, Performance Comparison of AODV
and DSDV Routing Protocols in Mobile Ad Hoc Networks,International
Research Journal of Applied and Basic Sciences, 2013
2. Manjusha S. Patil Bokade, Prof. M.N.Thakare, Prof. B. J. Chilke,
Performance Evaluation of MANET Routing Protocols DSDV, DSR and
AODV for Different Mobility Models,International Journal of Application
or Innovation in Engineering & Management (IJAIEM), 2014
3. Dr. Srinivasa Rao Angajala, A New Algorithm for CR Protocols In AD-Hoc
Networks, Professor Mekapati Rajamohan Reddy Institute of Technology &
Science,[IJESAT]International Journal Of Engineering Science & Advanced
Technology, 2012
4. G. Jose Moses* D. Sunil Kumar Prof.P.Suresh Varma N.Supriya, A
Simulation Based Study of AODV, DSR, DSDV Routing Protocols in
MANET Using NS-2, International Journal of Advanced Research in
Computer Science and Software Engineering, 201](https://image.slidesharecdn.com/85578728-62b1-40ca-8a62-e63455cc2e56-150625091632-lva1-app6891/75/Performance-Analysis-of-AODV-and-DSDV-FINAL-YEAR-PROJECT-30-2048.jpg)