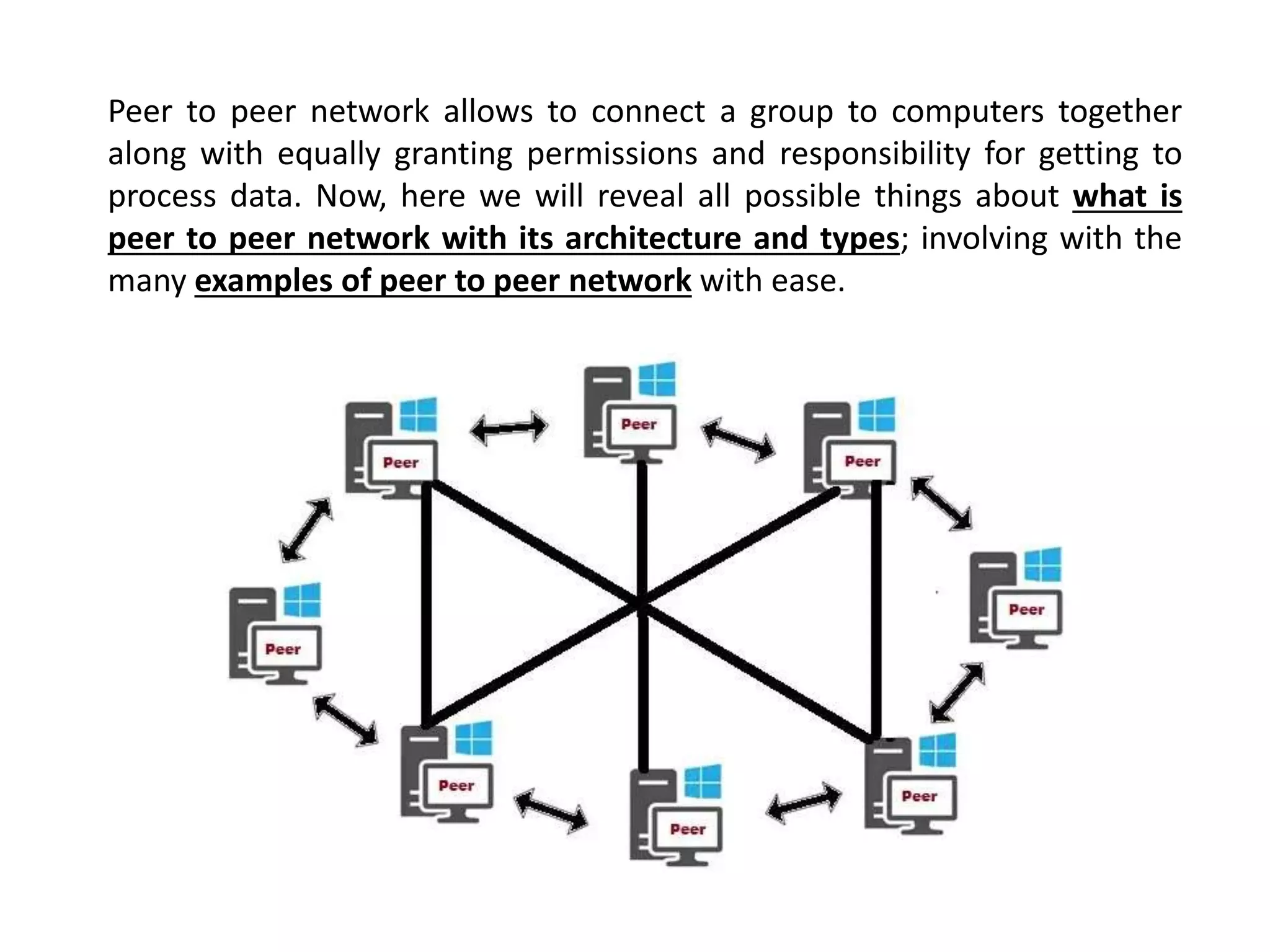
The document explains peer-to-peer (P2P) networks, describing their architecture, types, and examples such as Napster, BitTorrent, and Skype. P2P networks allow computers to connect without a central server, enabling file sharing where every user acts as both client and server. Additionally, it emphasizes the importance of security measures to protect data and prevent malware within P2P environments.