This document discusses service-based content sharing in mobile ad-hoc networks. It proposes a peer-to-peer file sharing system that allows efficient content distribution using low-cost Bluetooth links. Peers discover each other via scanning and share subscribed content in segments over Bluetooth. The system was implemented on Blackberry and Windows Mobile smartphones to test feasibility. Tests showed file transfers were practical between mobile devices using this approach, with segment size having little effect on performance.




![Service Based Content Sharing in the Environment of Mobile Ad-hoc Networks
www.iosrjournals.org 12 | Page
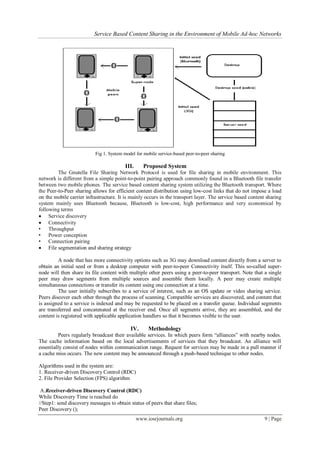
Fig. 5. Transaction times in the Windows Mobile device test, with different peer numbers and segment sizes utilized. The
throughput rate levels shown (in bits per second) are for 2, 3, and 4 peers communicating with each other, respectively, in
three successive blocks of time, each approximately 300 seconds in duration. Within each block, for the same number of
peers, the segment size was increased from 100 to 1400 bytes, but had little effect on the rate.
VI. Conclusion
The Service Based model that permits efficient file sharing between mobile smartphones over a low-
cost transport using Bluetooth. This results lead us to conclude that Service Based file transfers between today’s
mobile devices are practical using Bluetooth. But severe restrictions must be enforced on the transfer of data.
Where the Gnutella networks are used in the mobile device environment. Gnutella networks are uses in order to
reduce the amount of traffic for the mobile device and providing support for device mobility. Where the Service
Based Sharing allows for efficient content distribution using low-cost links that do not impose a load on the
mobile carrier infrastructure. Through experimentation on leading smartphones, we have found various optimal
strategies, including minimizing the upload-to-download ratio to conserve battery life, using larger file segments
to increase throughput, and using sockets to decrease memory overhead.
References
[1] A. Oram, “Peer-to-Peer: Harnessing the Benefits of a Disruptive Technology”. O’Reilly, 2001.
[2] K. Kant, “An analytic model for peer to peer file sharing networks,” in IEEE International Conference on Communications, May
2003, pp. 1801 – 1805 vol. 3.
[3] A. Legout, G. Urvoy-Keller, and P. Michiardi, “Rarest First and Choke Algorithms Are Enough,” in IMC’06, Rio de Janeiro,
Brazil, 2006.
[4] Yang, X. et al, “Service capacity of peer to peer networks,” in 23rd Joint Conference of IEEE Computer and Communications,
2004.
[5] Hu, T. H. et al, “Supporting mobile devices in Gnutella file sharing network with mobile agents,” in 8th IEEE Int. Symposium on
Computers and Communication, Sep. 2003, pp. 1035 – 1040 vol. 2.
[6] Dhurandher, S. K. et al, “A swarm intelligence-based p2p file sharing protocol using bee algorithm,” in IEEE/ACS Int. Conf. on
Computer Systems and Applications, 2009.
[7] Asadi, M. et al, “A scalable lookup service for p2p file sharing in manet,” in Proc. of the 2007 Int. Conference on Wireless Comm.
and Mobile Computing. New York, NY, USA: ACM, 2007.
[8] Huang, C.-M. et al, “A file discovery control scheme for P2P file sharing applications in wireless mobile environments,” in Proc. of
the 28th
Australasian Conference on C.S., 2005.
[9] O. Ratsimor, D. Chakraborty, A. Joshi, T. Finin, and Y. Yesha, “Service discovery in agent-based pervasive computing
environments,” Mob. Netw. Appl., vol. 9, no. 6, pp. 679–692, 2004.
[10] G. P. Perrucci and F. Fitzek, “Measurements campaign for energy consumption on mobile phones,” Aalborg University, Tech. Rep.,
2009.
[11] A. Kammer et al, “Bluetooth Application Developer’s Guide: The Short Range Interconnect Solution”. Rockland, MA: Syngress,
2002.
[12] D. Barkai, “Peer-to-Peer Computing”. Intel Press, 2001.
[13] S. Androutsellis-Theotokis et al, “A survey of peer-to-peer content distribution technologies,” in ACM Computing Surveys, Dec.
2004.
[14] M. Connolly et al, “Analysis of UDP Performance over Bluetooth,” in IT&T2003: Proc. of the IT & Telecommunications
Conference, Oct. 2003.
[16] A. Misic and V. Misic,”Performance Modeling and Analysis of Bluetooth Networks”. Boca Raton, FL: Auer Bach Publications,
2006.
[17] A. Huang et al, “Bluetooth Essentials for Programmers”. Cambridge University Press, 2007](https://image.slidesharecdn.com/b01020712-140428234447-phpapp02/85/Service-Based-Content-Sharing-in-the-Environment-of-Mobile-Ad-hoc-Networks-6-320.jpg)