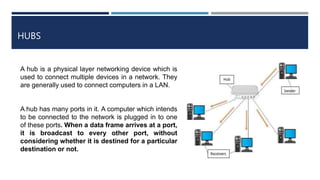
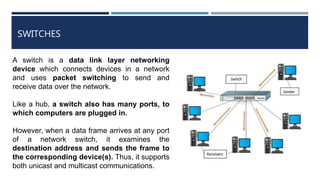
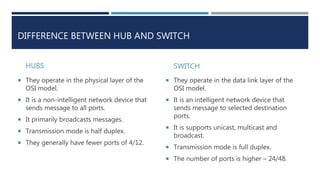
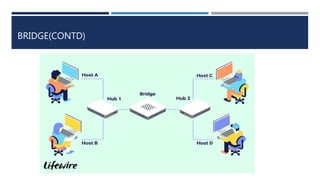
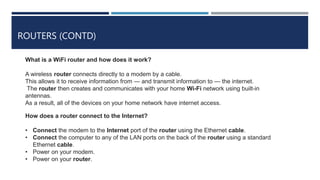
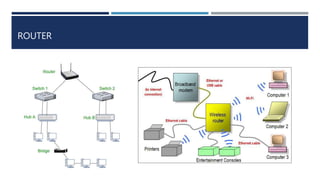
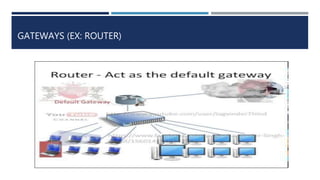
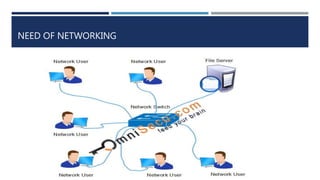
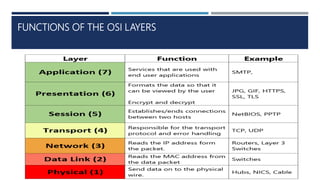
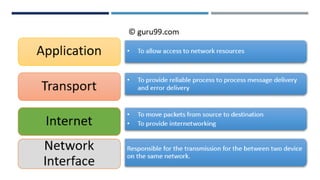
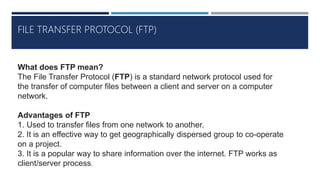
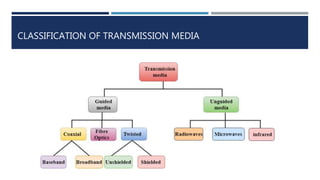
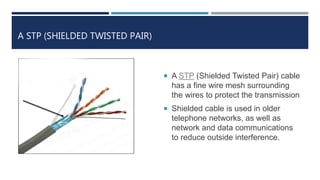
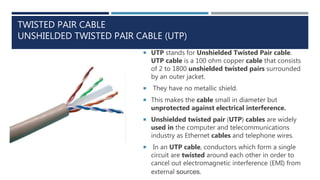
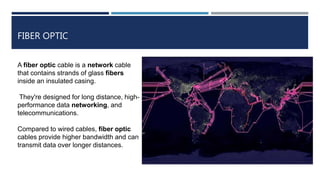
The document provides an overview of networking concepts, explaining what a network is, its goals, and the necessity of networking for resource sharing, communication, and reliability. It introduces important networking models such as the OSI and TCP/IP models, discussing their layers and functions, and highlights protocols like HTTP and FTP for data transfer. Additionally, it covers various network topologies, transmission media, and server types, emphasizing the importance of these elements in computer networking.



































![TYPES OF WIRELESS COMMUNICATION
Different types of signals are used in communication between the devices for
wireless transmission of data. The following are the different electromagnetic
signals are used depending on their wavelength and frequency.
•Radio Waves (Radio Frequency Transmission – RF Waves)
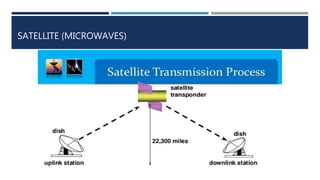
•Satellite [Satellite Microwave Transmission]
•Microwave
•Infrared
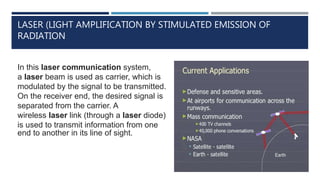
•Laser](https://image.slidesharecdn.com/networkingconceptsfinal-191130080303/85/Introduction-to-Computer-Networking-59-320.jpg)