The document summarizes an OWASP compliance report generated by Acunetix for a website. It found:
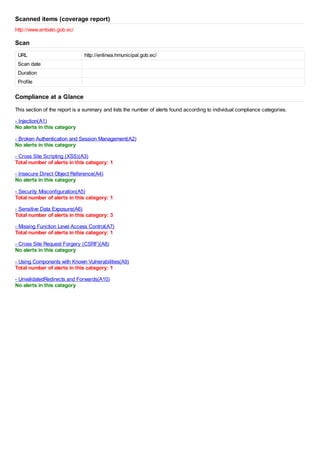
1 alert for security misconfiguration as the site has a web application firewall; 3 alerts for sensitive data exposure due to missing X-Frame-Options header and possible virtual hosting; and 1 alert for missing access controls also due to the missing X-Frame-Options header. The report analyzed the site for 10 common compliance categories and OWASP top vulnerabilities.