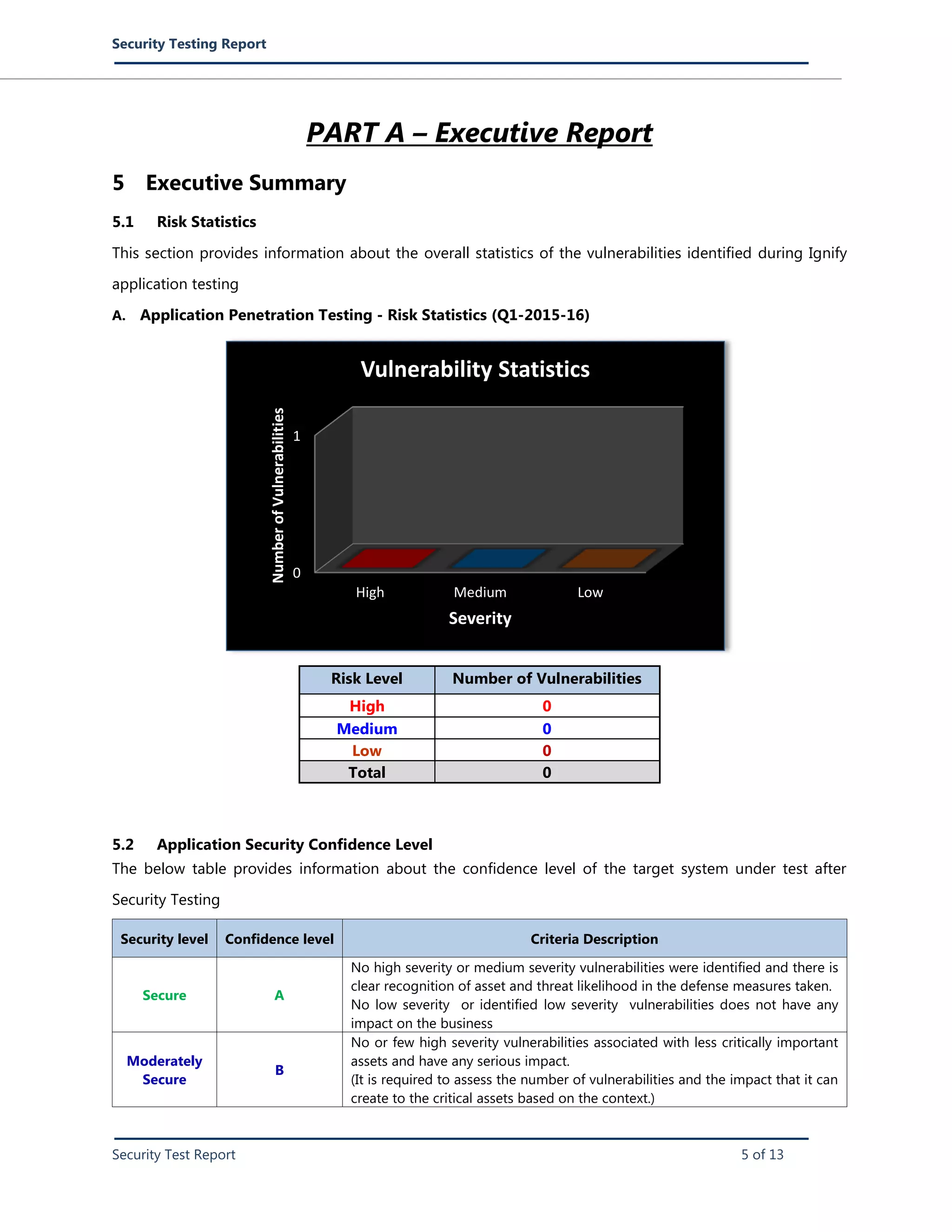
The summary provides an overview of the security testing report for the Ignify web applications. No high or medium severity vulnerabilities were found, resulting in an overall security confidence level of A (Secure). Some low severity issues were identified, such as weak password policies, but these do not significantly impact the applications or business. The report includes detailed information on vulnerabilities found, risk levels, ways to reproduce issues, and recommendations for remediation.




![Security Testing Report
Security Test Report 8 of 13
Ignify_Nav=PDCacheKey_5%3DBEST-SELLER-PRODUCTS-SESSION-
KEY%5EPDPrevNextReffer_5%3Dhttp%3A//ecom7.ignify.net/search/denim%3Ffilter%3D%26search%3Ddenim%26ty
pe%3Dq%26keywordoption%3DANY%26cid%3D0%26fltrdesc%3D%5ECurrentPDReferrer_5%3Dhttp%3A//ecom7.ig
nify.net/search/denim%3Ffilter%3D%26search%3Ddenim%26type%3Dq%26keywordoption%3DANY%26cid%3D0%2
6fltrdesc%3D%5E; WebStore_SessionId=thbrzrkjhobmkpe0k0cbhp3n; userdata=e5c362af-62a0-49a0-841b-
ad794907d1c4;__utmt=1;Ignify.eCommerce=9CF008C2998126F461C25A08DD261874B555C8EFFFDED2A6DD187A9
32D6BF8626C02C5AD1D6CDED550C9B5297EF297FF2867DAA5C6B063D57C65FFAA9C2BBD776DED5D5EF948A3DEC
BEC60A974EBE85CE8AA79F1DA731C0565E9E2A5DAFB04EFFE895D00DA7CE05CA46CDFBB9FD6B9755736D3D64E9
8A5813168E195E3DF7B054514CF7A
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
hdnSelectedVal=&hdnFromPrice=7.98&hdnToPrice=87.80&hdnIsQuickMenuVisible=&hdnCurrentProductIds=&hdnFilter
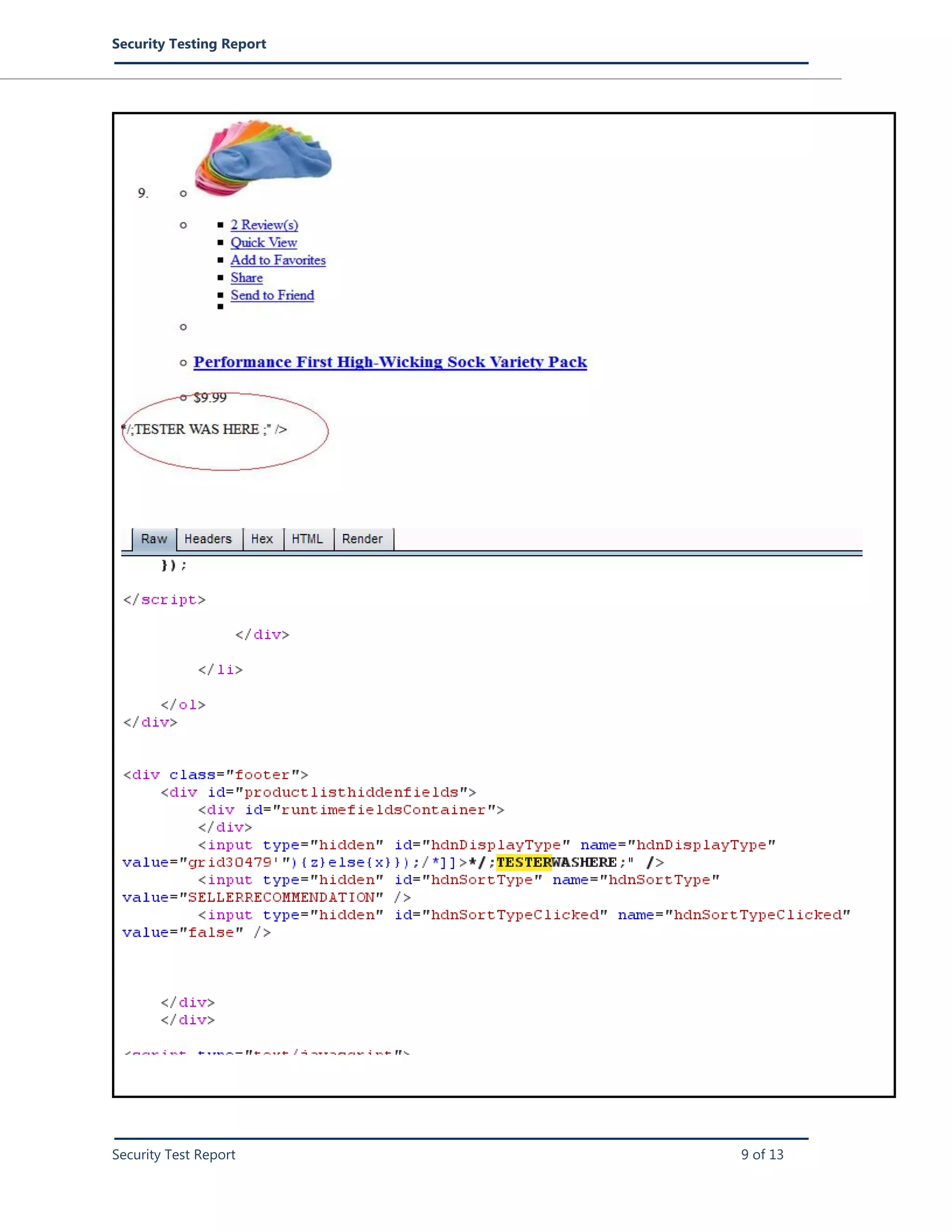
=1180&hdndiscountid=&hdnDisplayType=grid30479'"){z}else{x}});/*]]>*/;TESTERWASHERE;&hdnSortType=SELLERRECO
MMENDATION&hdnSortTypeClicked=false
Note: Observe that the Java script is executed and alert box appears. Provided XSS payload is an example but,
this can be exploited using maliciously crafted scripts
Impact
1. An attacker can inject malicious content in the application through browser
2. Threat to Integrity of the application
3. Content Manipulation
Countermeasure/Recommendations
1. Filter the meta characters ("special" characters) and validate the user input to prevent unintended changes
in the application
2. Web server should ensure that the generated pages are properly encoded to prevent unintended execution
of scripts
3. Use Attribute Escape Before Inserting Untrusted Data into HTML Common Attributes
Remarks :](https://image.slidesharecdn.com/securitytestingreporthitachiapplicationq1sep2015-160413110237/75/Security-Testing-Report-Hitachi-Application-Q1-Sep-2015-8-2048.jpg)