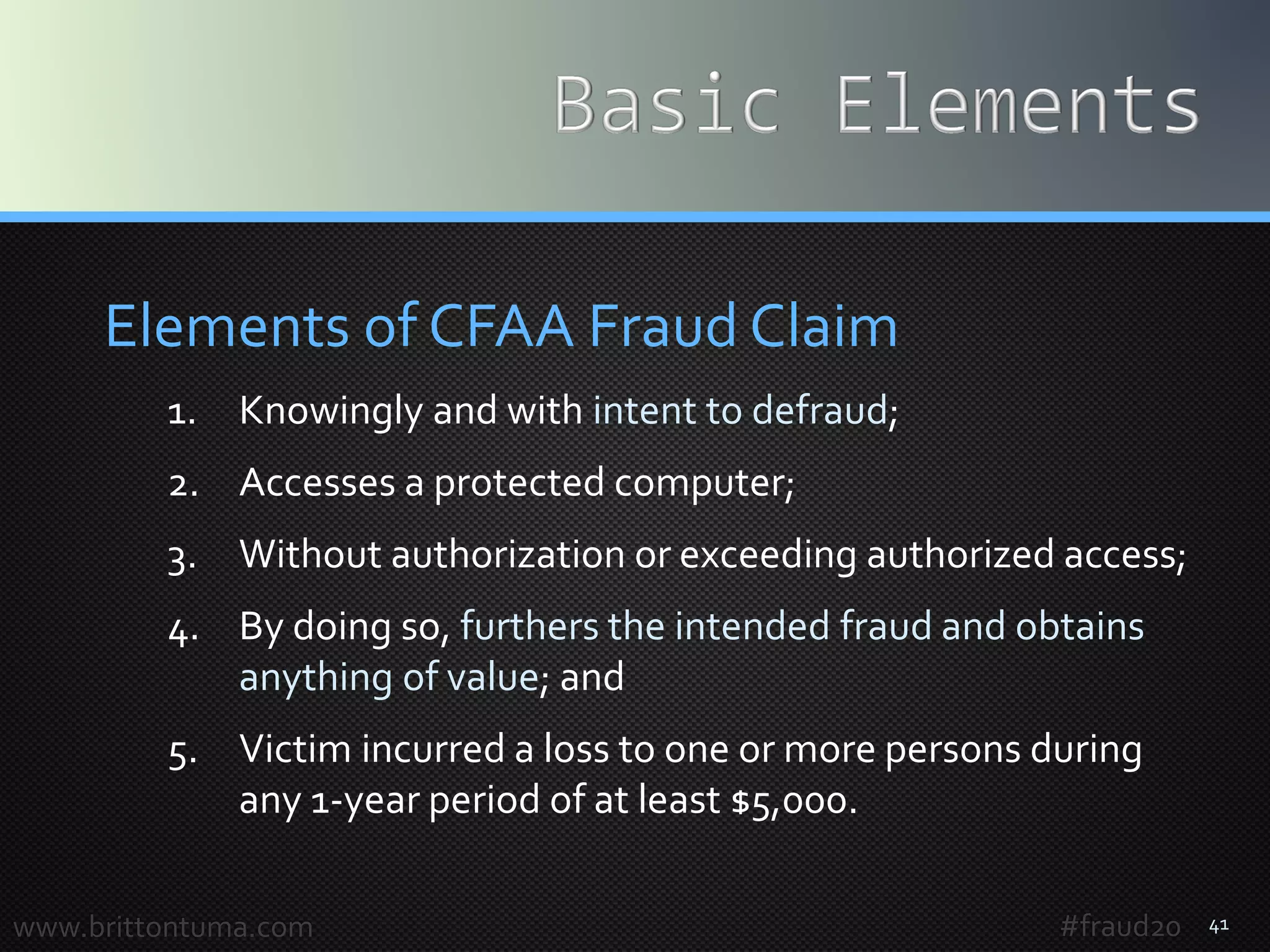
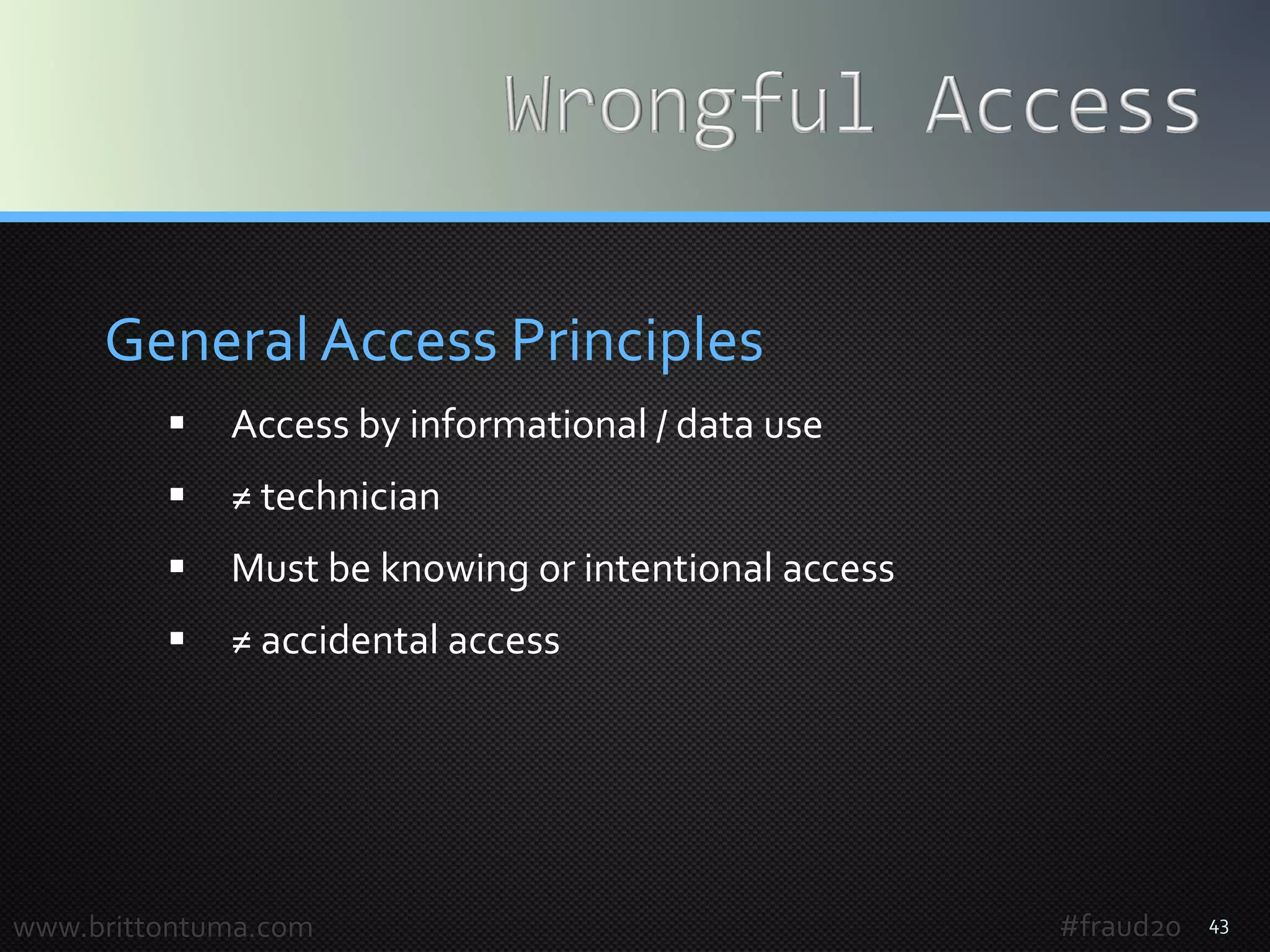
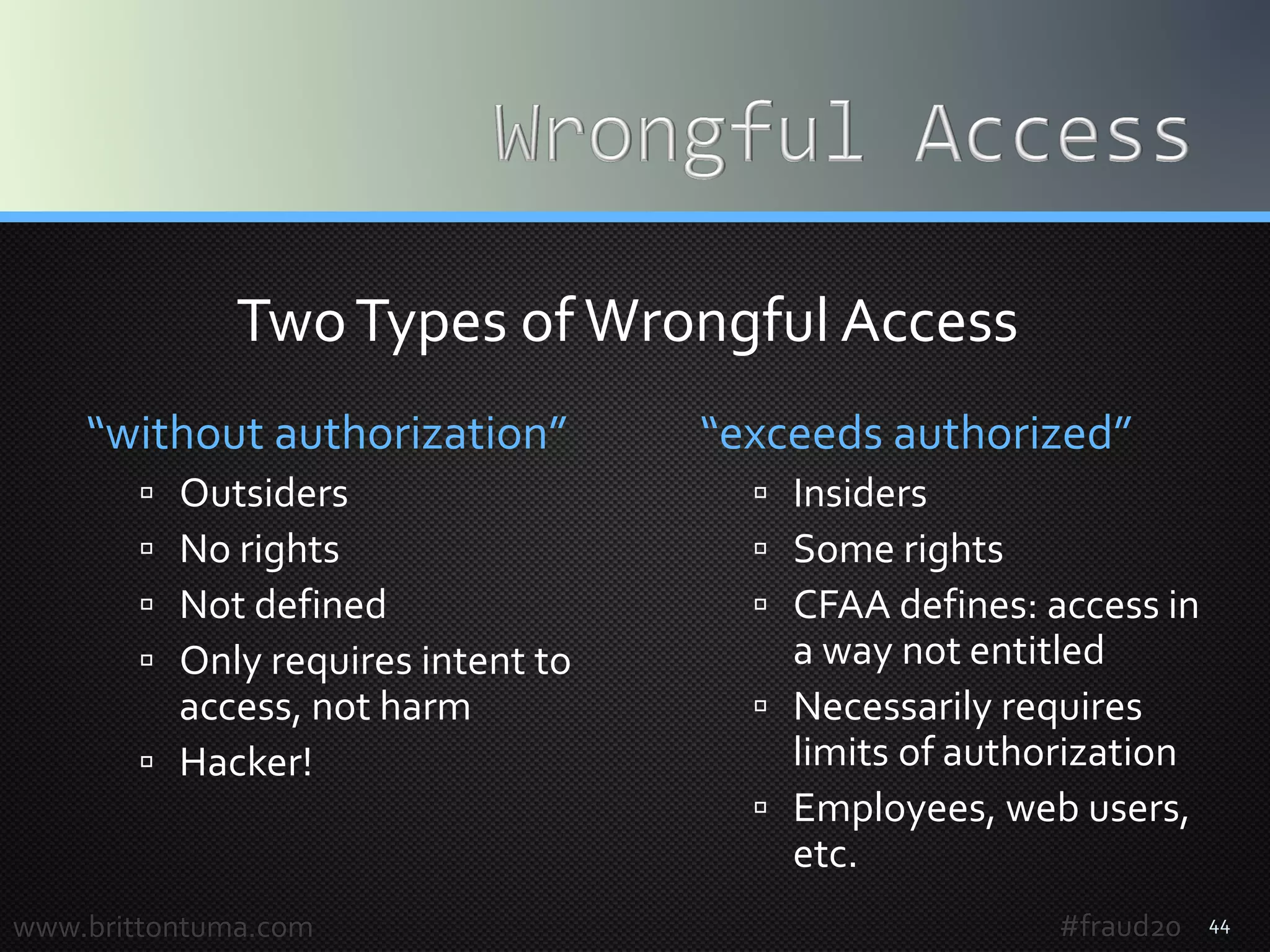
The document provides an overview of computer fraud, including statistics on cybercrime and a discussion on the Computer Fraud and Abuse Act (CFAA). It details the evolution of fraud into 'Fraud 2.0', highlighting concerns about unauthorized access, data breaches, and the implications of evolving technology. Key legal principles and case studies illustrate the application and complexity of the CFAA in addressing modern fraud and data security issues.





![10
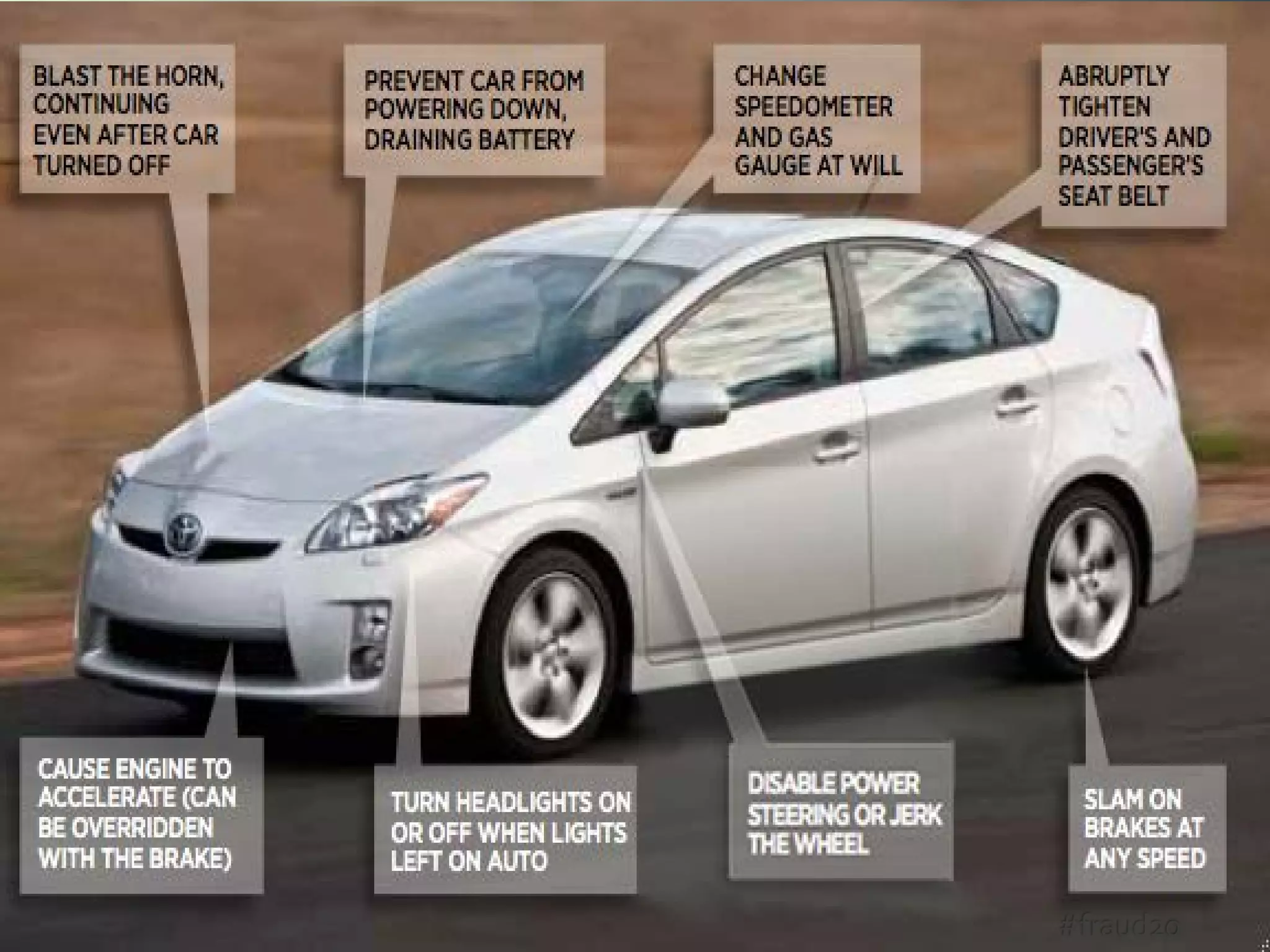
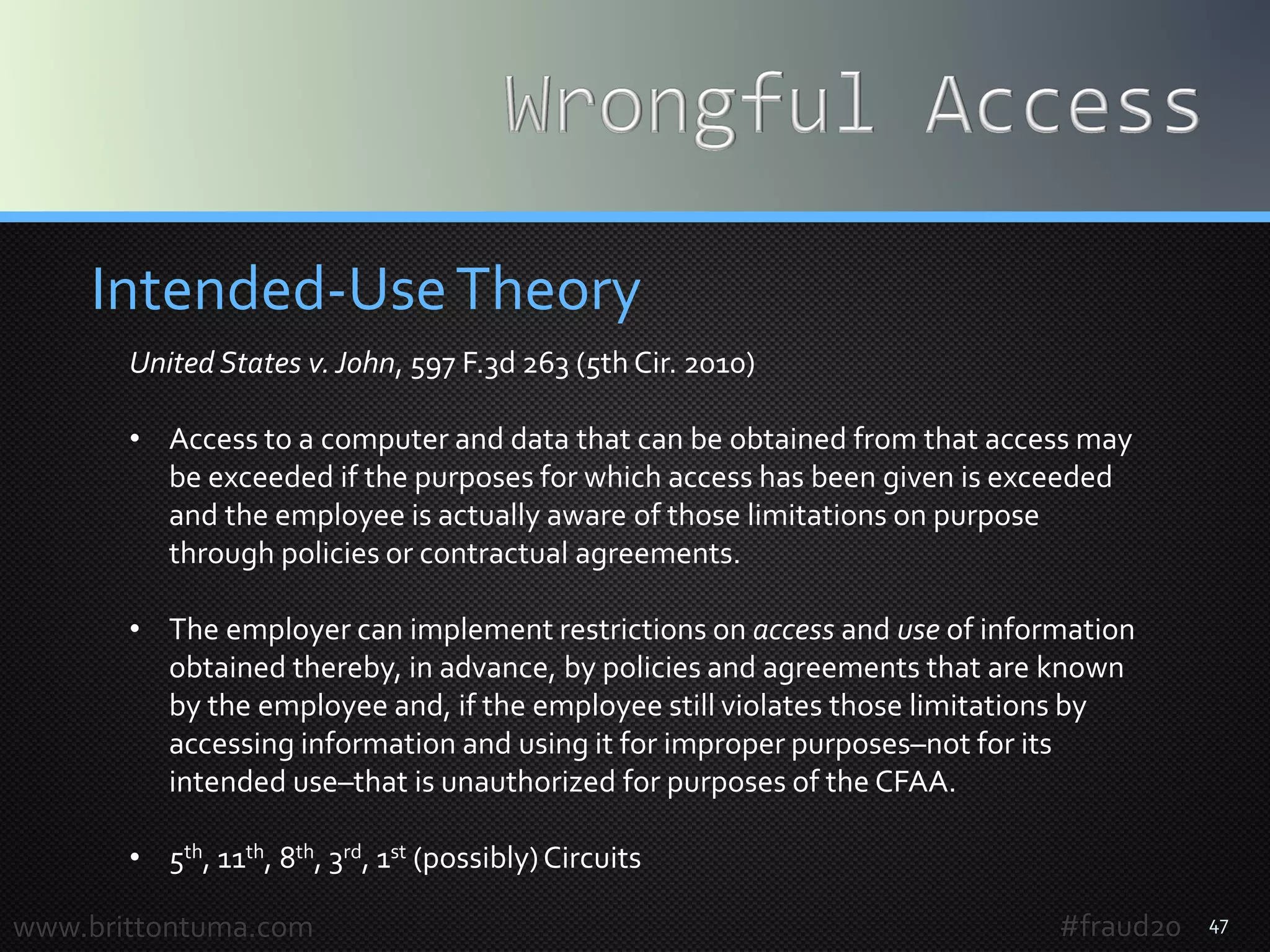
Computer Fraud = Fraud 2.0
• Deception, through the use of a computer
• “old crimes committed in new ways … using computers
and the Internet to make the task[s] easier”
• computer hacking, data theft, theft of money, breaches
of data security, corporate espionage, privacy breaches,
computer worms,Trojan horses, viruses, malware, denial
of service attacks
• mouse and keyboard = modern fraudster tools of choice
www.brittontuma.com #fraud20](https://image.slidesharecdn.com/updateonthecomputerfraudandabuseact-datasecurityprivacycommitteeofstatebaroftexas-130828131353-phpapp02/75/Overview-and-Update-on-the-Computer-Fraud-and-Abuse-Act-CFAA-for-the-Data-Security-Privacy-Committee-of-State-Bar-of-Texas-10-2048.jpg)

























![51
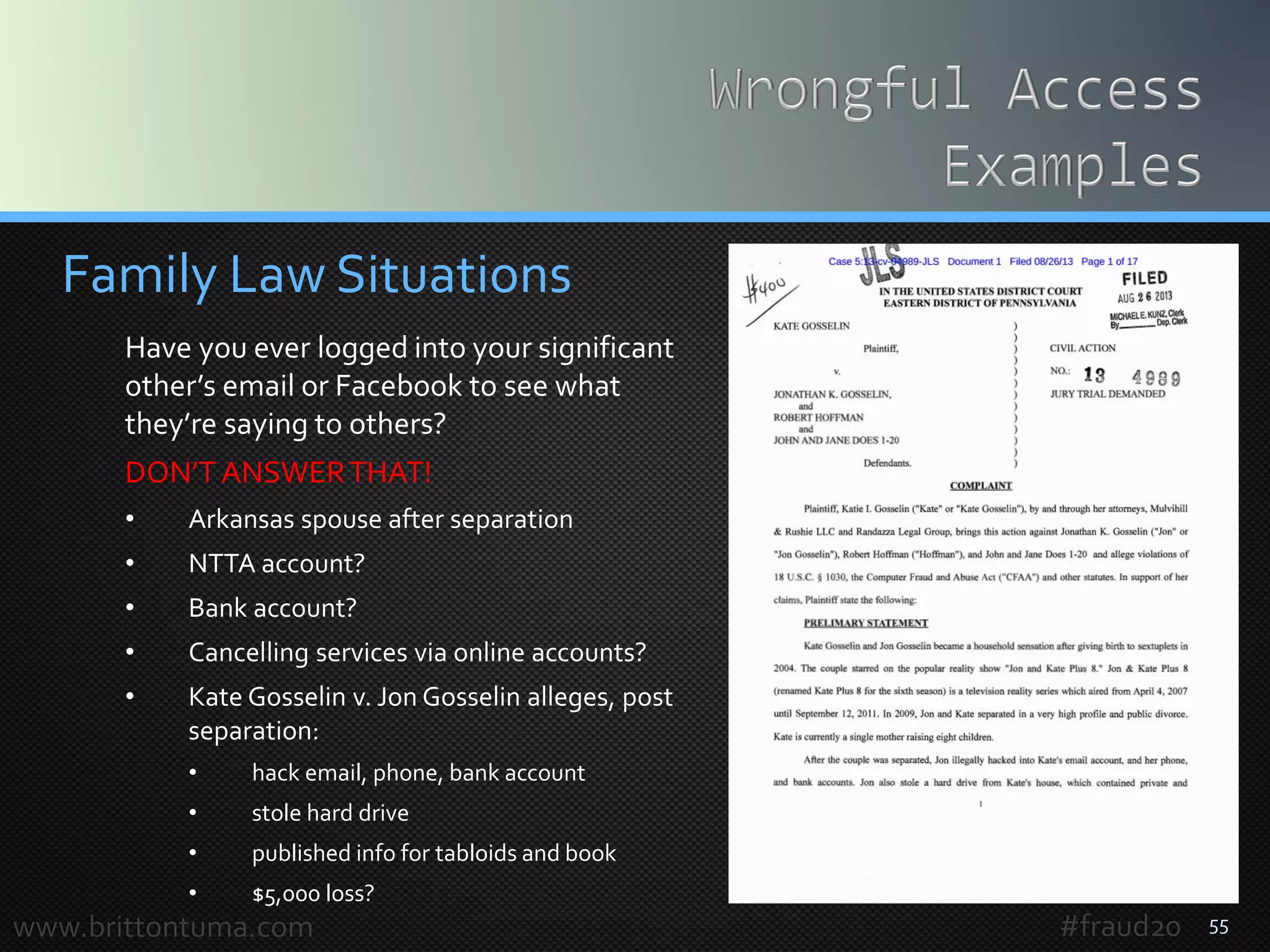
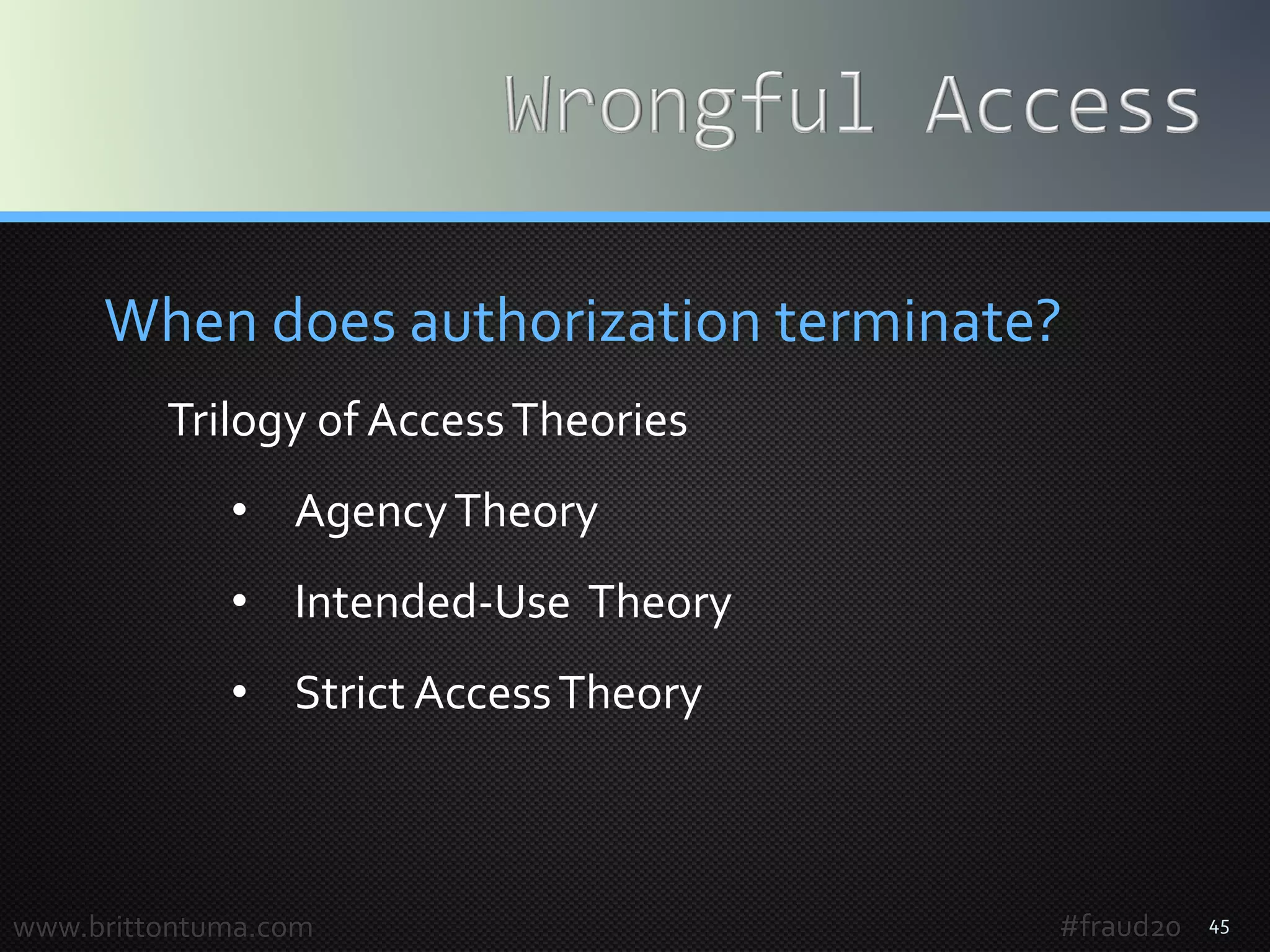
Ways to terminate for Strict Access
Craigslist Inc. v. 3Taps Inc., 2013WL 447520 (ND Ca. Aug. 16, 2013)
3Taps operates an online service that aggregates and republishes ads
from Craigslist.After learning, Craigslist took two important steps:
1. sent a cease-and-desist letter informing “[t]his letter notifies you that you
and your agents, employees, affiliates, and/or anyone acting on your behalf
are no longer authorized to access, and/or prohibited from accessing
Craigslist ‘s website or services for any reason” (clear and direct notice)
2. configured its website to block access from IP addresses associated with
3Taps (technological restrictions)
Craigslist as owner of the website rescinded that permission for 3Taps and
further access by 3Taps after that rescission was “without authorization.”
With active monitoring, access and use can be controlled with CFAA.
www.brittontuma.com #fraud20](https://image.slidesharecdn.com/updateonthecomputerfraudandabuseact-datasecurityprivacycommitteeofstatebaroftexas-130828131353-phpapp02/75/Overview-and-Update-on-the-Computer-Fraud-and-Abuse-Act-CFAA-for-the-Data-Security-Privacy-Committee-of-State-Bar-of-Texas-51-2048.jpg)